Malicious webpage discovery method and system based on feature detection
A malicious webpage and feature detection technology, applied in the field of network flow security, can solve problems such as long time consumption, low resource utilization rate, and large computing resource consumption, and achieve the best efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the drawings in the embodiments of the present invention.
[0045] The present invention will be described in detail below in conjunction with the above.
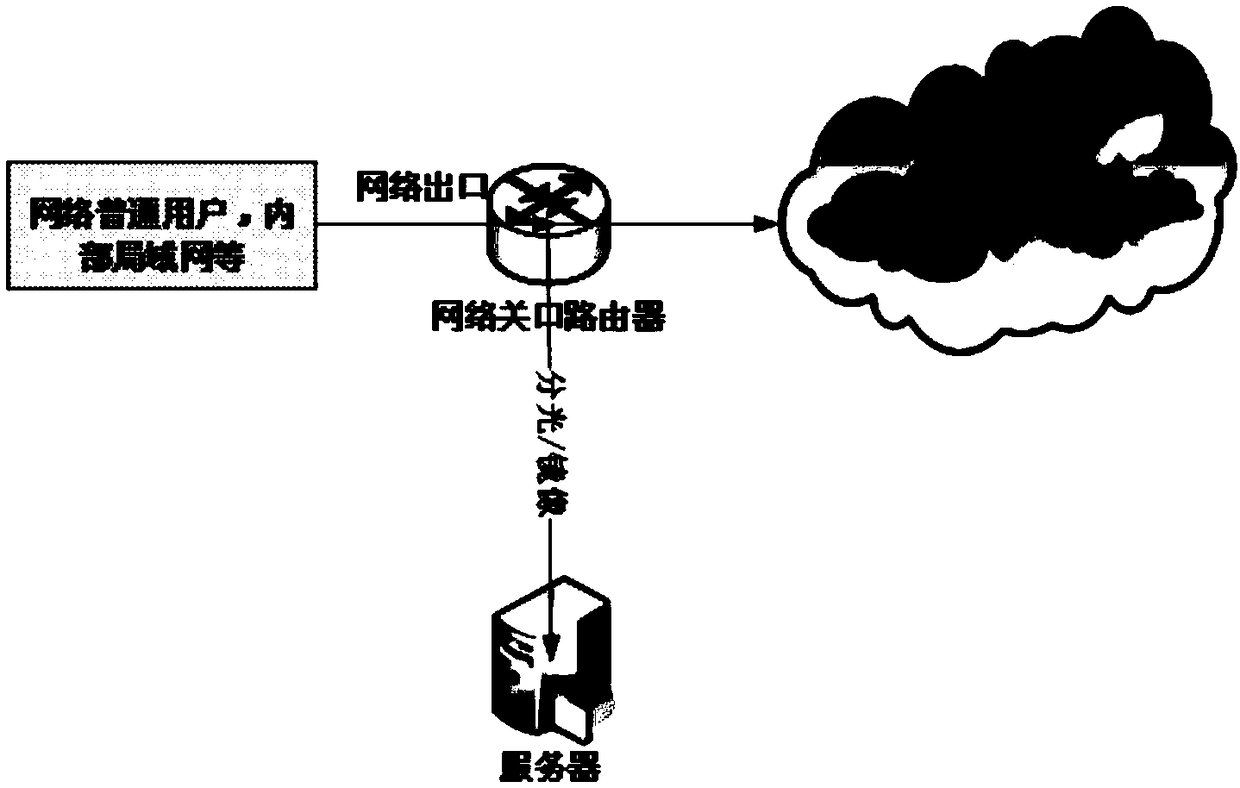
[0046] The system architecture diagram of the present invention is as follows figure 1 shown.
[0047] 1) Analyze HTTP traffic in real time through the network flow capture platform Papp. Papp has two configuration methods, one is to capture traffic in real time for analysis, and the other is to read network traffic Pcap packets (process characteristic analysis software package) for testing ; Among them, the network flow capture platform Papp is a special traffic acquisition tool, and its function is similar to the TCPDUMP command under Linux.
