Network security situation evaluation method based on CS and improved BP neural network
A BP neural network and network security technology, which is applied in the field of network security situation assessment based on CS and improved BP neural network, can solve the problems of one-sidedness of assessment results, prone to shocks, large time and space overhead, etc., to improve accuracy and practicability , speed up the convergence speed, and reduce the effect of subjective influence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] Embodiment 1, a network security situation assessment method based on CS and improved BP neural network, including the following four steps,
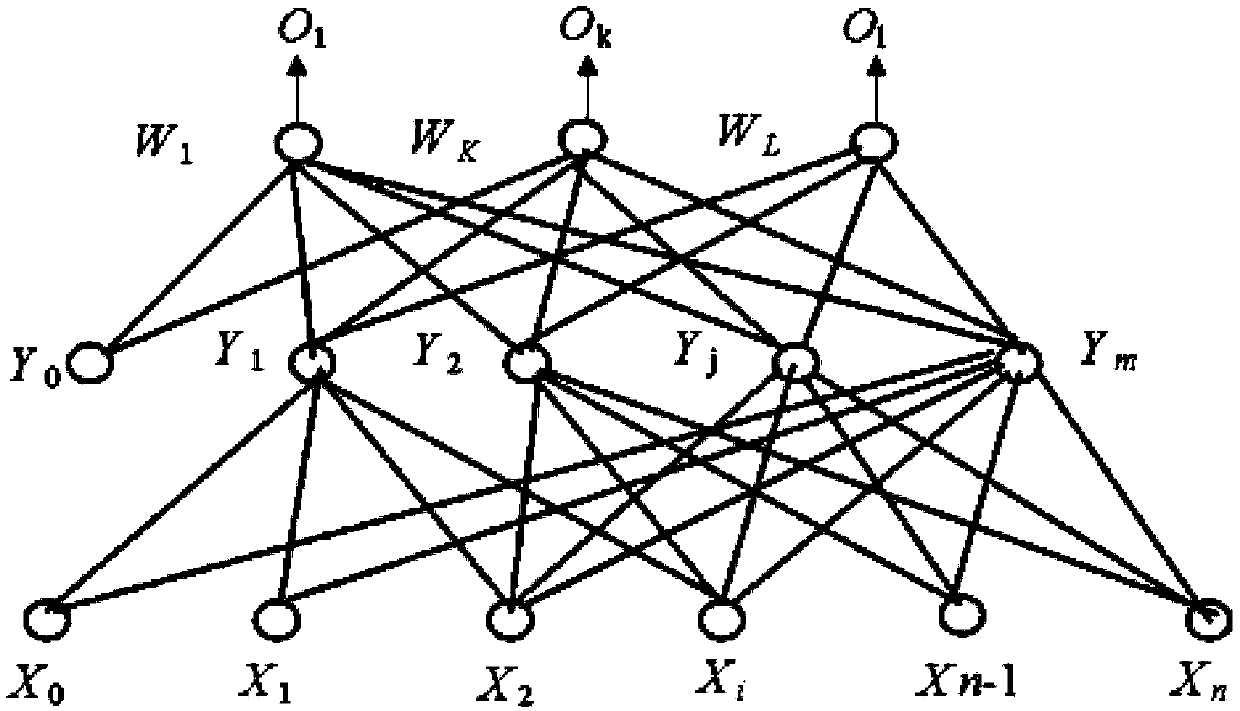
[0053] S1. Obtain elements of the network security situation, form a training sample set and a test sample set, and determine the structure of the BP neural network;
[0054] S2, using the cuckoo search (CS) algorithm to find the optimal initial weight and threshold;
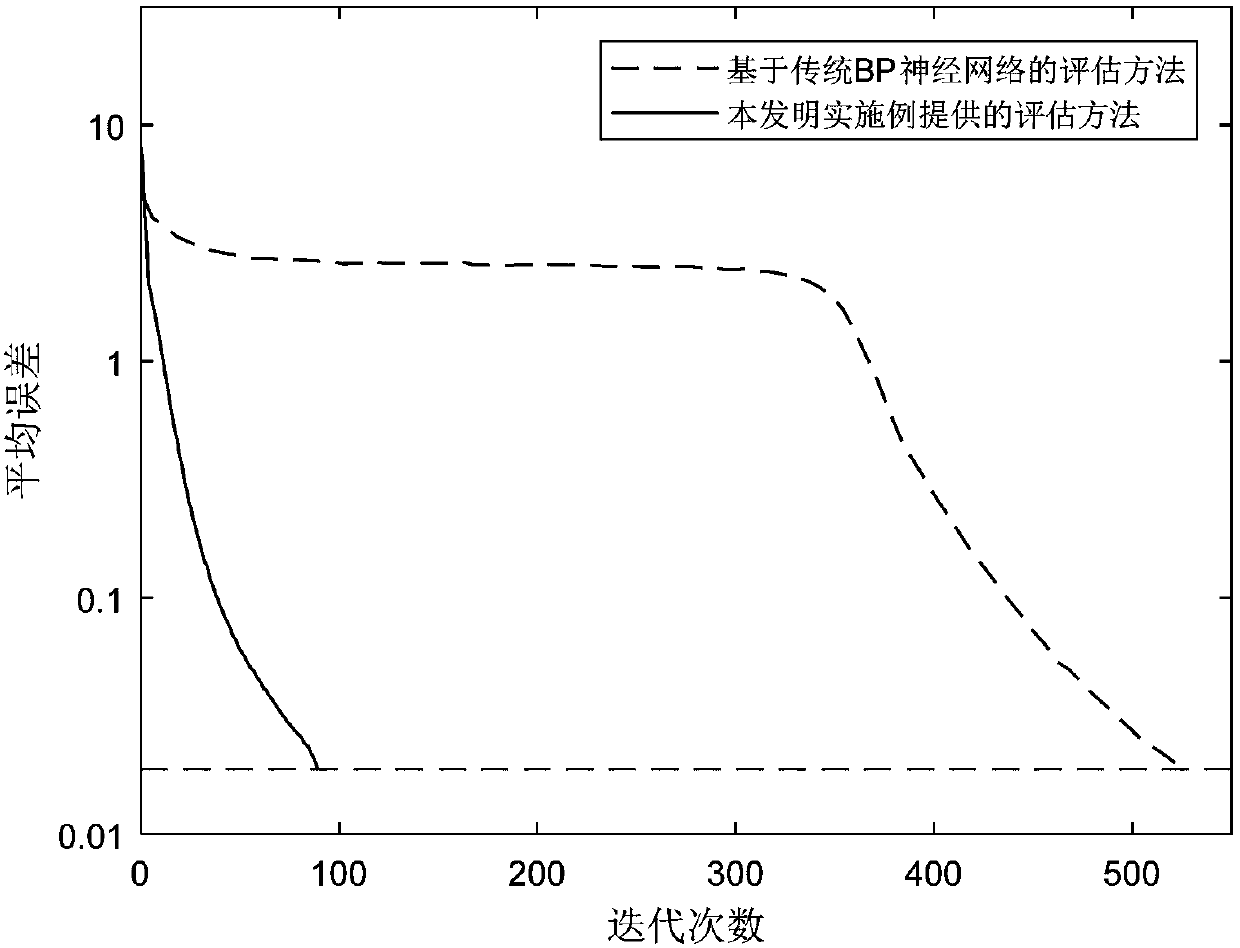
[0055] S3. In view of the shortcomings of the traditional BP neural network such as slow convergence speed, prone to oscillation and falling into local minimum, the momentum factor and steepness factor are introduced to improve the BP neural network;
[0056] S4. Train the improved BP neural network, and use the trained network for network security situation assessment to obtain the final situation value and security level.
Embodiment 2
[0057] Embodiment 2, on the basis of Embodiment 1, the step S1 specifically includes:
[0058] S11. Obtain elements of the network security situation to form a training sample set and a test sample set. The evaluation data sources mainly come from three categories: based on system configuration information, based on system operation information and based on network traffic information. The first type of data source refers to network design and configuration status, such as network topology, installation and configuration of service software, and system vulnerabilities; the second type of data source refers to the system operation when the network system is attacked, mainly from The third type of data source mainly refers to various traffic conditions of network instant communication, which can be monitored and obtained through special software. According to the current network status and the actual needs of the indicator system, the present invention selects Netflow data, Snor...
Embodiment 3
[0067] Embodiment 3, on the basis of Embodiment 1, the step S2 specifically includes:
[0068] The initial weights and thresholds of the BP neural network are randomly assigned, so its training time is generally longer, and the weights and thresholds obtained through training may not be optimal, so the present invention uses the cuckoo (CS) algorithm to find the optimal The weight and threshold of , the specific steps are as follows:
[0069] S21, initialize the population, randomly generate n cuckoos according to the characteristics of the neural network weight and threshold To encode n cuckoos, the encoding method adopts floating-point number encoding. The floating-point number encoding is intuitive and has the characteristics of easy control of encoding length, high encoding accuracy and strong search ability in large spaces, which can reduce computational complexity. Therefore, the present invention adopts floating-point number coding. According to the design structure ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com