Patents
Literature
142results about How to "Improve discovery rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
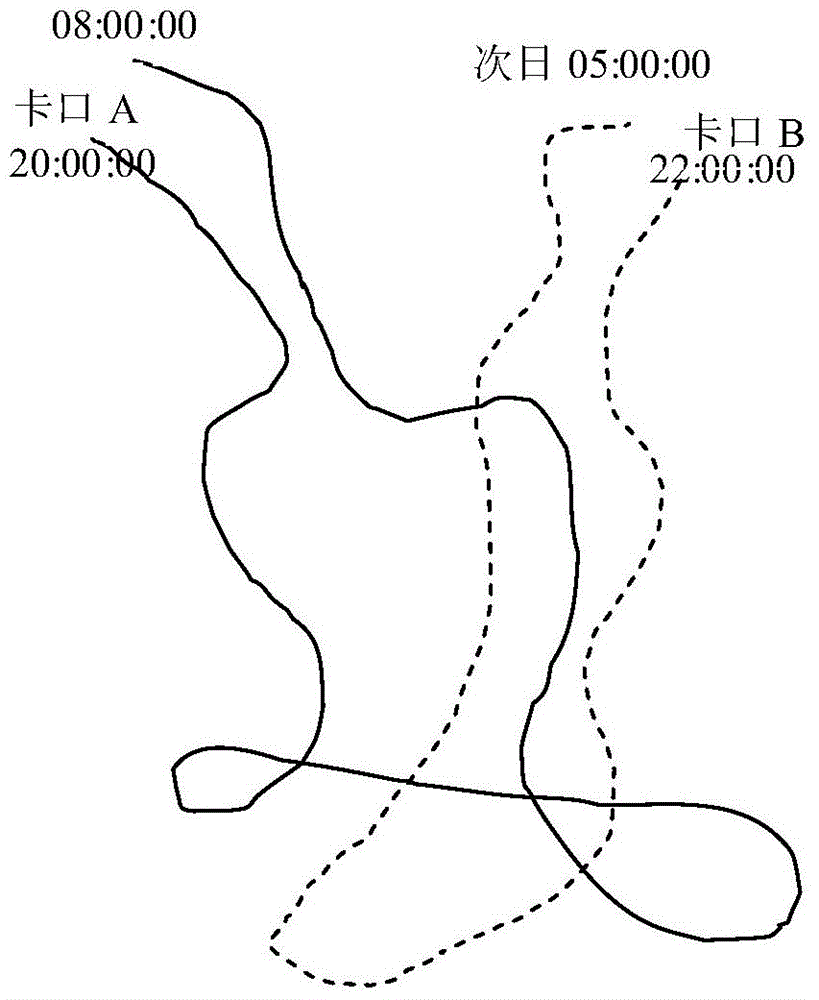
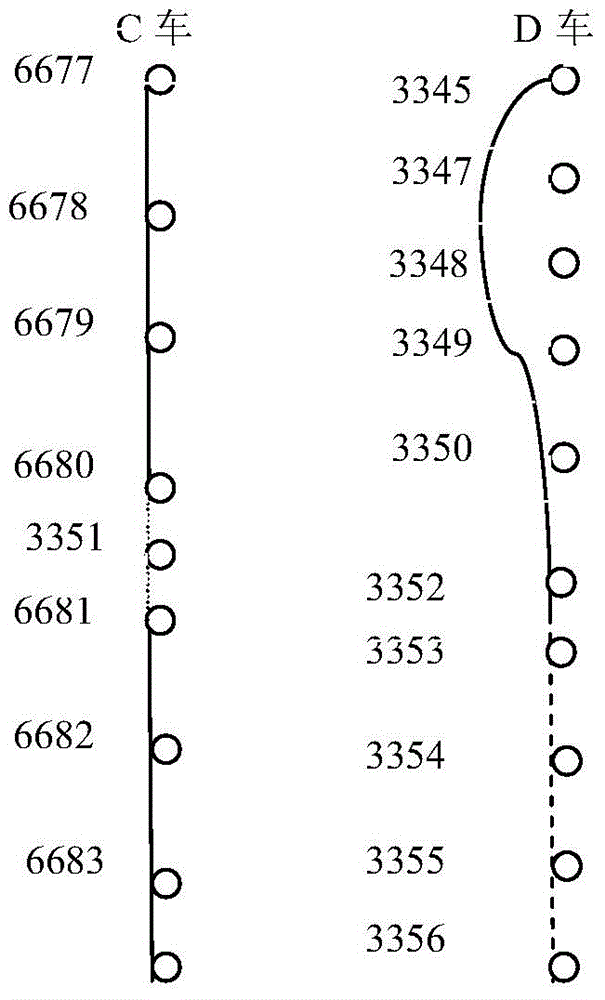
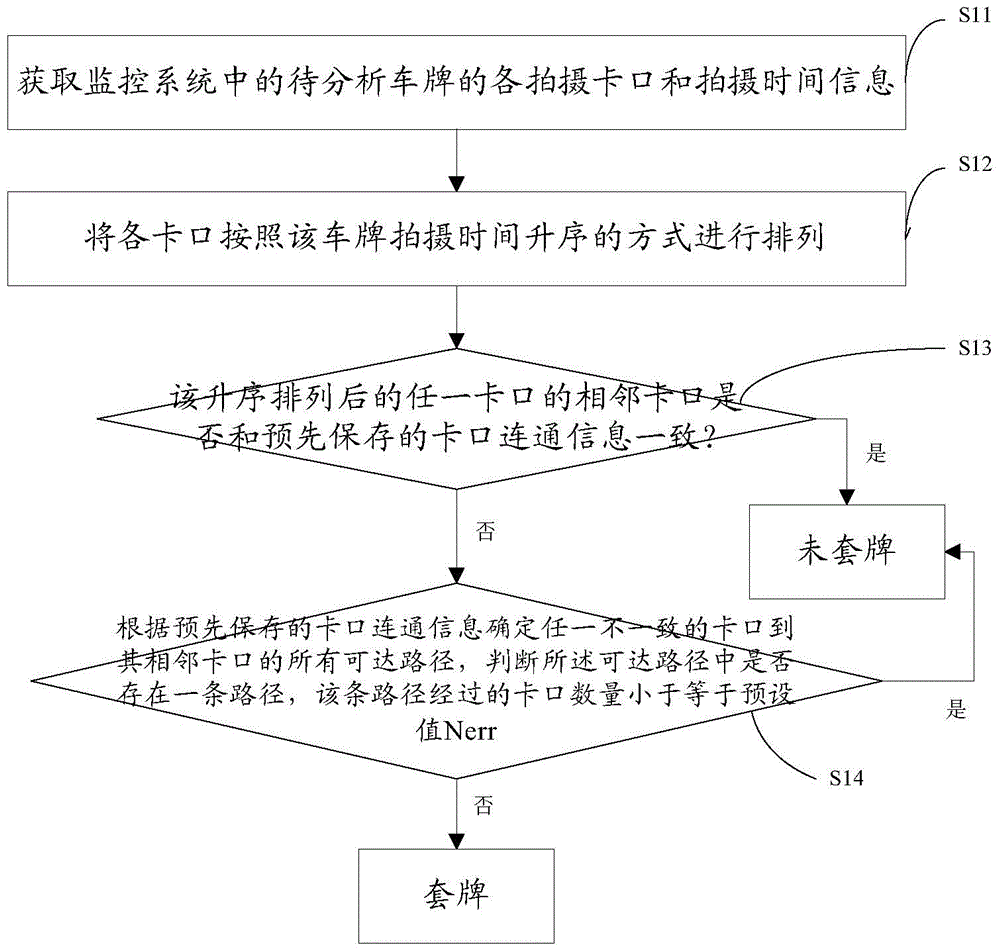
Method and device for fake-license-plate analysis
ActiveCN103914986AImprove discovery rateEfficient use ofRoad vehicles traffic controlTemporal informationMonitoring system
The invention provides a method for fake-license-plate analysis. The method comprises the steps that (1) information of all shooting checkpoints and information of the shooting time of license plates, to be analyzed, in a monitoring system are obtained; (2) the checkpoints are sequenced according to the sequence of the shooting time of the license plates; (3) whether information of a checkpoint adjacent to any checkpoint of the sequenced checkpoints is consistent with prestored checkpoint communicating information or not is judged, if yes, the license plates are real, and if not, the step (4) is executed, wherein the checkpoint communicating information is used for recording adjacency relation of the checkpoints; (4) all reachable paths from any inconsistent checkpoint to a checkpoint adjacent to the inconsistent checkpoint are determined according to the prestored checkpoint communicating information, whether a path meeting the requirement that the number of the checkpoints on the path is smaller than or equal to a preset value N exists in the reachable paths or not is judged, if yes, the license plates are real, and if not, fake license plates exist in the license plates. The method for fake-license-plate analysis overcomes the defect caused by fake-license-plate analysis through time track collisions.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
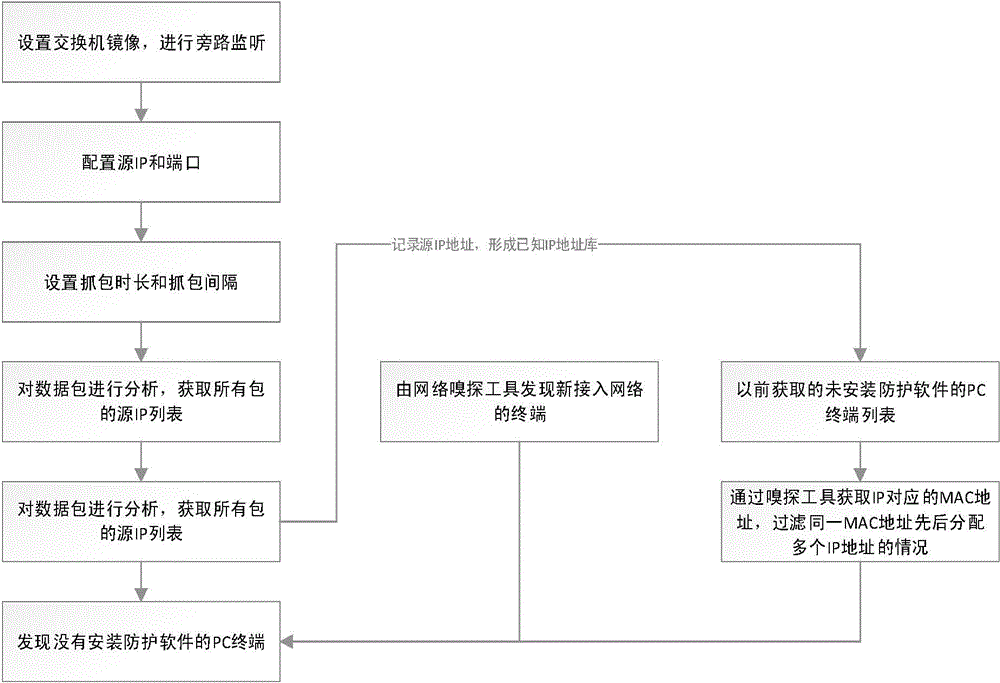
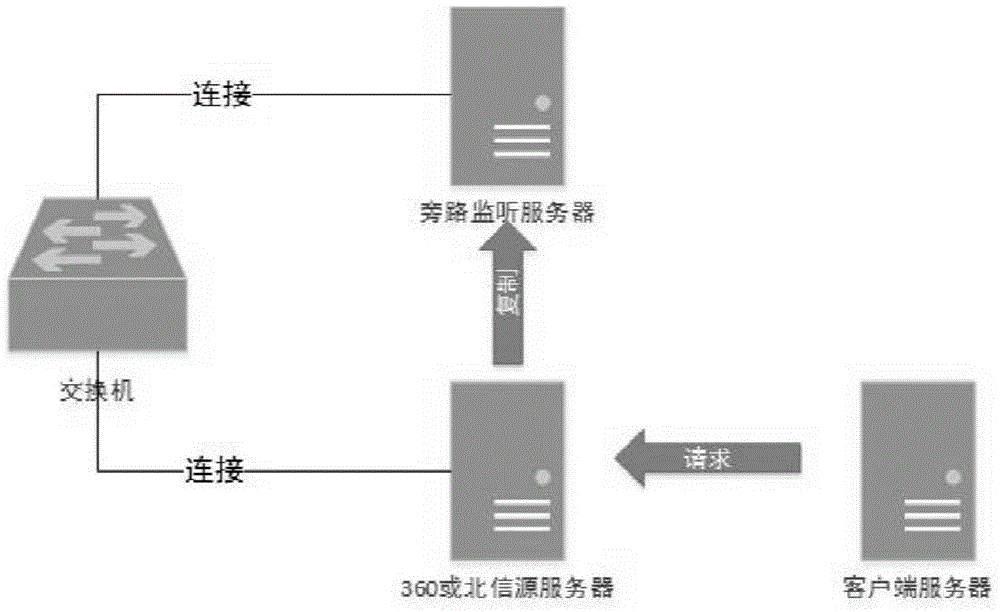
Network security monitoring method based on bypass monitoring and software packet capturing technology
InactiveCN104601570AImprove discovery rateSpeed of discoveryTransmissionIp addressLocal area network
The invention discloses a network security monitoring method based on bypass monitoring and software packet capturing technology. The method comprises the steps of (1) setting bypass monitor to an exchange at the same network section with a network security protection server; (2) configuring a source server IP of which the network packet is to be monitored and a data sending port; (3) setting the length of packet capturing time and packet capturing interval; (4) capturing and caching a network data packet, analyzing, and acquiring a source IP list in the data packet through a regular expression; (5) recording the source IP address to form a known IP address library; (6) finding out a new terminal accessed to the network through a network sniffing tool; (7) comparing the source IP list with all PC server lists in the LAN, and determining whether the corresponding security protection software is installed to a client PC terminal. With the adoption of the method, the rate and speed of finding the PC terminal without being provided with the security protection software are improved, and attack from the potential virus and Trojan caused by accessing the PC terminal without being equipped with the security protection software into the network can be reduced.
Owner:STATE GRID CORP OF CHINA +3
Radar detection system and method for low-altitude multi-target classification and identification
ActiveCN108051813ARealize classification recognitionImprove detection accuracyRadio wave reradiation/reflectionIntermediate frequencyWave shape
The invention discloses a radar detection system and method for low-altitude multi-target classification and identification. The radar detection system for low-altitude multi-target classification andidentification includes a waveform generator, an antenna unit, a reception unit and a signal processing unit, wherein the waveform generator is used for generating detection wave beams in which the energy is concentrated below the specified threshold according to the low-altitude area to be detected; the antenna unit is used for transmitting the detection wave beams output from the waveform generator and receiving a target echo signal; the reception unit is used for performing down-conversion on the target echo signal received by the antenna unit to become an intermediate frequency signal andoutput the intermediate frequency signal; and the signal processing unit is used for acquiring the positional information of the target according to the intermediate frequency signal output from thereception unit and outputting the identified target type. The radar detection method for low-altitude multi-target classification and identification is to realize low-altitude multi-target classification and identification. The radar detection system and method low-altitude multi-target classification and identification can realize real-time detection and classification and identification of low-altitude multiple targets, and have the advantages of high identification efficiency, high accuracy and high flexibility.
Owner:HUNAN NOVASKY ELECTRONICS TECH
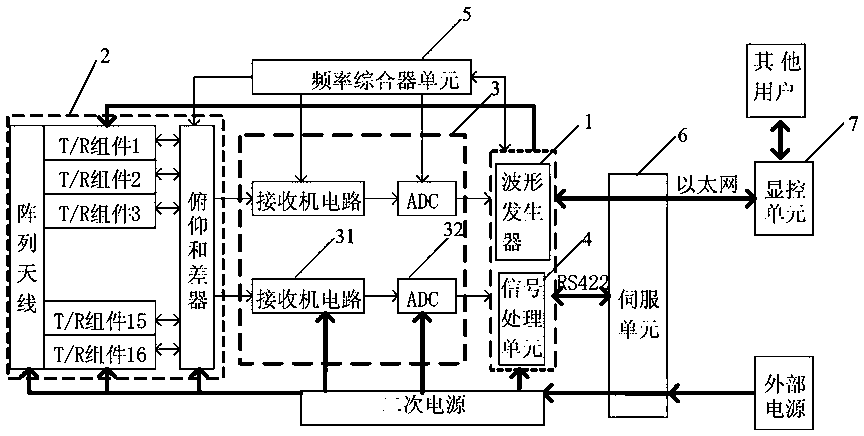
Two-dimensional frequency-phase scanning small target detection system
ActiveCN106291477AStrong anti-interference abilityGood high reliability performanceWave based measurement systemsVIT signalsTiming generator
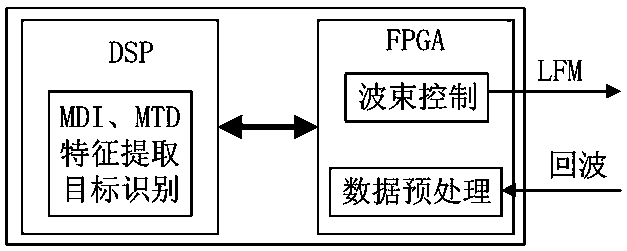
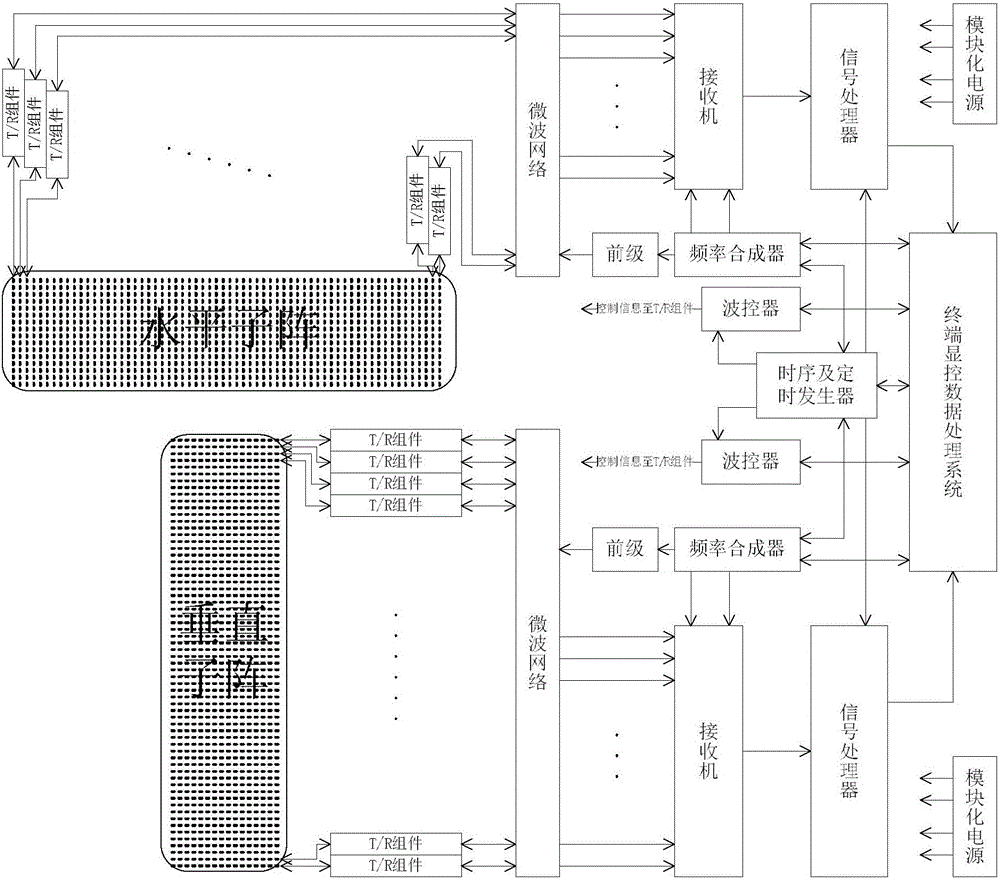
The invention provides a two-dimensional frequency-phase scanning small target detection system, aiming to provide a target detection system which is high in discovery rate, optimal in low-attitude detection performance, and high in anti-interference capability. The antennas of a horizontal sub-array and a vertical sub-array are connected with their respective microwave networks through their respective T / R components, the microwave networks are connected with receivers via n channels, the control information is sent to the T / R components via wave controllers through a time sequence and timing generator, frequency synthesizers are controlled by the time sequence and timing generator to generate excitation signals, the excitation signals are sent to the microwave networks via pre-amplifiers, the microwave networks radiate the beam through the T components to the antennas to the specified detection airspace and control the R components in the arrays to receive the radar echoes specified by emission, the radar echoes are sent to the receivers to signal processors for target detection after being amplified by each column of R components, the target detection data of the horizontal sub-array and the vertical sub-array are integrated, so that the high angle detection accuracy of orientation and pitching is achieved.
Owner:LINGBAYI ELECTRONICS GRP
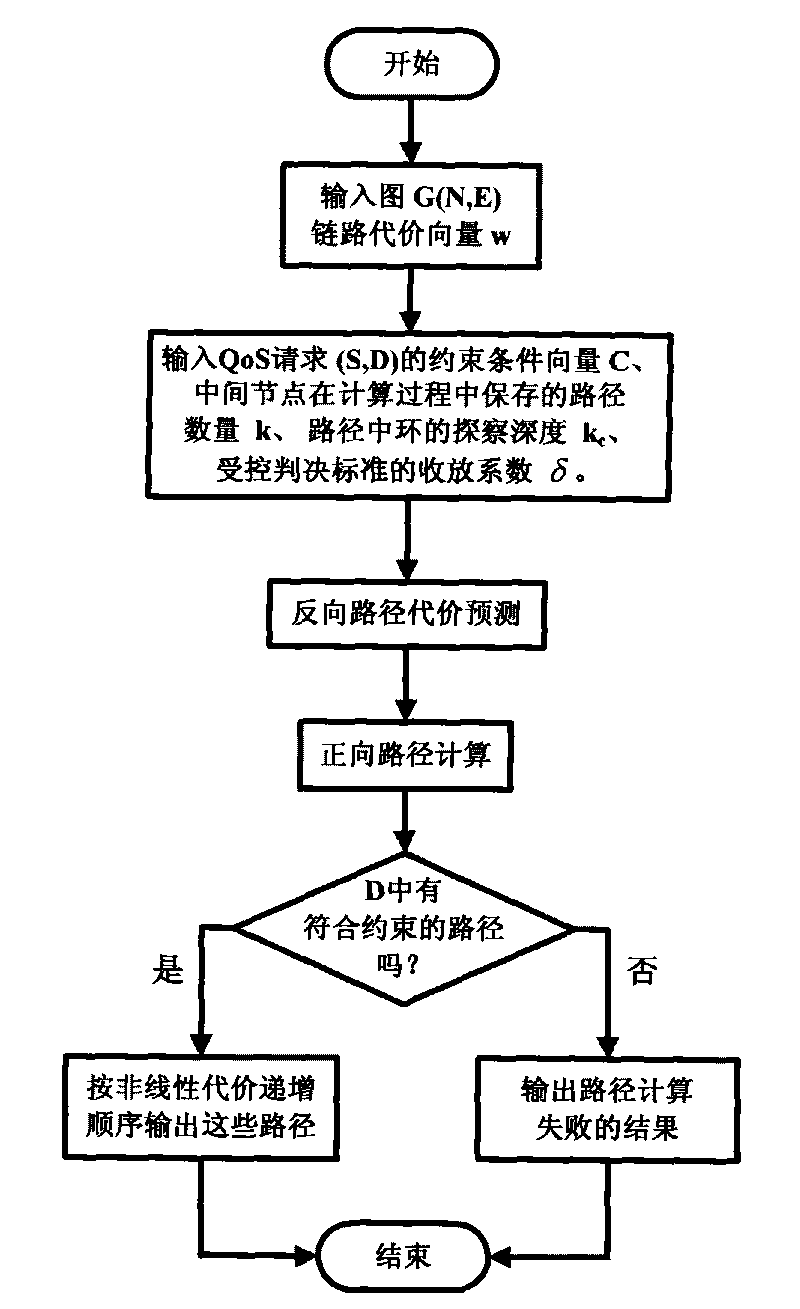
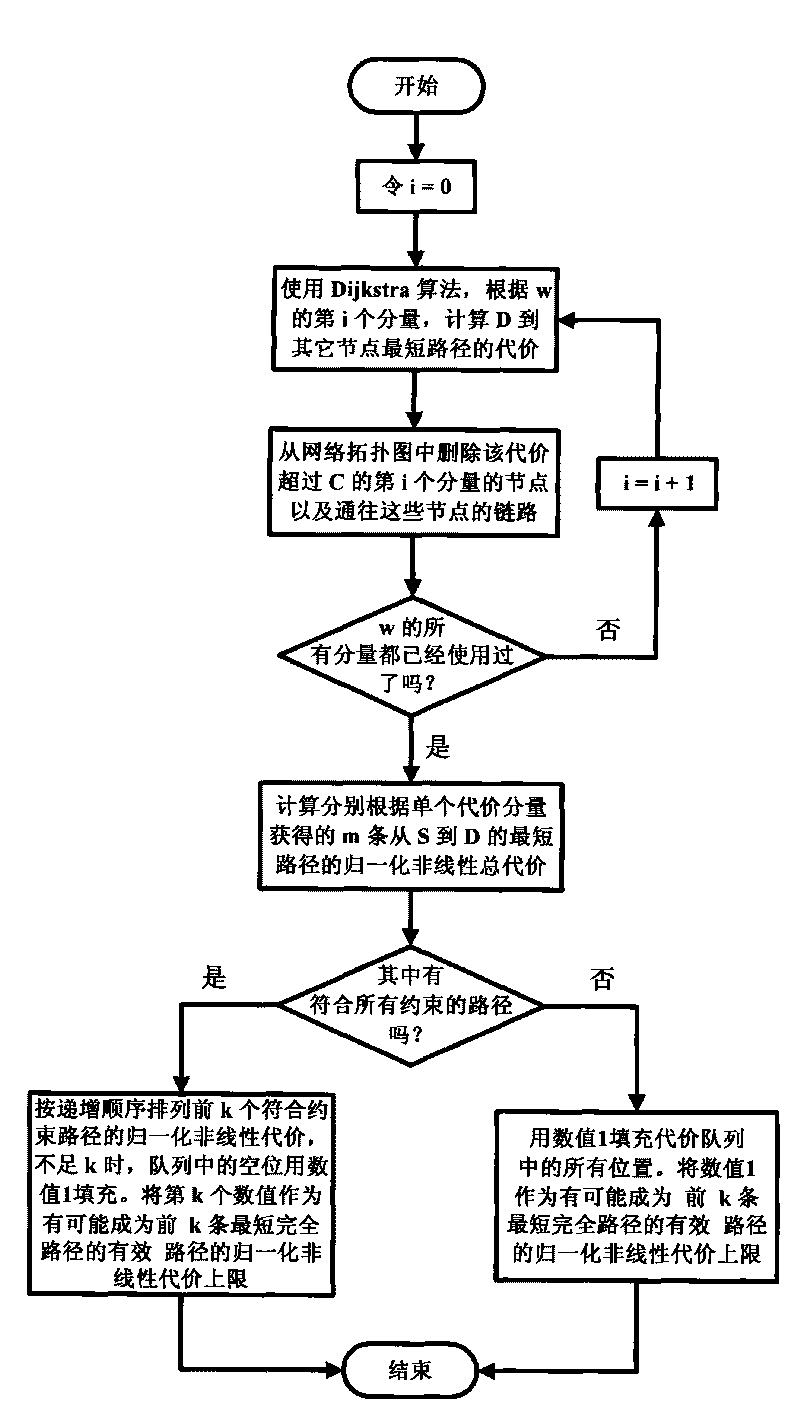
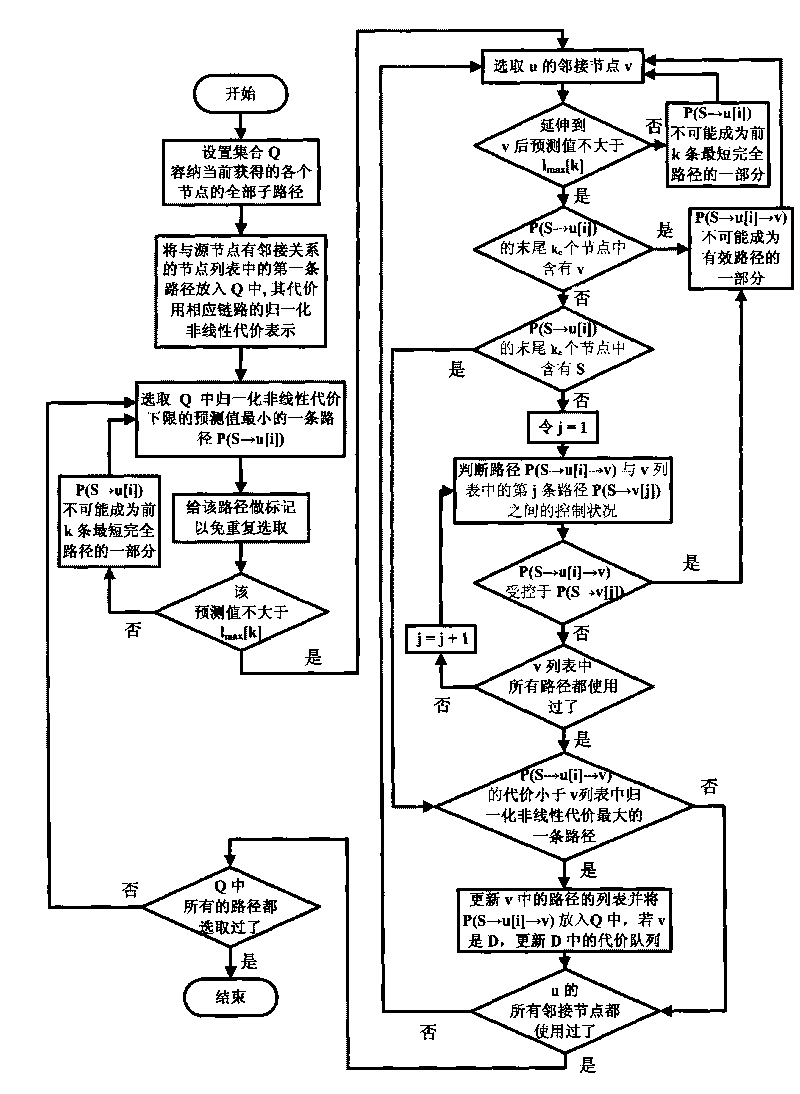
Heuristic method for working out a plurality of shortest simple routes in network under multiple constraints
InactiveCN101753425AIncrease the number ofQuality improvementData switching networksRound complexityComputer science
The invention discloses a heuristic method for working out a plurality of shortest simple routes in network under multiple constraints. The method uses improved route control rules and predication of lower price limit after extending the routes to destination nodes, and abandon the routes which contain rings, break the constraints and exceed the cost of the k obtained shortest simple route. In the reserved routes, front k shortest simple routes meeting constrain conditions are searched in the breadth-first way and adjustable precision. The method has strong adaptability on network types, scales and change of constrain degrees, and the complexity of the method is approaching to the traditional breadth-first searching method. The heuristic method for working out a plurality of shortest simple routes in network under multiple constraints can shown excellent and stable performances on the aspects like route quantity, quality and capacity for discovering routes by setting the probing depth of middle ring of route and retracting coefficients of controlled decision.
