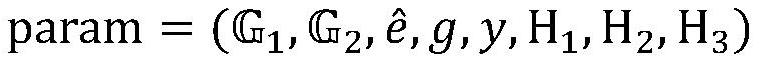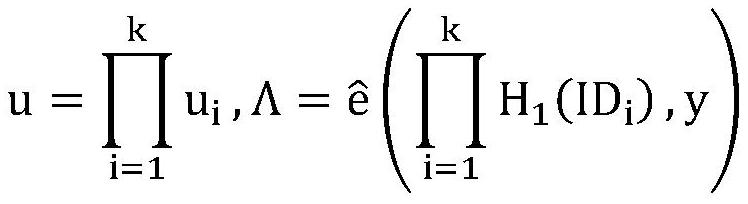A Privacy-Preserving Resource Allocation Method in Fog Computing
A technology for resource allocation and privacy protection, which is applied in the field of resource allocation to protect privacy and can solve problems such as metadata leakage from terminal devices.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
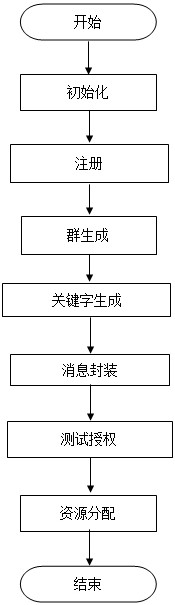
[0024] The privacy-protecting resource allocation method in fog computing of the present invention includes the following entities: a terminal device, a fog node, a mechanism for generating and distributing system parameters, that is, a trusted organization TA, an intelligent gateway, and a cloud server; the method includes the following steps:
[0025] (1) Initialization
[0026] Input a security parameter p, TA selects two cyclic multiplication groups whose order is a prime number q according to p and The generator of is g, and there is a bilinear map bilinear map satisfy the following properties:
[0027] Bilinear: for any is a quotient group of order q with established;
[0028] Non-degenerate: present satisfy not equal to 1;
[0029] Computability: There exists an efficient algorithm for can be calculated
[0030] TA randomly selects as the master key of the system; compute y=g η ; Select the cryptographic hash function H, public system parame...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com