Traffic big data suspect vehicle inspection deployment and control method and device
A technology of suspect vehicles and big data, applied in the field of urban traffic safety, can solve the problem of unrecognizable cloned cars, and achieve the effect of improving the success rate of seizure, avoiding waste, and reducing the number of false alarms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
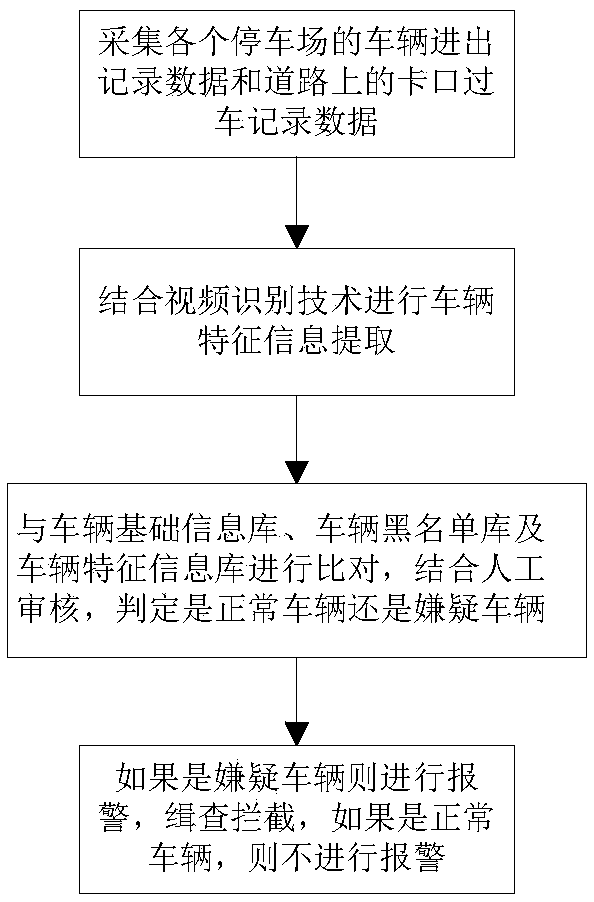
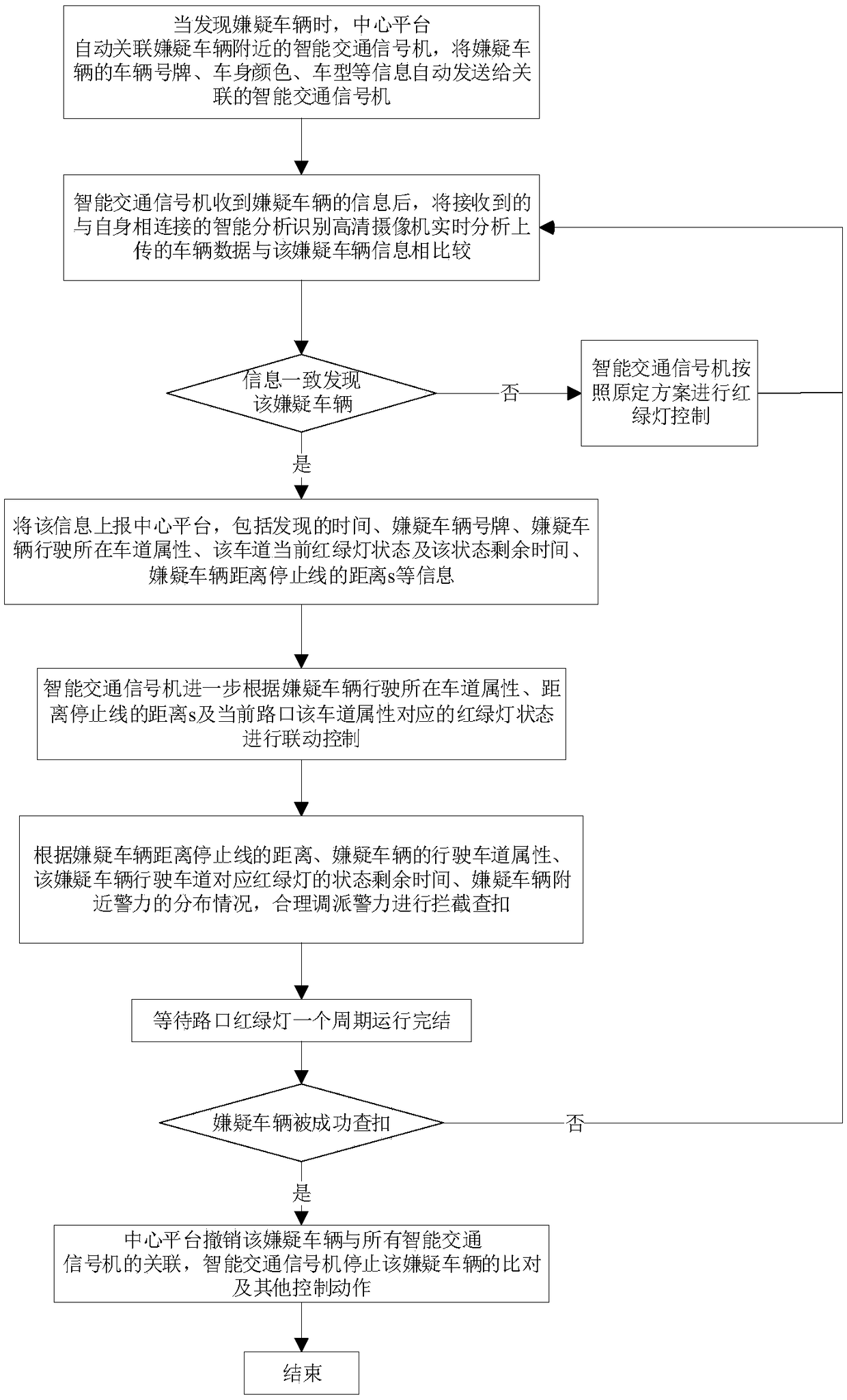
[0082] This embodiment provides a traffic big data suspect vehicle detection and deployment method based on vehicle characteristics. Through the suspect vehicle discovery method, the suspect vehicle blacklist and the suspect vehicle feature information are determined. When a vehicle with the same license plate as the suspect vehicle appears, according to The basic information and characteristic information of the suspect vehicle determine whether it is a suspect vehicle or a normal vehicle. If it is a suspect vehicle, it will be alarmed and intercepted, and it will be linked with the nearby intelligent traffic signal to prolong the time for the suspect vehicle to pass through the intersection; if it is a normal vehicle, it will not Make an alarm.