Owner:BEIHANG UNIV
Direction-of-arrival estimation method based on sparse representation
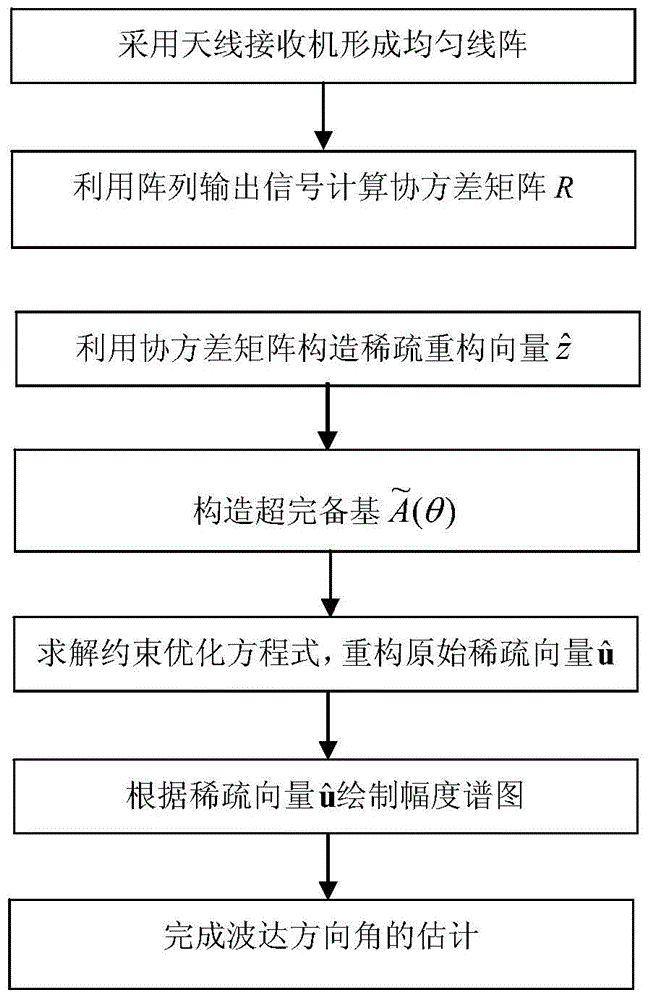
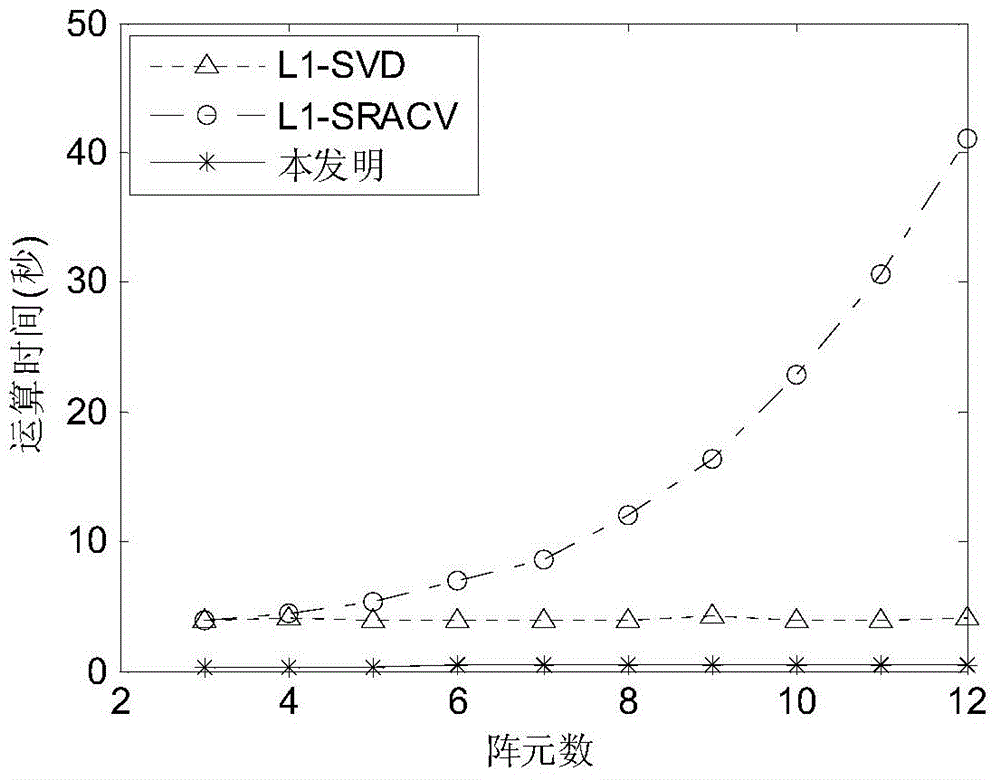
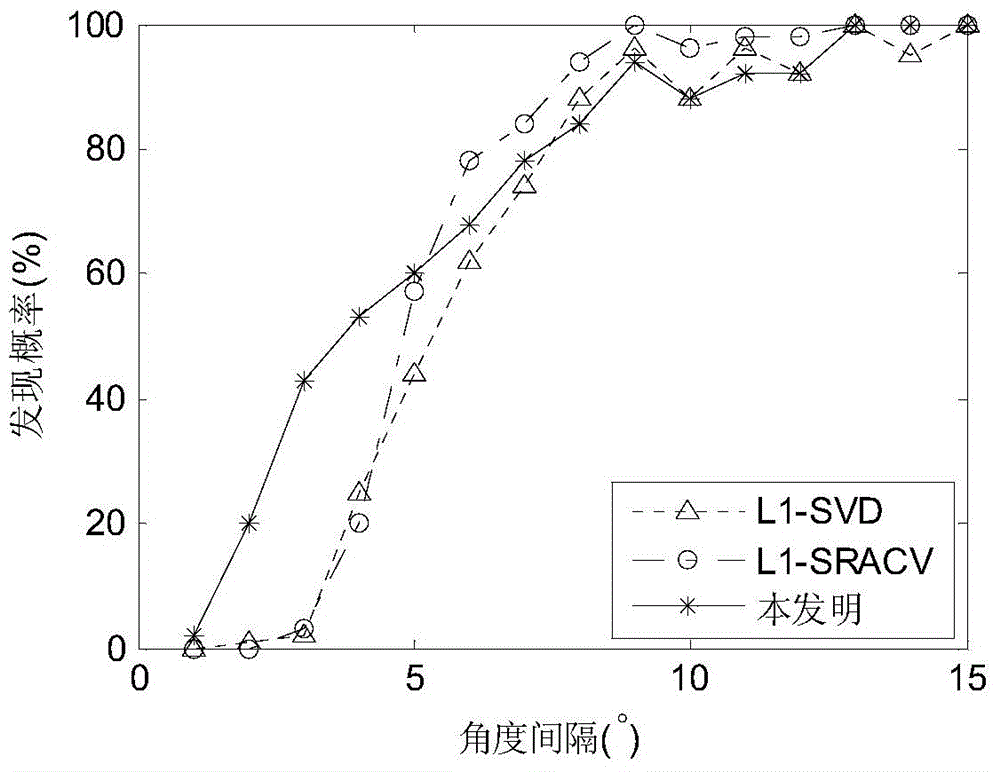
InactiveCN104020438AAvoid anglesBreaking through the Rayleigh limit of resolutionRadio wave direction/deviation determination systemsEstimation methodsImage resolution
The invention discloses a direction-of-arrival estimation method based on sparse representation. The method mainly solves the problems that because a similar technology is large in calculation amount and low in angular resolution, the estimation speed of target reconnaissance and passive location is low and estimation errors in target reconnaissance and passive location are large. The method comprises the implementation steps: (1) acquiring output signals of an array and calculating a covariance matrix R of the signals, (2) constructing reconstructed sparse vectors through lower triangular elements of the covariance matrix R, (3) carrying out mesh generation on a spatial domain to construct a perfect base, (4) converting the direction-of-arrival estimation issue into the issue of solving a constrained optimization equation according to the sparse representation relation between the reconstructed sparse vectors and the perfect base, (5) solving the constrained optimization equation according to the convex optimization method to obtain the optimal estimation vectors, (6) drawing a magnitude spectrum according to the one-to-one correspondence of the optimal estimation vectors and spatial domain angles to obtain the direction-of-arrival value. By means of the method, the calculation speed of target reconnaissance and passive location is decreased, and the estimation errors in target reconnaissance and passive location are reduced. The method can be applied to target reconnaissance and passive location.
Owner:XIDIAN UNIV
Kit for colorectal cancer detection and application thereof
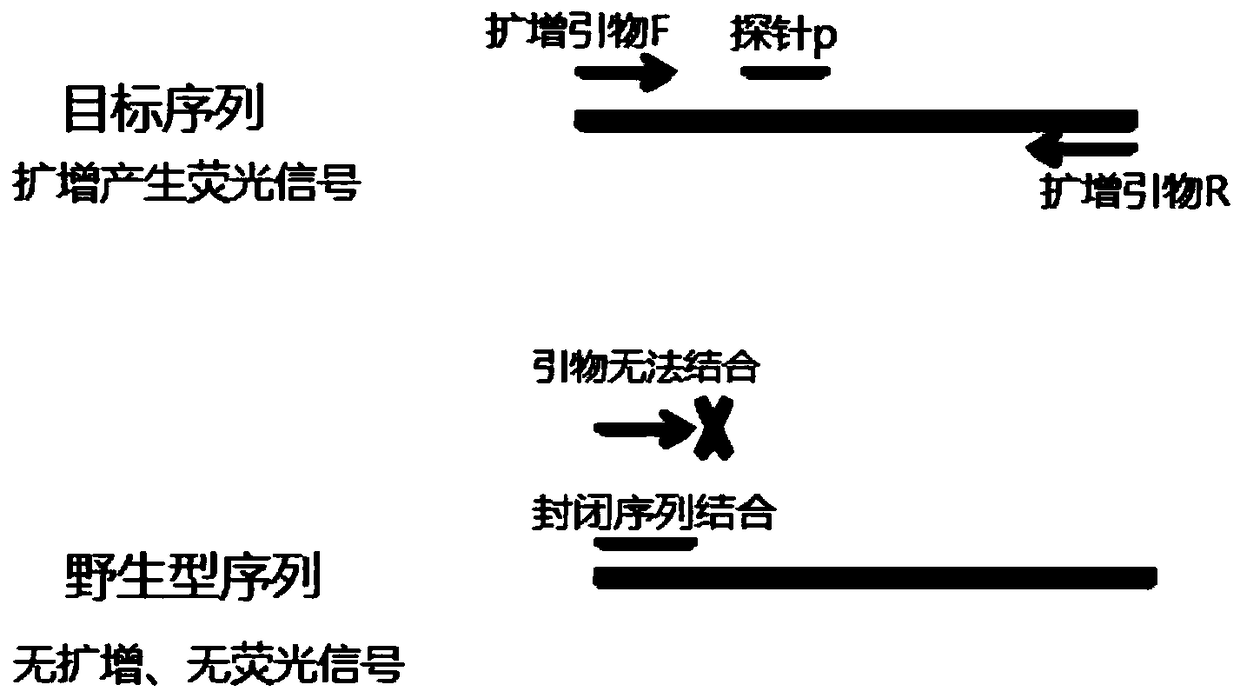
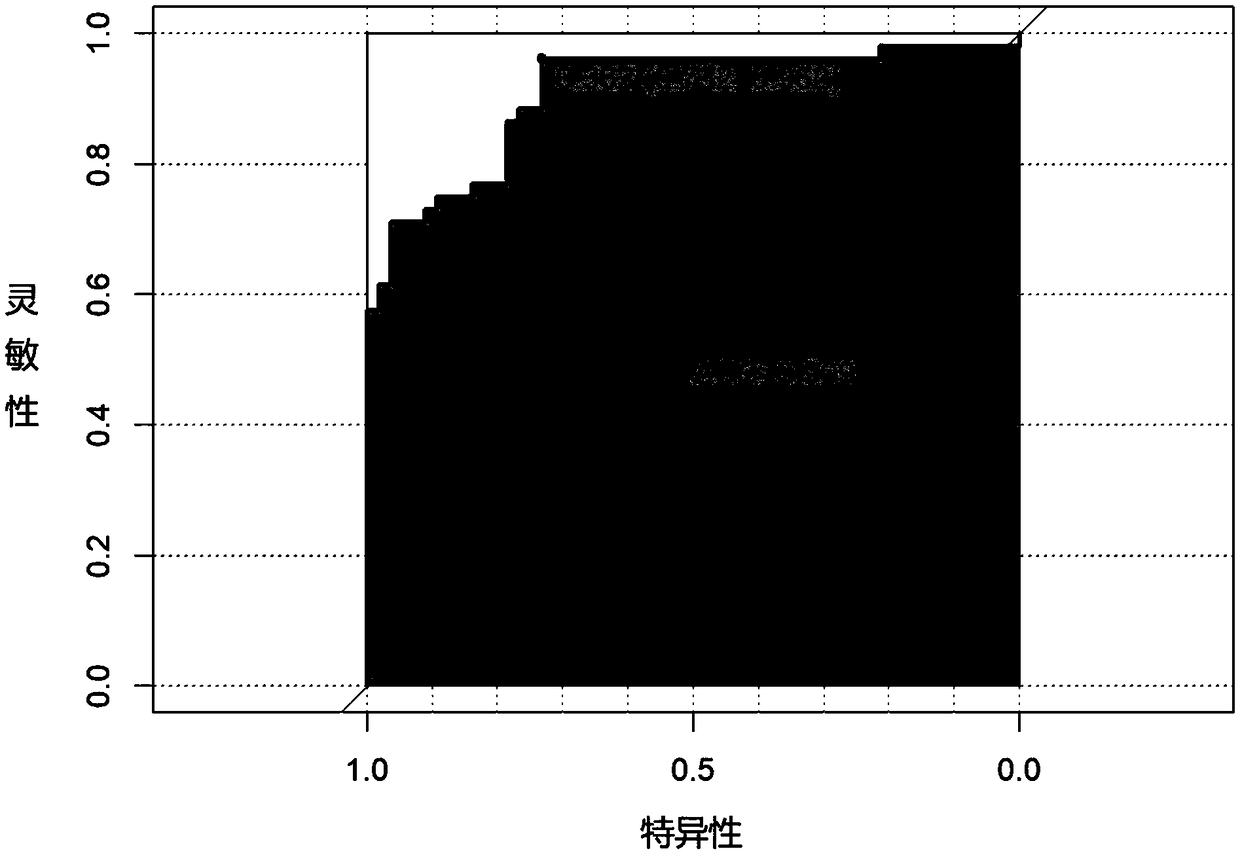
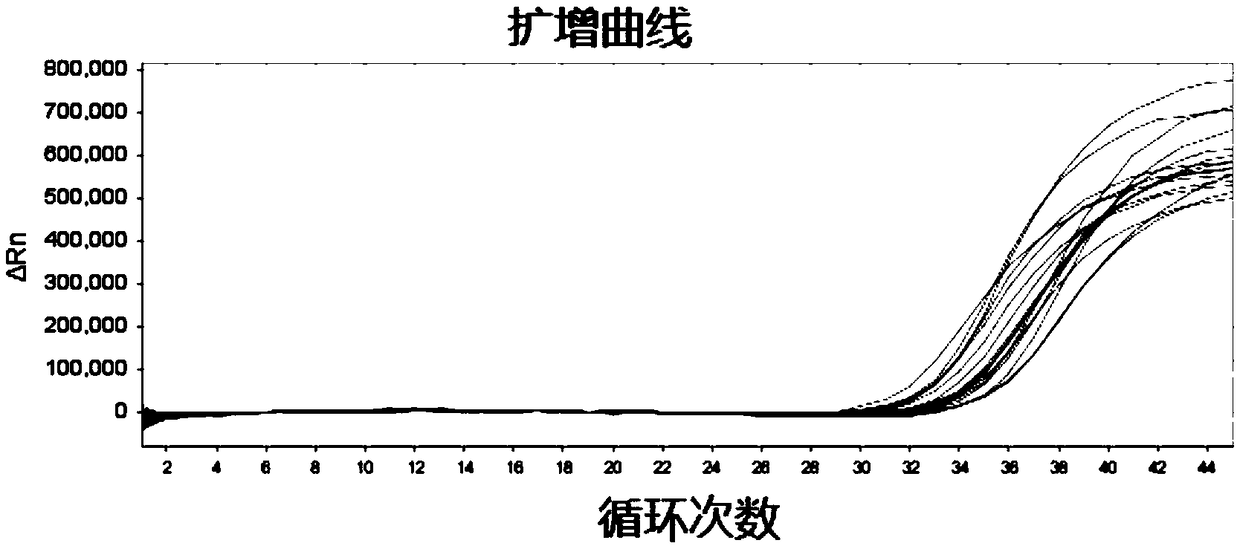
ActiveCN109207592AHigh sensitivityStrong specificityMicrobiological testing/measurementDNA/RNA fragmentationMedicineColorectal cancer
The invention discloses a kit for colorectal cancer detection and an application thereof. The kit comprises a primer composition, and a probe composition. The primer composition comprises BS-S9-F, BS-S9-R, BS-N4-F, BS-N4-R, BS-SDC2-F, BS-SDC2-R, BS-ACT-F and BS-ACT-R. The probe composition comprises BS-S9-P, BS-N4-P, BS-SDC2-P and BS-ACT-P. The kit of the invention can be applied to the detectionof colorectal cancer, and has the advantages of high sensitivity and high specificity.
Owner:GENETALKS BIO TECH CHANGSHA CO LTD +1
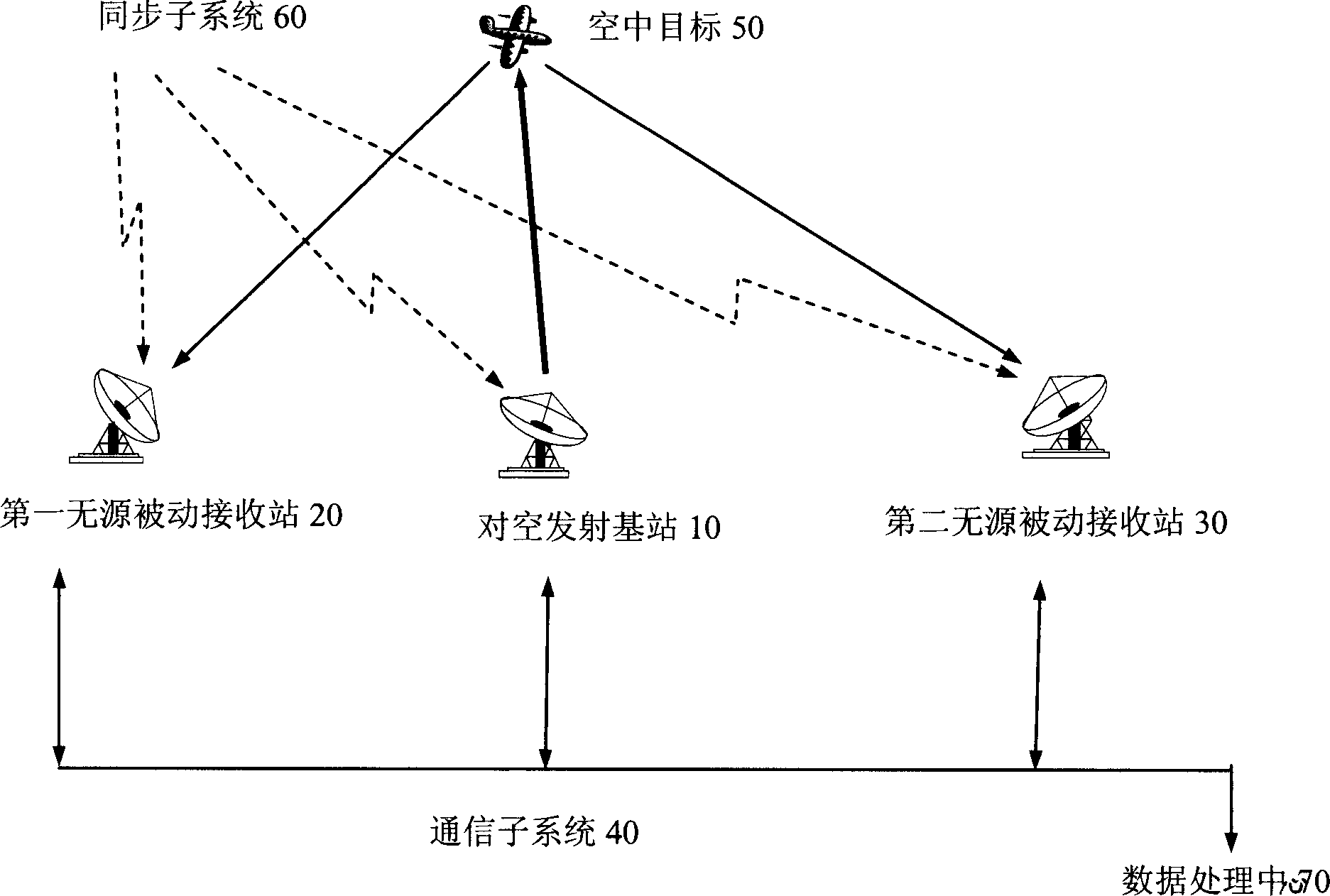
System and method for implementing aerial target monitoring based on public mobile communication network
InactiveCN1633050AImprove stabilityGuaranteed to workPosition fixationRadio transmission for post communicationSurvivabilityEngineering
This invention provides a system and a method for monitoring air targets based on public mobile communication network, which sets up or reforms a communication base station as the air transmission base station and distributes a certain numbers of passive receiving stations around it. The passive receive stations receive the echoes of the air transmission base station radiation signals reflected by the air target and measure the delay time, arriving angle, frequency and phase variance of the echo then to transfer the data to a data process center via network, which processes the data in terms of multi-curve surface intersection method to get data of location, speed, course of the air target and send them to users.
