Automatic discovery and traceability system of open vSwitch illegal port operation in openstack platform
An automatic discovery and port technology, applied in the network field, can solve problems such as inability to connect and communicate remotely, illegally changing port configuration, and cloud network administrators being unable to perceive network changes in the first place
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
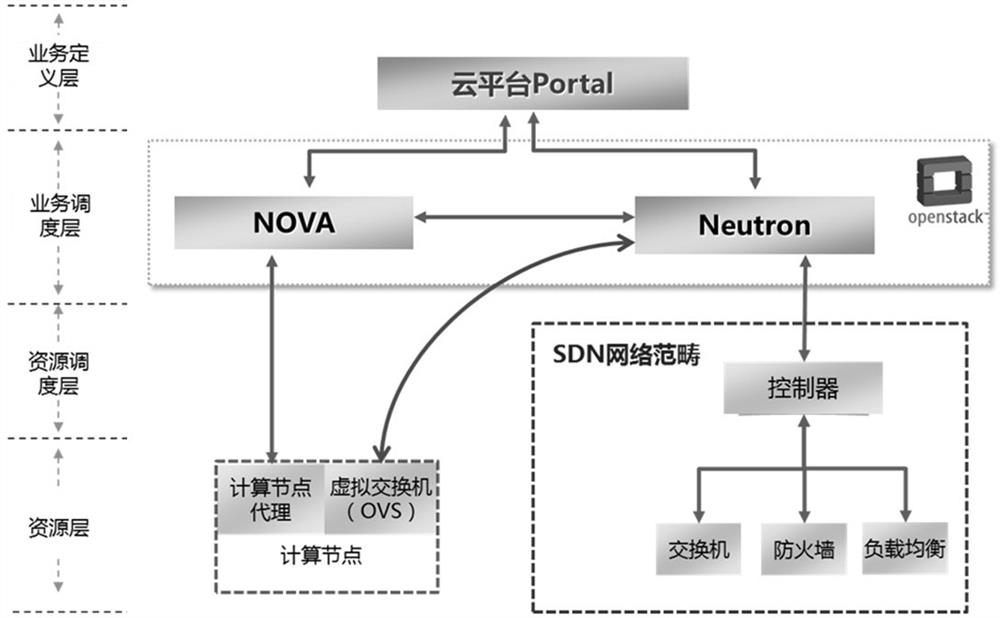
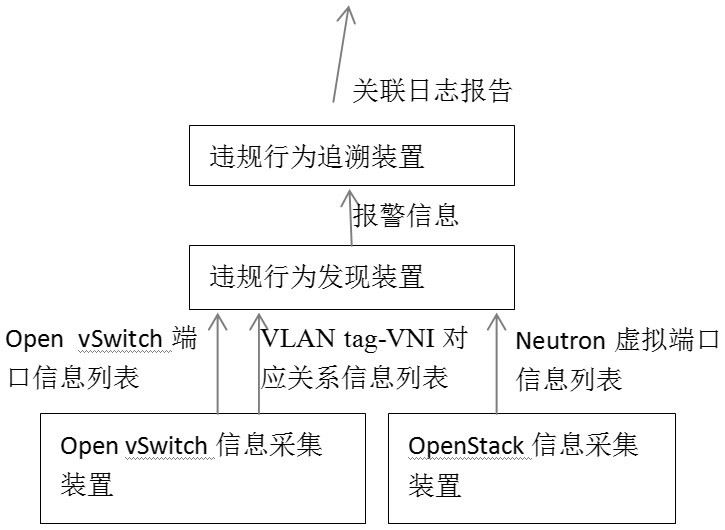
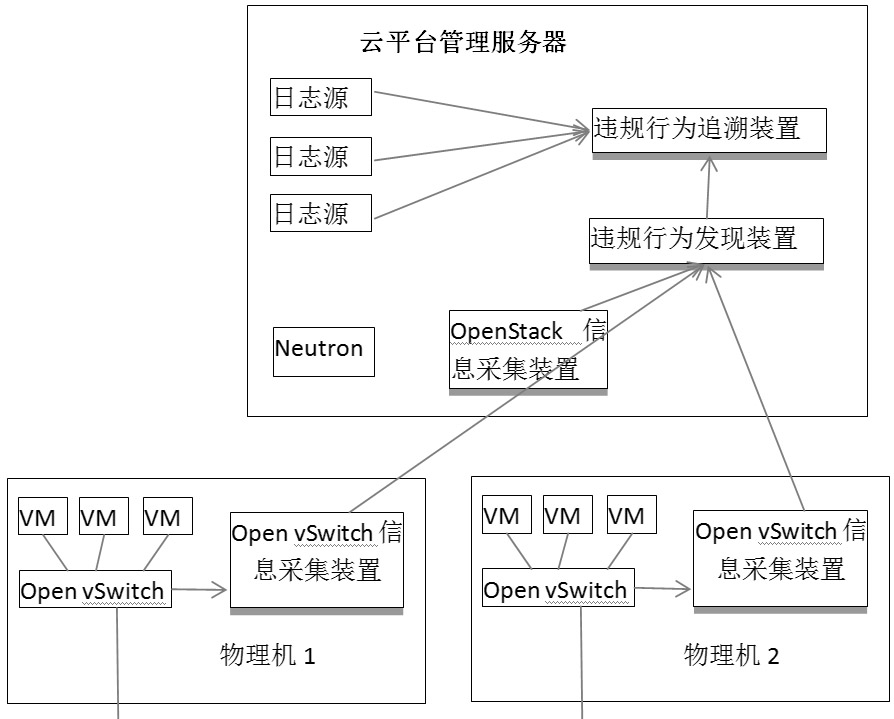
[0056] as attached image 3 As shown, the present invention is composed of an Open vSwitch information collection device, an OpenStack information collection device, a violation behavior discovery device, and a violation behavior tracing device. In specific implementation, they can all be implemented in the form of software. The OpenvSwitch information collection device is installed on each physical machine of the cloud platform, and the OpenStack information collection device, violation discovery device, and violation tracing device are installed on a cloud platform management server.
[0057] As a software running on all physical machines, the Open vSwitch information collection device can be automatically invoked and executed by using the timing mechanism of the physical machine operating system, for example, by using the cron service on Linux. The software calls the ovsdb-client tool, connects to the ovsdb-server, and obtains all the ports of the Open vSwitch on the curren...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com