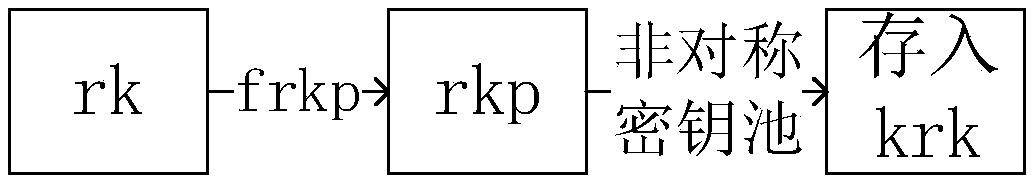Anti-quantum computing smart home cloud storage method and system based on key card
A smart home, quantum computing technology, applied in transmission systems, digital transmission systems, public keys for secure communications, etc., can solve problems such as malware or malicious operation theft, paralysis of smart home solutions, and the danger of cloud servers. The effect of reducing risk, reducing the risk of malware or malicious action stealing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
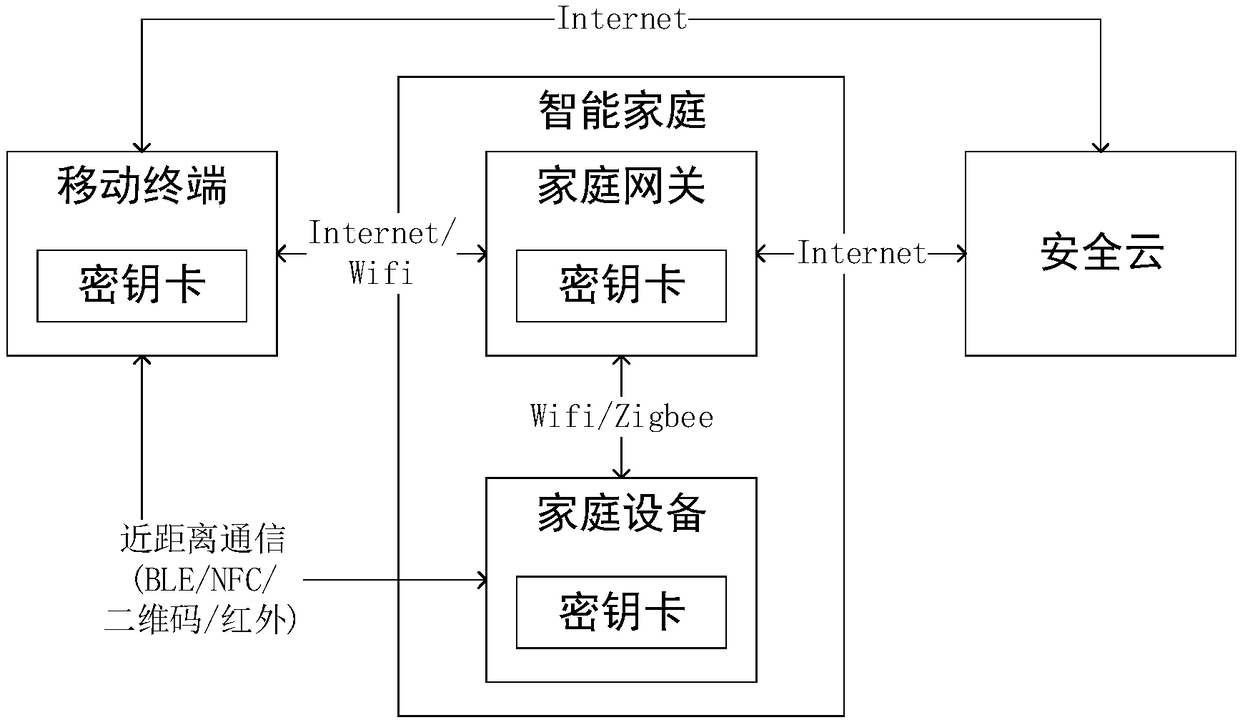
[0065] In this embodiment, the smart home component uploads files to the security cloud, and the uploading of files to the security cloud by the smart home component is divided into the following four situations, the mobile terminal M uploads the file to the security cloud, the home gateway S uploads the file to the security cloud, and the high-performance home device CH uploads files to the secure cloud and low-performance home device CL uploads files to the secure cloud.
[0066] Case 1: The mobile terminal uploads files to the secure cloud.
[0067] Step 1.1.1: The mobile terminal encrypts files.
