Network security monitoring method based on bypass monitoring and software packet capturing technology
A network security and bypass monitoring technology, applied in electrical components, transmission systems, etc., can solve the problems of low detection rate and slow detection speed of automatic alarm and disconnection, so as to reduce potential virus and Trojan attacks, protect security, and improve Discover the effect of speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific embodiments.
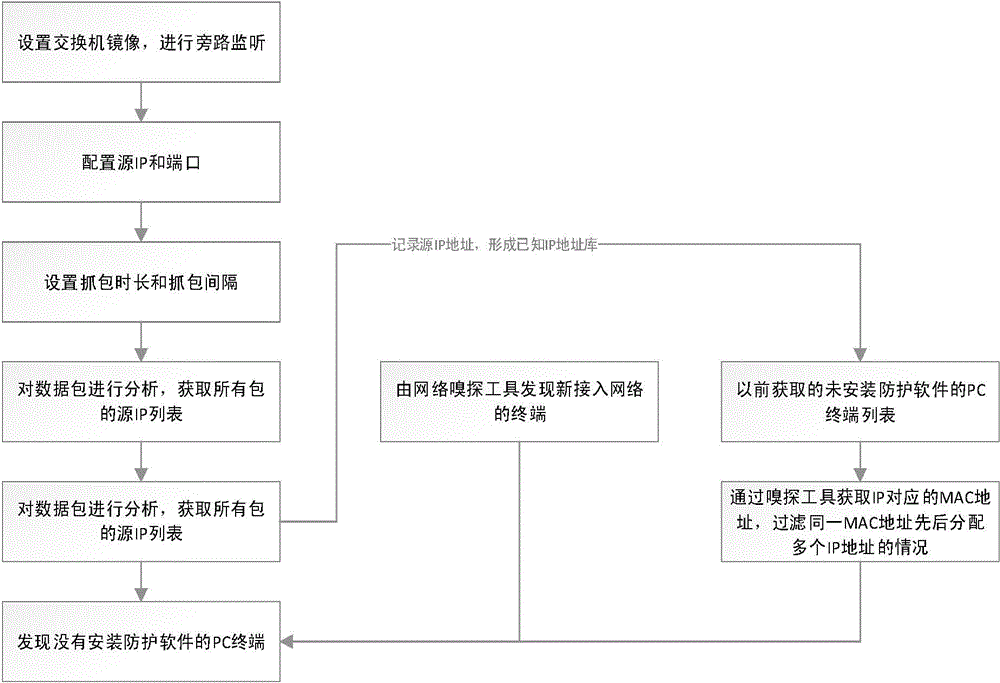
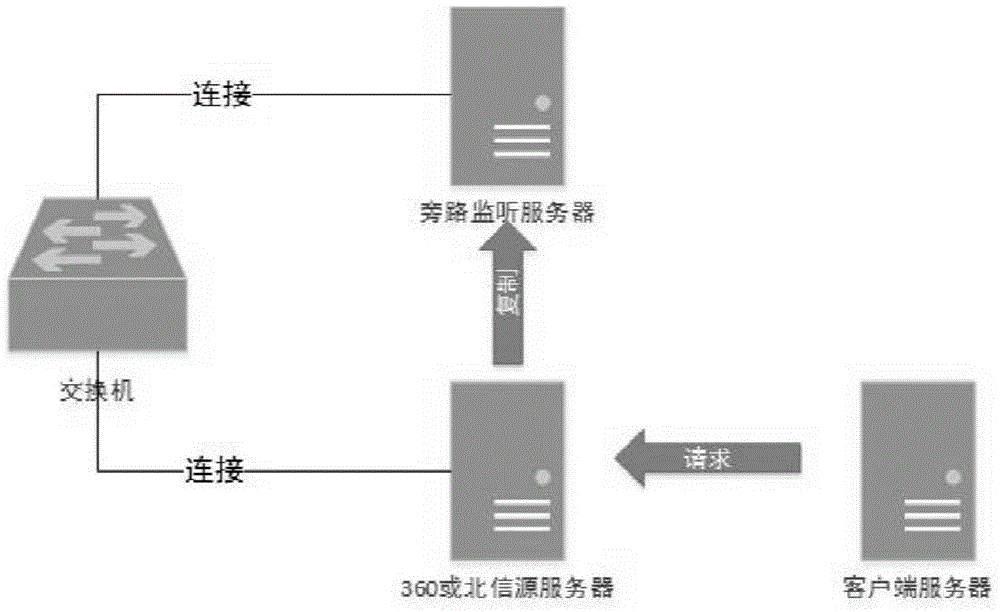
[0028] see figure 1 , the present invention regularly analyzes all data packets arriving at the security protection server in the network by setting a bypass monitor on the switch on the same network segment as the network security service monitoring software server, and analyzes whether the designated client PC terminal and the security monitoring server are There is login, request or heartbeat data, so as to determine whether the corresponding security protection software is installed on the client PC terminal.
[0029] The principle of the present invention is to mirror on the switch port of the network where the security server is located, set up bypass monitoring, use the JAVA programming language to analyze these network data packets, obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com