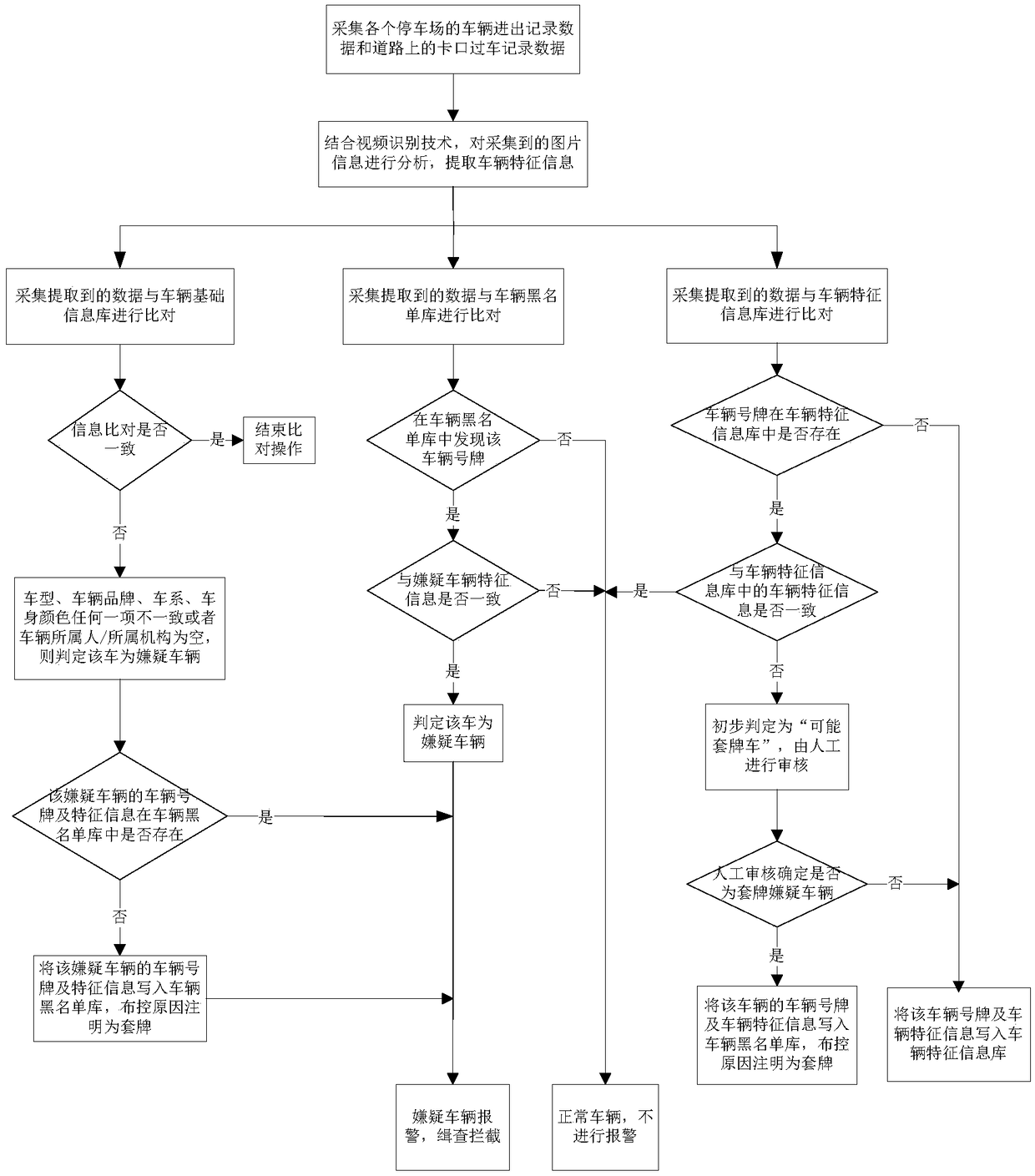
[0083] see figure 1 In this embodiment, the suspected vehicle discovery method is to collect the vehicle entry and exit record data of each parking lot and the checkpoint passing record data on the road. The specific information inc...
Embodiment 2
[0129] see Figure 5 This embodiment provides a device for detecting and controlling suspected traffic big data vehicles based on vehicle characteristics that can implement the method for detecting and controlling suspected traffic big data vehicles based on vehicle characteristics described in Embodiment 1. It mainly includes a central platform and The front-end subsystem, the central platform and the front-end subsystem are connected by communication. The central platform mainly includes the central control module, the suspect vehicle discovery module, the alarm module, the communication module, the basic vehicle information database, the vehicle blacklist database and the vehicle characteristic information database. The central control The modules are respectively connected with the suspect vehicle discovery module, the alarm module, and the communication module, and the suspect vehicle discovery module is connected with the vehicle basic information database, vehicle blackl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com