Method and system for secure distribution of d2d content based on Stein Kohlberg game
A content security and content technology, applied in the field of mobile communication, can solve the problems of not taking into account the threat of eavesdropping, and the threat of eavesdropping is not completely equal, so as to achieve the effect of less consumption and safety risk, ensuring effectiveness and safety, and more benefits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
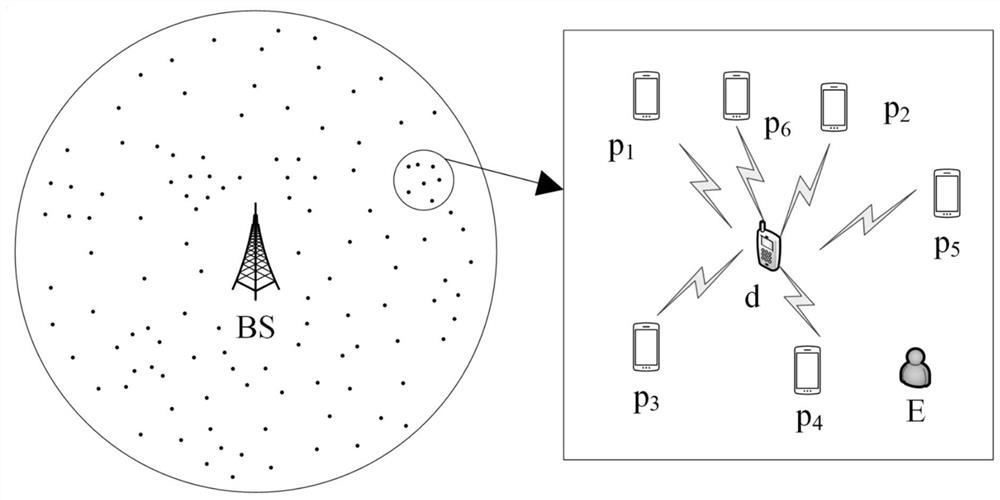
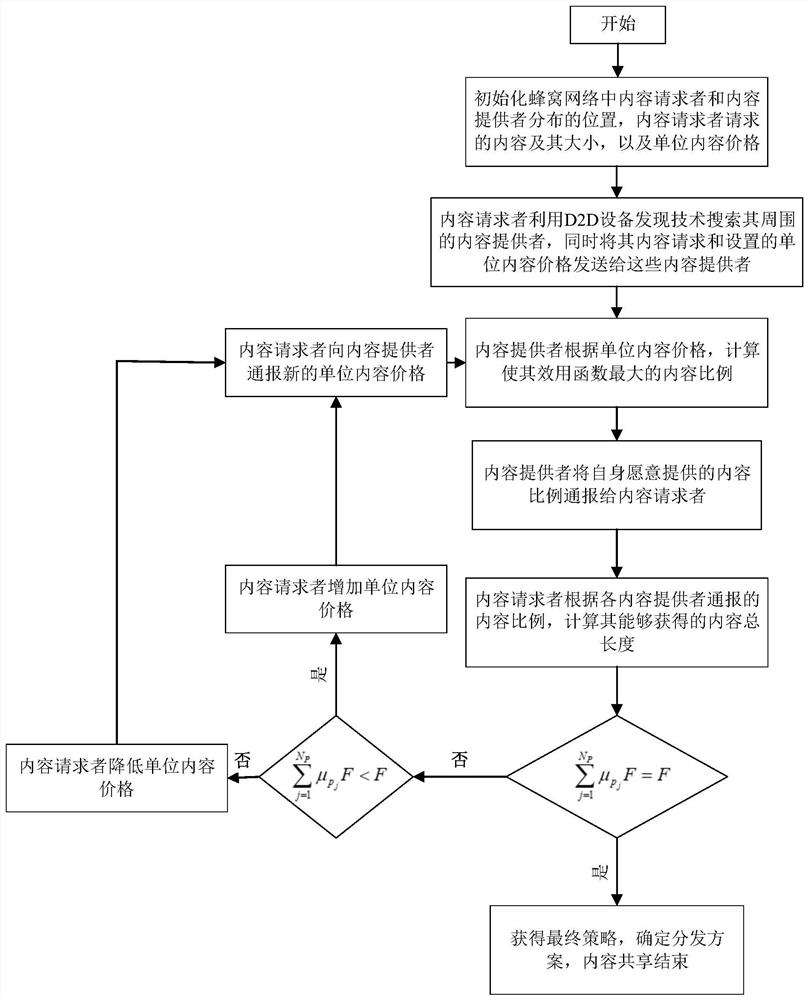
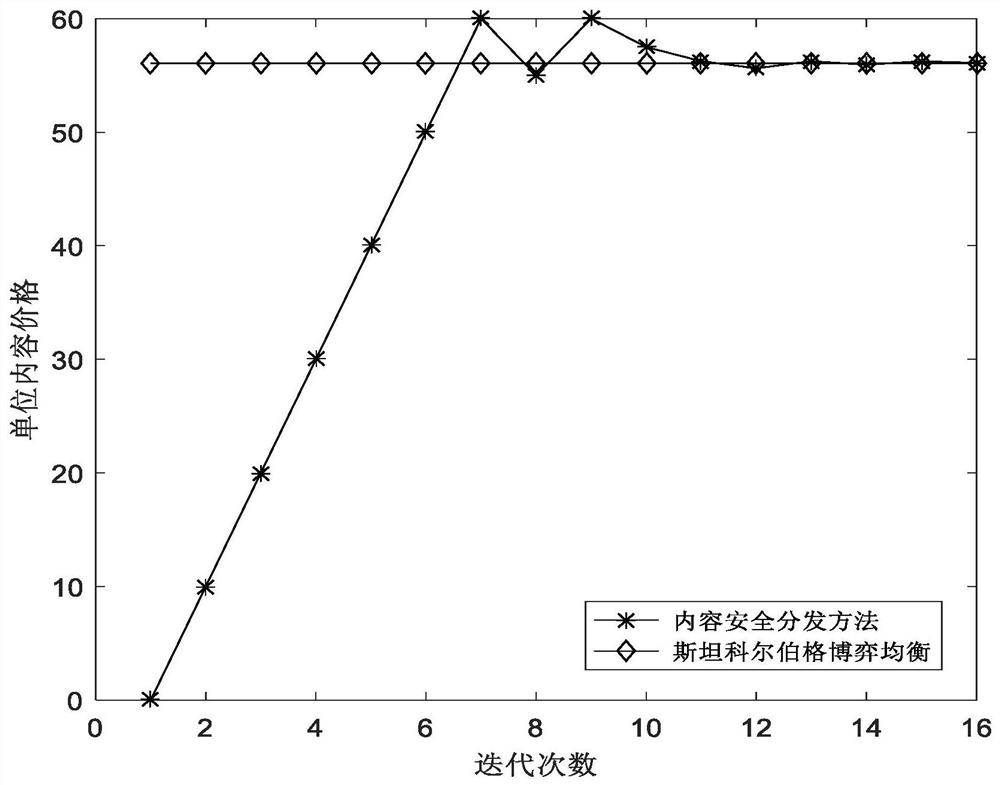
[0029] figure 1 It is a schematic diagram of a communication scenario according to the present invention. refer to figure 1 , in the cellular network based on D2D communication, there is one content requester d, and multiple content providers and potential eavesdropper E. Wherein, J is a positive integer, and j is any positive integer between [1, J]. Content requester d requests content f, whose content size is F. In addition, content requester d can use D2D device discovery technology to search for content providers around it, and at the same time send its content request to these searched content providers, and the content provider that receives the content r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com