Quantum database access control and two-way identity authentication method based on bell state
A two-way identity authentication and identity authentication technology, applied in the field of Bell state quantum database access control and two-way identity authentication, can solve the problems of lack of equivalence and equality of identity authentication protocols, and achieve resistance to external attacks and good noise tolerance performance. , low-complexity effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
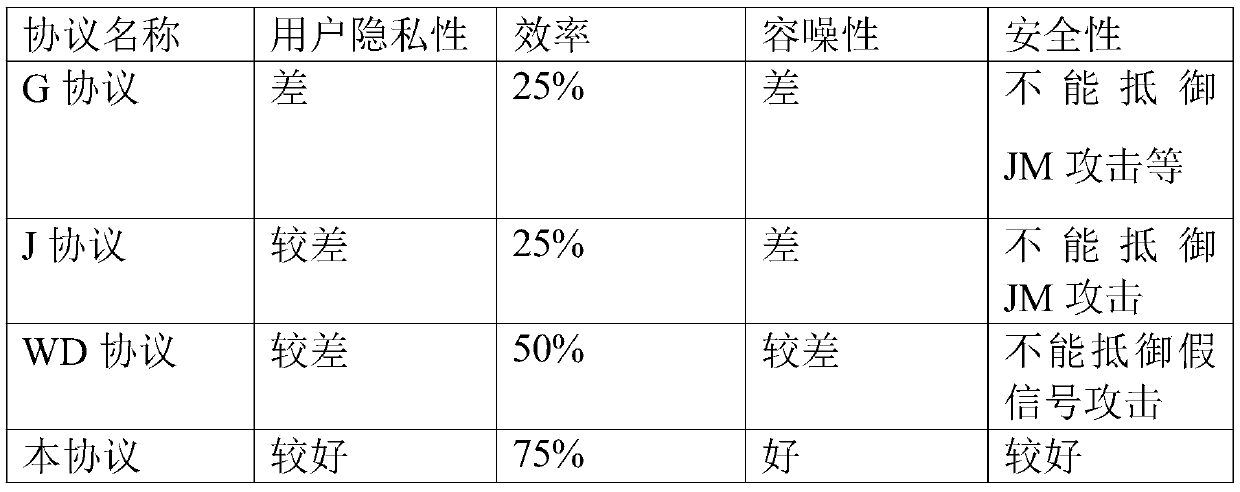
Method used
Image
Examples
specific example
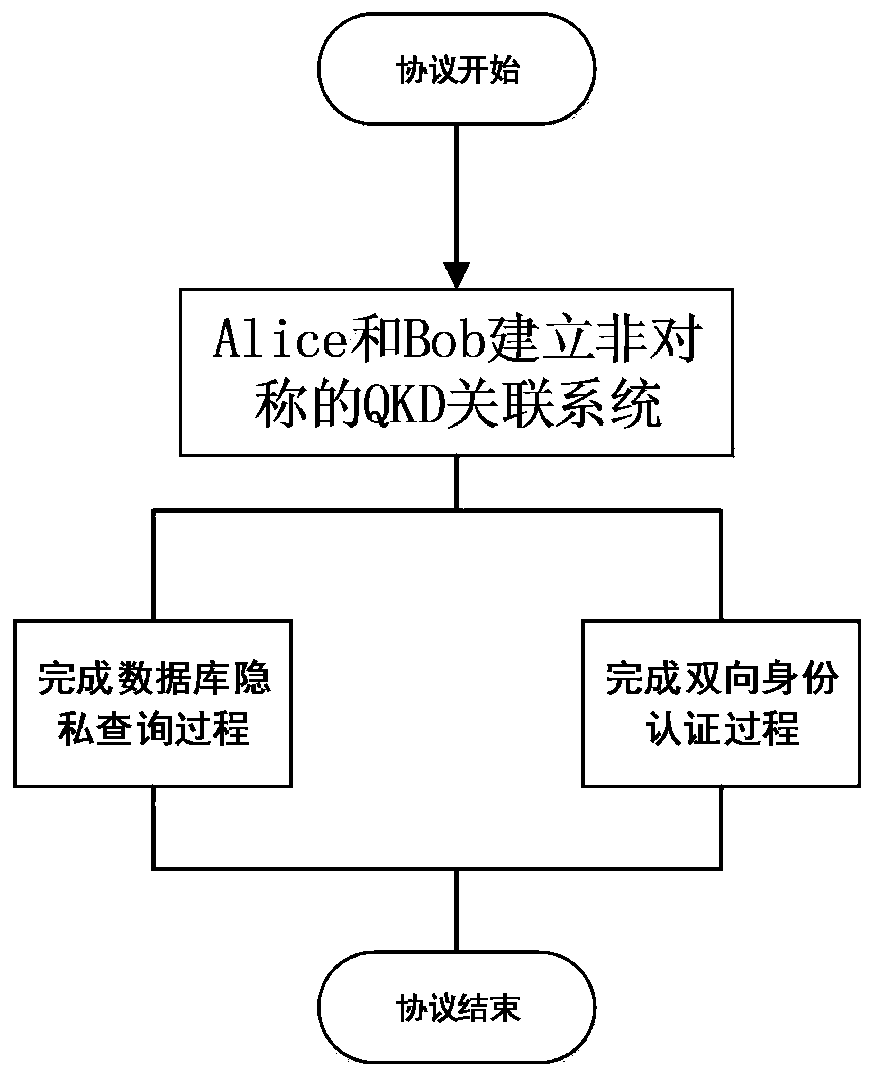
[0055] According to the protocol description of the present invention, when the first communication party and the second communication party establish an asymmetric QKD association, the first communication party knows 1 / 4 of the entire key key, while the second communication party knows all of it. A specific example of QPQ is as follows:
[0056] The second communication party encrypts the entire database using a one-time pad (OTP). At this time, if the key string in the hands of the first communication party is the sixth key, and she wants to query the content of the database at the eleventh position, the first communication party A conversion value s=11-6=5 is published. The second communication party of the database manufacturer performs an XOR operation on the key in hand according to the value of s, and encrypts the database with the generated new key. At this time, the first communication party can query the corresponding content of the database according to the key val...
