Safety device and anti-attack method thereof thereof
A security device and anti-attack technology, which is applied in the field of information security, can solve problems such as poor protection performance, and achieve good anti-attack, protection ability, good security, and good information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
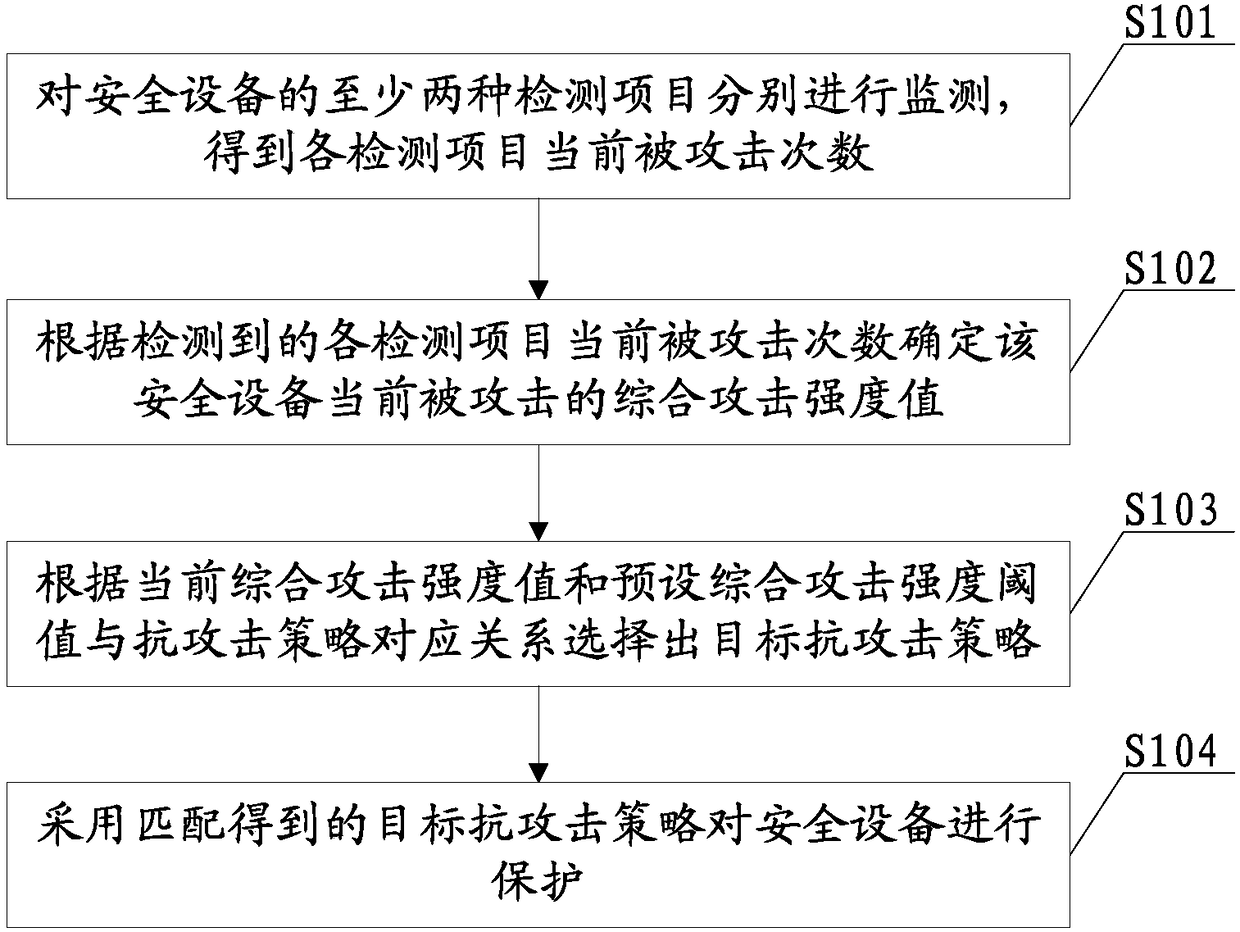
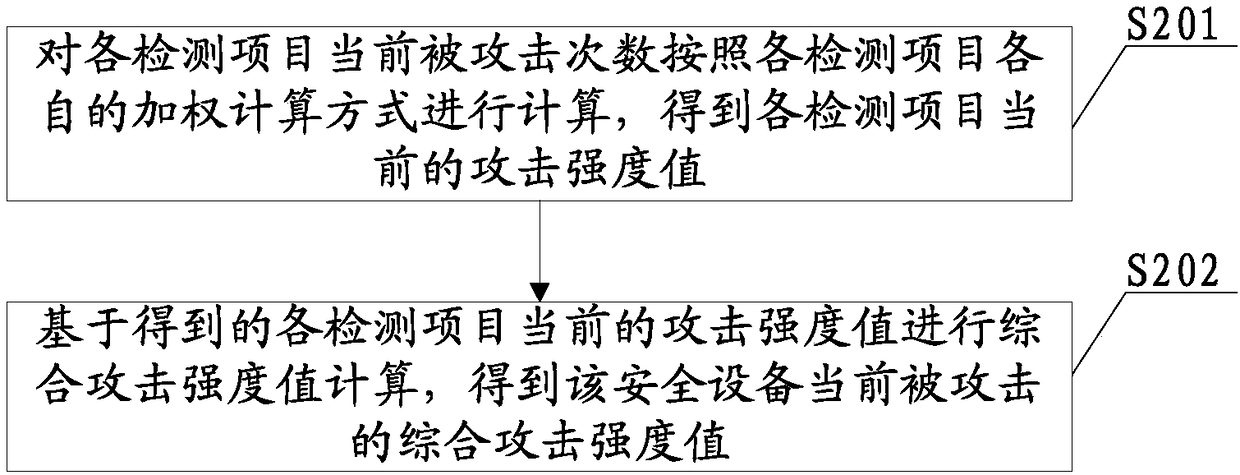
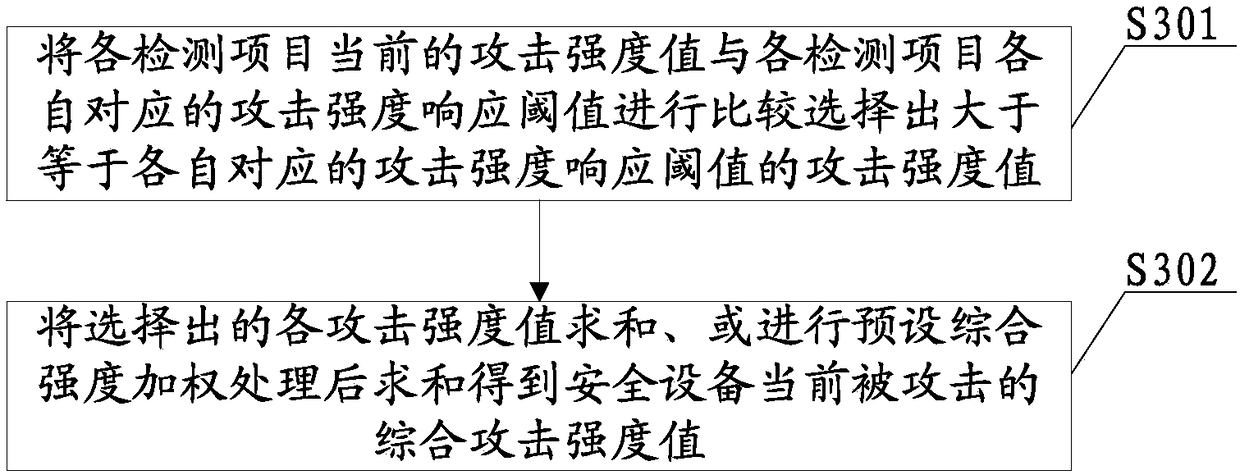
[0051]The security device anti-attack method provided in this embodiment first sets the corresponding relationship between the comprehensive attack strength threshold and the anti-attack strategy in advance. During the setting, different levels of anti-attack strategies can be set for different comprehensive attack strength thresholds, that is, different comprehensive attack strengths. . Then at least two detection items of the security equipment are monitored respectively to obtain the current number of attacks on each detection item; determine the current comprehensive attack strength value of the security equipment according to the current number of attacks on each detection item detected; and then according to the current comprehensive The attack strength value and the preset comprehensive attack strength threshold correspond to the anti-attack strategy, select the anti-attack strategy that matches the current comprehensive attack strength value as the target anti-attack st...
no. 2 example
[0077] This embodiment provides a security device, see Figure 4 shown, including:
[0078] The monitoring module 41 is configured to monitor at least two detection items of the safety equipment respectively.