Owner:于耕
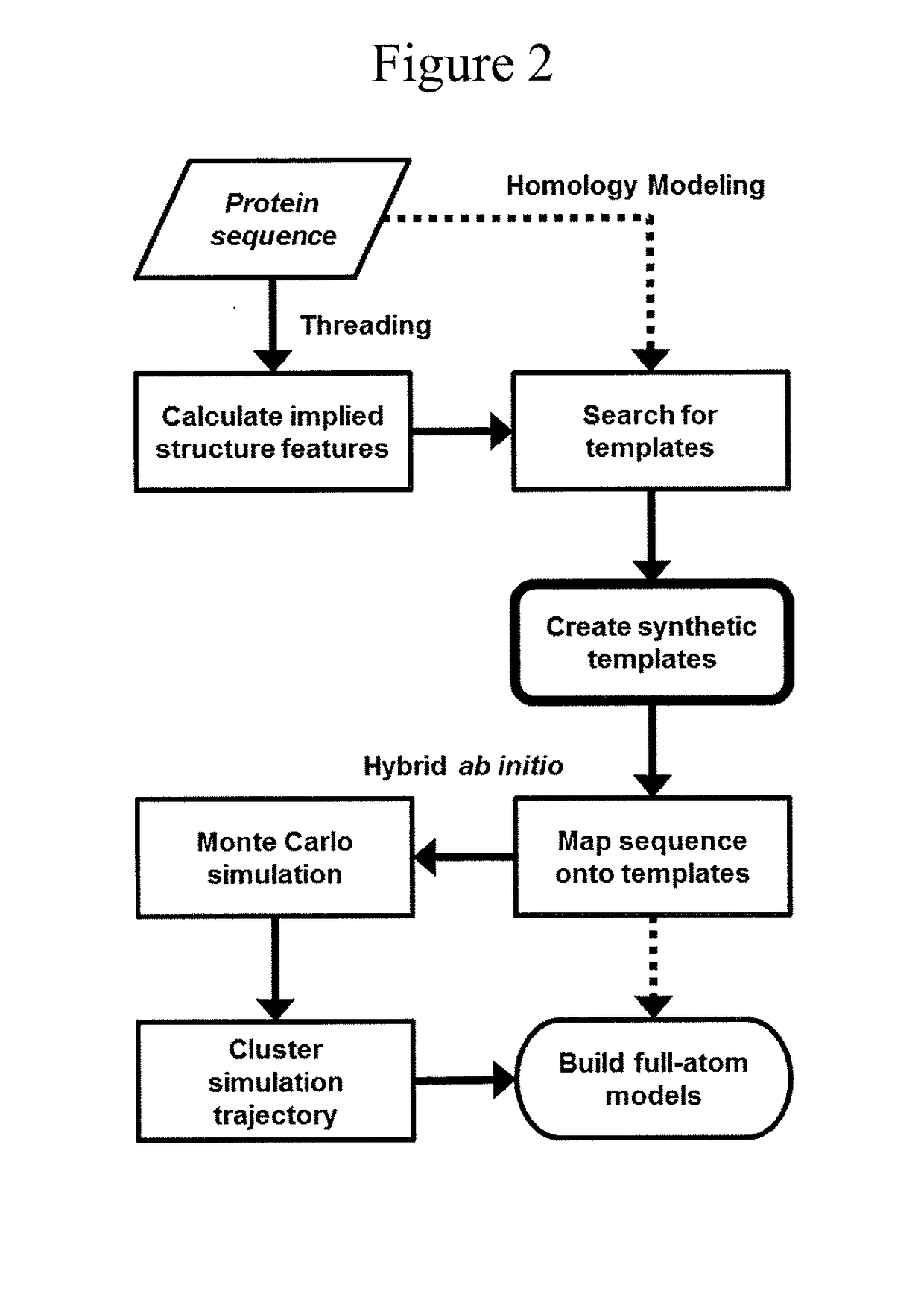
Protein structure prediction system
ActiveUS20180260517A1Increase structural diversityImprove discovery rateChaos modelsNon-linear system modelsEnergy minimizationTarget peptide
The present invention is an accelerated conformational sampling method for predicting target peptide and protein structures comprising a process of determining energy minimized synthetic templates using a simple system for modeling individual molecular bonds within the subject peptide or protein. Use of these synthetic templates greatly reduces the computational resources necessary for optimally determining structural features of the target peptide or protein. The present invention also provides methods for rapid and efficient analysis of the effect of mutations on target peptides and proteins.
Owner:DNASTAR
Method for realizing wireless personal area network routing protocol based on ultra-wide band positioning assist
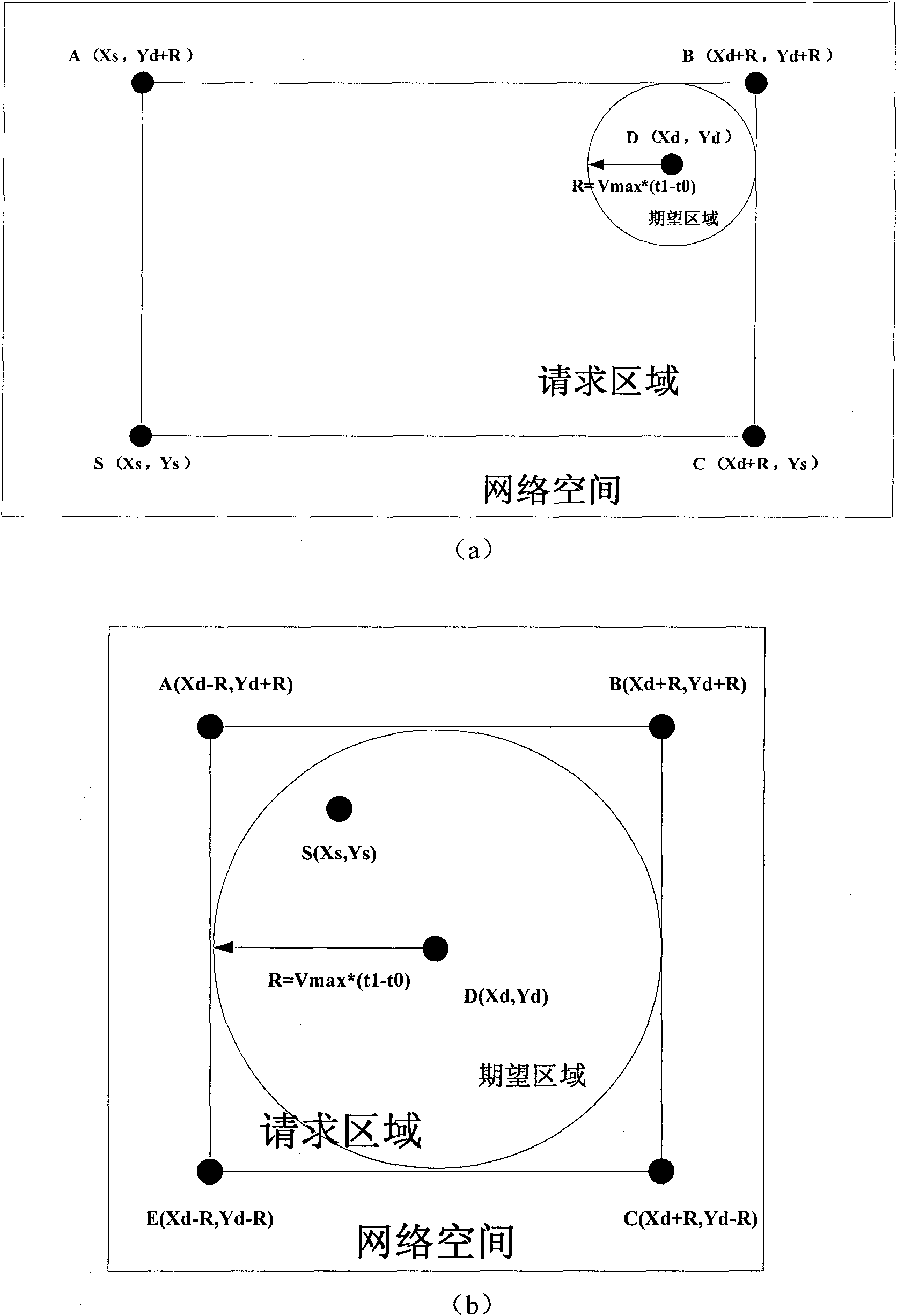
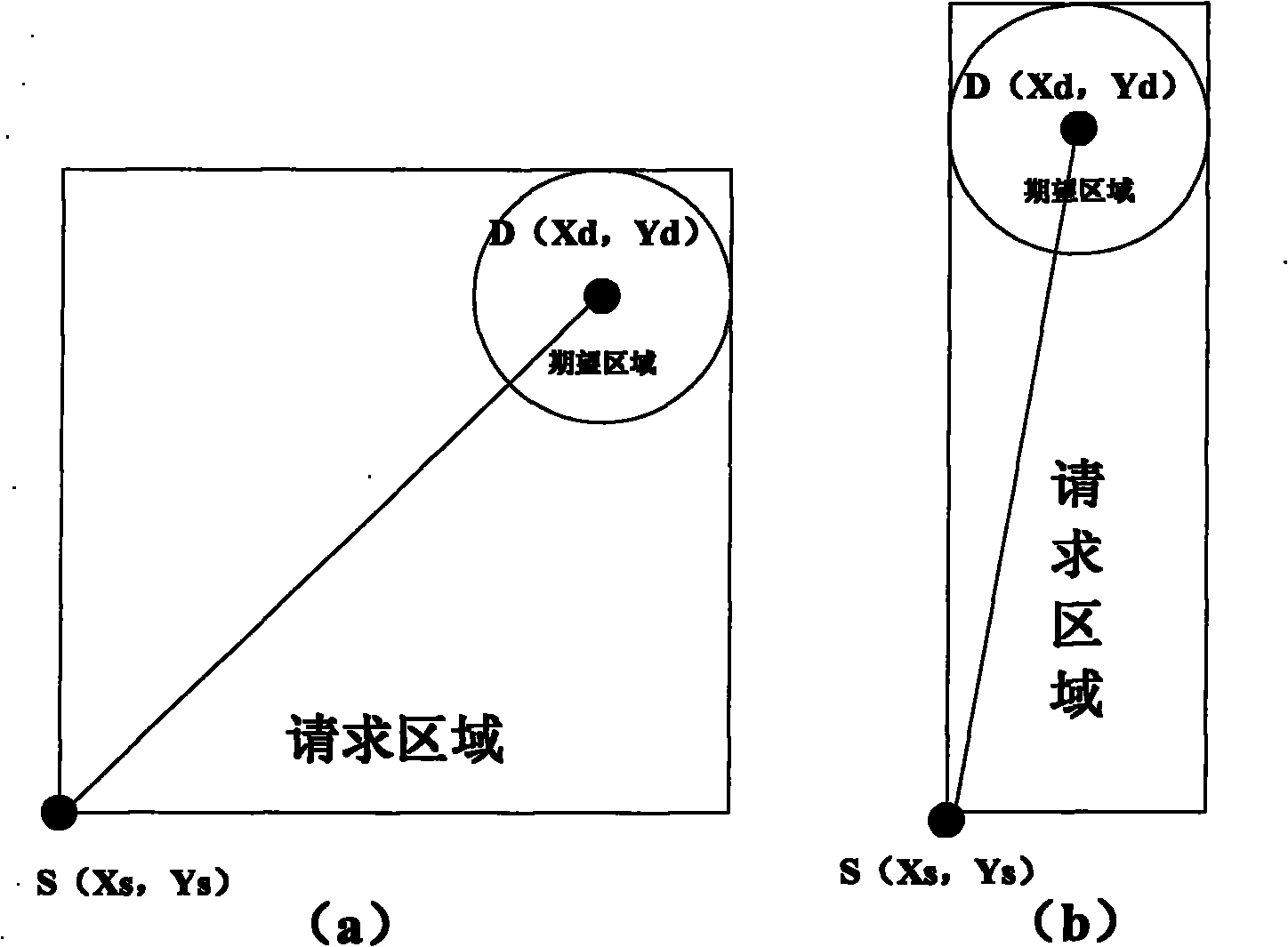
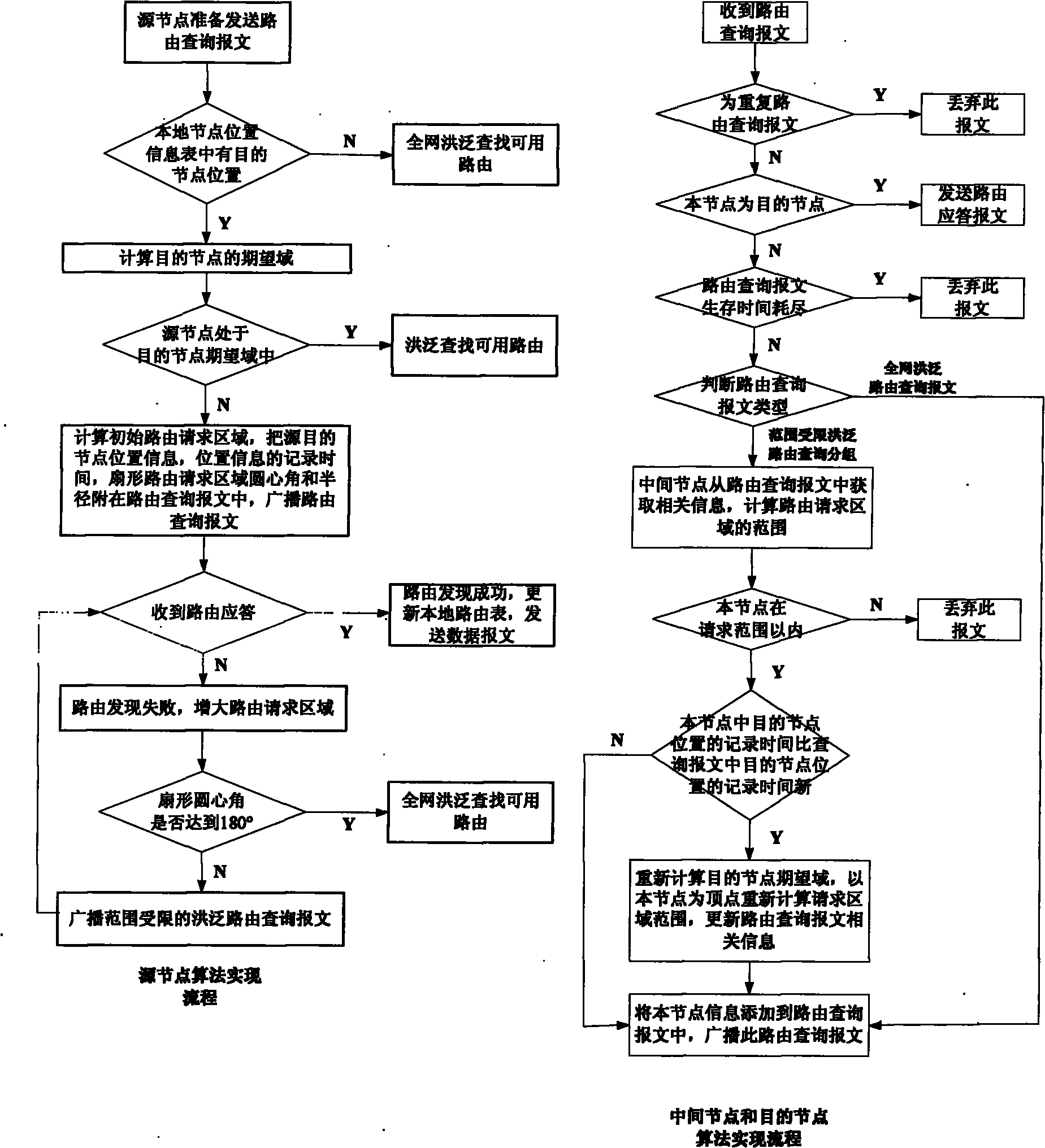
InactiveCN101888682AImprove discovery rateReduce control overheadHigh level techniquesWireless communicationBroadbandLocation aided routing
The invention relates to a method for realizing wireless personal area network routing protocols based on ultra-wide band positioning assist, comprising the following steps of: firstly acquiring the coordinate of each node in a network by utilizing an ultra-wide band positioning technique, then carrying out flooding routing discovery with a limited range by using the nodes based on positioning information, updating routing request areas by utilizing the middle node receiving a routing querying message according to the recording position information of the node, and then selecting fan-shaped areas with dynamically regulated ranges in the routing request areas. The simulated and analyzed results show that compared with LAR (Location-Aided Routing) protocols, after carrying out node positioning with low node energy consumption and calculation and updating on the routing request areas, the invention reduces the overheads of routing control messages, shortens the end-to-end average time delay of data messages, and obviously improves effects.
Owner:SOUTHEAST UNIV
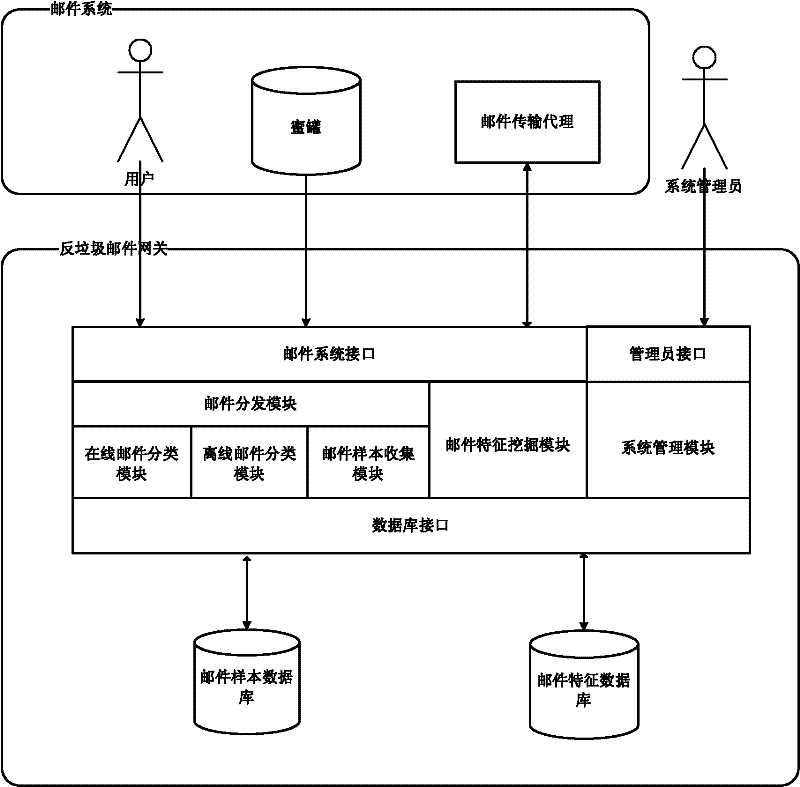
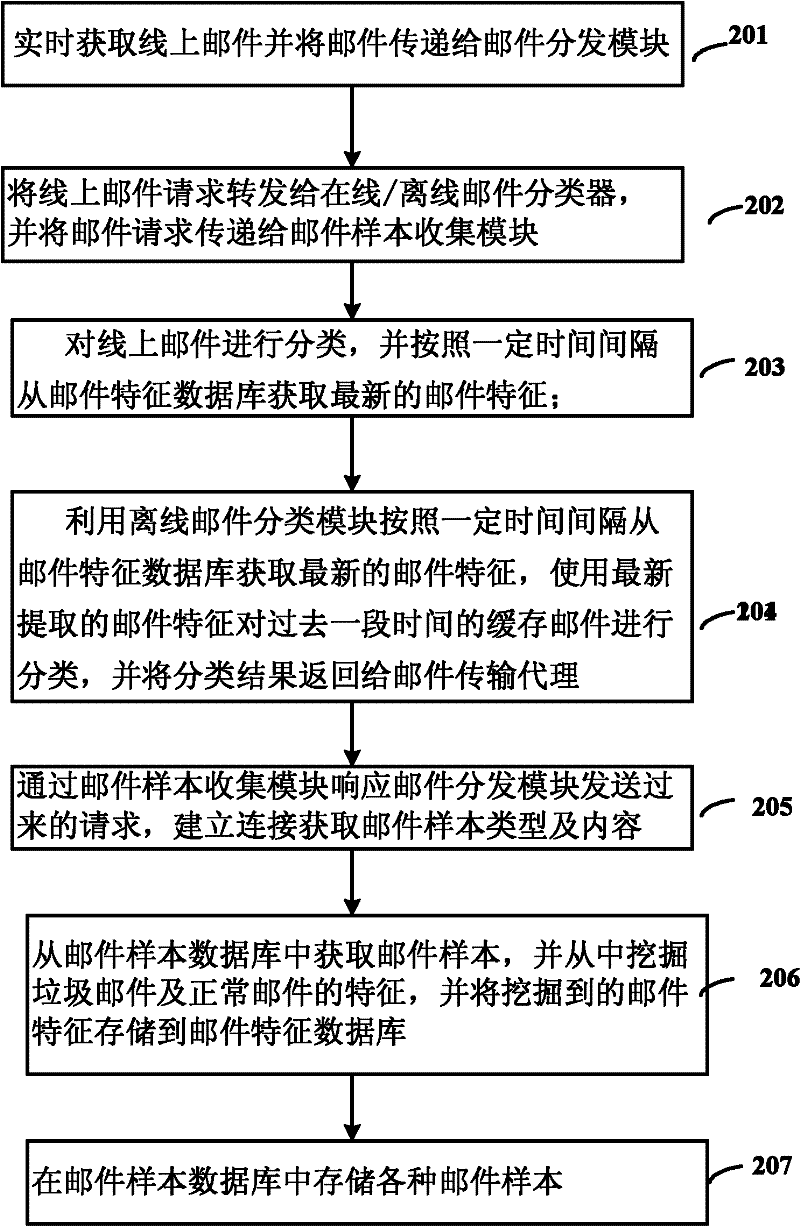
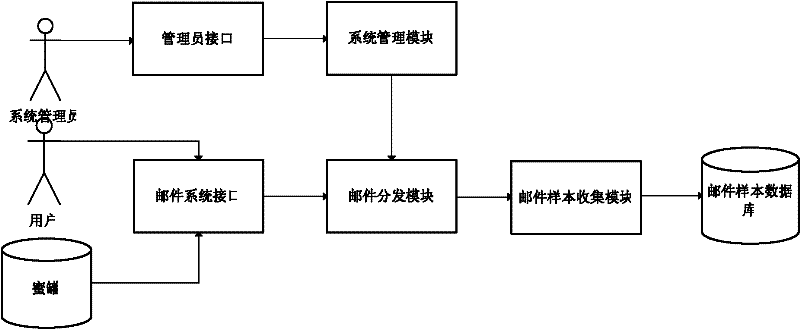
Anti-spam gateway system and method
ActiveCN102377690AReduce the probability of misjudgmentHigh miss rateData switching networksSpecial data processing applicationsData miningData library
The invention discloses an anti-spam gateway system and an anti-spam method. The system comprises a mail sample database for storing various mail samples, and a mail characteristic exploration module for acquiring the mail samples from the mail sample database, comparing the mail samples with all central points, and directly adding the samples into the central points if the similarity between the mail samples and all the central points is less than a certain threshold value, wherein each central point represents a type of samples; when the similarity between the mail samples and the central points is calculated, the mail samples and the central points are resolved into a plurality of parts of contents respectively; for each part, the similarities of the mail sample and the central point are compared; and the global similarity between the mail samples and the central points can be acquired by weighted combination of the similarities of the parts. By using the system and the method, the sample database and a characteristic database have better adaptability to burst spam types and the like; therefore, the leakage rate of spam is low, the instantaneity is high, the manual intervention is low and the system contractability is high.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
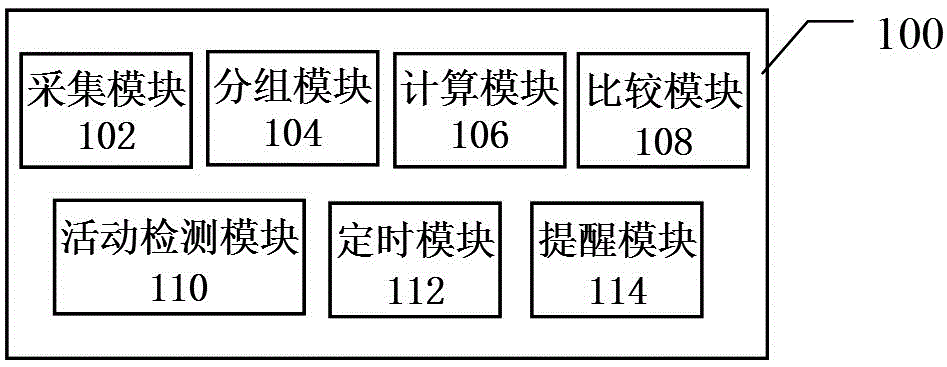
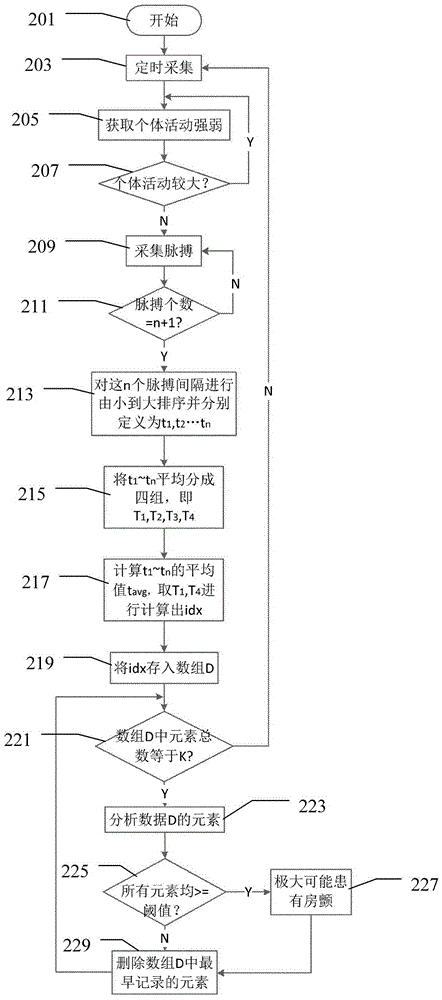
Atrial fibrillation detector and intelligent wearable device having same
ActiveCN105902265AImprove the detection rate of atrial fibrillationReduce misdiagnosis and misjudgment ratesDiagnostics using lightCatheterAtrial fibrillationPulse time
The invention discloses an atrial fibrillation detector comprising the following elements: an acquisition module used for collecting a pulse signal sequence and recording pulse time intervals; a grouping module used for ranking the recorded pulse time intervals from small to big, and dividing into groups of a preset number; a calculation module used for calculating a pulse time interval deviation value; a comparison module used for comparing repeatedly collected and calculated pulse time interval deviation value of the preset number with a preset threshold value, determining whether the calculated deviation value is bigger than or equal to the preset threshold value, thus determining whether atrial fibrillation exists or not. The atrial fibrillation detector and an intelligent wearable device having same can improve atrial fibrillation discovery rate, so people can self-operate under non-medical conditions, thus carrying out atrial fibrillation detection.
