Encrypted stream identification method and device
An identification method and technology for encrypted flow, applied in the field of identification method and device of encrypted flow, can solve the problems of long time identification of encrypted flow and increased harm to users, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
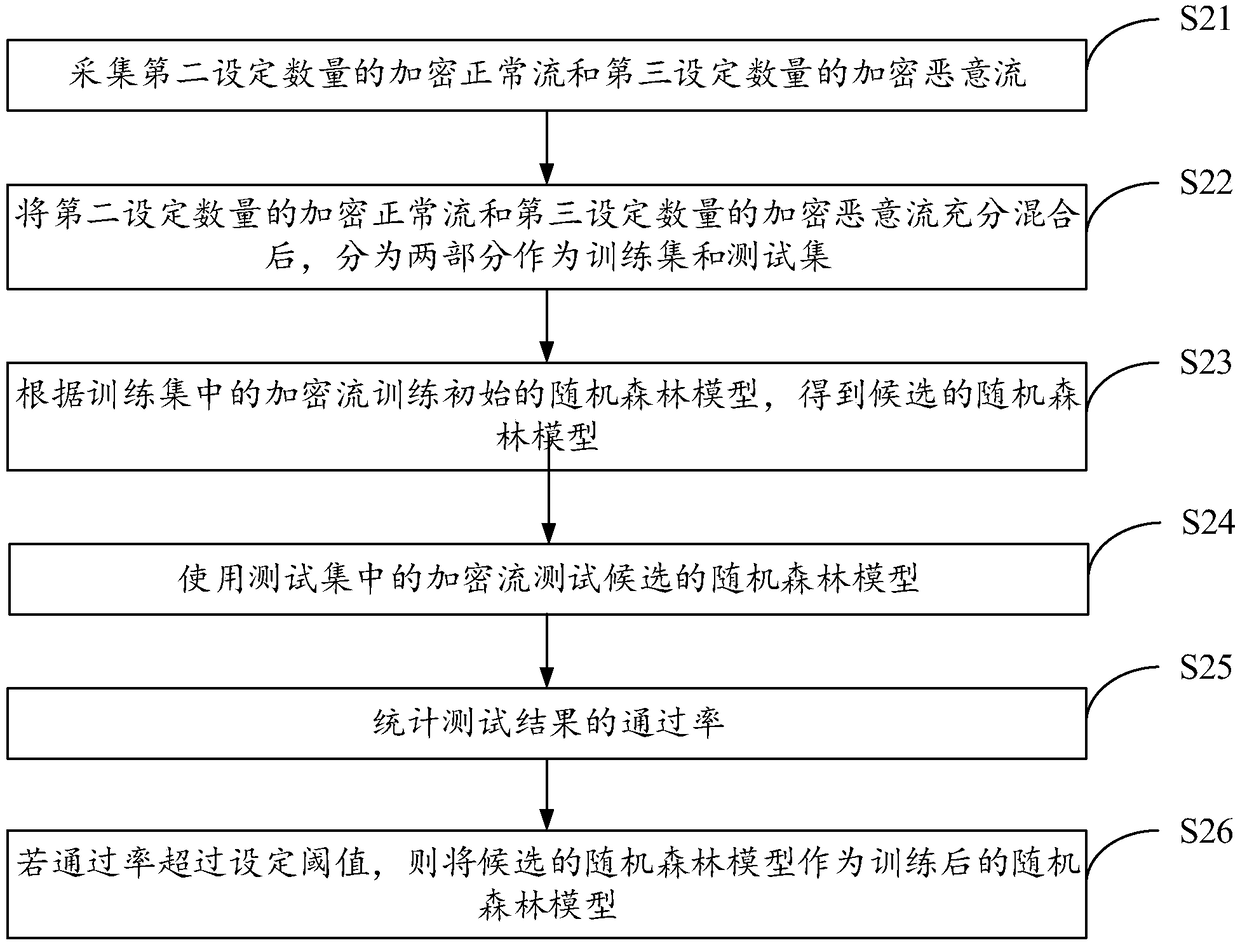
[0077] In view of the time-consuming identification of encrypted streams in the prior art and the potential harm to users, the embodiment of the present invention provides an identification method of encrypted streams, which is applied in the server. The method needs to use training The final random forest model can be obtained by training the initial random forest model. Therefore, it can be divided into the training phase and the use phase of the random forest model. The following two phases are introduced respectively.
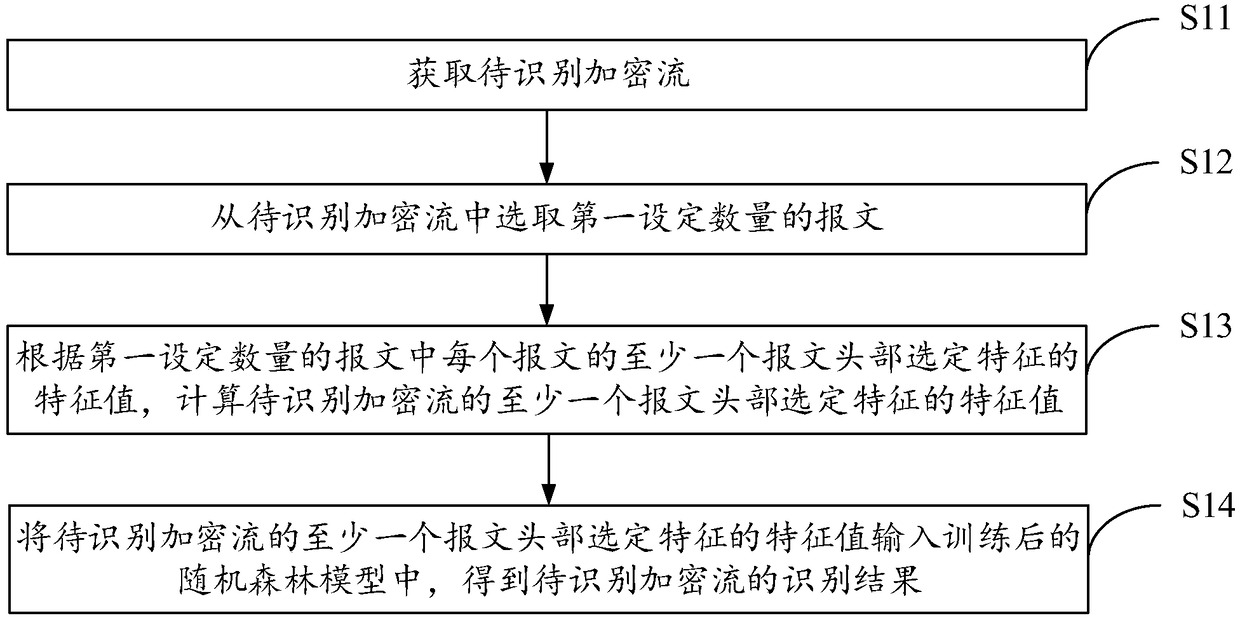
[0078] Firstly, it introduces the flow of the identification method of the encrypted stream in the stage of using the trained random forest model as follows: figure 1 As shown, the execution steps are as follows:
[0079] S11: Obtain the encrypted stream to be identified.
[0080] S12: Select a first set number of packets from the encrypted stream to be identified.
[0081] Usually, a to-be-identified encrypted flow will contain a lot of messages, it is n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com