Network combination method
A network, network-defined technology, applied in network topology, connection management, electrical components, etc., can solve the problem of no BLEBeacon application scenarios, and achieve the effect of convenient use experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
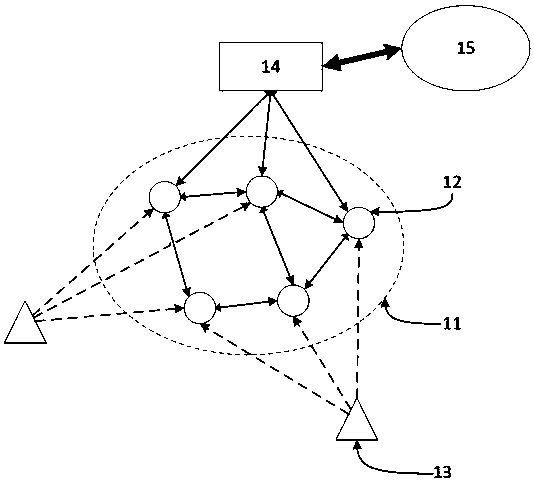
[0035] figure 1 A schematic diagram of a system combining a preferred BLE Beacon device with a SIG Mesh network according to an embodiment of the present invention, as shown in figure 1 As shown, the elliptical dotted line frame is the SIG Mesh network 11. There are multiple SIG Mesh network nodes 12 in the SIG Mesh network 11, and each SIG Mesh network node 12 is bidirectionally connected and communicated with the surrounding SIG Mesh network nodes, thereby forming a SIG Mesh network node. Network, part of the SIG Mesh network nodes 12 are connected to the home gateway 14, and communicate with the network cloud 15 through the home gateway 14.
[0036] There are one or more BLE Beacon nodes 13 outside the SIG Mesh network 11. Under the current BLE GATT protocol, only the connection between the central node and the peripheral node in the BLE Beacon node 13 can be realized, but the BLE Beacon in the present invention The node 13 can be connected to the SIG Mesh network node 12 ...
Embodiment 2
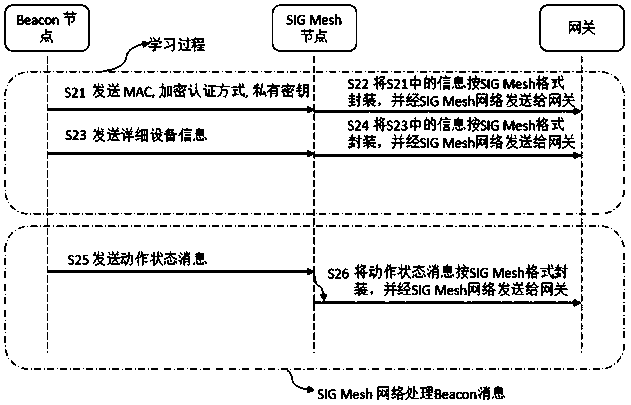
[0038] figure 2 It is a schematic diagram of the preferred BLE Beacon device and SIG Mesh network combination method in the embodiment of the present invention, as shown in figure 2 As shown, the specific process of combining BLE Beacon device with SIG Mesh network is as follows:
[0039] Step S21, the Beacon device broadcasts the MAC address of its own node, the encryption authentication mode ENC mode, and the static private key private key, so as to be received by the SIG Mesh node, which can serve as the proxy node of the beacon device.
[0040] Step S22, the SIG Mesh proxy node encapsulates the received MAC address of the Beacon device, encryption authentication method, and static private key in the SIG Mesh format, and sends it to the gateway through the SIG Mesh network; the gateway then sends the information to the network Cloud devices, realize the registration of Beacon devices in the network cloud.
[0041] Among them, the MAC address of the Beacon device is used...
Embodiment 3
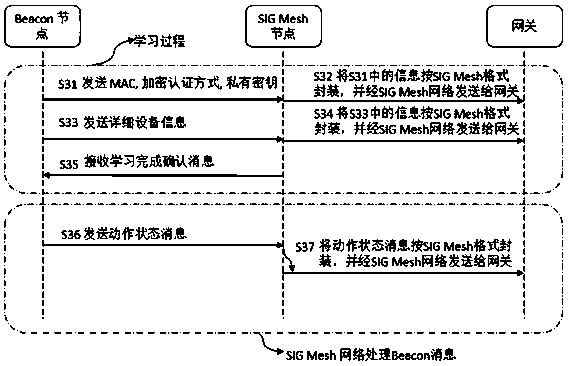
[0049] image 3 A schematic diagram of a method for combining a BLE Beacon device with a SIG Mesh network including a confirmation process, which is preferred in the embodiment of the present invention, as shown in image 3 As shown, the specific process of the method of combining the BLE Beacon device with the SIG Mesh network including the confirmation process is as follows:
[0050] Step S31, the Beacon device broadcasts the MAC address of its own node, the encryption authentication mode ENC mode, and the static private key private key, so that it is received by the SIG Mesh node, and the SIG Mesh node can serve as the proxy node of the beacon device.
[0051] Step S32, the SIG Mesh proxy node encapsulates the received MAC address of the Beacon device, encryption authentication method, and static private key in the SIG Mesh format, and sends it to the gateway through the SIG Mesh network; the gateway then sends the information to the network Cloud devices, realize the regi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com