Implementation method and system of sm2 encryption, signature and key exchange based on efficient modular multiplication
A technology of key exchange and implementation method, applied in the field of SM2 series algorithm implementation methods and systems, can solve problems such as low computational efficiency, and achieve the effect of resisting SPA analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
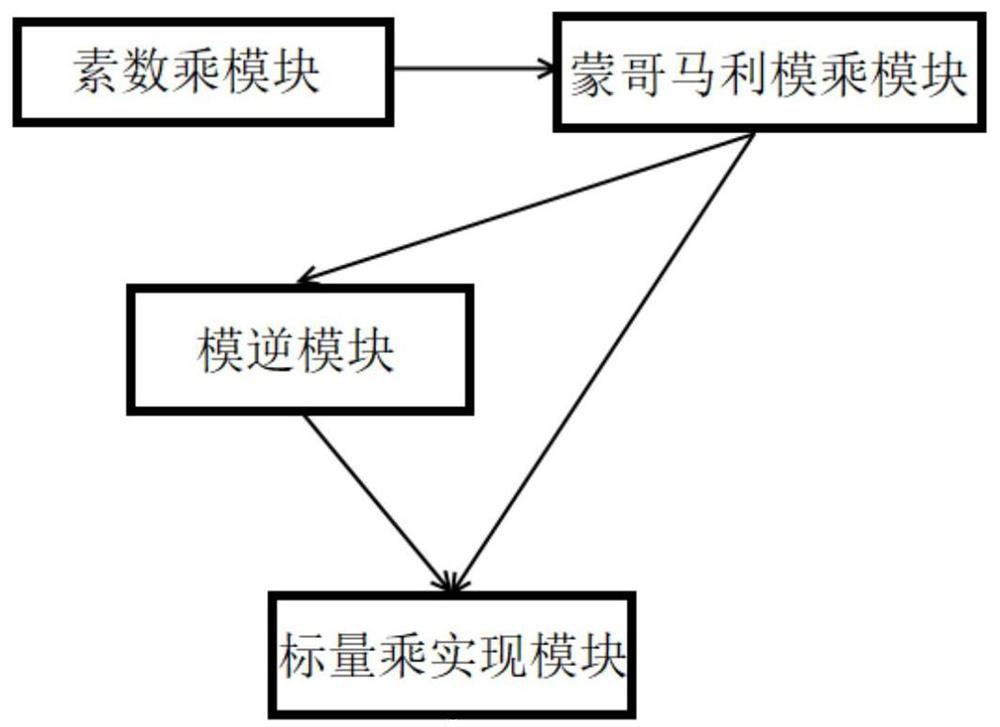
[0028] Such as figure 2 As shown, the present embodiment relates to the system that realizes the implementation method of SM2 encryption, signature and key exchange based on modular multiplication, including: prime number multiplication module, Montgomery modular multiplication module, modular inverse module, scalar multiplication realization module, wherein: prime number multiplication The module converts the multiplication operation involving SM2 prime numbers into shift and subtraction operations. The Montgomery modular multiplication module updates the calculation efficiency of the shift and subtraction operations according to the prime number characteristics and generates a fast realization of prime number multiplication and outputs it to the modular inverse module. The modular inverse module Carry out the modular inverse operation and generate a complete and efficient modular multiplication implementation and output it to the scalar multiplication implementation module. ...
Embodiment 2
[0035] This embodiment relates to an optimized key pair generation scheme for a digital currency hardware wallet, specifically comprising the following steps
[0036] Step 1. The user adds the seed of the key generation algorithm in the digital currency hardware wallet.
[0037] Step 2. Use the key derivation algorithm to generate the user public key as the user account address, and generate the user private key for signing the blockchain information based on the public key and the Montgomery Modular Multiplication method optimized for the prime number feature.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com