Password protection method applied to plaintext protocol proxy in operation and maintenance auditing system
A password protection and protocol technology, applied in the field of password protection of plaintext protocol agents, can solve problems such as uncontrollability, and achieve the effect of protecting passwords, protecting system security, and not changing operating habits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
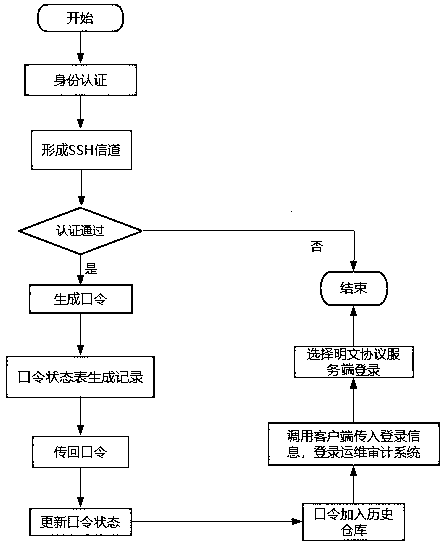
[0046] The present invention is realized through the following technical solutions, as Figure 1-Figure 3 As shown, a password protection method applied to plaintext protocol agents in the operation and maintenance audit system, the operation and maintenance device login terminal initiates the identity authentication of the operation and maintenance audit system user to the operation and maintenance device server through the SSH encryption protocol, and establishes an SSH encrypted channel ;The operation and maintenance device server generates a one-time password and returns it to the operation and maintenance device login terminal. Clear text protocol server.
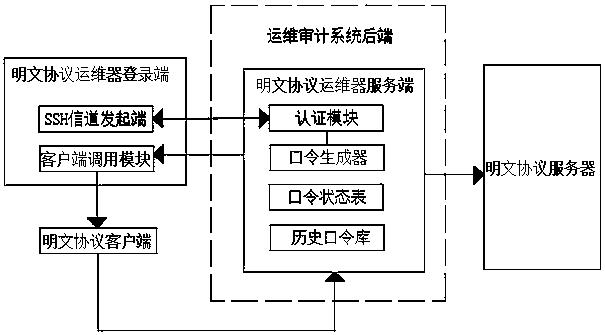
[0047] It should be noted that, through the above improvements, the present invention discloses a password protection method applied to plaintext protocol agents in the operation and maintenance audit system. The present invention includes a plaintext protocol operation and maintenance device login terminal and a plain...
Embodiment 2
[0052] This embodiment is further optimized on the basis of the above embodiments, such as Figure 1-Figure 3 As shown, it specifically includes the following steps:
[0053] Step F1: The operation and maintenance device login terminal uses the SSH encryption protocol to initiate a user identity authentication request to the operation and maintenance device server, and establishes an SSH encrypted channel;
[0054] Step F2: The password generator at the server side of the operation and maintenance device generates a one-time password, and transmits the one-time password to the login terminal of the operation and maintenance device;
[0055] Step F3: The operation and maintenance device login terminal starts the client calling module, calls the plaintext protocol client according to the plaintext protocol selected by the user in the protocol option, and transmits the user login information to the plaintext protocol client;
[0056] Step F4: Log in to the plaintext protocol ope...
Embodiment 3
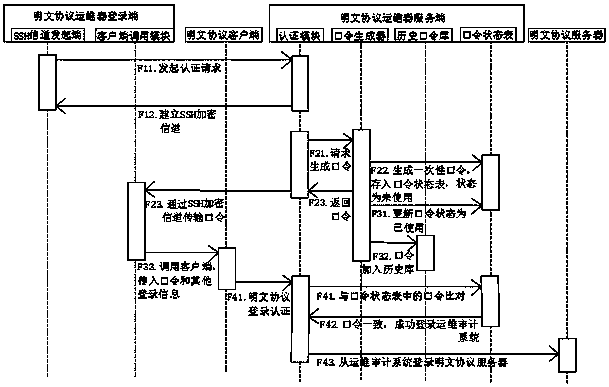
[0062] This embodiment is further optimized on the basis of the above embodiments, such as Figure 1-Figure 3 As shown, the step F1 specifically includes the following steps:
[0063] Step F11: The operation and maintenance device login terminal uses the SSH encryption protocol to initiate a user identity authentication request to the operation and maintenance device server;
[0064] Step F12: Between the authentication module of the operation and maintenance device server and the operation and maintenance device login terminal, the two parties negotiate to establish an SSH encrypted channel;
[0065] Step F13: The operation and maintenance device login terminal transmits the IP and user identity information of the operation and maintenance audit system to the operation and maintenance device server through the SSH encrypted channel;
[0066] Step F14: The operation and maintenance device server receives the user identity information and performs authentication; if the identi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com