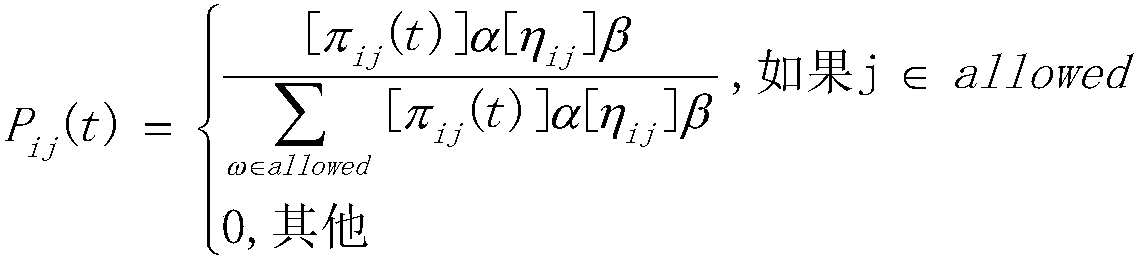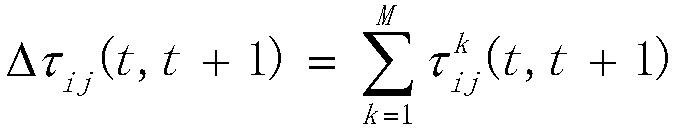Ant colony clustering intrusion detection method based on transduction support vector machine
A support vector machine and intrusion detection technology, applied in the direction of instruments, calculation models, electrical components, etc., can solve the problems of difficult detection of attacks and difficulties in obtaining training data, and achieve low false negative rate, good detection effect, and high detection accuracy rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
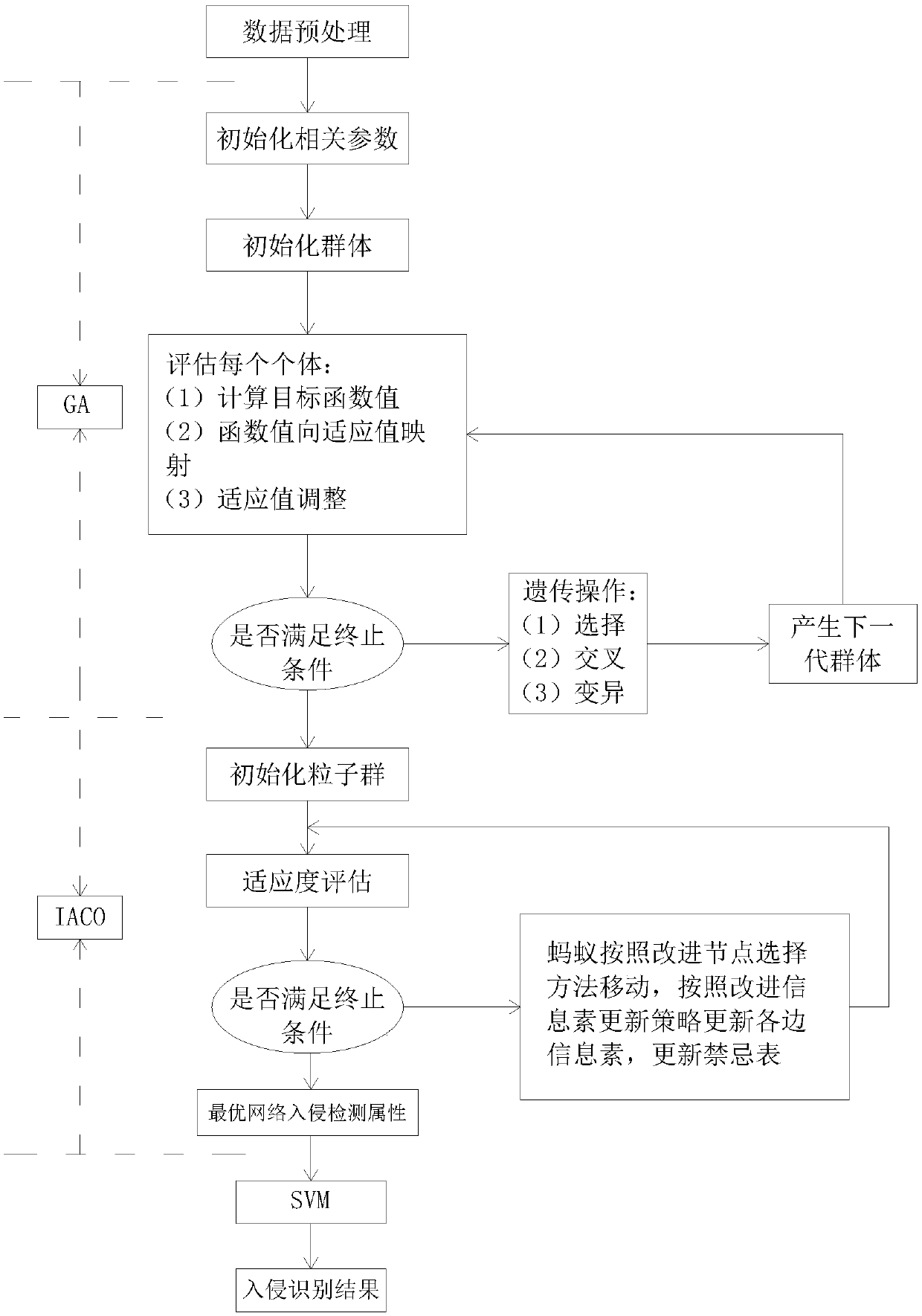
[0046] The KDD CPU 99 data set is used as the detection object for simulation experiments. KDD CPU 99 includes DOS, U2R, U2L, PROBE and other attack methods, and also contains a large amount of normal data. Among them, the training set contains 5 million records, and the test machine contains 2 million records. Some data are selected for simulation experiments. Among them, the DOS training data 3000 records, 600 tests; 5000 PROBE training records, 1200 test records; 300 U2R training records, 100 test records; 600 R2L training records, 150 test records; 30000 normal data records, 8000 test records. Use PC computer, MATLAB to simulate,
[0047] Using a transduction support vector machine-based ant colony clustering intrusion detection method to process the data, including the following steps:
[0048] Step 1, preprocessing the network data and extracting the attributes of the network data;
[0049] Step 2, initialize GA related parameters, including crossover probability, muta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com