Network data protection system
A protection system and network data technology, which is applied in the field of network security, can solve the problems of easy leakage or tampering of data information, achieve the effect of preventing malicious tampering, expanding the scope of monitoring and alarming, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
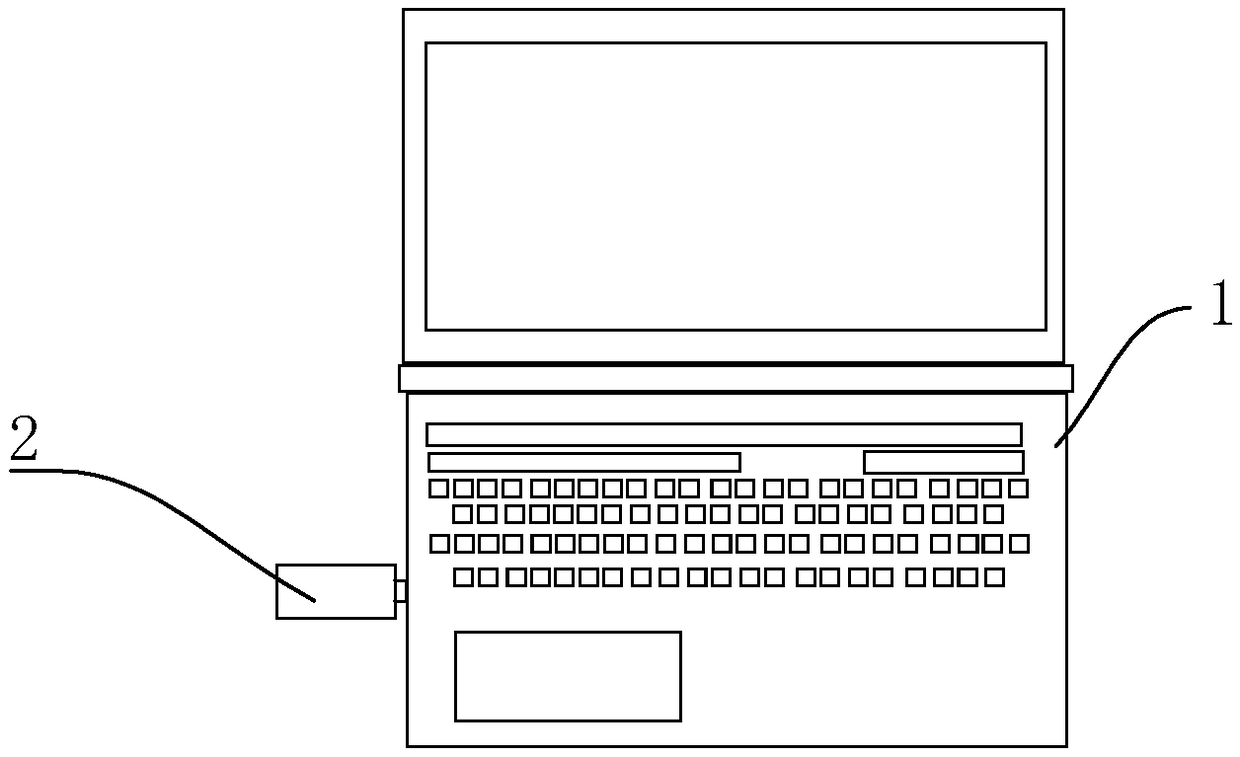
[0047] Such as figure 1As shown, this embodiment provides a network data protection system, including hardware and software, and the hardware includes several clients 1 . Client 1 accesses a biometric device and / or a password device, verifies the identity and position of the person, and authorizes the user to operate. In addition, an identity verification module 31 is also provided in the software system to verify the identity of the user who will log in when no external verification device is connected. In this way, one or more of the three methods can be selected for verification, so as to achieve the integration of people, terminal equipment, positions, and use rights.