Embodiment
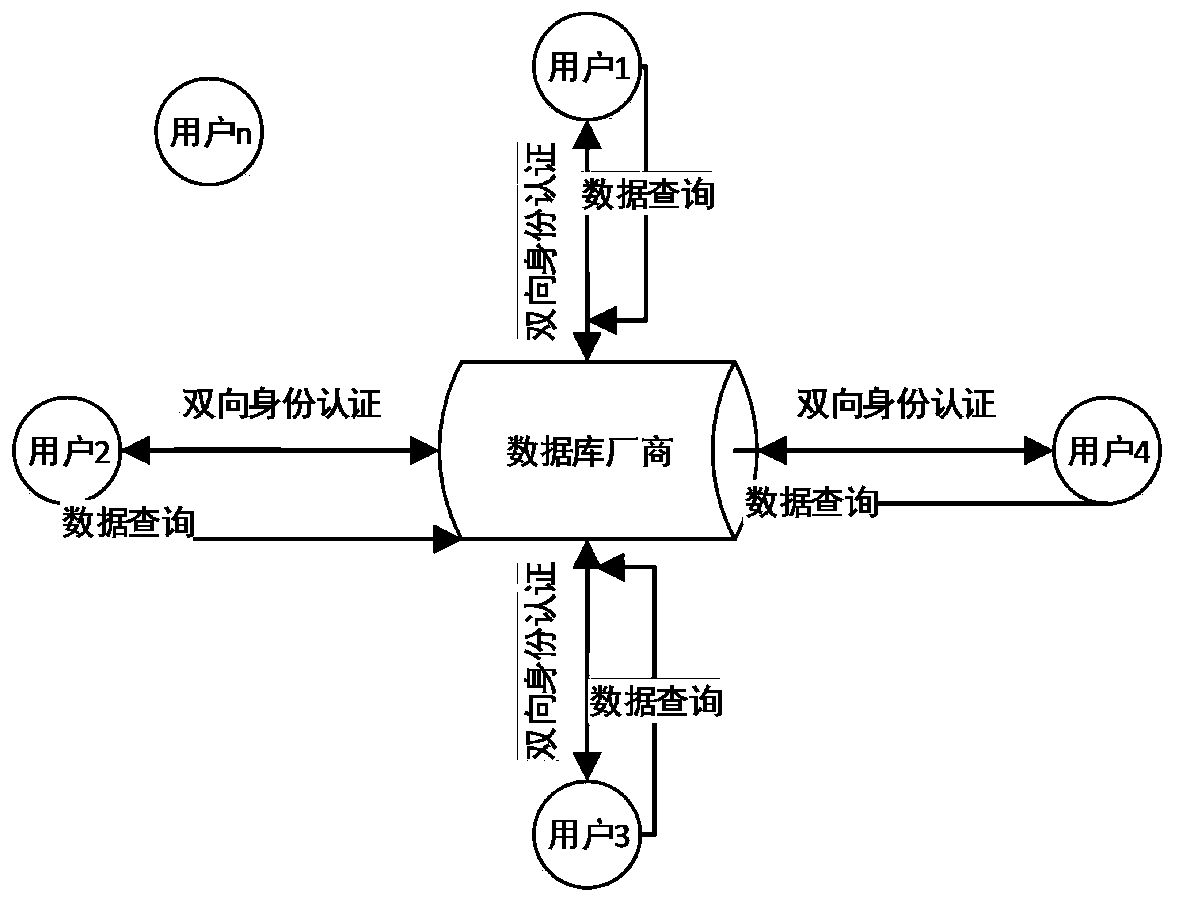
[0099] Such as figure 2As shown, the database manufacturer Bob provides data resources, and users 1 to n can query the database. The usage scenarios of this agreement are described in detail below:
[0100] Assume that user 1 (set as Alice) requests to query the data content in the database manufacturer Bob, and the query process of other users is similar.
[0101] First, Alice initiates a query request, and Alice prepares 2N pairs of Bell state particles to Bob. By using this protocol, Alice and Bob establish an asymmetric QKD connection. At this time, Bob and Alice use the contents of the two-way identity authentication part of the protocol to perform Two-way authentication. After confirming that both parties are legitimate communication participants, execute this agreement again to re-establish the asymmetric QKD relationship. After XOR and other operation steps, Alice can only query the data content she purchased. At this point, the database query process is also comp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com