Owner:GUANGDONG TRANSTEK MEDICAL ELECTRONICS CO LTD
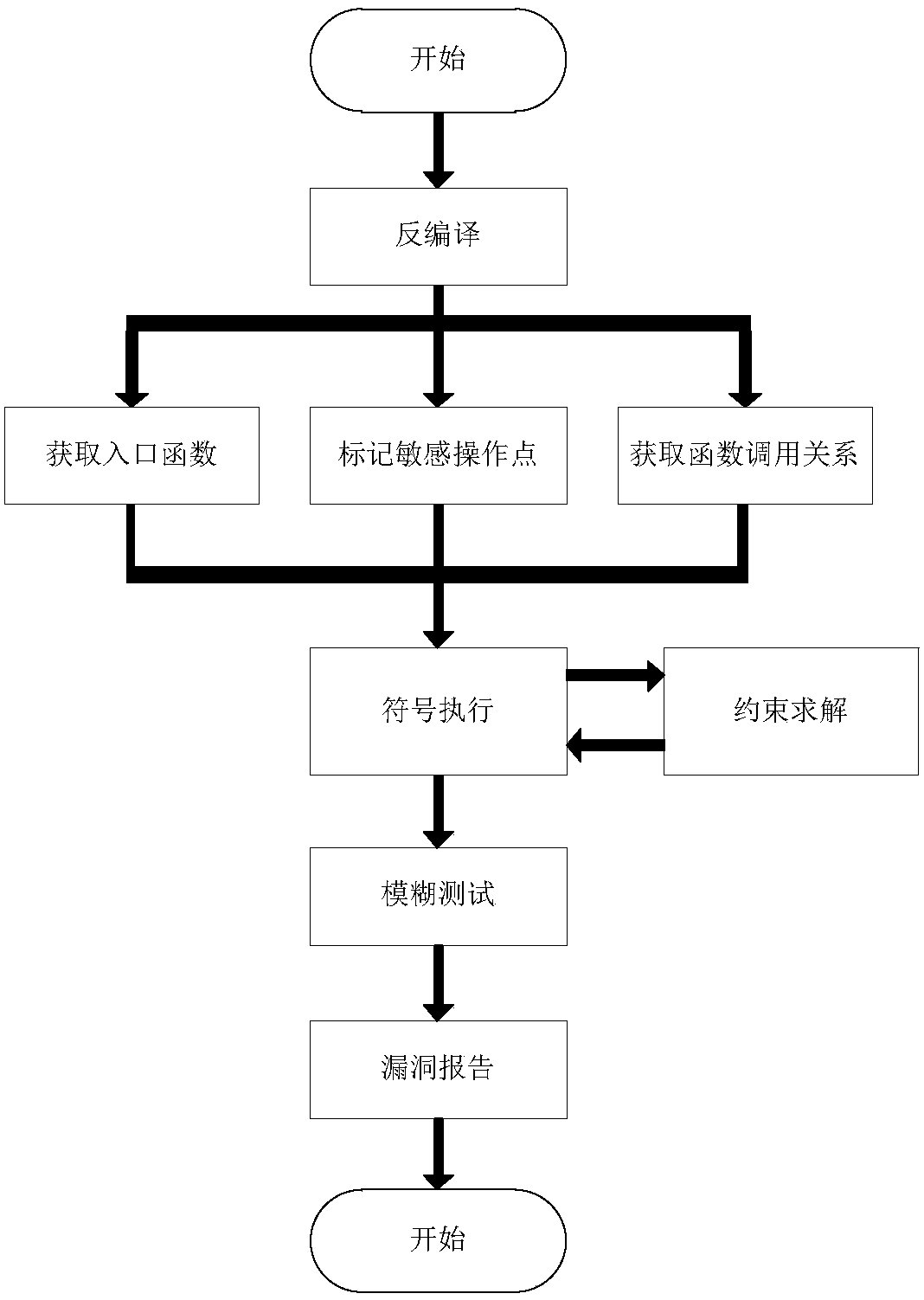
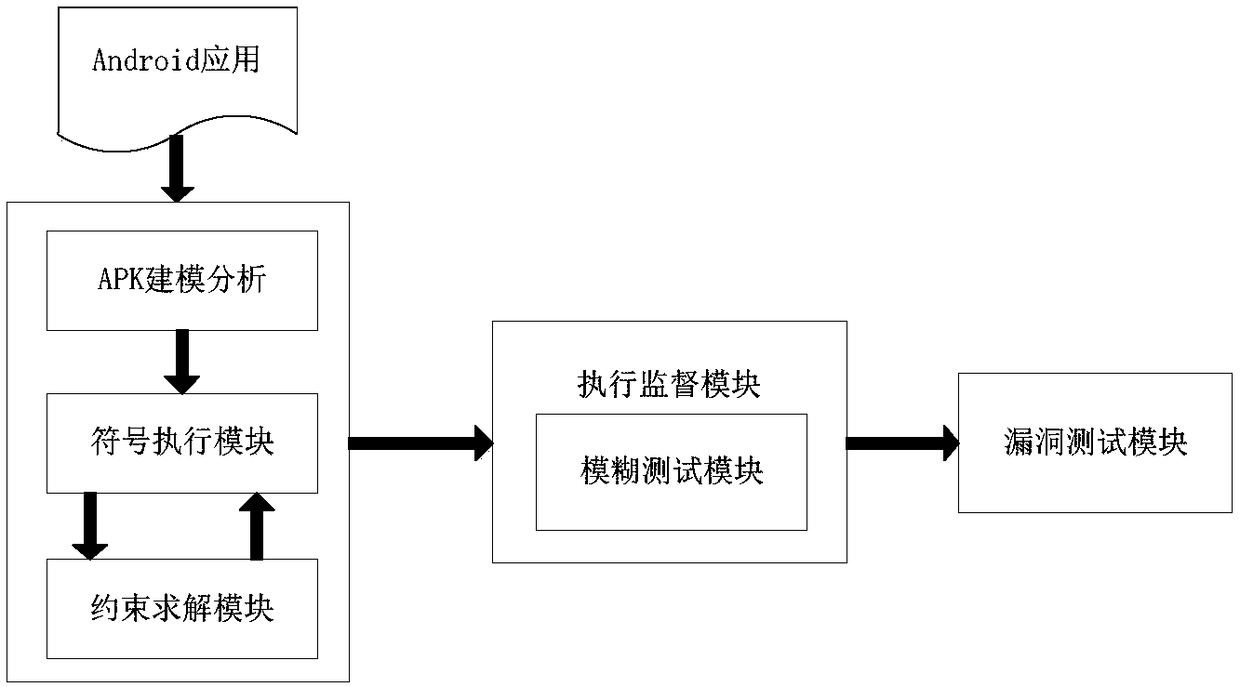
Android application-oriented intelligent fuzzy test method
ActiveCN108268371AAvoid full path coverage testsAccurate analysisSoftware testing/debuggingPlatform integrity maintainanceControl flowOperation point
The invention discloses an Android application-oriented intelligent fuzzy test method. The method comprises application reverse symbol execution and Android application fuzzy testing. Android vulnerability characteristics are used for performing modeling analysis on an Android application to obtain an Android application entry function, a sensitive operation point, control flow and function call information; the reverse symbol execution is performed by taking the sensitive operation point as an entry to obtain path constraint information; the path constraint information is subjected to constraint solving to obtain a path test case triggering a vulnerability; the generated path test case is used for performing fuzzy testing on the Android application to monitor a program running state; andthe program running information is analyzed to generate a related vulnerability report. The test case triggering the vulnerability can be generated, so that the path explosion is avoided and the fuzzytesting under the guidance of the method is more targeted. Compared with a conventional fuzzy testing method, the method solves the problem of fuzzy testing blindness and improves the fuzzy testing efficiency.
Owner:NANJING UNIV OF SCI & TECH
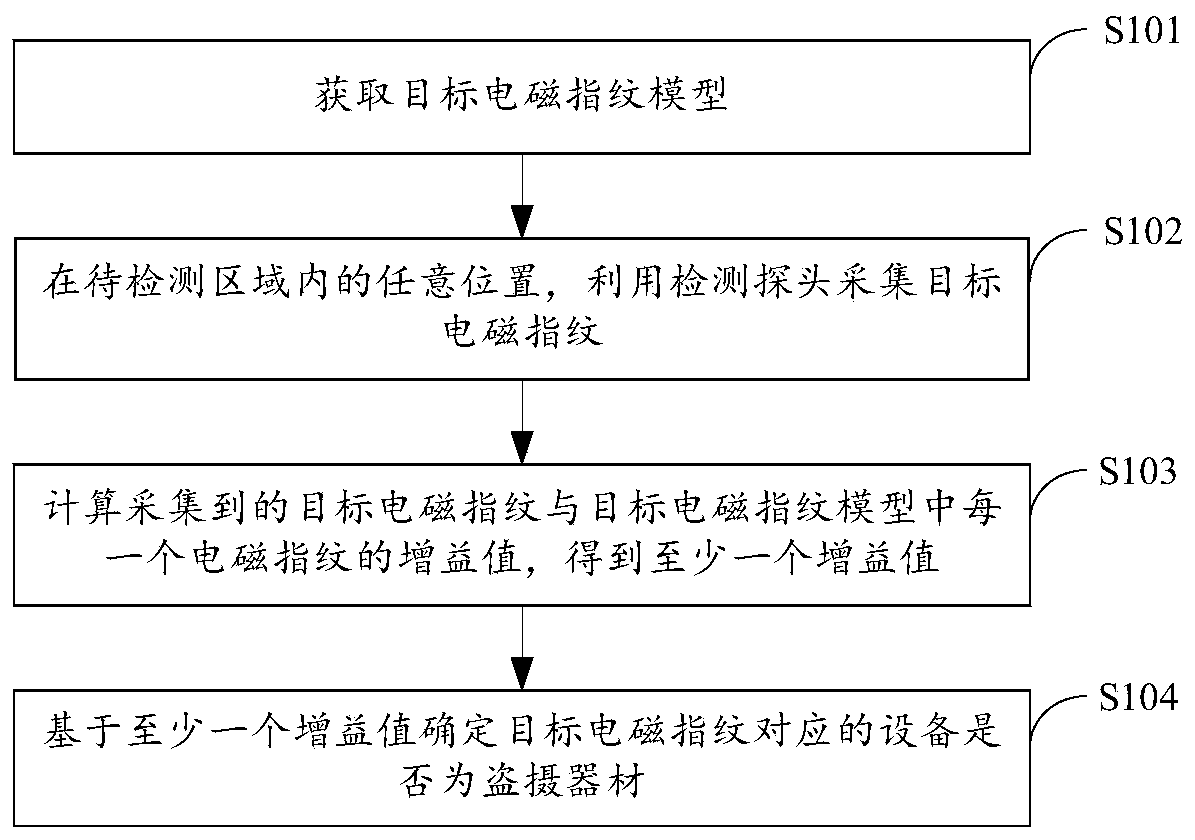
Method and device for detecting robbery equipment based on electromagnetic leakage
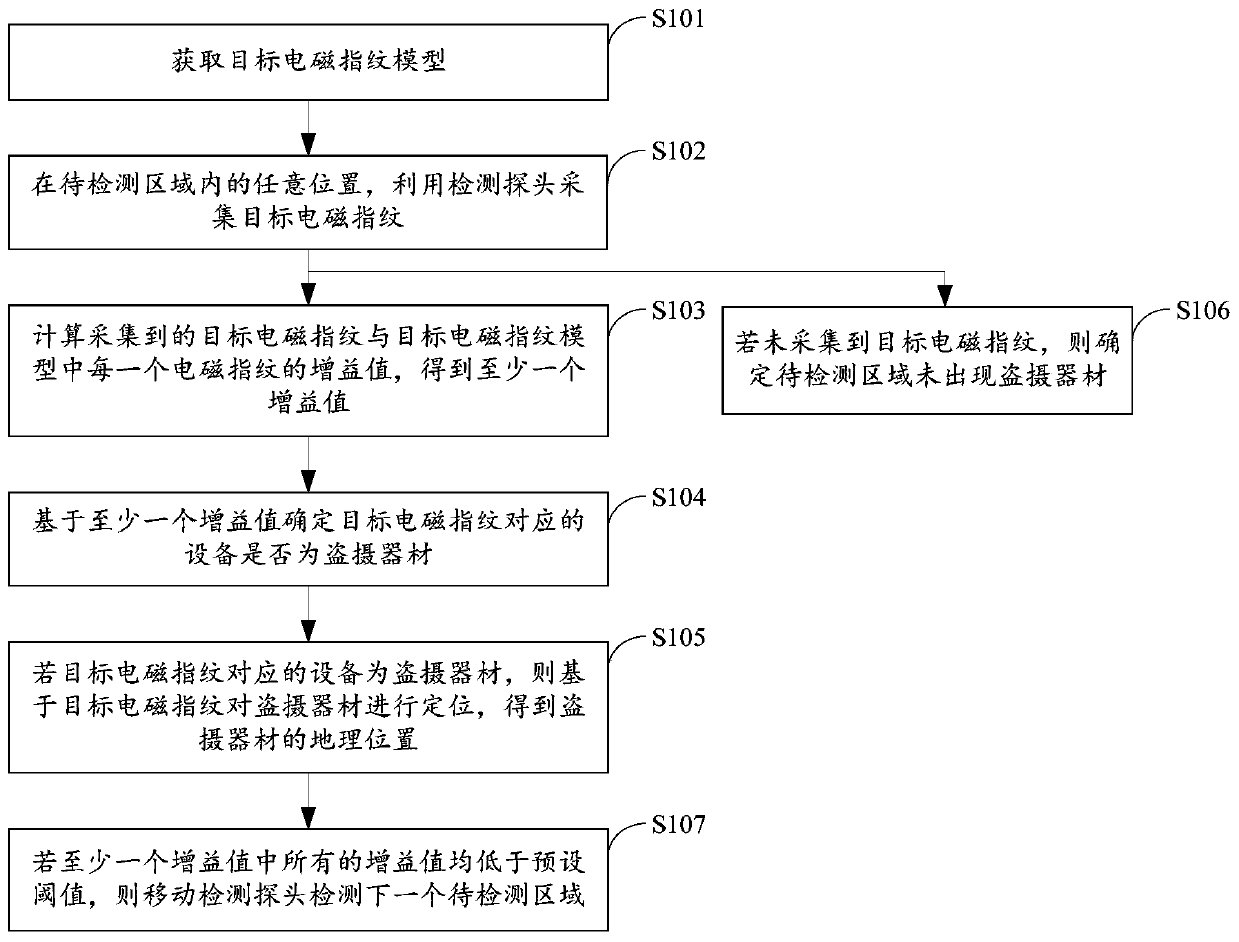
ActiveCN110941020AAutomate discoveryImprove discovery ratePosition fixationDetection using electromagnetic wavesElectrical and Electronics engineeringReal-time computing
The invention, which relates to the technical field of the electronic product, provides an electromagnetic-leakage-based method and device for detecting a stealing-shooting device, comprising: firstly, obtaining a target electromagnetic fingerprint model; acquiring a target electromagnetic fingerprint at any position in the to-be-detected area by using a detection probe; calculating gain values ofthe collected target electromagnetic fingerprint and each electromagnetic fingerprint in the target electromagnetic fingerprint model to obtain at least one gain value; and finally determining whether the device corresponding to the target electromagnetic fingerprint is a stealing device based on the at least one gain value. The target electromagnetic fingerprint model can avoid the interferenceof the external environment, and improves the detection accuracy. Automatic collection of electromagnetic fingerprints can be achieved through the detection probe. Due to the fact that electromagneticleakage protection is difficult to achieve in the use scene of the stealing and shooting equipment, the discovery rate of the stealing and shooting equipment can be increased.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Artificial intelligence-based bad case discovery method and apparatus, and storage medium
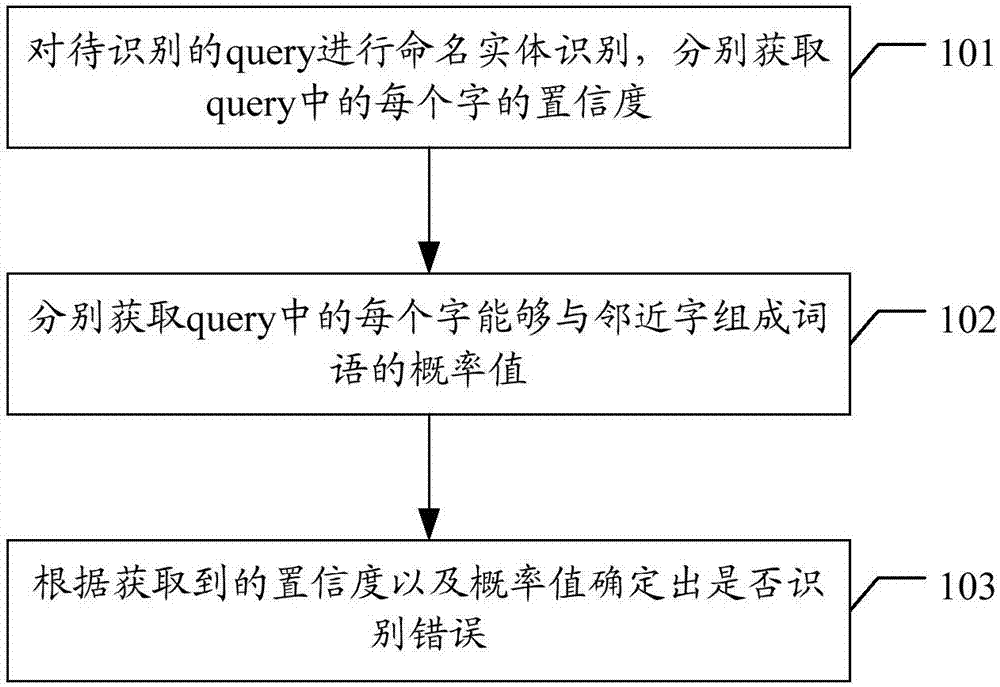
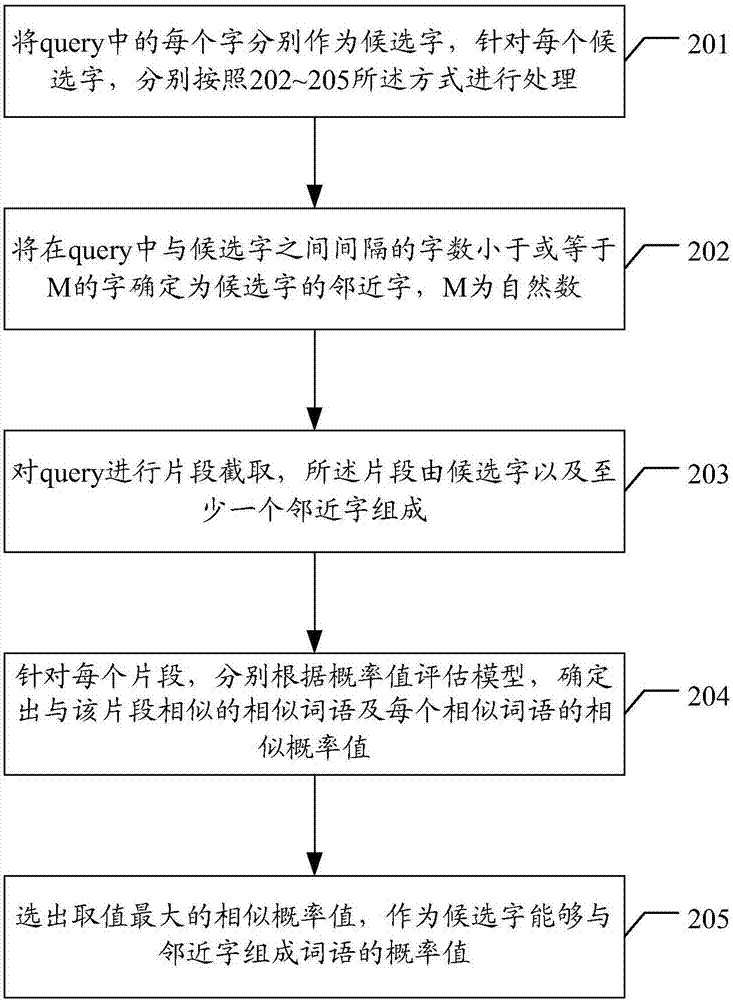
ActiveCN107038157AAvoid undetected situationsImprove discovery rateGeneral purpose stored program computerCharacter and pattern recognitionNamed-entity recognitionArtificial general intelligence
The invention discloses an artificial intelligence-based bad case discovery method and apparatus, and a storage medium. The method comprises the steps of performing named entity recognition on a to-be-recognized query to obtain the confidence degree of each word in the query; obtaining a probability value of forming terms by each word in the query and adjacent words; and determining whether a bad case exists or not according to the obtained confidence degrees and probability values. By applying the scheme, the labor cost can be reduced, the processing efficiency can be improved, the bad case discovery rate can be increased, and the like.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Target extraction method based on ground surveillance radar system
ActiveCN109188430AImprove object extraction accuracyImprove stability and reliabilityRadio wave reradiation/reflectionComputer visionSecondary surveillance radar
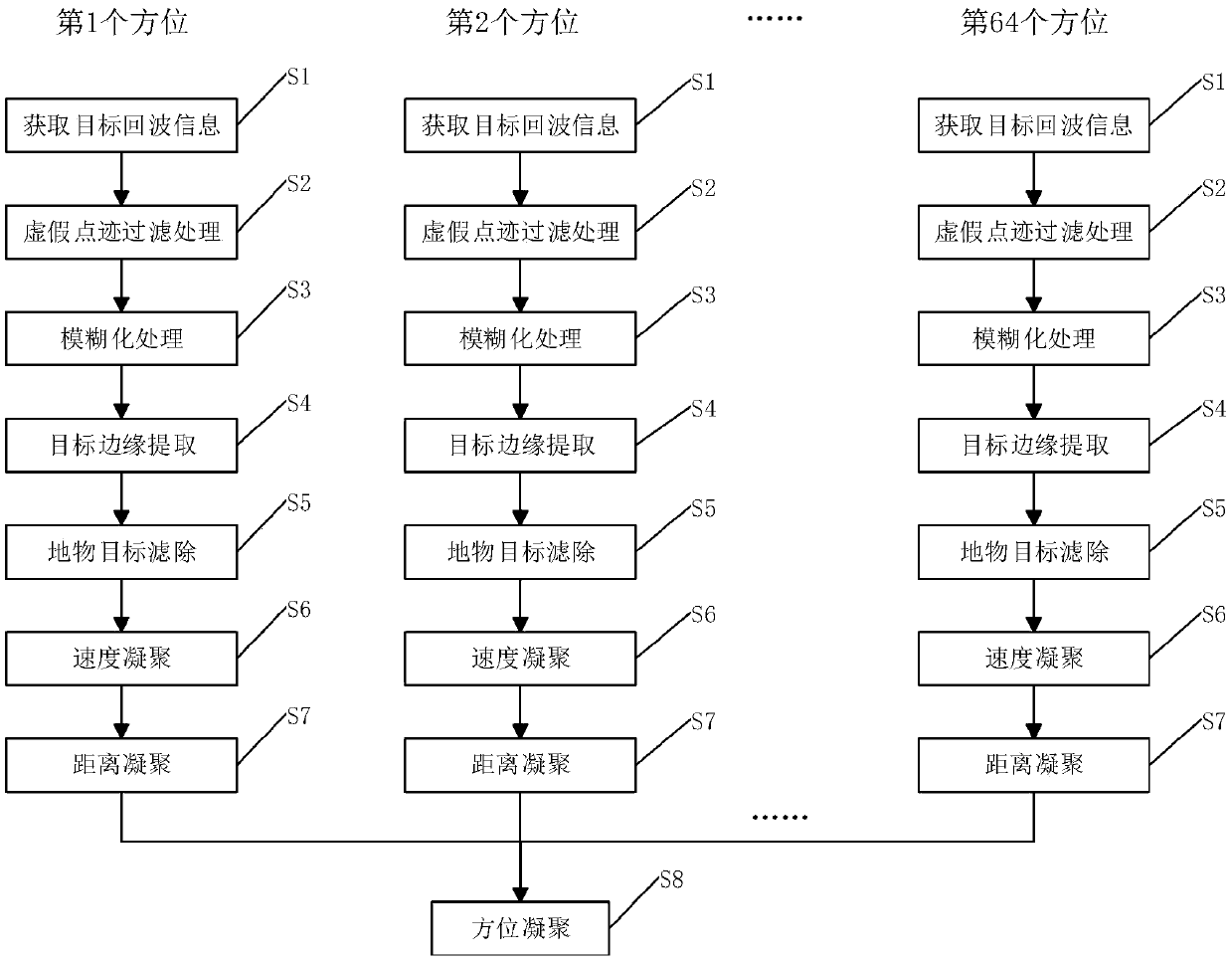
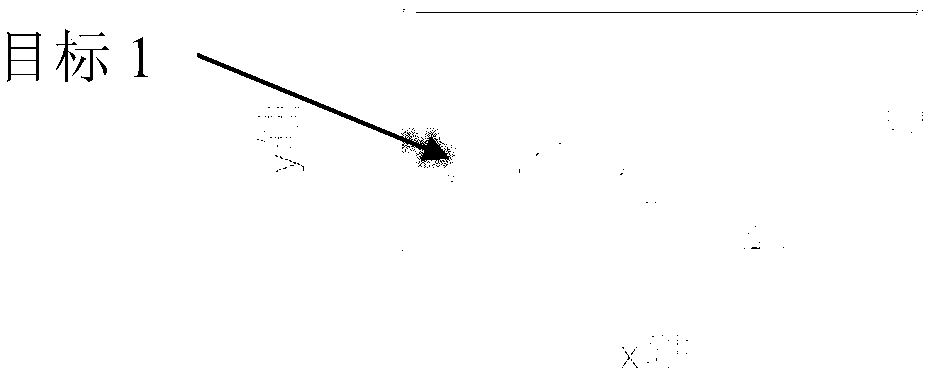
The invention discloses a target extraction method based on a ground surveillance radar system. The method comprises the following steps of: obtaining target echo information processed by the front end of a radar; performing a false plot filtering process on the target echo information; performing a fuzzification process on the target echo information after the false plot filtering process; forming a two-dimensional image on the target echo information after the fuzzification process, and performing target edge extraction on the two-dimensional image; performing ground object target filteringprocess on the obtained target echo information which belongs to the same target after the edge extraction; and obtaining the target echo information which belongs to the same target after the groundobject target filtering process. According to the target extraction method based on the ground surveillance radar system, the target extraction integrity is improved, the target extraction precision is improved, and the risk that the same target is split into multiple targets when performing target extraction is reduced.