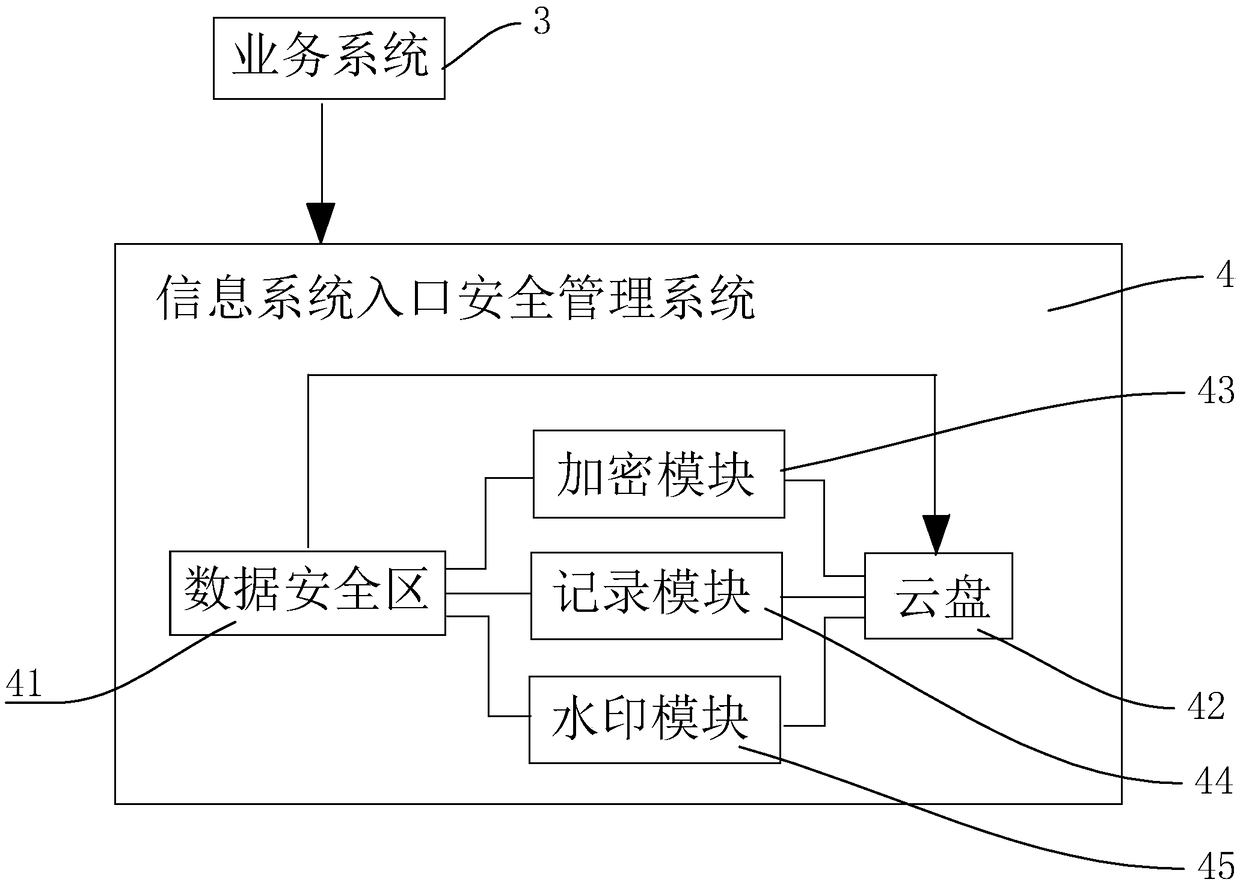
[0048] Such as figure 2 As shown, the software is installed on each client 1, and the software includes an information system entrance security management system 4 and a business system 3. Information system entrance security management system 4 receives files from business system 3 .