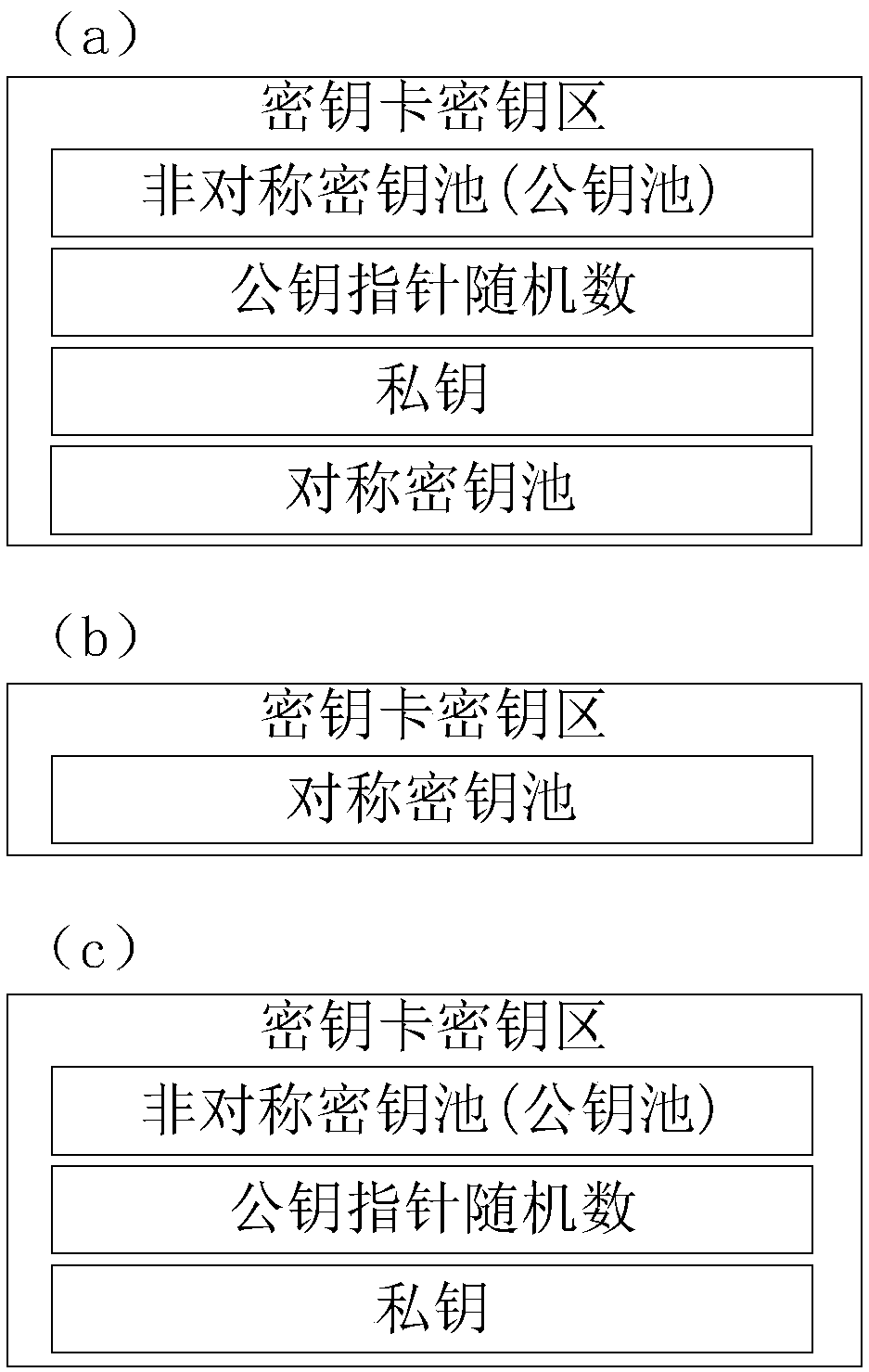
[0068] Mobile terminal M generates file encryption random number rf according to the true random number generator in the matching key card, uses rf to encrypt the file to be uploaded and uses its own public key to encrypt rf.
[0069] Step 1.1.2: The mobile terminal shares files with other smart home components.
[0070] Step 1.1.2.1: If it needs to be shared with some other mo...
Embodiment 2
[0104] In this embodiment, the smart home component downloads files from the security cloud, and the smart home component downloads files from the security cloud into the following four situations. The mobile terminal M downloads files from the security cloud, and the home gateway S downloads files from the security cloud. , the high-performance home device CH downloads files from the secure cloud and the low-performance home device CL downloads files from the secure cloud.
[0105] Case 1: The mobile terminal downloads files from the secure cloud.
[0106] After the mobile terminal M obtains the rf encrypted with M's public key and the encrypted file from the security cloud SS, it decrypts the rf with its own private key and decrypts the file with the rf.
[0107] Case 2: The home gateway downloads files from the secure cloud.
[0108] After the home gateway S obtains the rf encrypted with S's public key and the encrypted file from the security cloud SS, it decrypts the rf w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com