[0079] A detection item of a security device may correspond to one type of attack, or may correspond to multiple types of attack. When the at least two detection items of the safety equipment are monitored separately, the safety equipment may be monitored in real time, or may be monitored according to a preset time rule.
[0080] It should be understood that in this embodiment, all detection items of the security device (that is, all items that may be attacked) may be monitored, and at least two of the detection items of the security device may be selectively monitored. Specific testing items can be flexibly set according to actual needs. For example, one of the implementation methods can detect all detection items, and set the corresponding weight value of each dete...
no. 3 example
[0102] In order to better understand the present invention, this embodiment is described in conjunction with a specific security device structure as an example.
[0103] see Image 6 As shown, the monitoring module 61 of the security device in this embodiment includes n monitoring units, namely monitoring unit 1...monitoring unit n; the statistical module 62 includes n counting units, namely counting unit 1...counting unit n; The weighted calculation unit of the processing module 63 comprises n weighting units, i.e. weighting unit 1 ... weighting unit n; its integrated processing unit comprises n primary judging units, i.e. primary judging unit 1 ... primary judging unit n, also includes a comprehensive Calculation unit; matching module 64 and execution module 65 have m anti-attack strategies, namely, anti-attack strategy 1 . . . anti-attack strategy m. The value of n in this embodiment can be determined according to the actual number of items detected by the security device;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com