Owner:ANHUI SUN CREATE ELECTRONICS
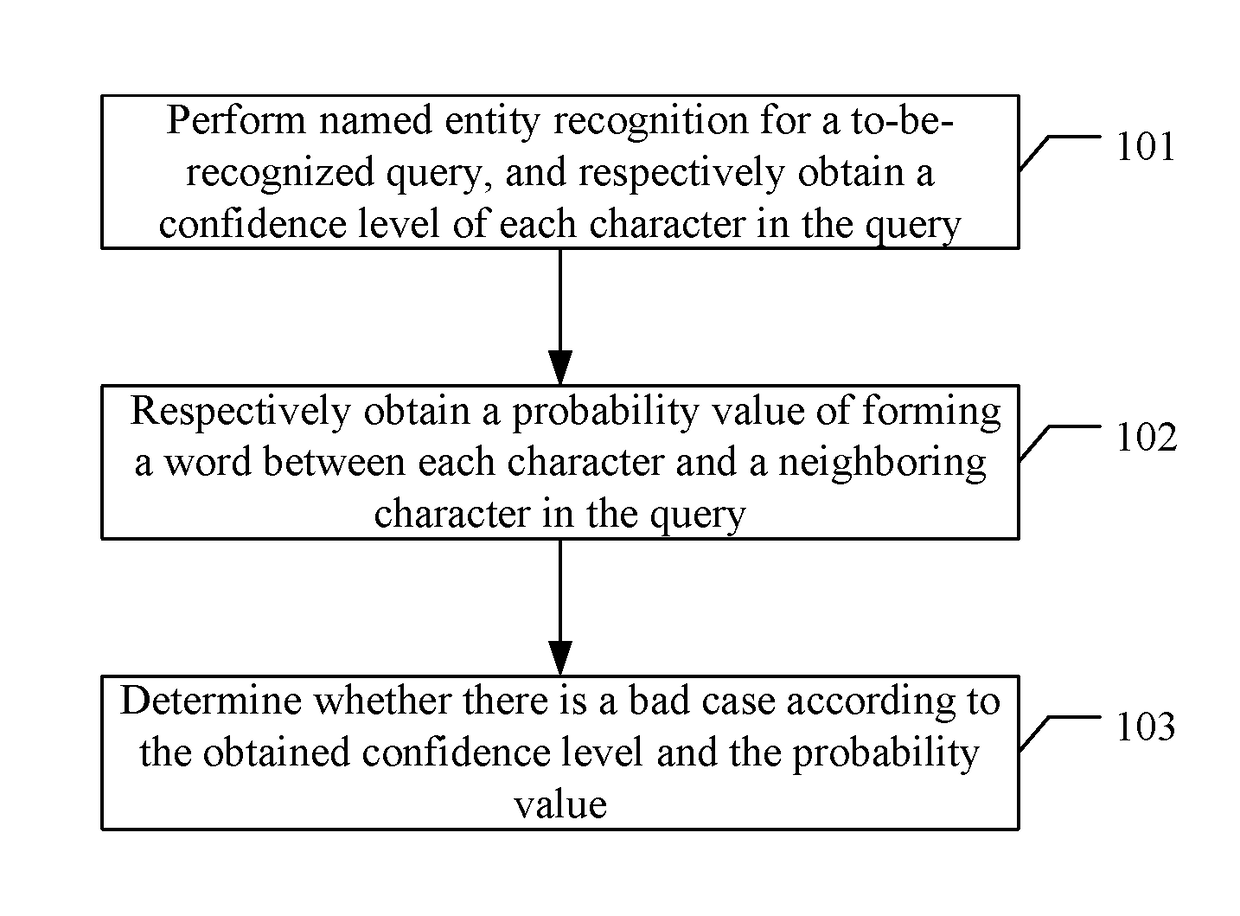
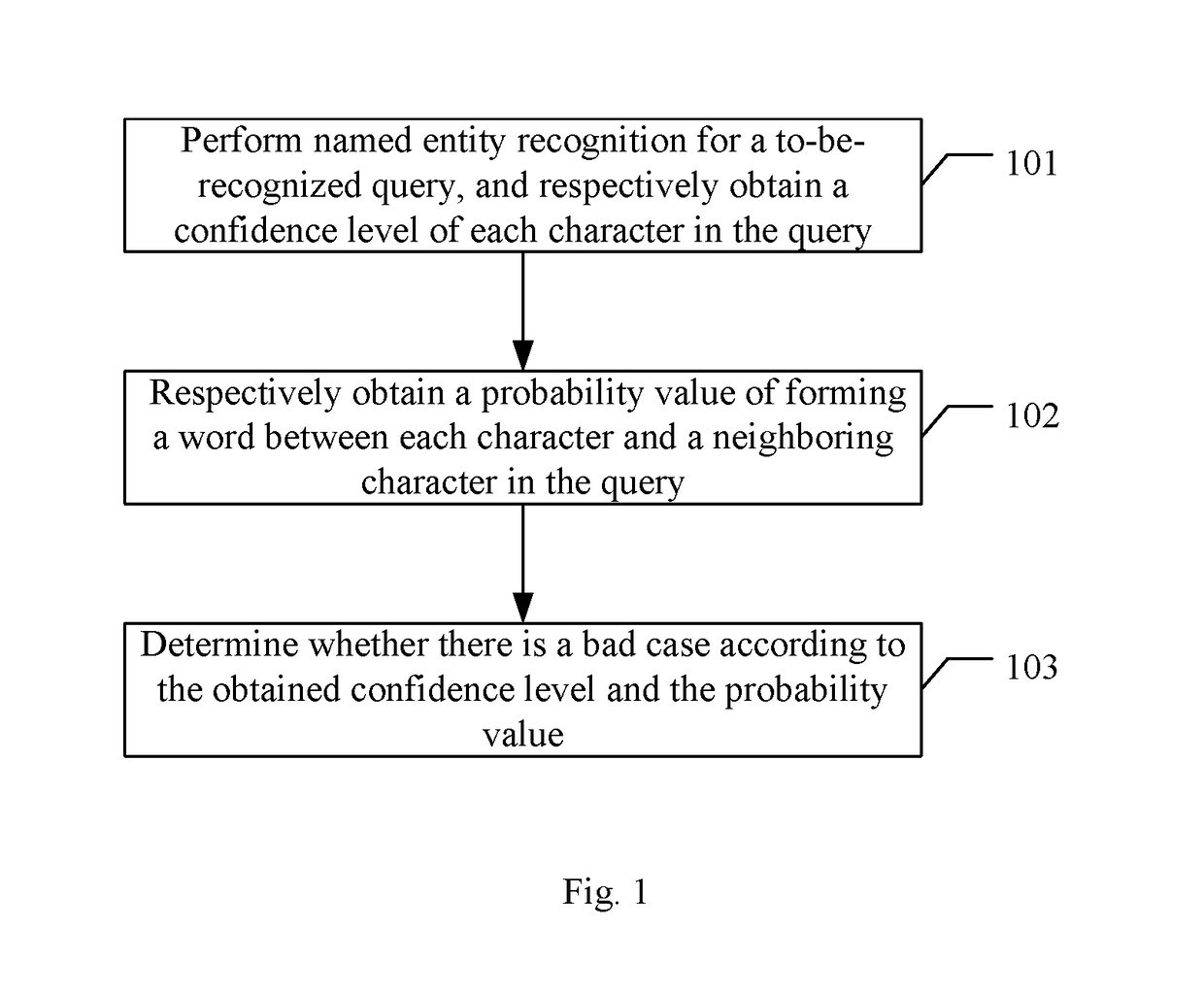
Method and apparatus of discovering bad case based on artificial intelligence, device and storage medium
ActiveUS20180322370A1Save man power costImprove processing efficiencyGeneral purpose stored program computerCharacter and pattern recognitionNamed-entity recognitionData mining
The present disclosure provides a method and apparatus of discovering a bad case based on artificial intelligence, a device and a storage medium, wherein the method comprises: performing named entity recognition for a to-be-recognized query, and respectively obtaining a confidence level of each character in the query; respectively obtaining a probability value of each character of forming a word with a neighboring character in the query; determining whether there is a bad case according to the confidence level and the probability value. The solution of the present disclosure may be applied to save man power costs, and improve the processing efficiency and enhance a discovery rate of bad cases.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method for discovering neighbor nodes in wireless ad hoc network of switchable beam antenna
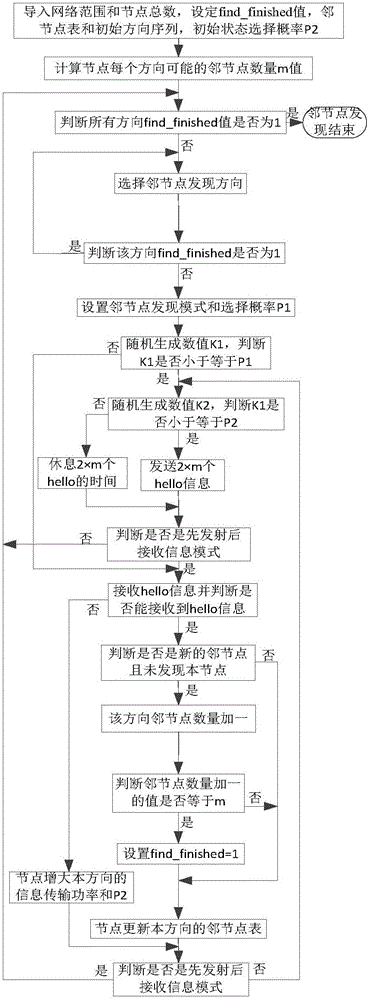
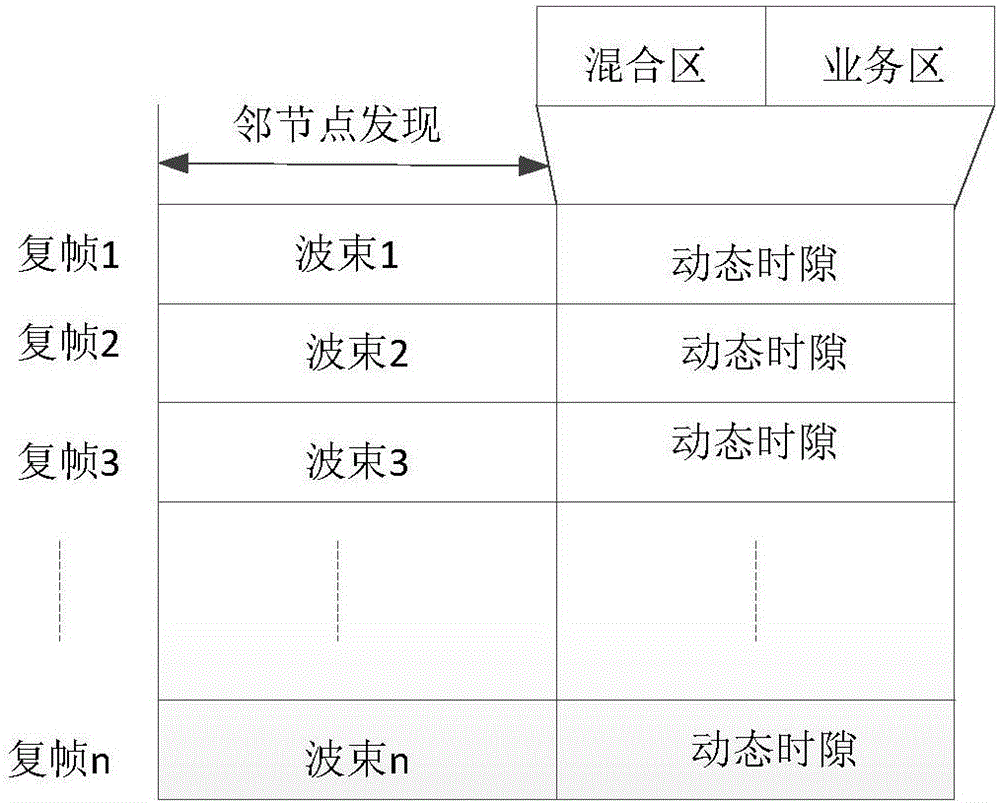
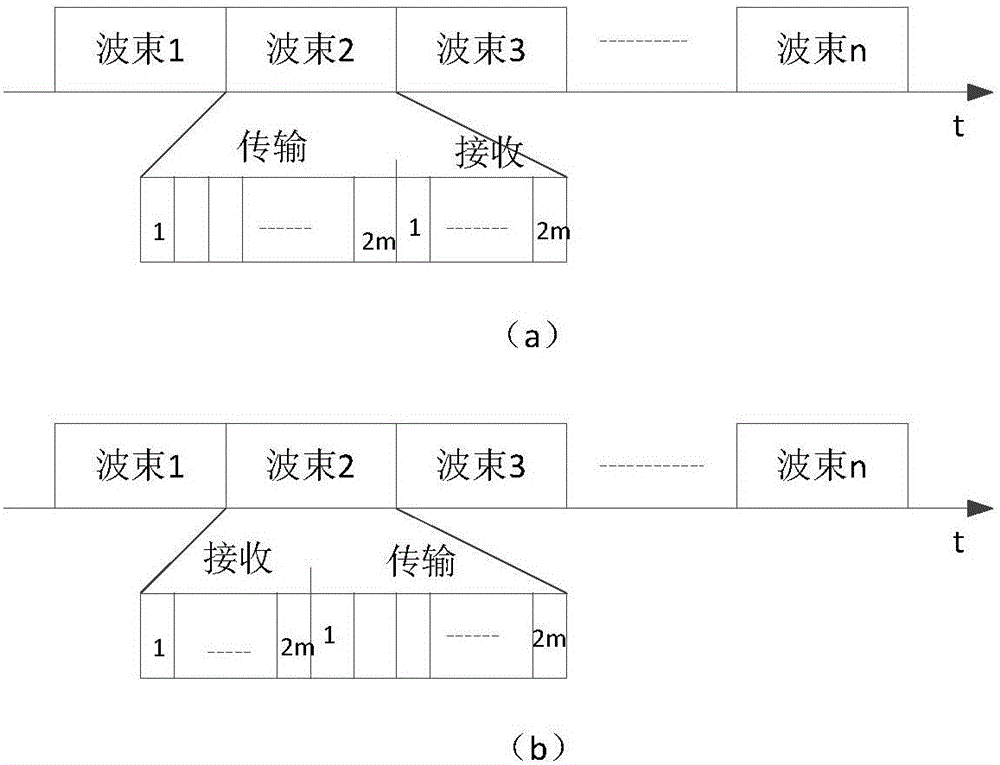
ActiveCN105873007AReduce time to discoveryImprove discovery efficiencyPower managementSpatial transmit diversityInformation transmissionWireless ad hoc network
The invention provides a method for discovering neighbor nodes in a wireless ad hoc network of a switchable beam antenna, and aims to solve the problem of low neighbor node discovery efficiency in the prior art. The method comprises the following steps: calculating a quantity of probable neighbor nodes in different directions of a certain node; judging whether finding is finished or not in different directions of the certain node; selecting discovery directions of the neighbor nodes of the certain node; judging whether discovery of the neighbor nodes in the directions is finished or not; selecting a mode for the certain node to execute neighbor node discovery; if a first mode is selected, transmitting information firstly and receiving information secondly by the certain node; if a second mode is selected, receiving information firstly and transmitting information secondly by the certain node; and judging the neighbor node information by the certain node according to the received information, and preparing for next neighbor node discovery. According to the method, next execution of the neighbor node discovery in the different directions is adjusted according to the information of the neighbor nodes discovered by the certain node in the different directions; and meanwhile, direction change of the neighbor node discovery is driven, and the information transmission power of the neighbor node discovery is adjusted according to events. Thus, the neighbor node discovery time and the informational conflict probability are reduced.
Owner:XIDIAN UNIV
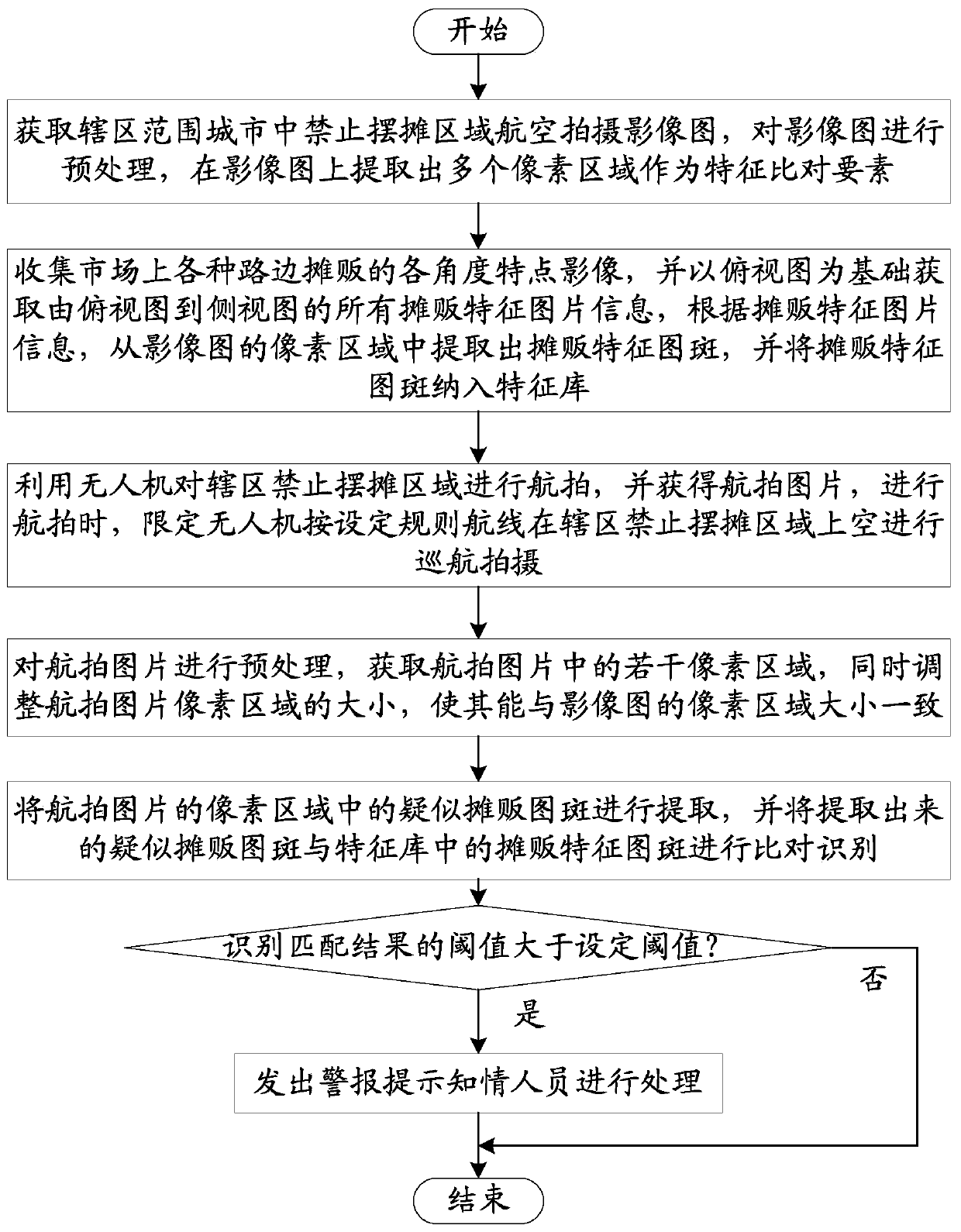
Unmanned-aerial-vehicle-based automatic identification and early warning method for vendors in no-peddler area
The invention provides an unmanned-aerial-vehicle-based automatic identification and early warning method for vendors in a no-peddler area. The unmanned-aerial-vehicle-based automatic identification and early warning method comprises the following steps: obtaining an aerial shooting image of the no-peddler area in a city in a jurisdiction range, and extracting a plurality of pixel areas from the image as feature comparison elements; collecting feature images of various roadside vendors in the market at various angles, acquiring feature image information of a plurality of vendors, and extracting vendor feature image spots from pixel areas of the image images according to the feature image information of the vendor, wherein the unmanned aerial vehicle is used for aerial photography of the jurisdiction no-peddler area to obtain an aerial photography picture; obtaining a plurality of pixel areas in the aerial image; and comparing and identifying suspected vendor image spots in the pixel region of the aerial photo with vendor feature image spots in a feature library, and when a threshold value of an identification matching result is greater than a set threshold value, giving an alarm. Through an artificial intelligence mode, the vendors in the no-peddler area are rapidly positioned, and the pressure on city management is reduced.
Owner:HENGFENG INFORMATION TECH CO LTD
Target clustering method based on ground surveillance radar system
ActiveCN109100697AHigh precisionReduce the risk of merging into the same targetRadio wave reradiation/reflectionSecondary surveillance radarRadar systems
The invention discloses a target clustering method based on a ground surveillance radar system. The method comprises the following steps of acquiring target echo information after radar front-end processing; carrying out false plot filter processing on the target echo information in order to obtain filtered target echo information; carrying out speed clustering on the filtered target echo information in order to obtain target echo information after speed clustering on a distance library; carrying out distance clustering on the target echo information after speed clustering on the distance library in order to obtain target parameters and target echo information after distance clustering at the azimuth; and carrying out azimuth clustering on the target echo information after distance clustering at the azimuth in order to obtain target parameters and target echo information which belong to the same target after azimuth clustering. According to the method, the risk that the targets at different speeds are merged into the same target is reduced, the precision of target clustering is improved, and a reliable foundation is provided for follow-up track processing.
Owner:ANHUI SUN CREATE ELECTRONICS
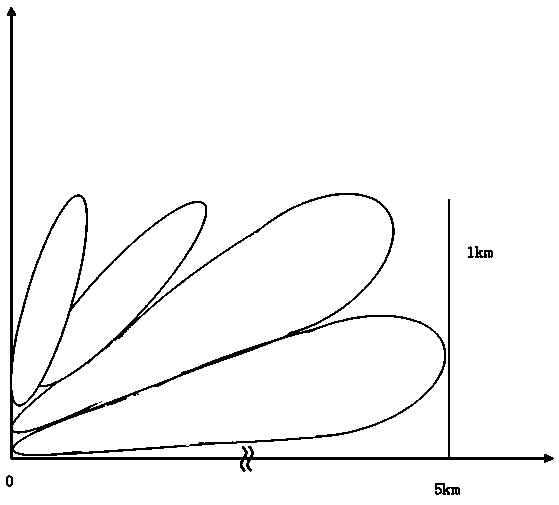
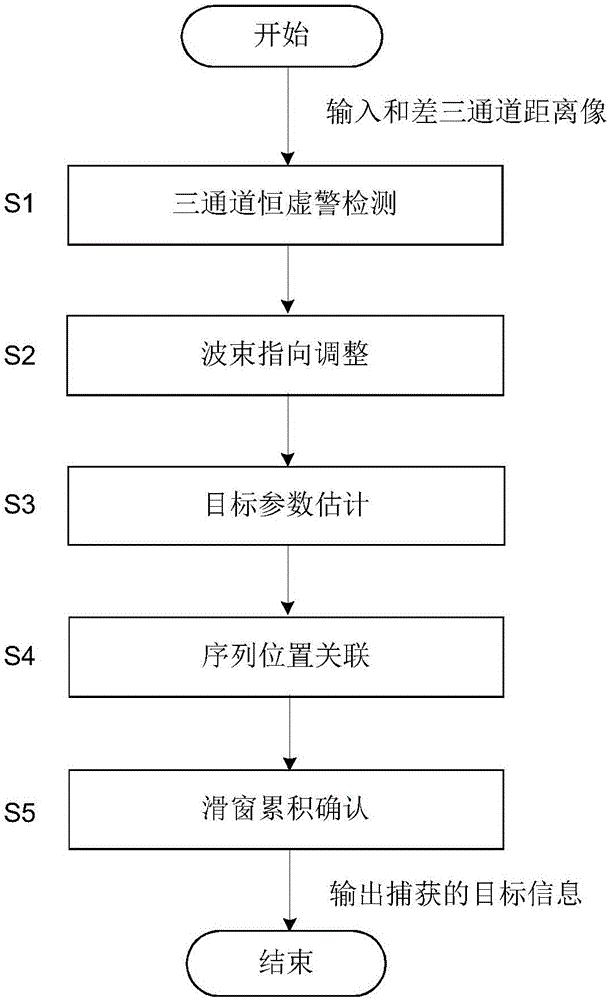
Air target quick capturing method of monopulse radar
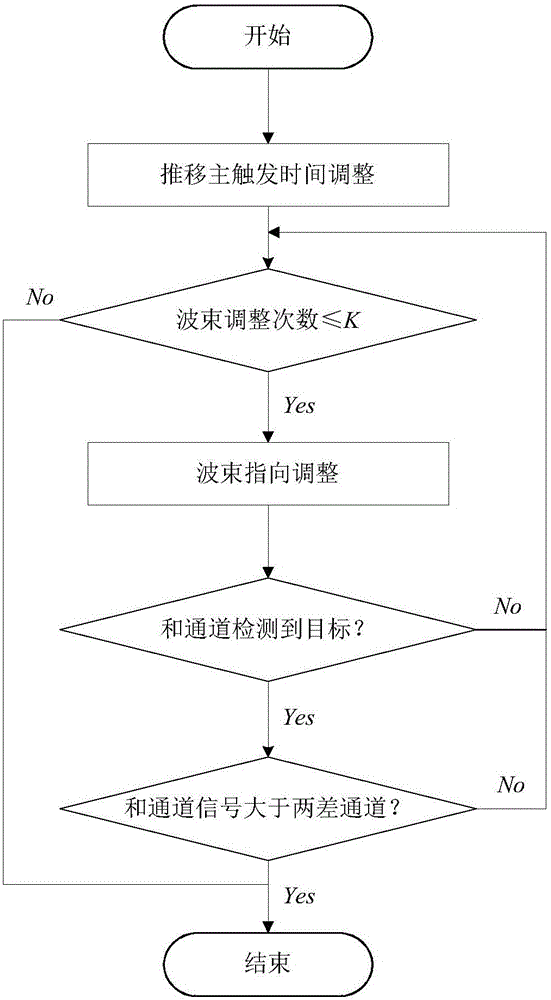
ActiveCN105842688AIncreased beam widthImprove discovery rateRadio wave reradiation/reflectionSignal-to-noise ratio (imaging)Target signal
The invention provides an air target quick capturing method of monopulse radar. By means of the method, a target searching and capturing capability of the radar can be remarkably improved on conditions of low signal-to-noise ratio and high-speed target movement, thereby realizing quick target capturing. The air target quick capturing method is realized through a technical solution which is characterized in that DSP embedded software is composed of a three-channel constant false-alarm rate detecting module, a wave beam direction adjusting module, a target parameter estimating module, a sequence position correlation module and a slide window accumulation confirmation module, wherein the method comprises the steps of inputting summation, direction difference and pitch difference three-channel distance images, performing constant false-alarm rate determination on the three-channel distance images, thereby obtaining a target signal with a highest amplitude; then changing elapse main triggering time, and adjusting the wave beam according to a designed strategy; performing target parameter estimation by means of a phase and a difference type monopulse measured angle; determining a fact that target correlation successes or fails by means of sequence position correlation; performing sliding window type accumulation on the correlation result, determining the accumulation result, and outputting the target information which is successively captured through the monopulse radar.