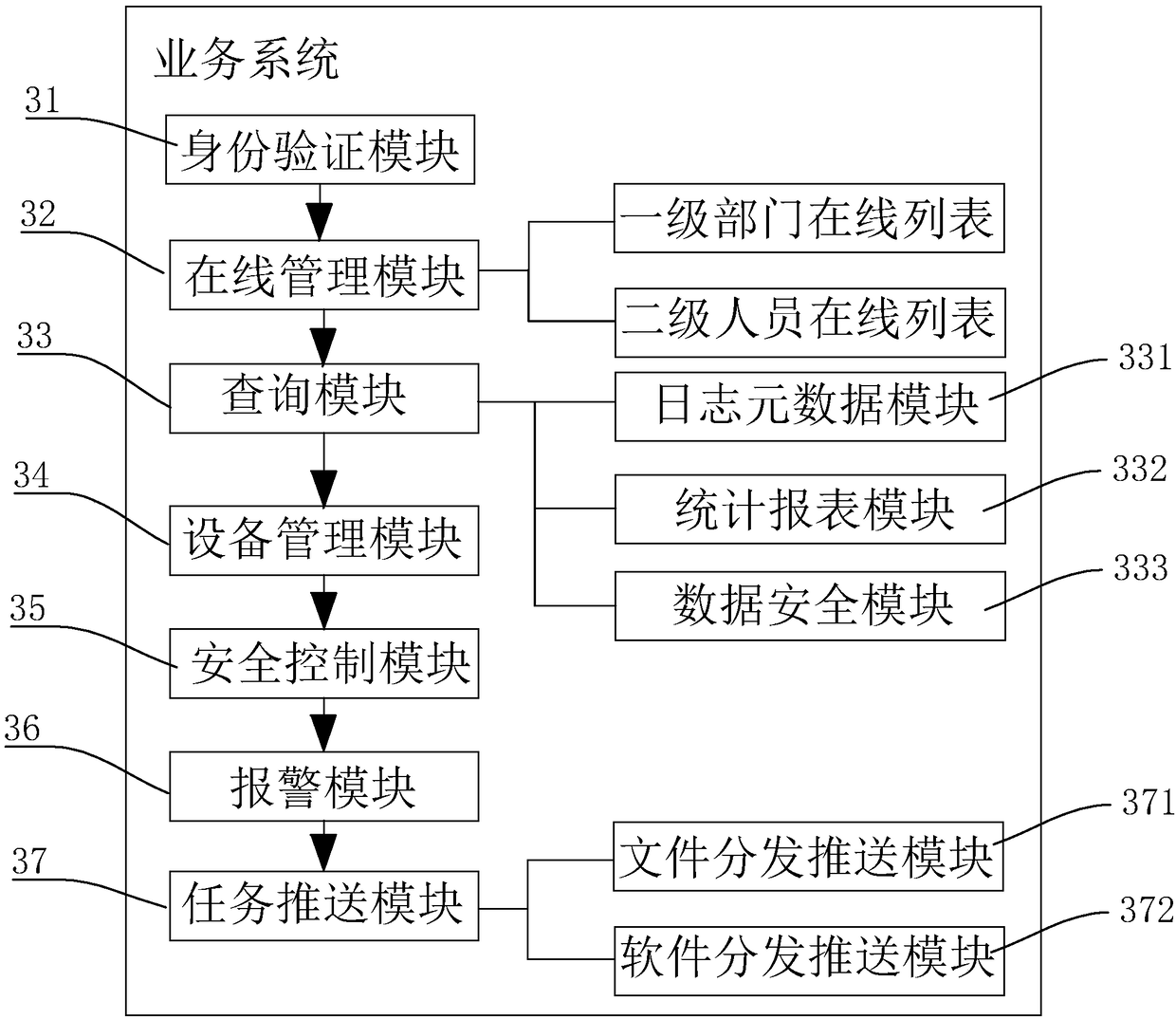
[0049] Such as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com