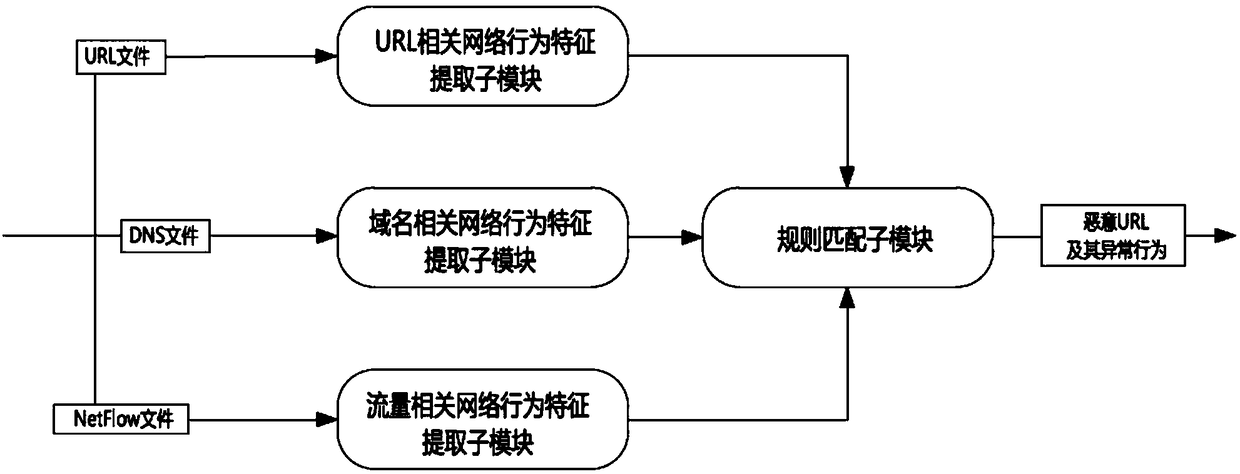
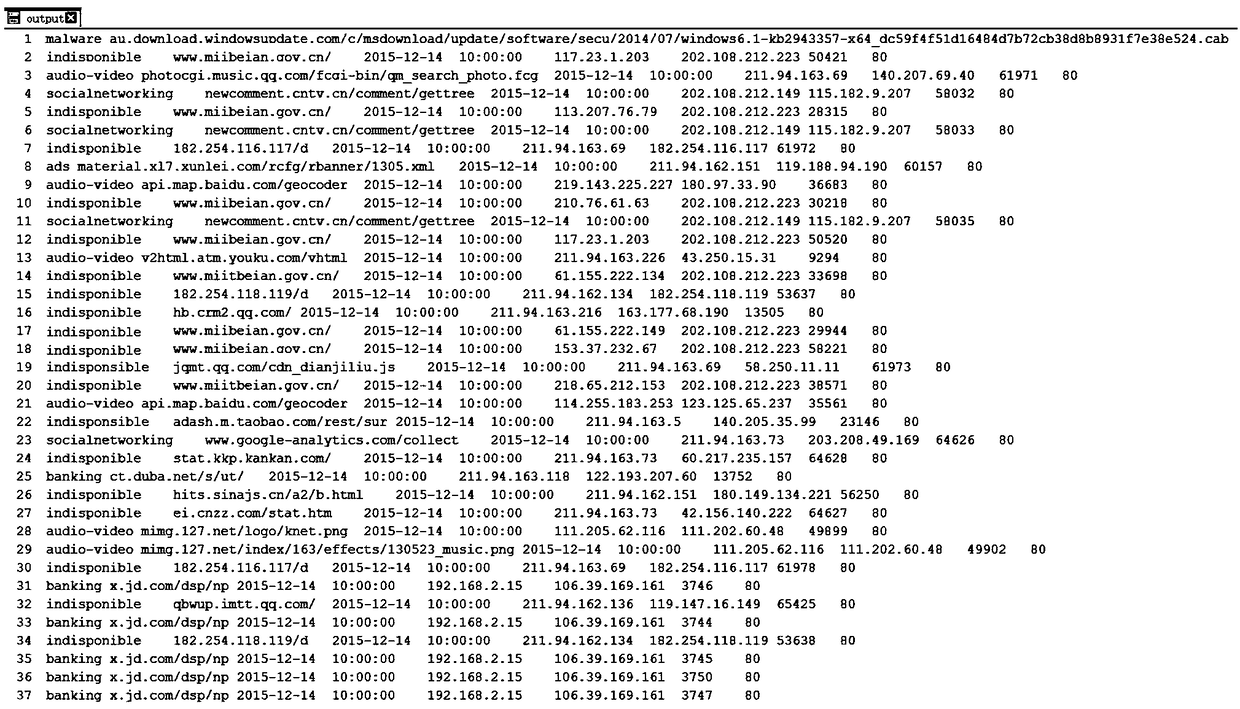
[0048]2) URL features are extracted from traffic parsed by the Papp platform.
[0049] It is implemented through the URL-related network b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com