Owner:10TH RES INST OF CETC
Two-stage threshold constant false alarm detection algorithm under strong ground clutter
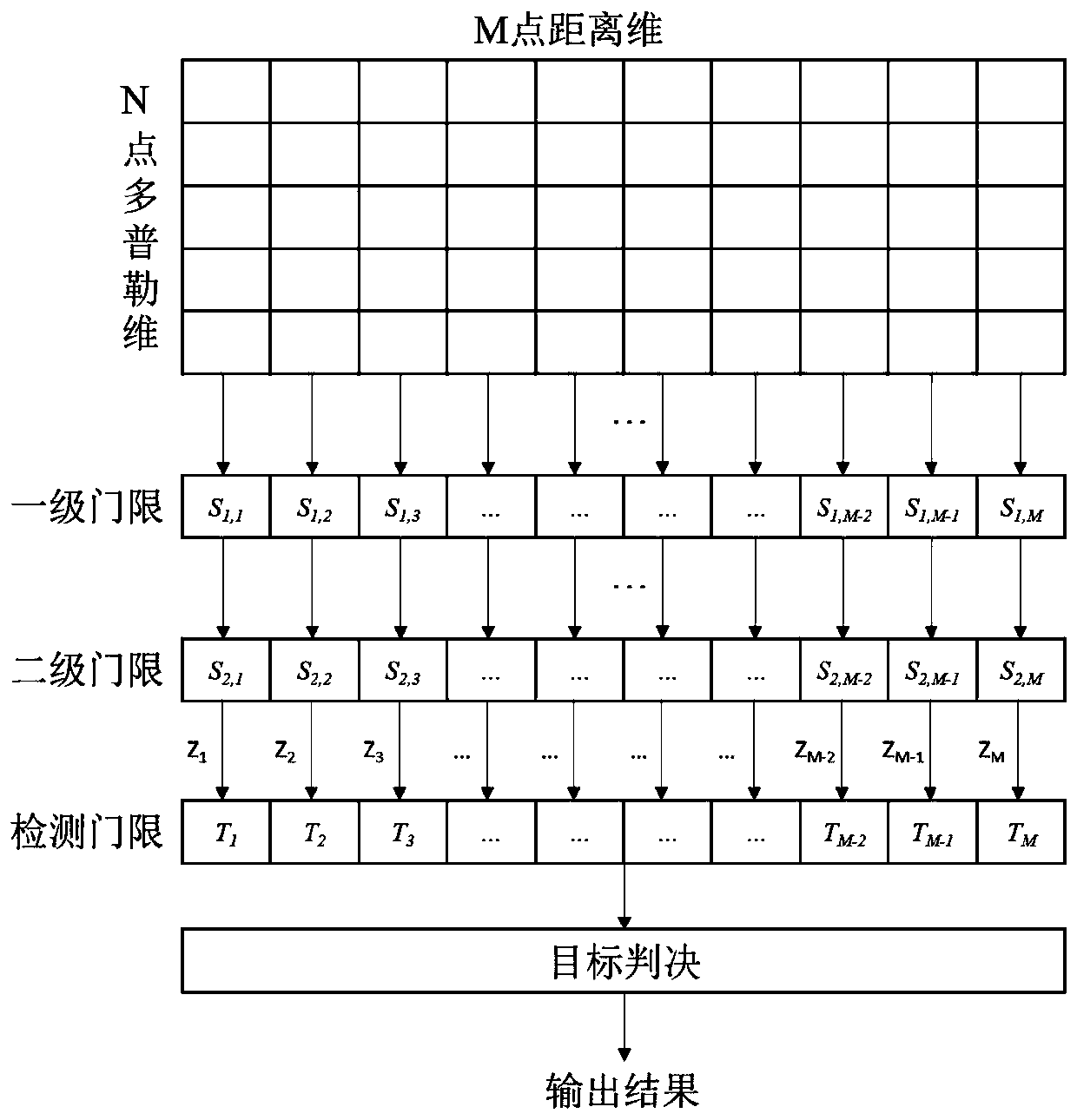
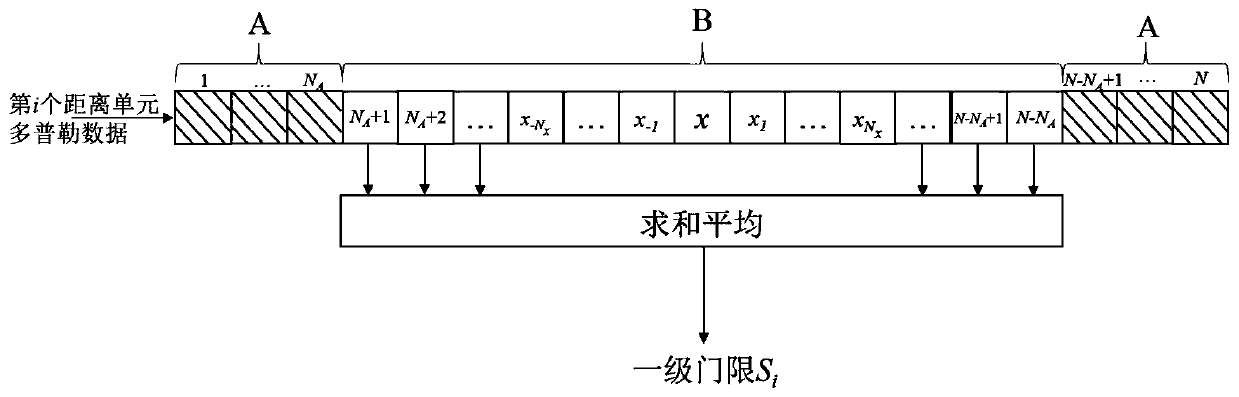
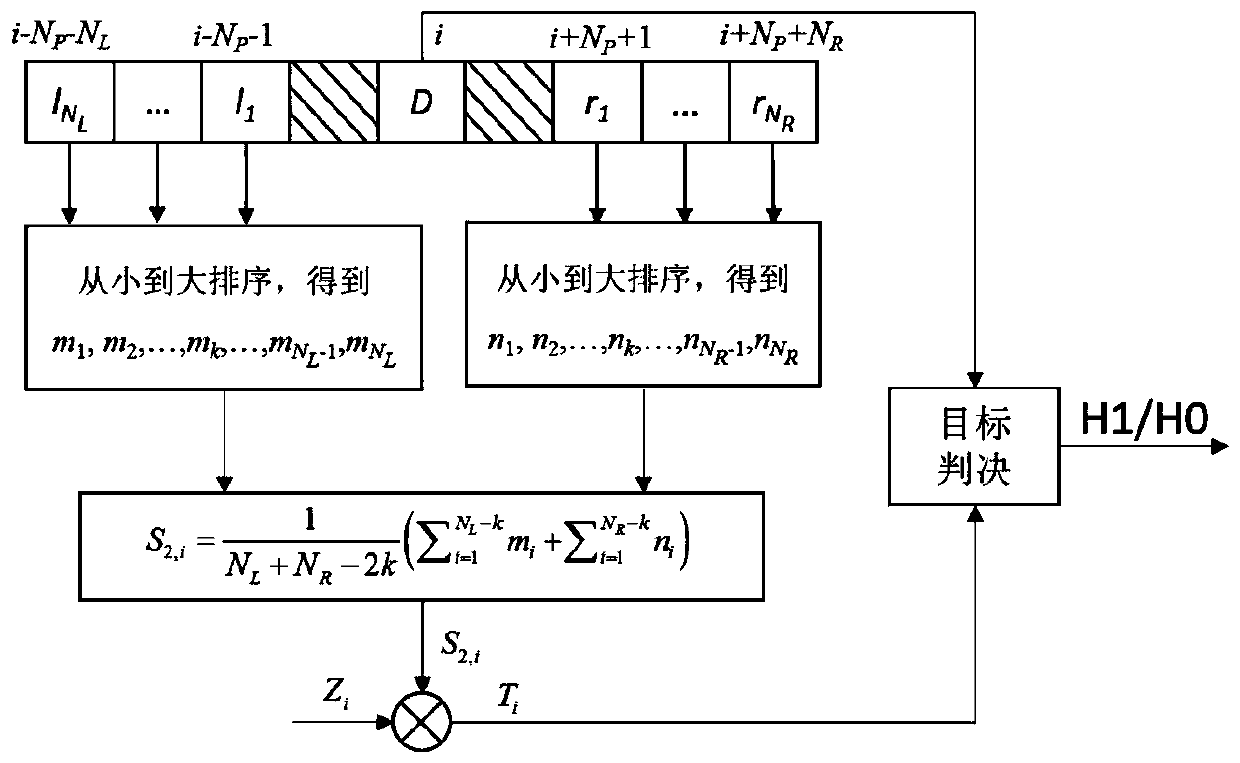
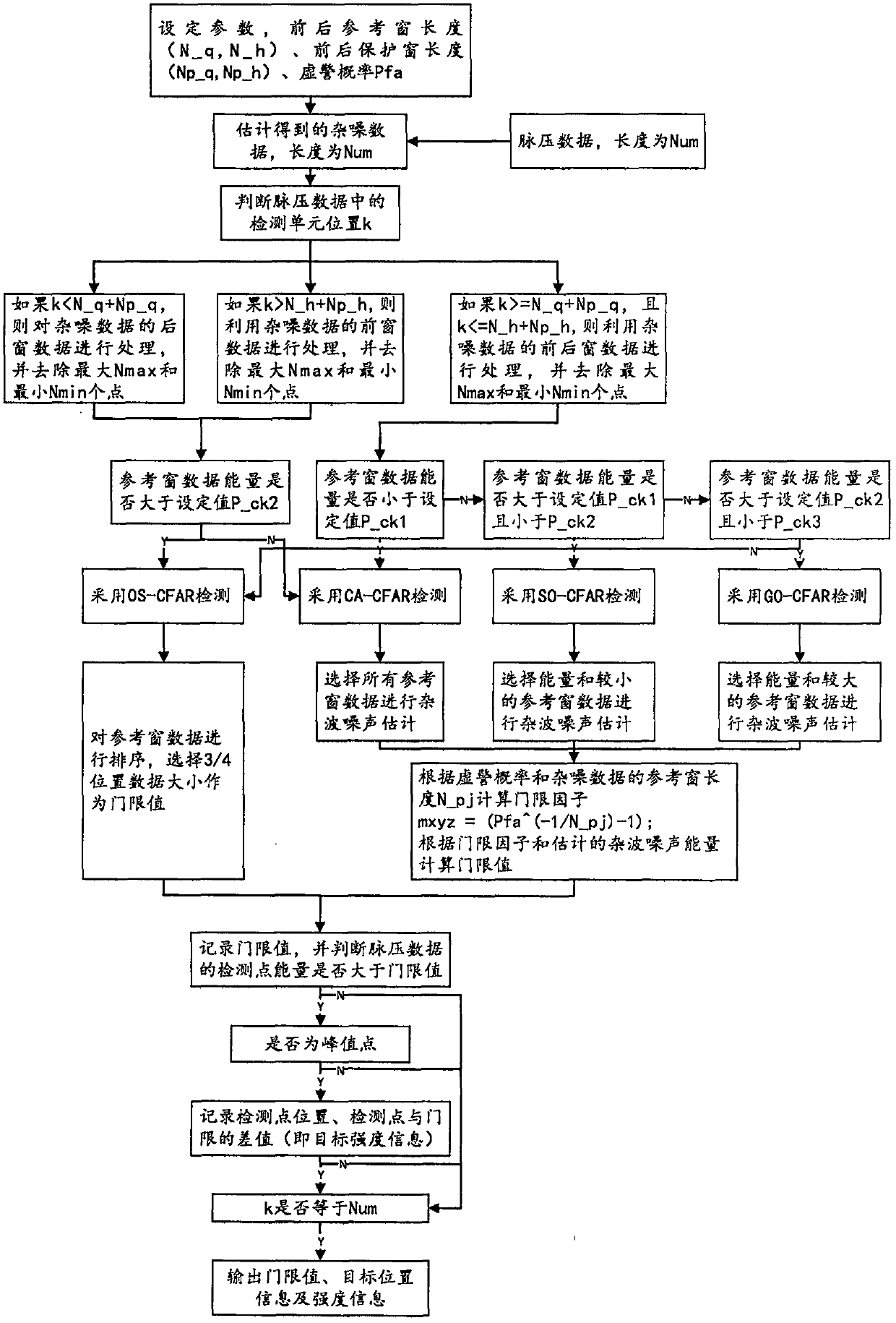
PendingCN111157953AMeet real-time requirementsImprove discovery rateWave based measurement systemsRadar systemsFalse alarm
The invention discloses a two-stage threshold constant false alarm detection algorithm under strong ground clutters. Radar receiving echoes are subjected to down-conversion, decimation filtering, pulse compression and phase-coherent accumulation to form distance-Doppler two-dimensional data; and a two-stage threshold deletion average CFAR detection algorithm is adopted to determine the position ofthe target in the two-dimensional data, namely distance and Doppler information. Aiming at the problems of the ground reconnaissance radar CFAR detection technology, a two-stage threshold deletion average CFAR detection algorithm is designed, the discovery probability is improved, the false alarm probability is reduced, the calculation time is shortened, and the real-time requirement of a radar system is met.
Owner:NANJING UNIV OF SCI & TECH
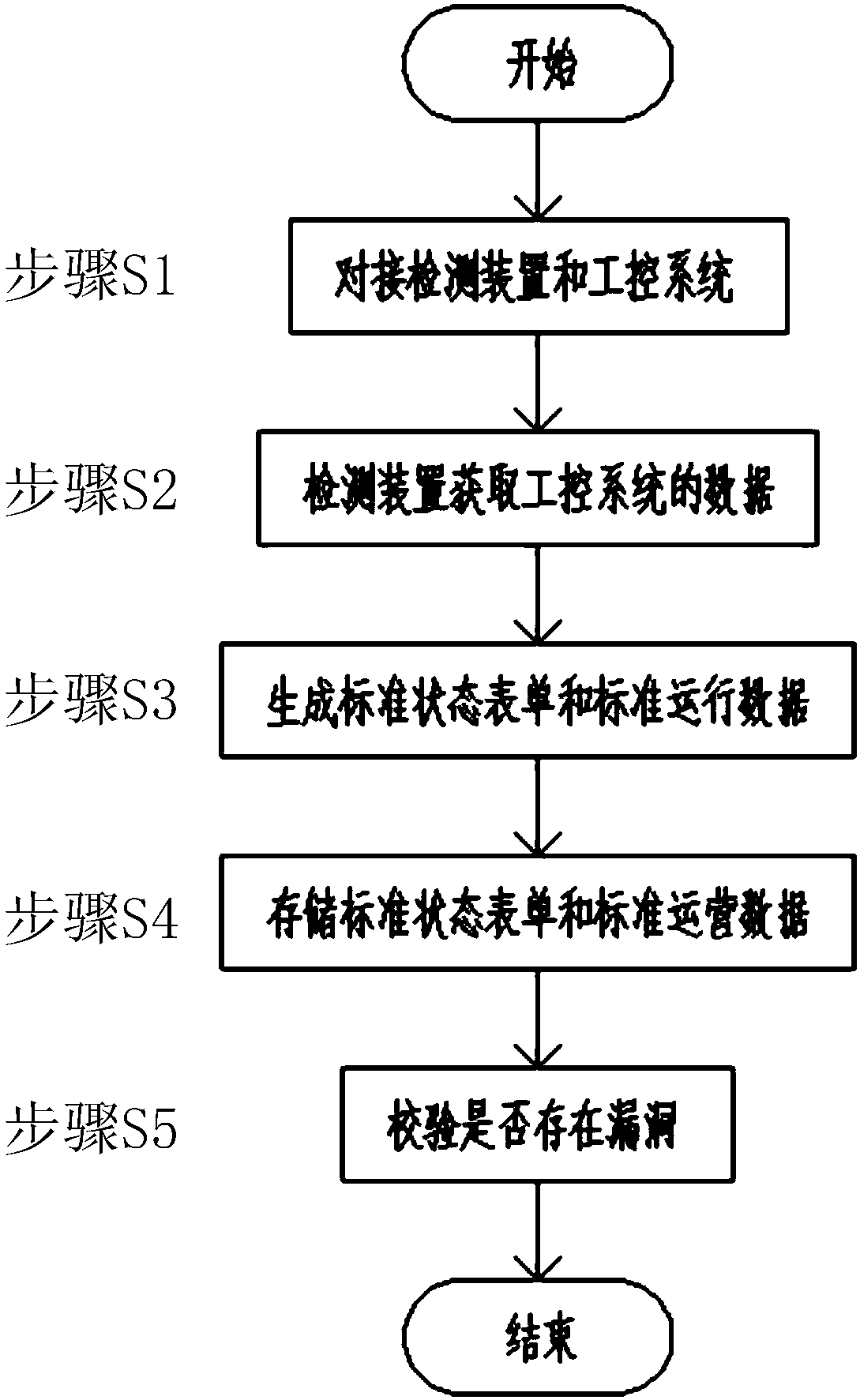
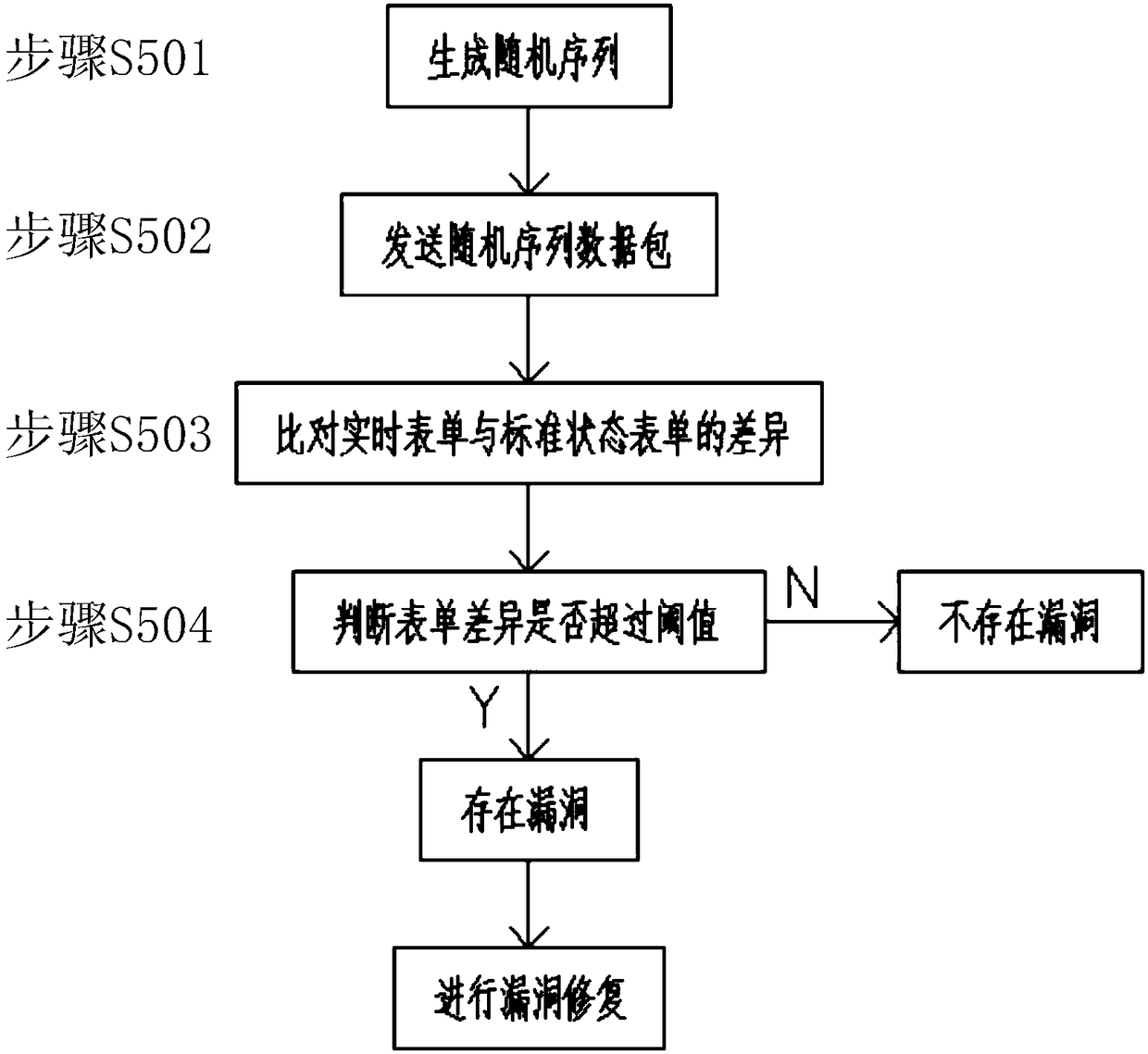
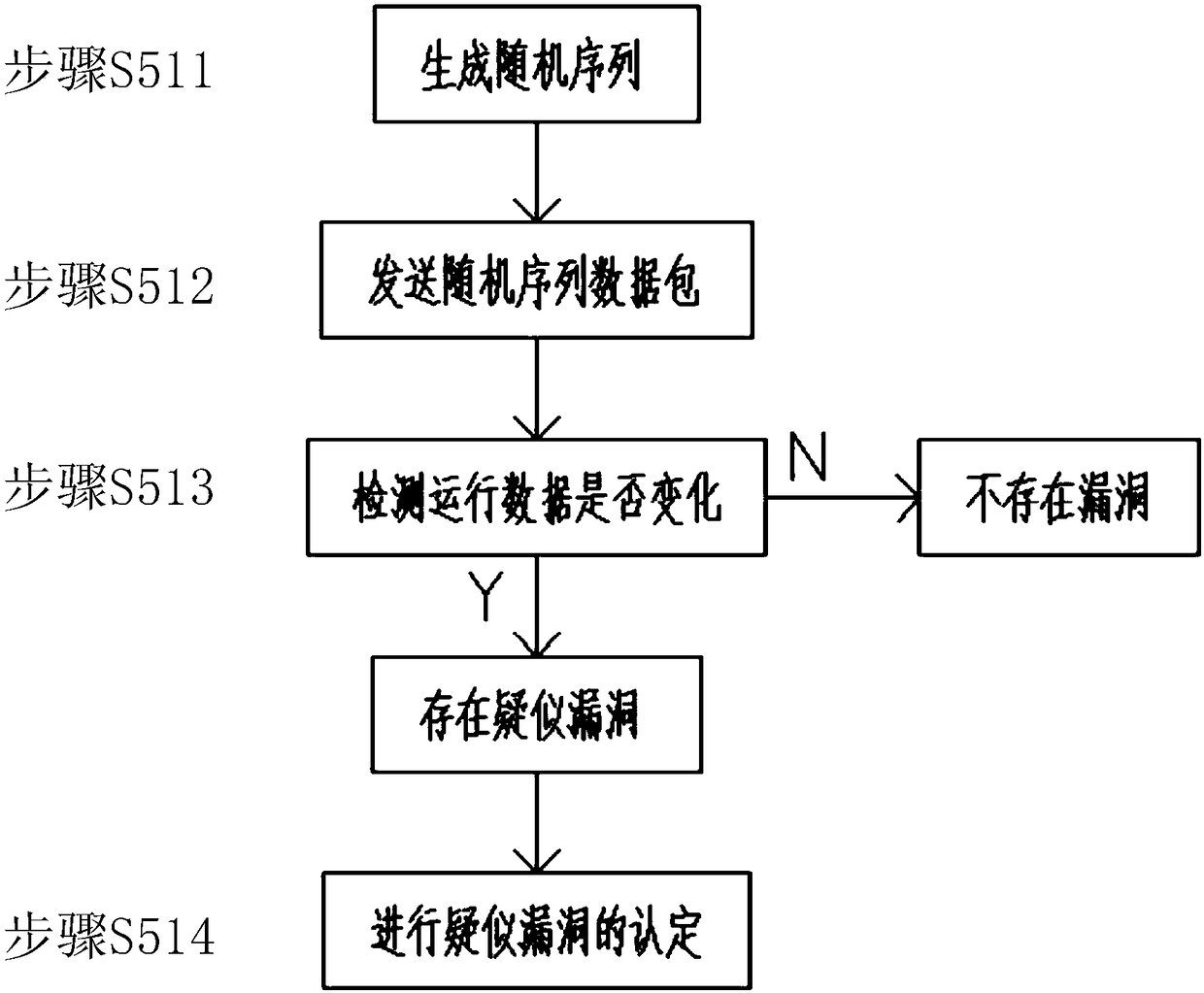
Fuzz testing-based industrial control system vulnerability mining method and apparatus, and vulnerability restoration method
InactiveCN108509797AReduce error rateImprove discovery ratePlatform integrity maintainanceStandard stateRestoration method
The invention discloses a fuzz testing-based industrial control system vulnerability mining method and apparatus, and a vulnerability restoration method, and relates to the technical field of vulnerability detection. The vulnerability mining method comprises the steps of firstly connecting a detection apparatus to an industrial control system; obtaining data of the industrial control system by thedetection apparatus after the detection apparatus is connected to the industrial control system; generating a standard state form and standard running data by the detection apparatus; storing the standard state form and the standard running data after the standard state form and the standard running data are generated; and starting vulnerability detection by the detection apparatus wherein the vulnerability detection is performed through fuzz testing. By adopting the technical scheme, during delivery, the vulnerability detection is firstly performed, and original passive vulnerability detection and restoration become active vulnerability detection, so that the error probability of the industrial control system after delivery is reduced and the user experience is improved; and the fuzz testing is performed through the state form and the running data, so that the vulnerability discovery probability is higher and the accuracy is higher.
Owner:福州恒奥信息科技有限公司
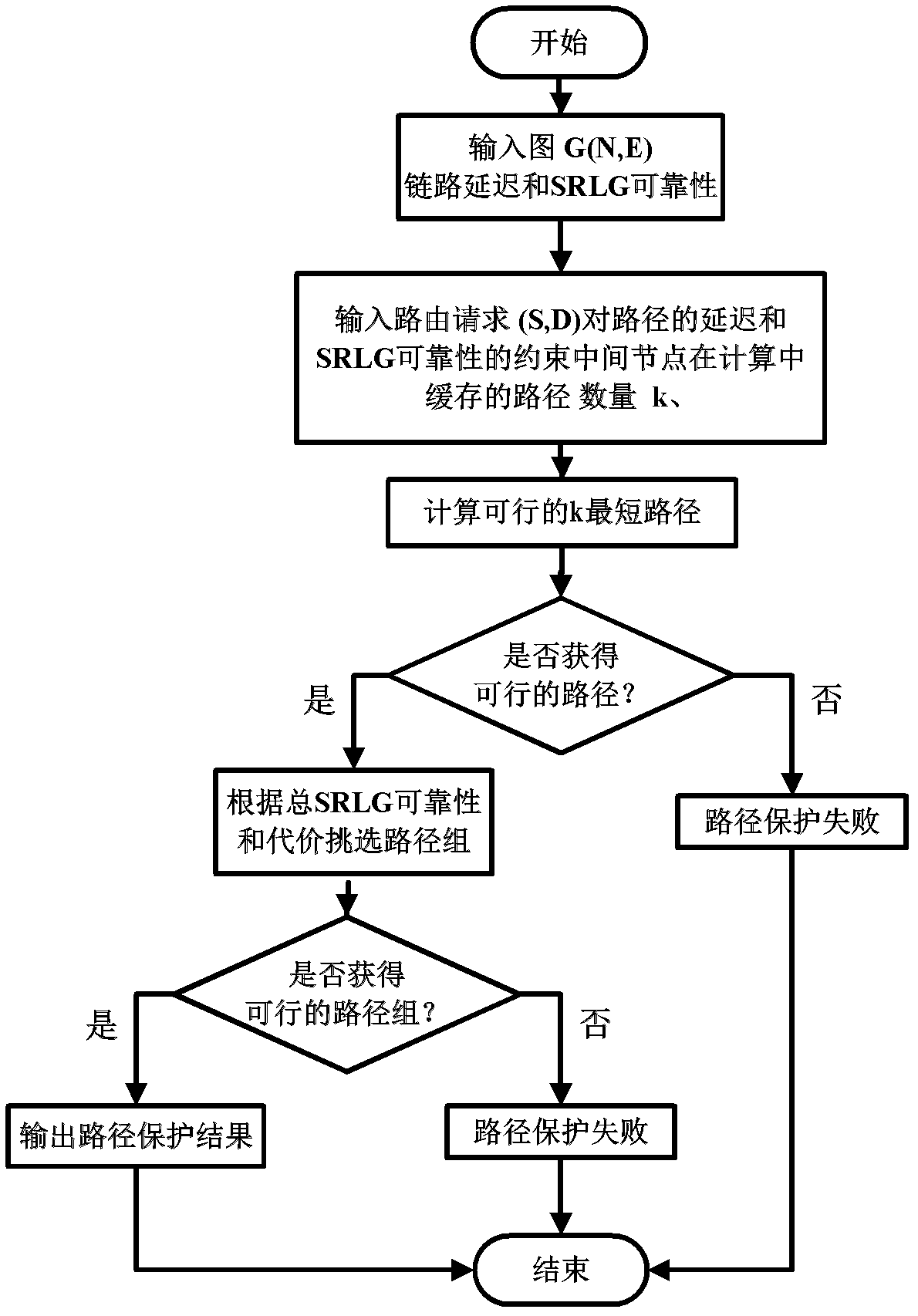
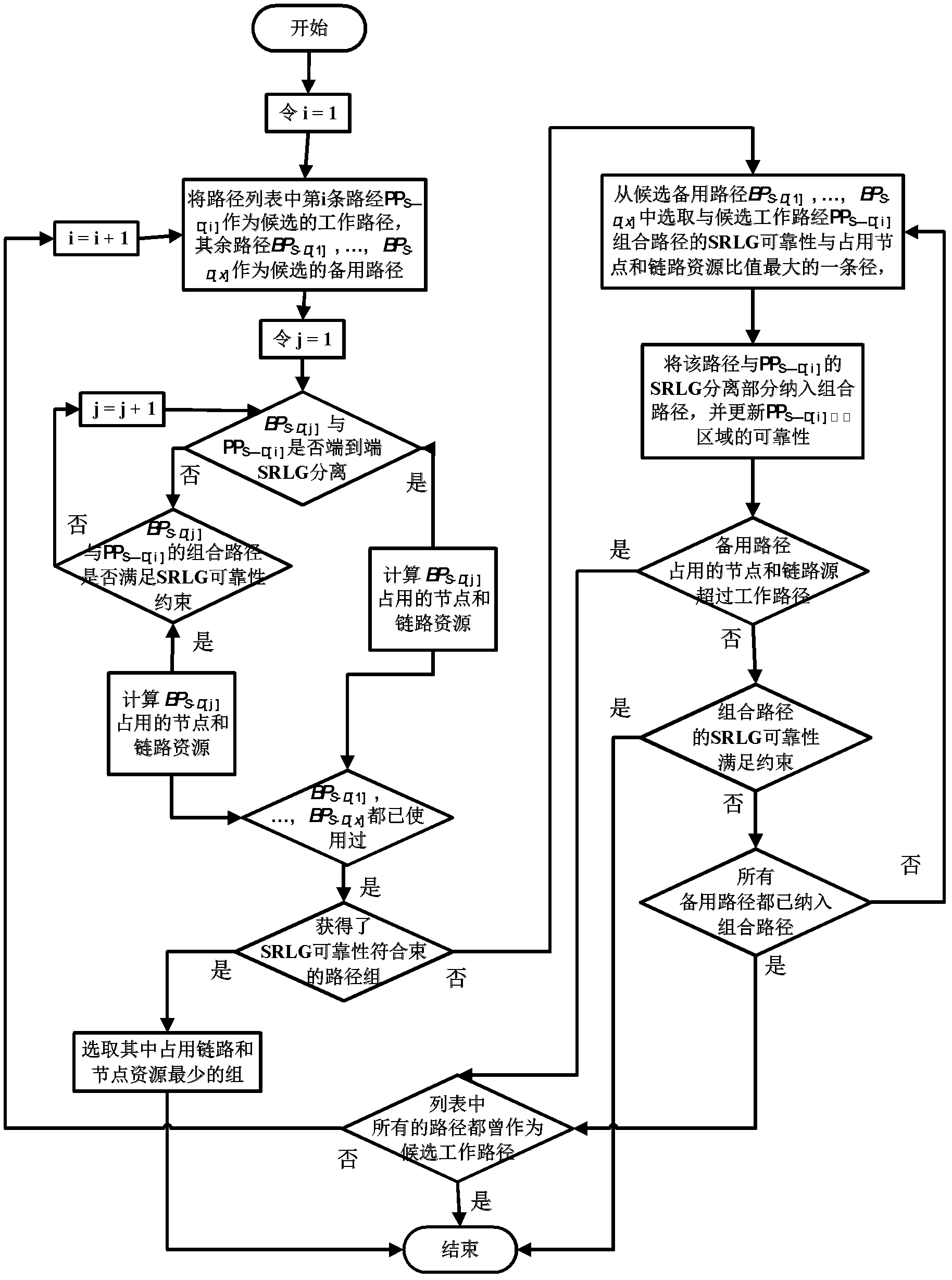
Path protection method for optimizing node sleep under delay and shared risk link group restraint
InactiveCN102325088AConvenient route calculationImprove protectionData switching networksRound complexityNetwork link
The invention discloses a path protection method for optimizing node sleep in a green network under delay and shared risk link group restraint. By using the method, in path calculation, the influence of sleep or awakening delay on a node due to path delay before a sleep node is taken into consideration and the path end-to-end delay calculating precision is improved. A cost function used when the obtained path is selected not only ensures that the reliability of a combined path meets restraint, but also encourages link and sleep node resource share between the protecting paths through calculation of path occupied network link and node resources, therefore, the proportion of the sleep node in the network is increased and the awakening frequency on the sleep node is reduced. The complexity of the method approaches that of the traditional k shortest path calculation-based path protection method; and the invention has strong adaptability on the change of the data flow of the network and expresses excellent and stable performance.
