A Joint Error Correction Security Method Based on Raptor Codes
A technique for keeping secrets and secreting information, which is applied in the field of information communication, can solve the problem of high decoding complexity, and achieve the effect of self-adaptive channel characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0036] The technical scheme that the present invention solves the problems of the technologies described above is:
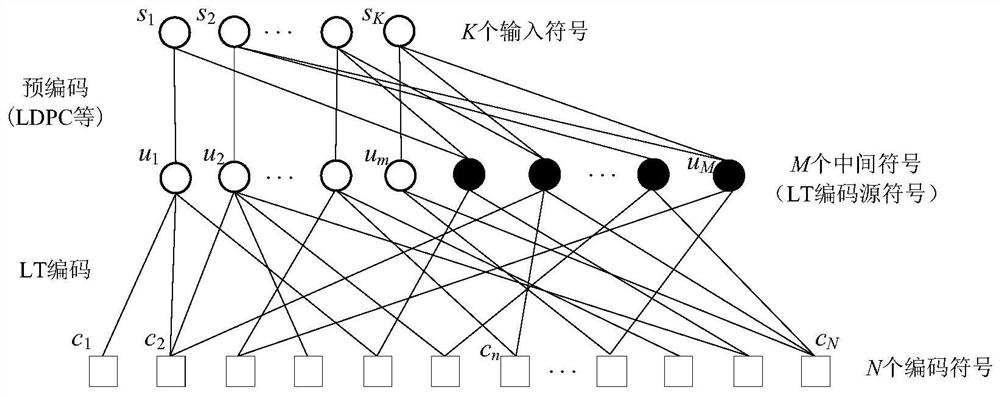
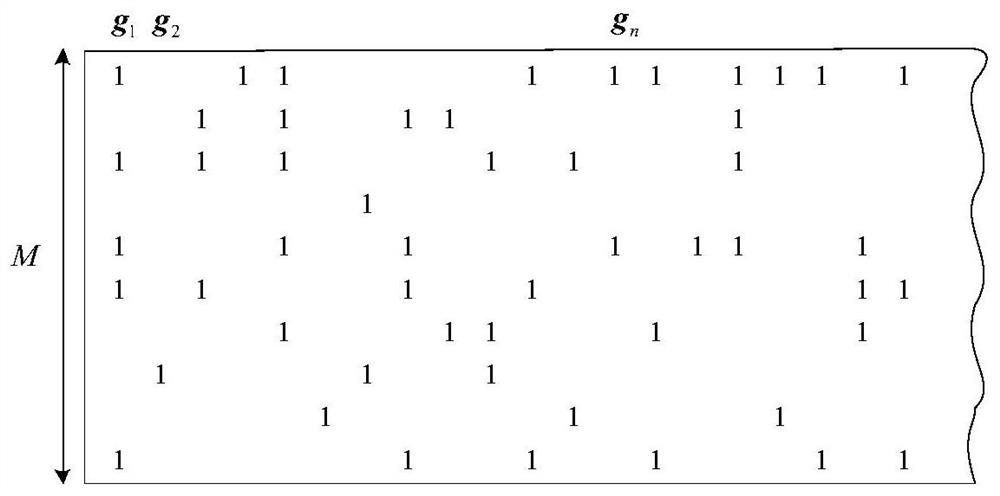
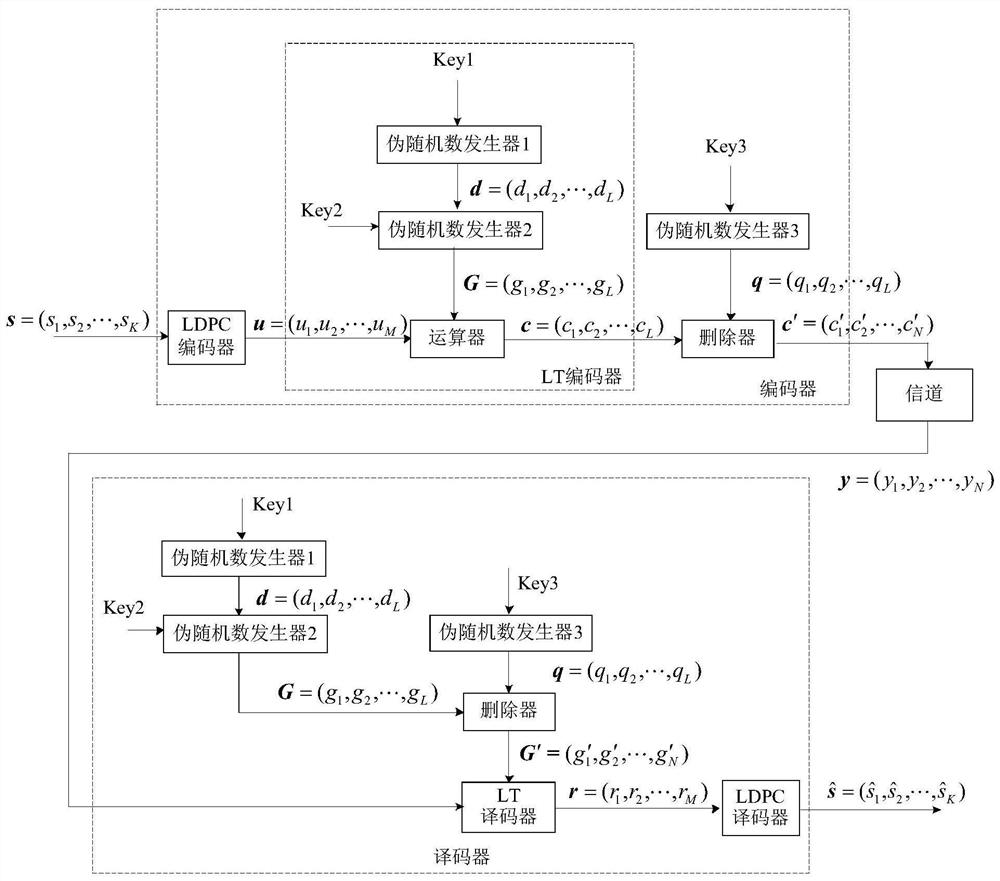
[0037] The present invention includes the encoding and decoding process of Raptor codes. The structure of the Raptor code (Tanner graph) is as follows figure 1 As shown, the precoding (i.e. the outer code) adopts the encoding of a fixed code rate (LDPC code is adopted in the present invention), the LT encoding (i.e. the inner code) is a rateless encoding, and the encoding process is random, and the final code rate, namely The length N of the codeword is determined according to the channel quality. The specific encoding process of Raptor code is as follows:
[0038] (1) K input symbols s ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com