A Quantitative Network Security Evaluation Method and Evaluation System
A technology for network security assessment and network flow, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems that cannot reflect the actual function and effect of security control measures, and it is difficult to quantitatively analyze the real security and confidentiality of the network. Explain the actual threat of the system and the possibility of the threat, so as to achieve a more certain effect of the evaluation result
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
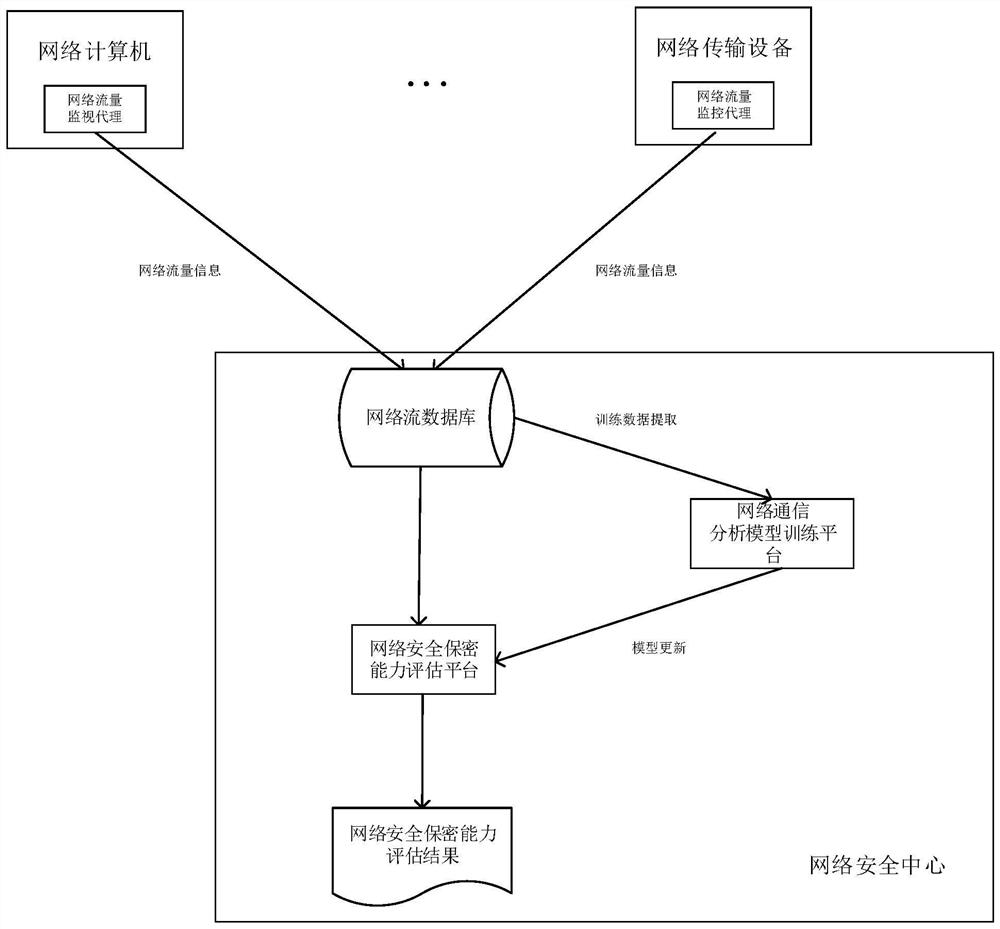
[0046] image 3 For the logical diagram of the quantitative network security assessment of the present invention, in image 3 Among them, the network computer and network transmission equipment are the network nodes of the target system, the network flow database is the network flow data storage module, the network security confidentiality assessment platform is the network security assessment module, and the network communication analysis model training platform is the model parameter calculation module. Network computers and network transmission equipment send network traffic information to the network flow database, and the network communication analysis model training platform extracts training data from the network flow database, calculates and updates model parameters and sends them to the network security and confidentiality assessment platform to update the network communication analysis Model, the network security confidentiality assessment platform receives network t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com