Owner:BEIHANG UNIV
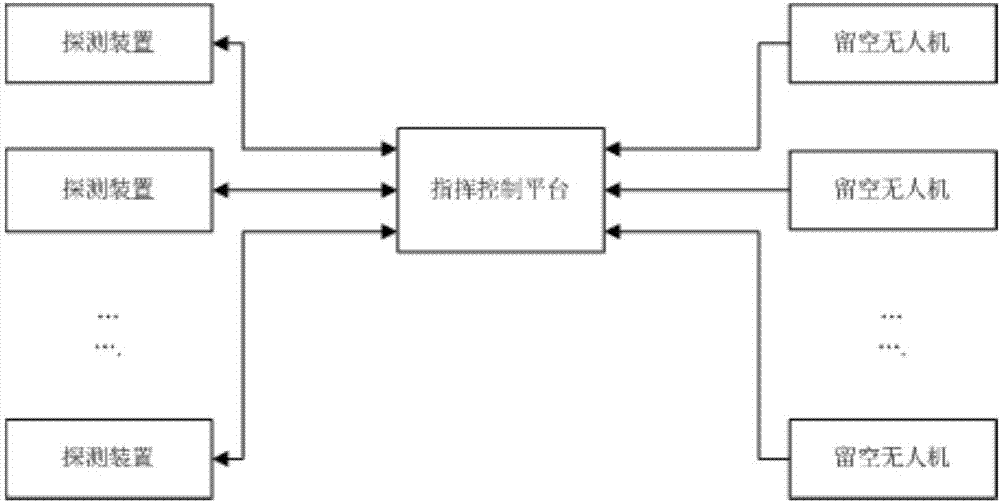
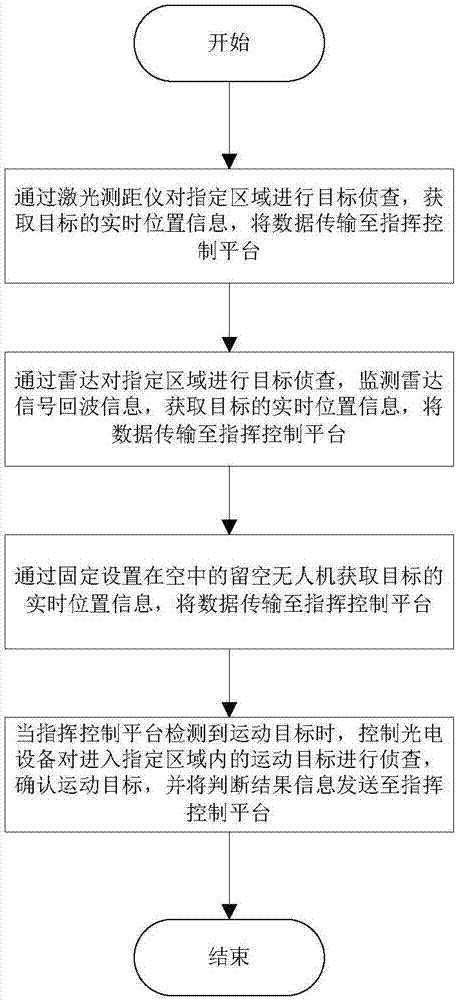
System and method for monitoring low-slow-small unmanned aerial vehicle
InactiveCN107577198AImplement auto-discoveryAchieving identifiabilityProgramme controlOptical rangefindersLaser rangingRadar
The invention provides a system and method for monitoring a low-slow-small unmanned aerial vehicle. The system comprises a detection device used for collecting target information and vacant unmanned aerial vehicle fixedly arranged in the air, wherein the detection device and the vacant unmanned aerial vehicle are sequentially distributed in a set range, and a photoelectric device and a command control platform arranged on the ground are arranged on the vacant unmanned aerial vehicle; a probe device comprises a laser range finder, a radar and a photoelectric device; the detection device and thevacant unmanned aerial vehicle transmit data to the command control platform through a wireless network. According to the system, the radar, the laser range finder, the photoelectric device and the vacant unmanned aerial vehicle are combined, the vacant unmanned aerial vehicle can be automatically found and identified, and the system is compatible with various monitoring means; the data is sent to the command control platform through the wireless network for data analysis, processing and storage, the defects that a single discovery mode is low in finding rate and missed alarm situations are likely to occur are overcome, the finding rate is increased, the missed alarm situations are reduced, and the working efficiency is improved.
Owner:中航天元防务技术(北京)有限公司
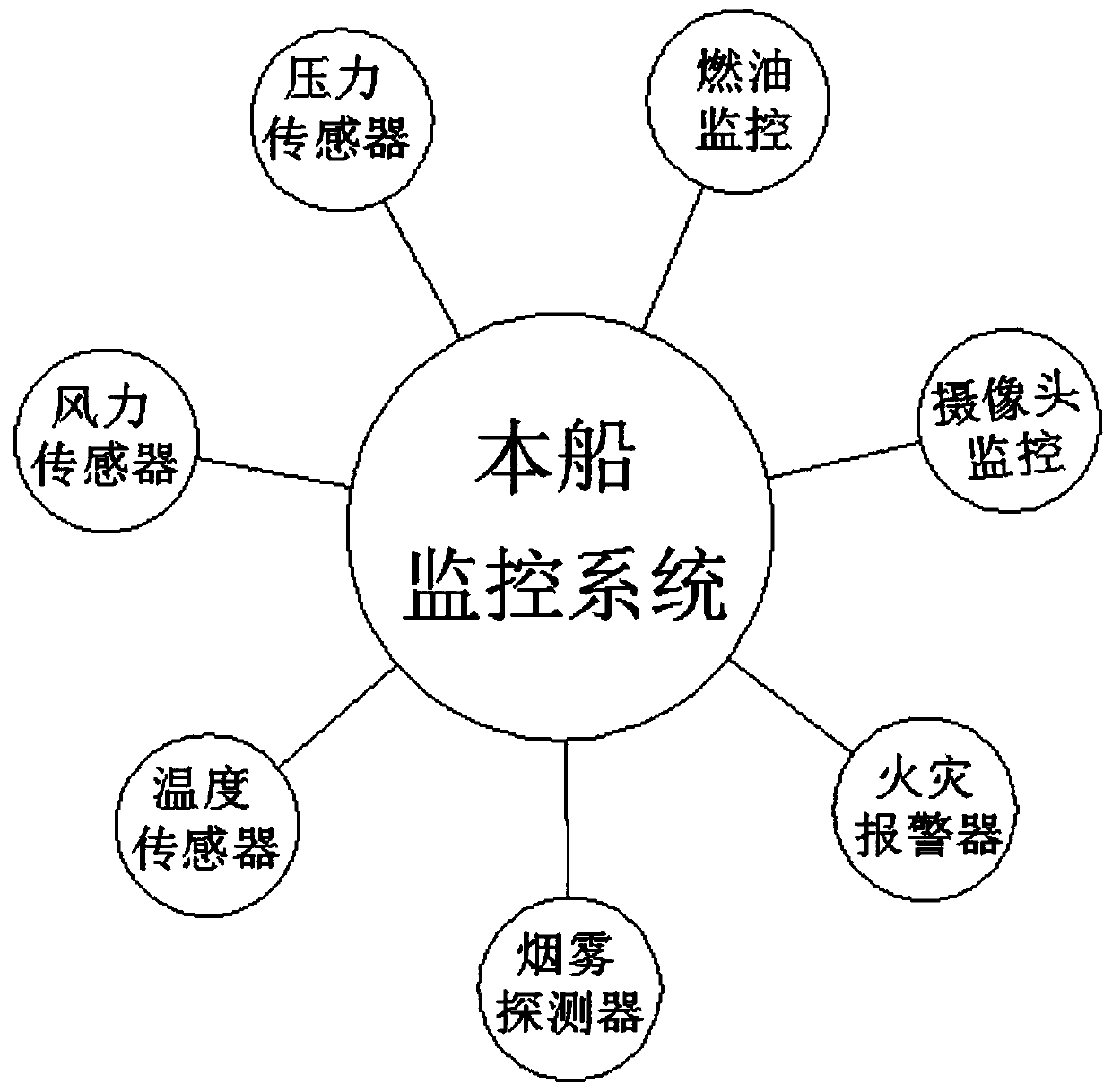
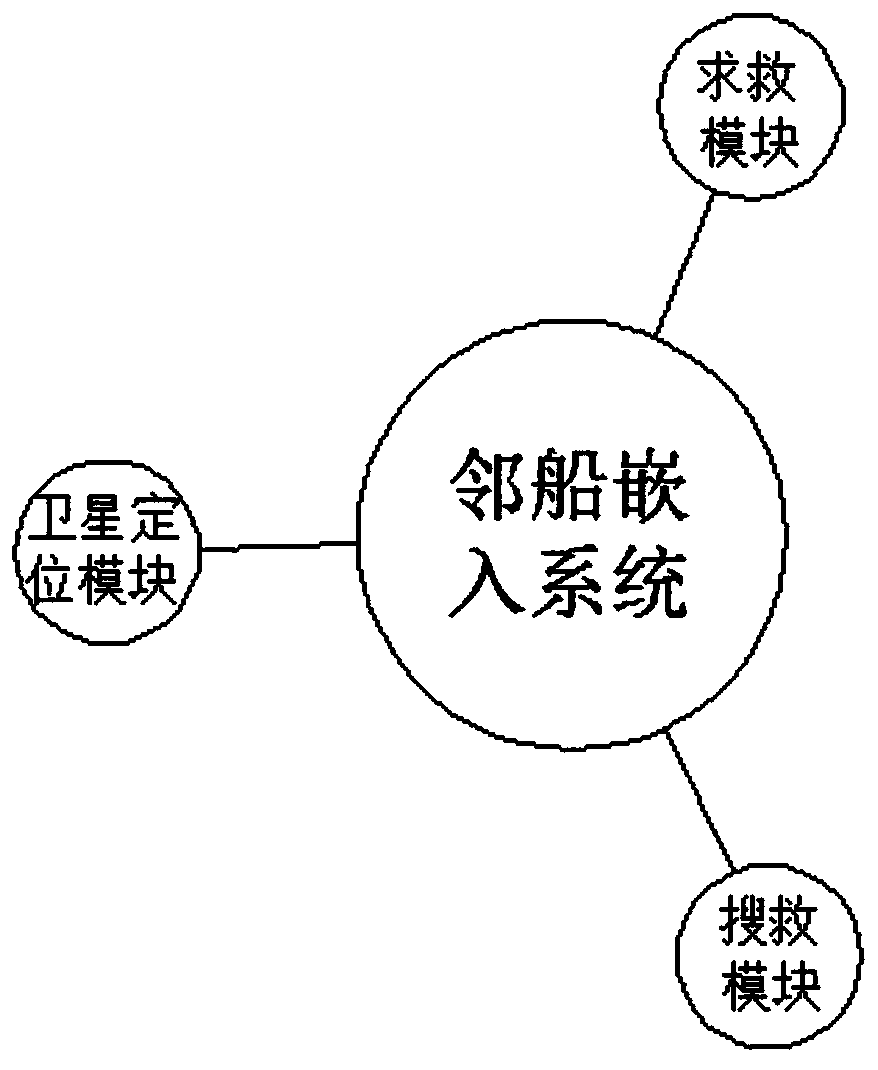
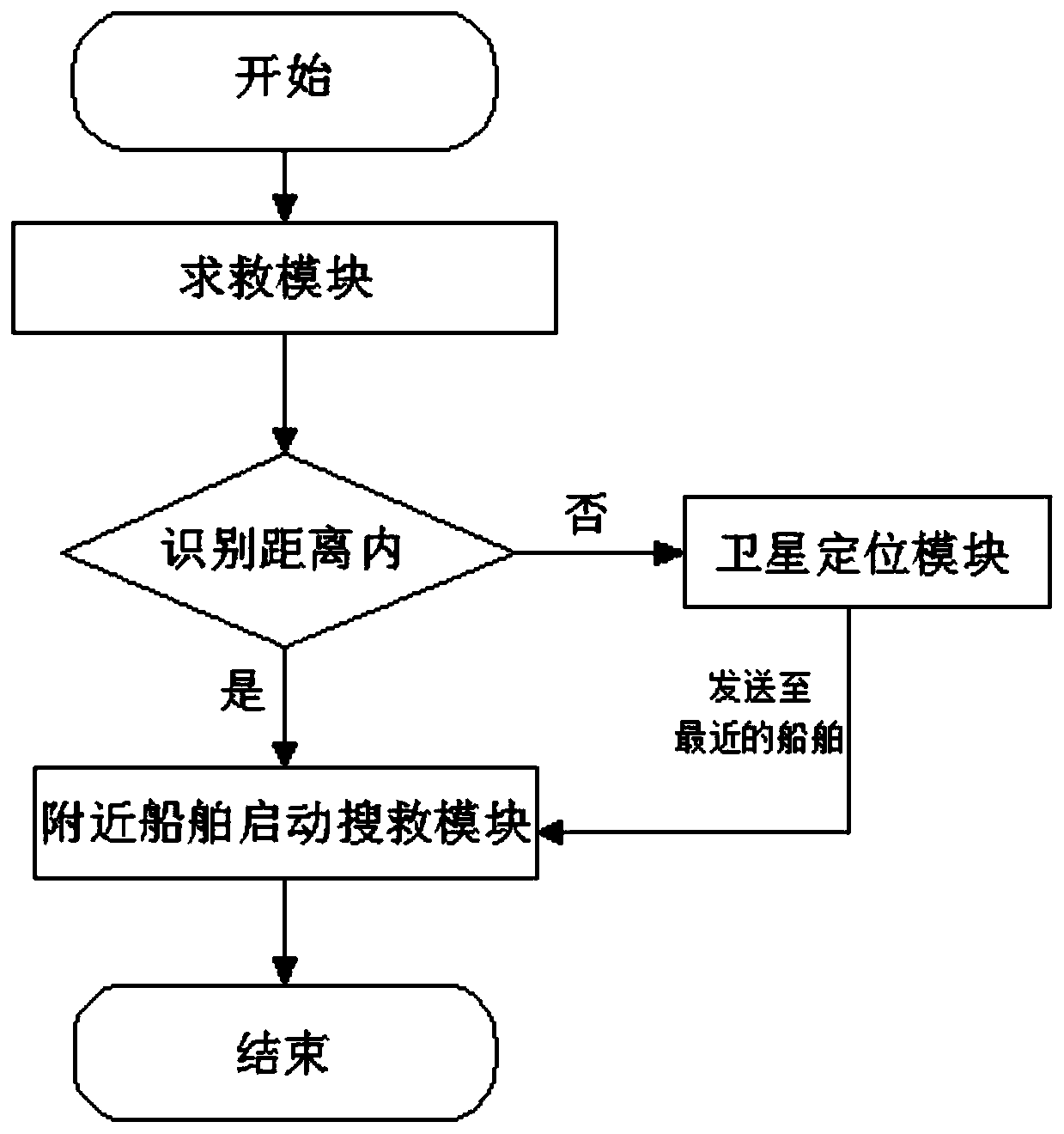
Ship safety monitoring system and using method thereof
ActiveCN109878657AReal-time graspTo offer comfortBody suitsVessel signalling devicesMonitoring systemShip safety
Owner:上海卯瑞船舶设备有限公司
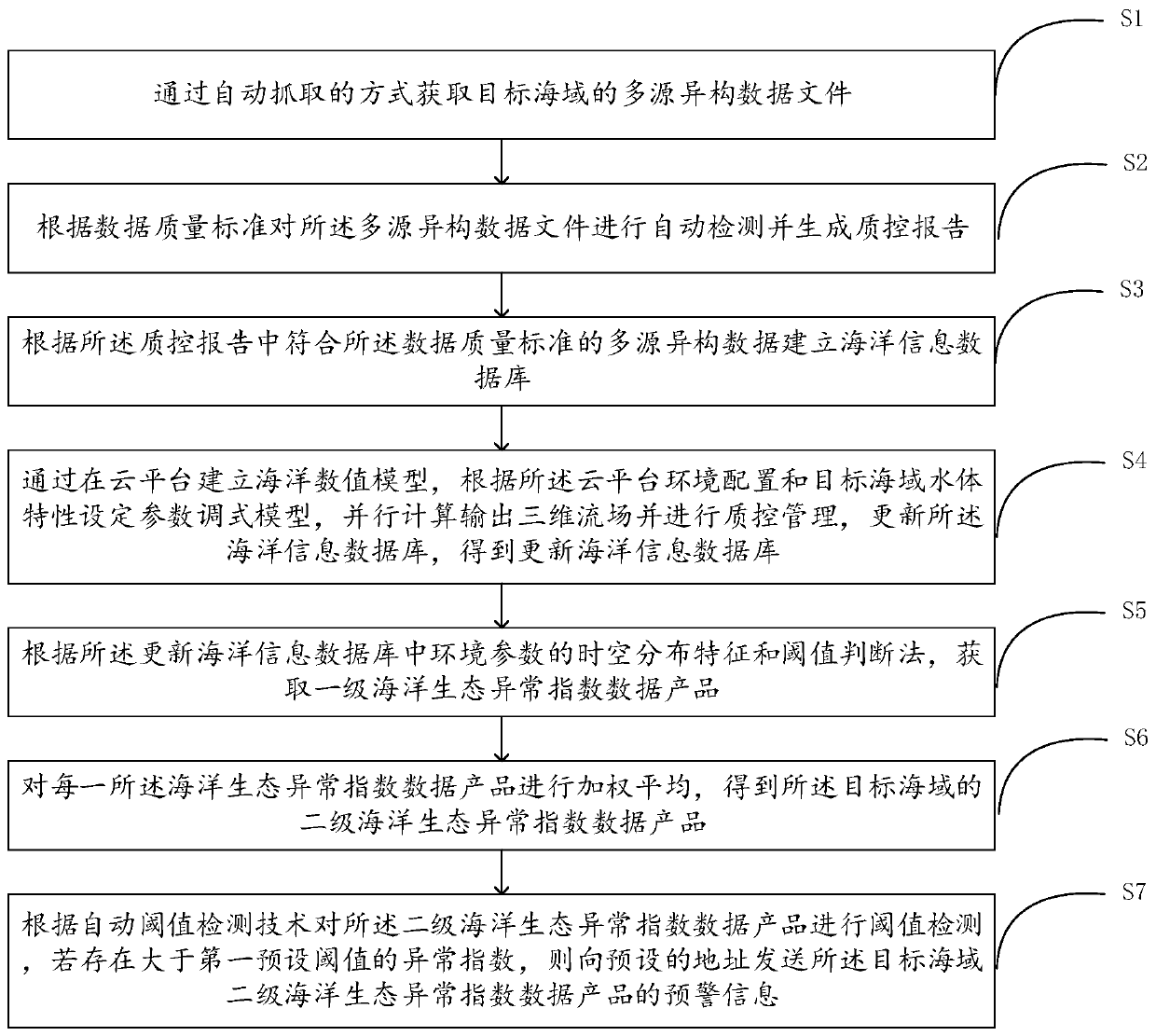
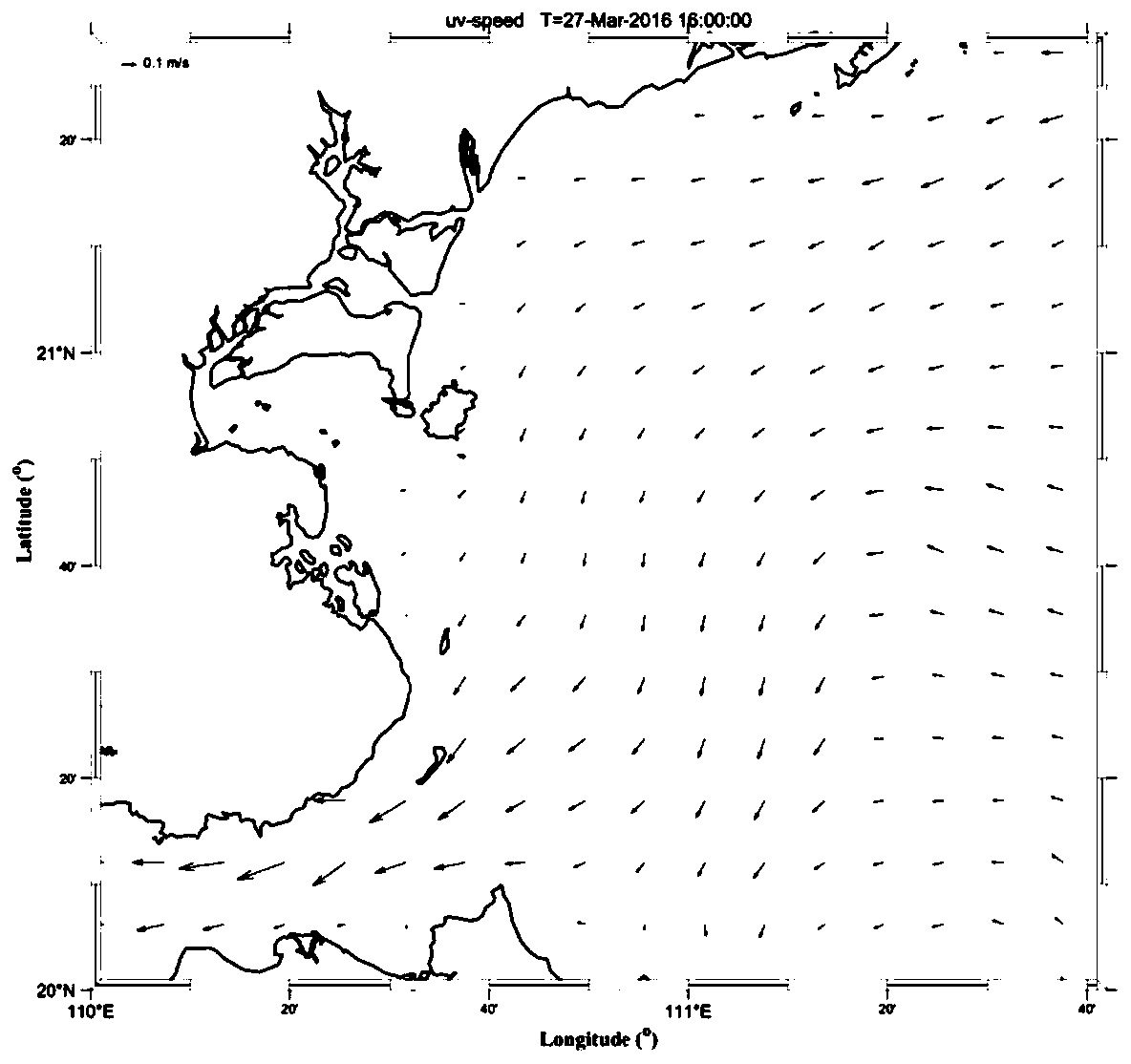
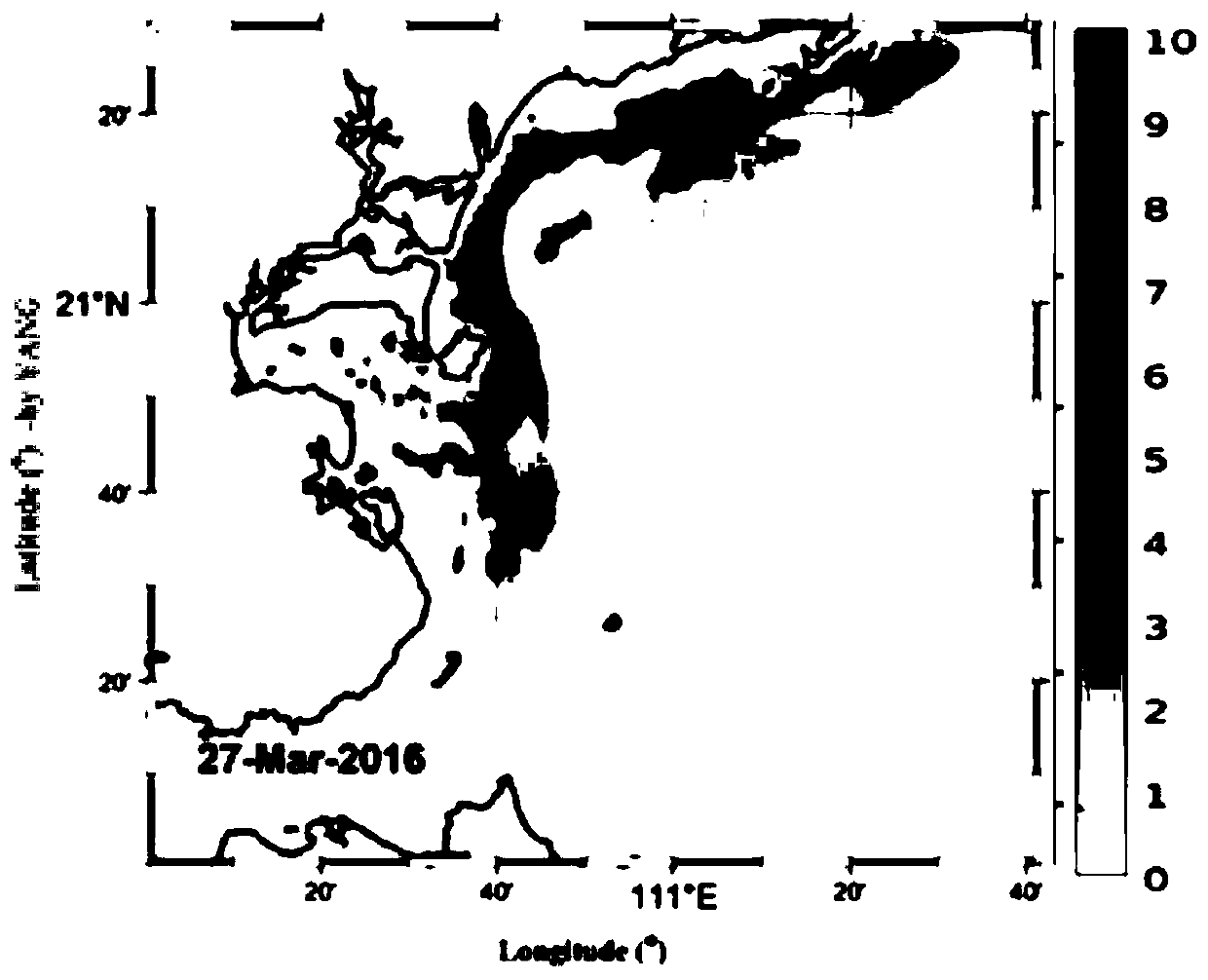
Marine ecological anomaly risk identification method and device based on multi-source heterogeneous data
ActiveCN111311081ATake complexity into accountImprove accuracyWeb data indexingDesign optimisation/simulationData fileRisk identification
The invention discloses a marine ecological anomaly risk identification method based on multi-source heterogeneous data. The method comprises the steps that a multi-source heterogeneous data file of atarget sea area is acquired; generating a quality control report according to the multi-source heterogeneous data file; establishing a marine information database according to the multi-source heterogeneous data meeting the data quality standard; the method comprises the steps of establishing an ocean numerical model on a cloud platform, and updating an ocean information database to obtain an updated ocean information database; obtaining a first-level marine ecological anomaly index data product according to the updated marine information database; performing weighted average on each marine ecological anomaly index data product to obtain a secondary marine ecological anomaly index data product of the target sea area; and carrying out threshold detection on the secondary marine ecology abnormal index data product, and if an abnormal index greater than a first preset threshold exists, sending early warning information. According to the marine ecological anomaly risk identification method based on the multi-source heterogeneous data, the accuracy of marine ecological anomaly risk identification can be effectively improved.
