Network security system and method based on big data
A network security system and big data technology, applied in the direction of road vehicle traffic control system, traffic control system, traffic flow detection, etc., can solve the problems such as the inability to divert the traffic flow in advance, the lack of key protection for sudden accidents at the intersection, etc. The effect of preventing secondary accidents, reducing the possibility, and saving human resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
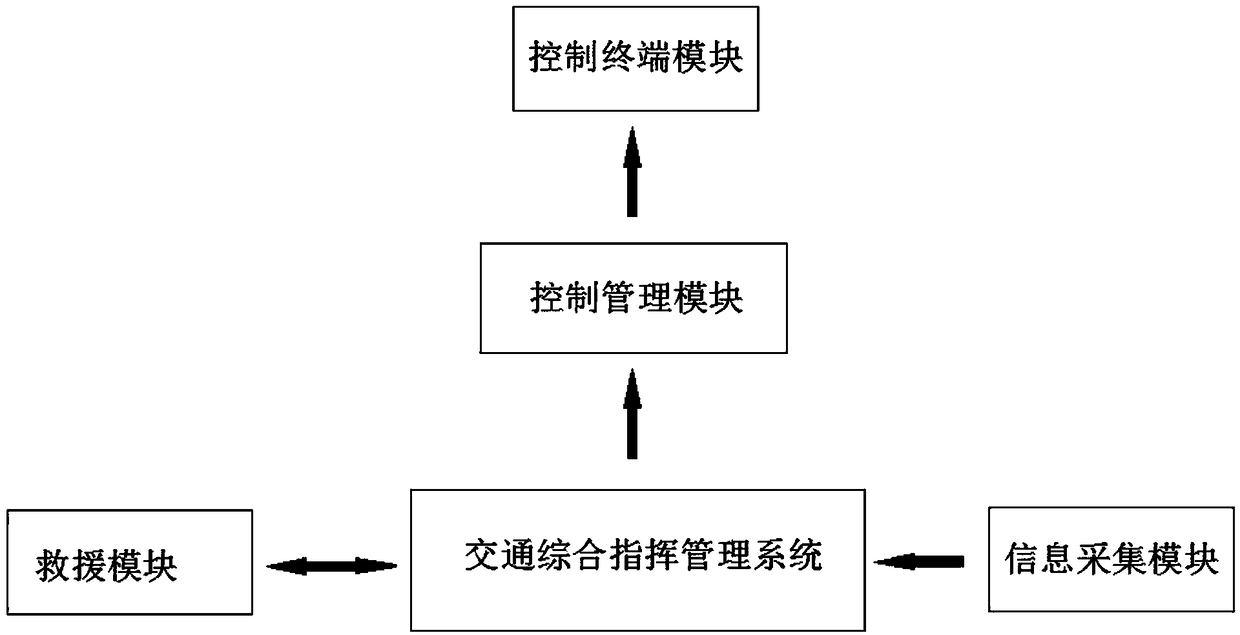
[0049] Such as figure 1 Shown, a kind of network security system based on big data, it comprises comprehensive traffic management system, information collection module, control management module, control terminal module and rescue module; The traffic information on the corresponding road is transmitted to the comprehensive traffic management system; the comprehensive traffic management system controls the control terminal module located at the intersection of the corresponding road through the control management module; the control terminal module includes railings, traffic lights, broadcasters and screen; the railing is arranged at the crossing, corresponding to the traffic signal light information, and is used to control the flow of traffic; the broadcaster is used to broadcast the road conditions ahead; the screen displays the road conditions ahead in text form Play; the screen and the broadcaster will forecast the vehicles passing the intersection at the accident site, rem...
Embodiment 2
[0055] A method for using a network security system based on big data, adopting a network security system based on big data described in Embodiment 1, the specific operation steps of the method are described below:
[0056] a. adopt a kind of network security system based on big data described in claim 1, the information collection module will monitor the traffic information on the intersection corresponding road and deliver to the comprehensive traffic management system, and the comprehensive traffic management system will receive from the information collection The pass information of the module is screened and parsed.
[0057] b. The comprehensive traffic management system controls the control terminal module located at the corresponding road intersection through the control management module, and specifically controls the traffic status of the railings and the display status and display duration of the red street lights according to the traffic information such as the average...
Embodiment 3
[0059] A method for using a network security system based on big data, using the network security system based on big data described in Embodiment 1, the specific operation steps of the cooperation between the rescue module and the integrated traffic management system will be described below :
[0060] A method for using a network security system based on big data, the steps of which are:
[0061] A. The network security system also includes a rescue module and a rescue module; after the traffic information received from the information collection module is screened and analyzed by the comprehensive traffic management system, the traffic conditions of the accident situation and the roads around the accident are analyzed. The data information is passed to the rescue module.
[0062] B. The rescue module feeds back the driving route of the rescue vehicle to the comprehensive traffic management system; the comprehensive traffic management system controls the control terminal mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com