Owner:国家海洋局南海预报中心
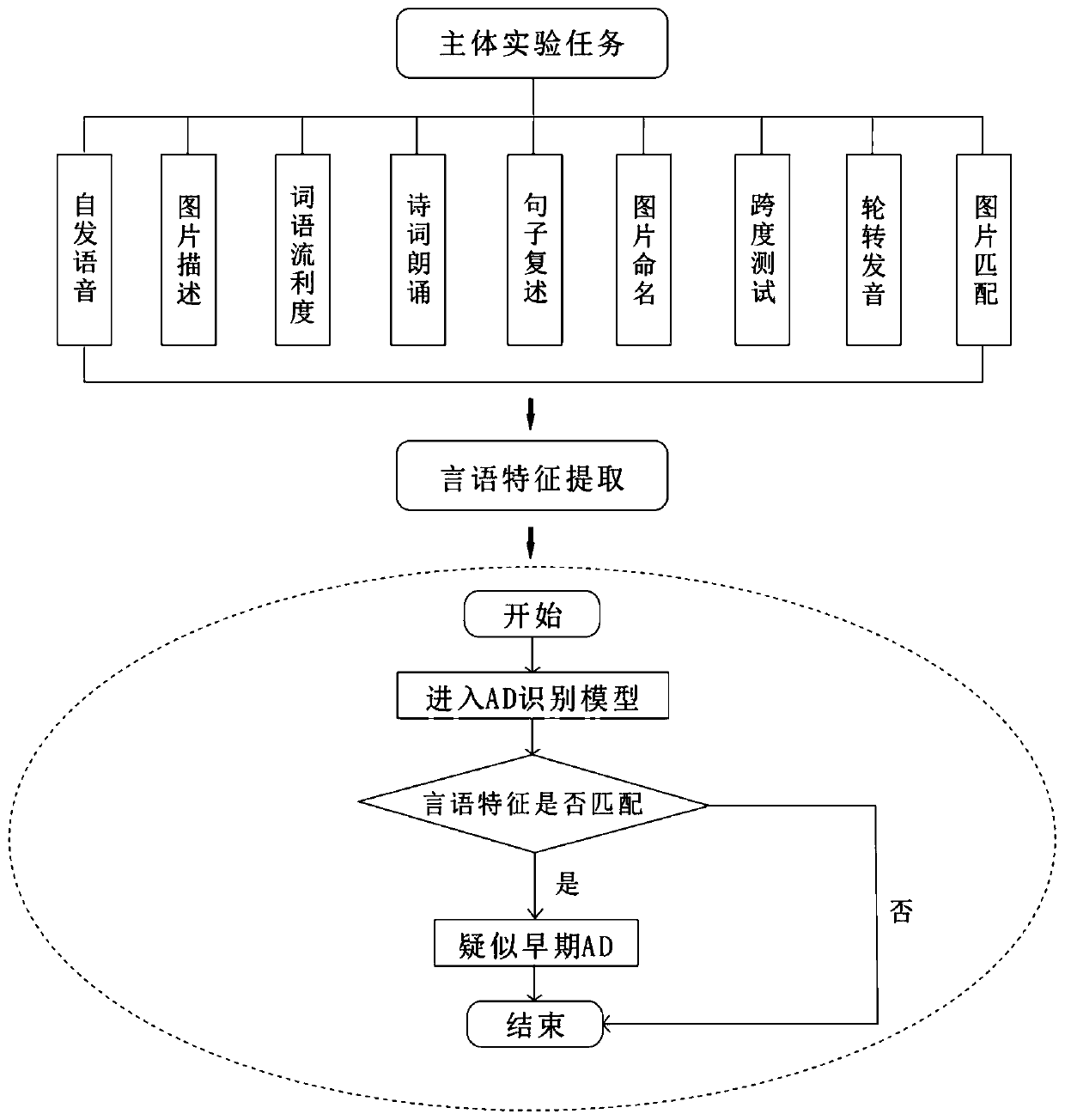
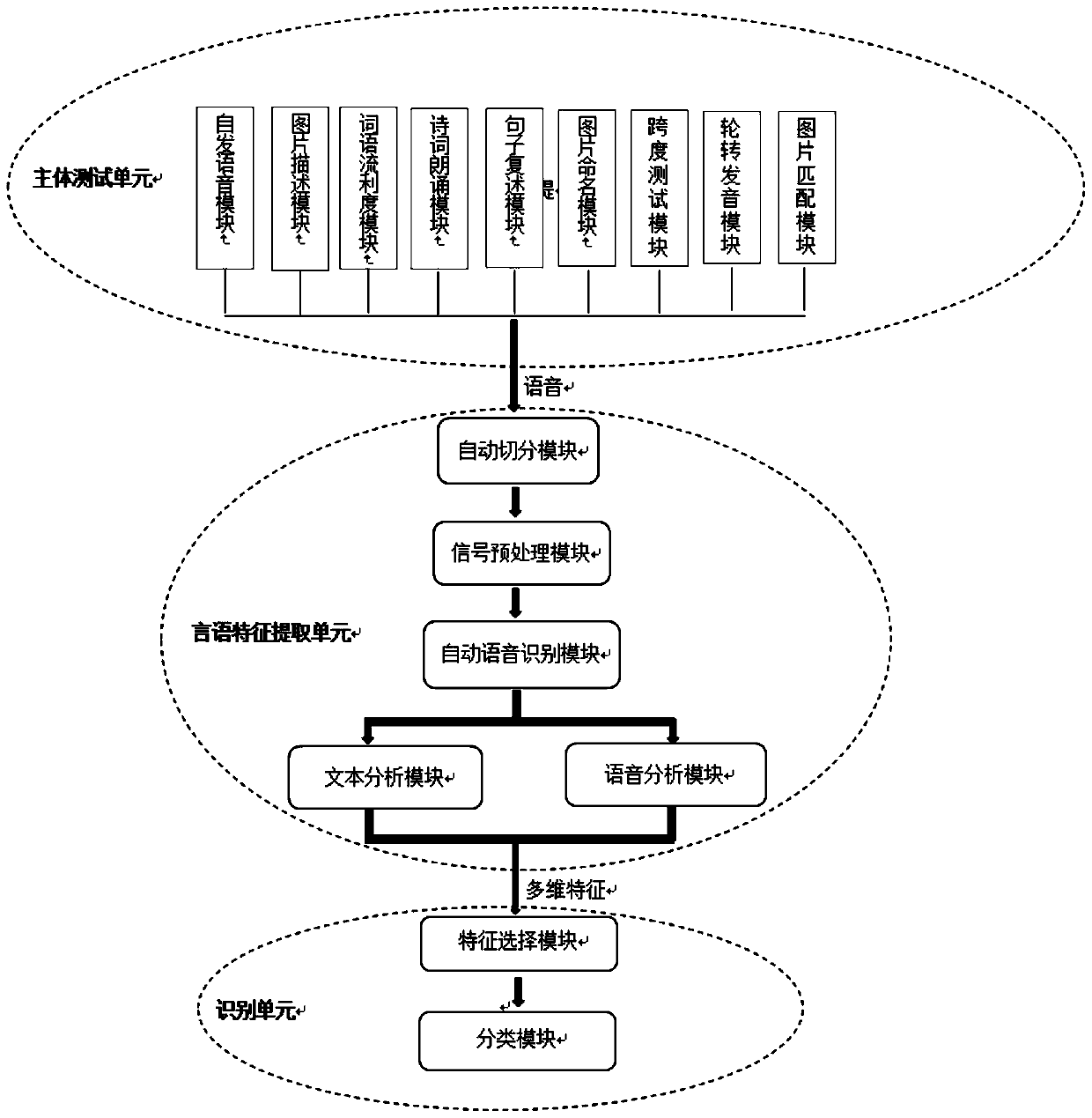
Early-stage AD speech auxiliary screening system aiming at mandarin Chinese
ActiveCN109841231ALow costEasy to realize large sample collectionSpeech recognitionResearch ObjectFeature extraction
The invention relates to an early-stage AD speech auxiliary screening system aiming at mandarin Chinese. The system comprises a main body testing unit, a speech feature extracting unit and a recognizing unit, wherein the main body testing unit is used for testing a tested object; the speech feature extracting unit is used for extracting the speech features of the tested object and storing the speech features; the recognizing unit is used for recognizing the speech features; and the main body testing unit comprises a spontaneous voice module, a picture describing module, a word fluency module,a poem reciting module, a sentence repeating module, a picture naming module, a span testing module, a cycle pronouncing module and a picture matching module. The system starts from the aspect that the early-stage AD speech function is damaged, aiming at the research object of AD early-stage screening of the mandarin Chinese, the invention provides the assorted device relevant to the early-stage AD speech specific features, which has the advantages that the cost is low, the rich data can be acquired in real time, the large sample collection can be easily realized, remote collecting and analysis can be realized, etc.
Owner:SHENZHEN INST OF ADVANCED TECH
Improved TBD algorithm
InactiveCN109839621AImprove signal-to-noise ratioImprove discovery rateWave based measurement systemsSignal-to-noise ratio (imaging)Reference window
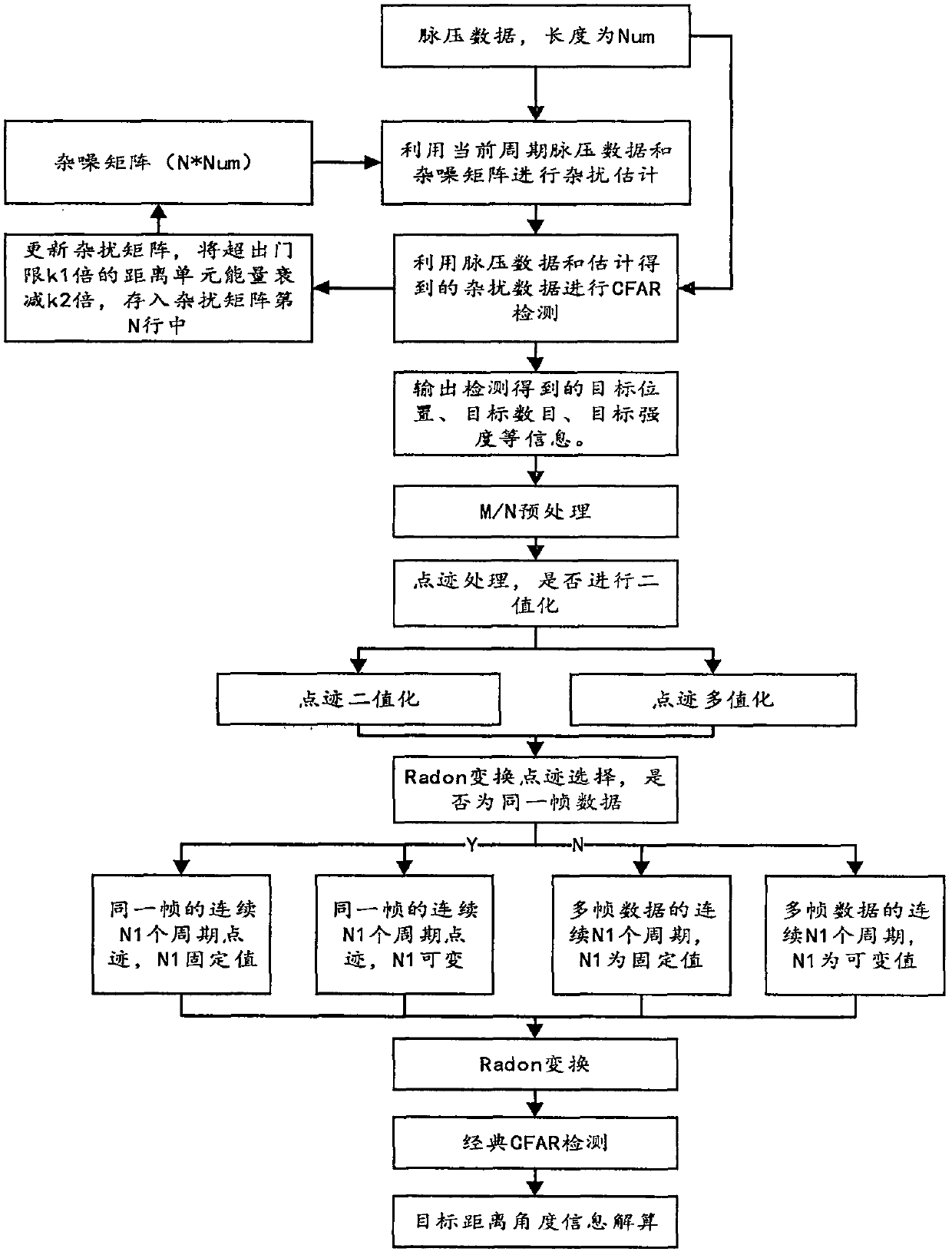
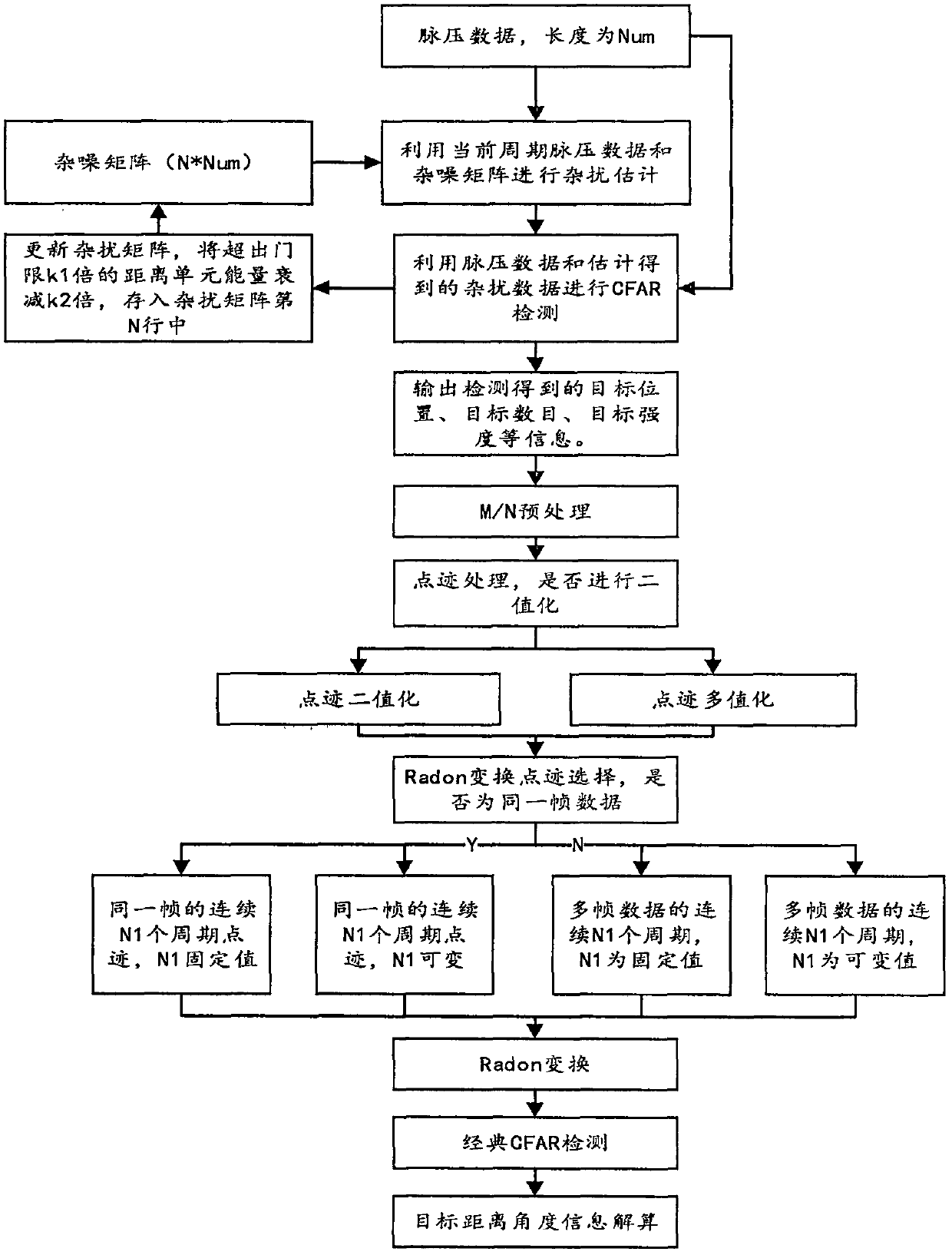
The invention provides an improved TBD algorithm, which belongs to the technical field of radar target detection. The improved TBD algorithm is divided into four parts that: (1) an algorithm based onCA-CFAR detection causes a false alarm rate at the edge of clutters, and judges a current environment according to data in a reference window; (2) N_cpi points can be sampled in each CPI, and N / M processing can be performed on the plots after the judgment; (3) the preprocessed plot for Radon transform is selected; (4) and angular information of a target and a distance from a central point positioncan be obtained according to the result after Radon transform. The TBD algorithm based on Radon transform is adopted for increasing a signal-to-noise ratio of the target plot, an improved CFAR detection algorithm is adopted to perform confidence level classification on the threshold plot and process the multi-frame plots, and the detection probability of the target plot is increased by effectively suppressing sea clutters and part of interference signals.
Owner:艾索信息股份有限公司
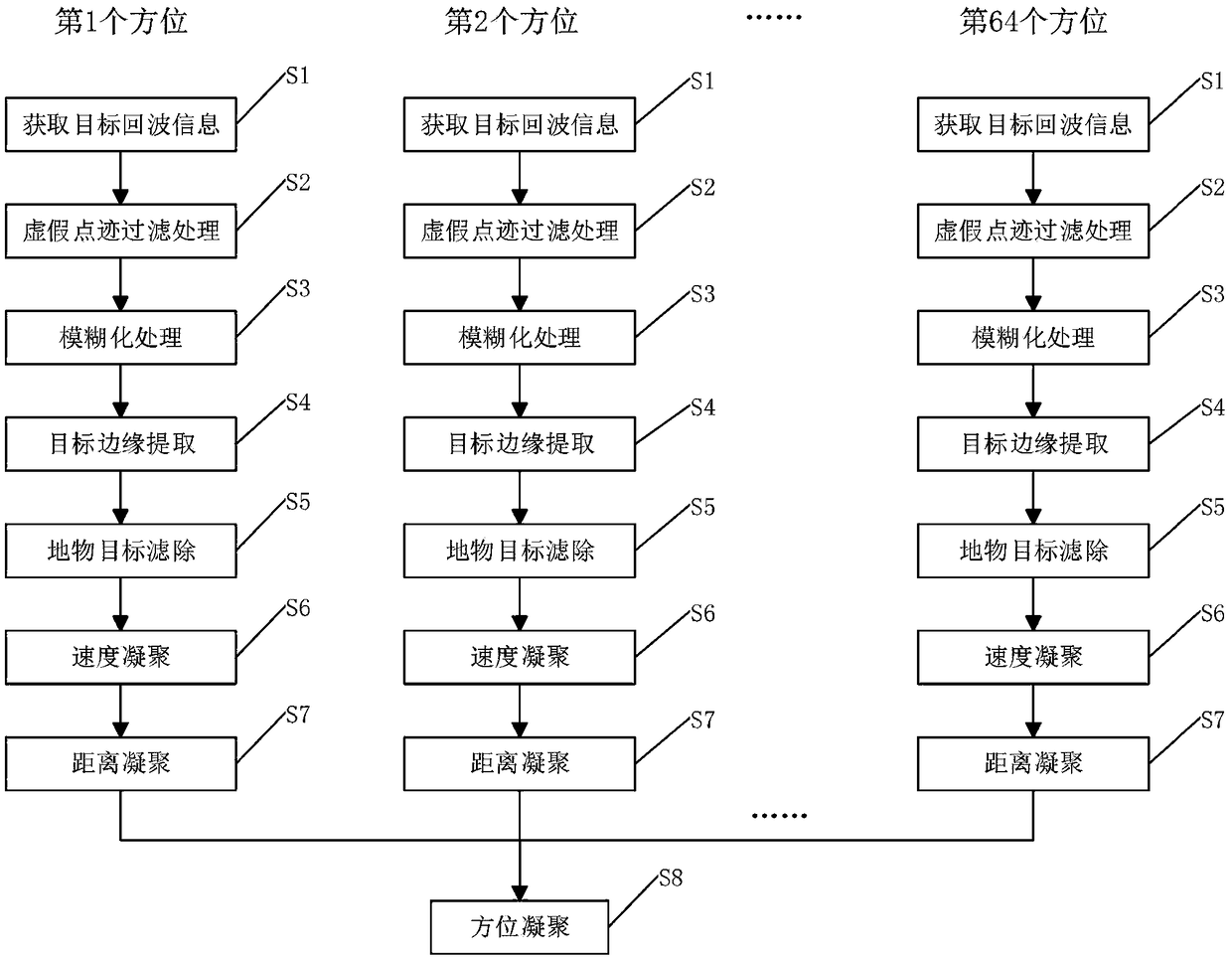
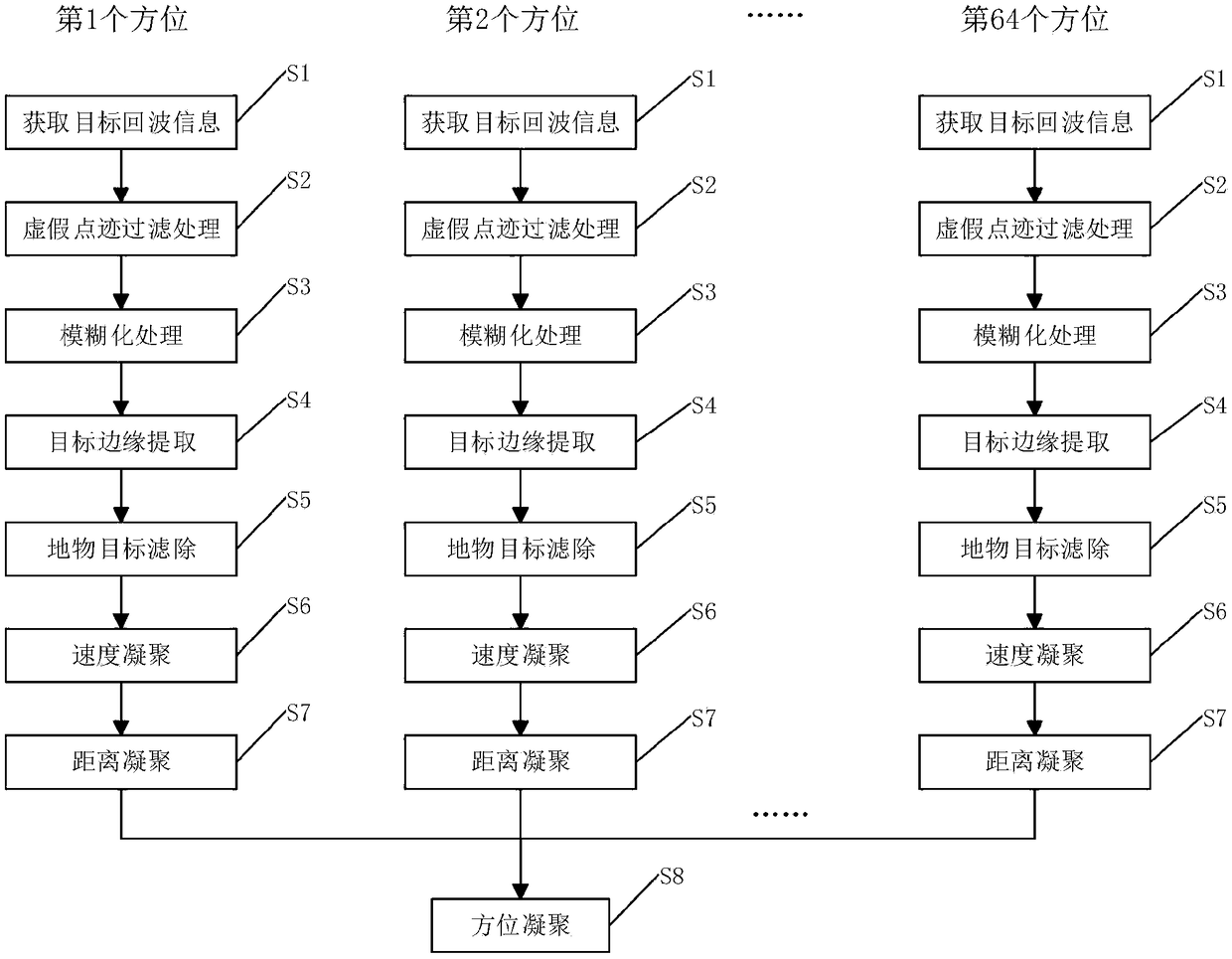
Target extraction and aggregation method based on ground surveillance radar system
ActiveCN108983194AReduce false alarm rateImprove discovery rateWave based measurement systemsSecondary surveillance radarRadar systems
The invention discloses a target extraction and aggregation method based on a ground surveillance radar system. The method comprises a step of performing false dot filtering processing on target echoinformation, a step of blurring the filtered target echo information to form a two-dimensional image, a step of performing target edge extraction on the two-dimensional image, a step of performing ground object target filtering processing after the target edge extraction, a step of sequentially carrying out velocity aggregation and distance aggregation on target echo information belonging to the same target after the ground object target filtering processing, and a step of performing azimuth aggregation on the target echo information which is subjected to distance aggregation to obtain targetecho information and target parameters belonging to the same target after the azimuth aggregation. According to the invention, the risk that the same target is split into multiple targets when the target extraction is performed is reduced, the risk that targets of different speeds are merged into the same target when the targets are aggregated is reduced, the integrity and accuracy of the target extraction and the accuracy of the target aggregation are improved, and a reliable basis is provided for subsequent track processing.
Owner:ANHUI SUN CREATE ELECTRONICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com