A privacy protection control method for a fog computing medical system
A medical system and privacy protection technology, applied in the field of network information security, can solve problems such as user privacy threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
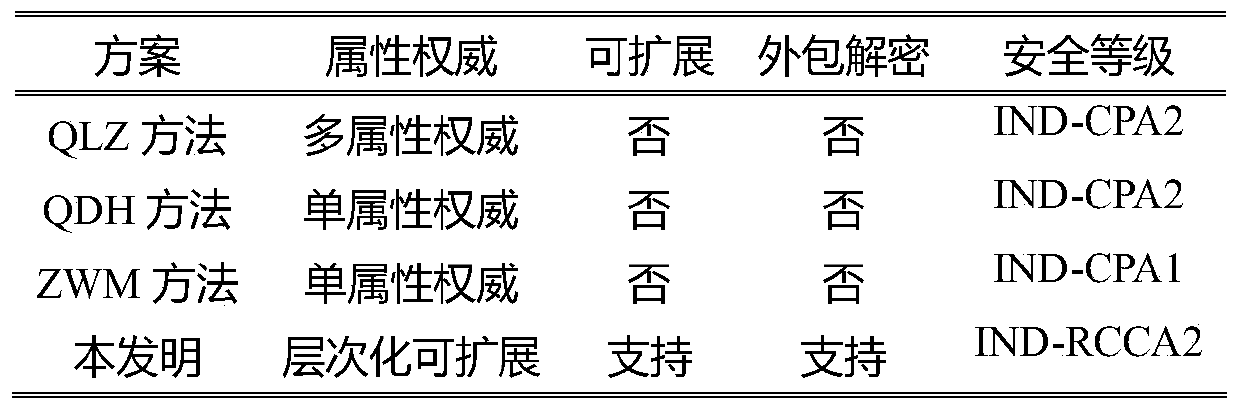
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in detail below in conjunction with the accompanying drawings and examples.
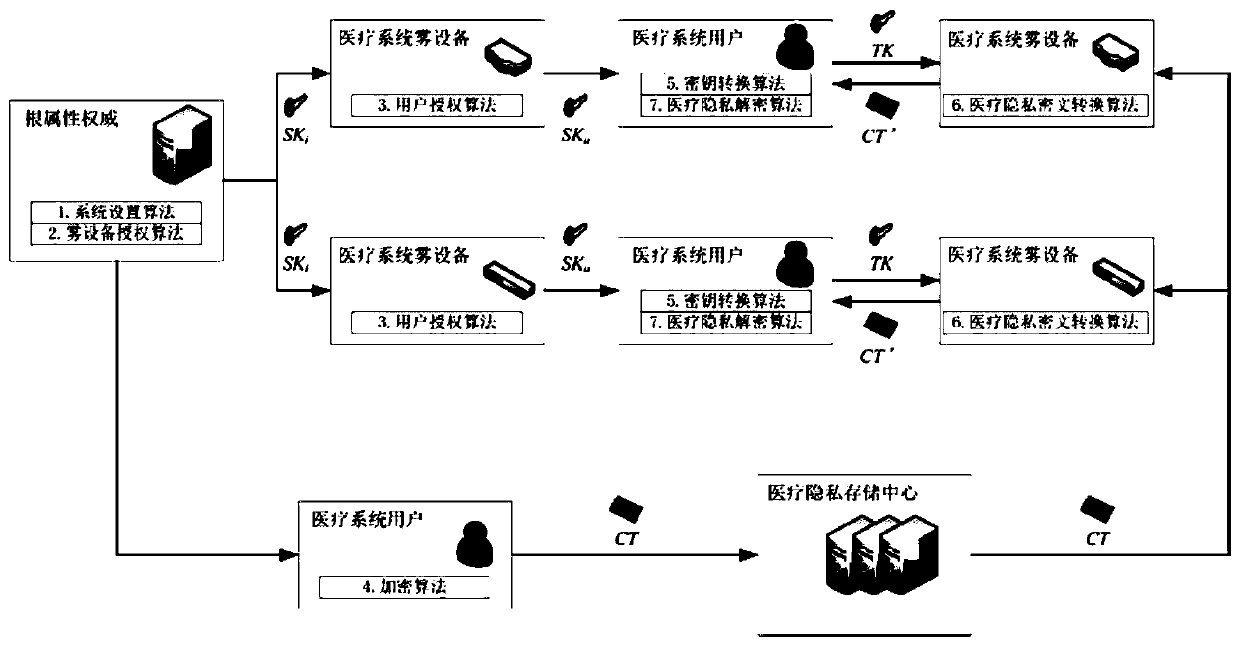
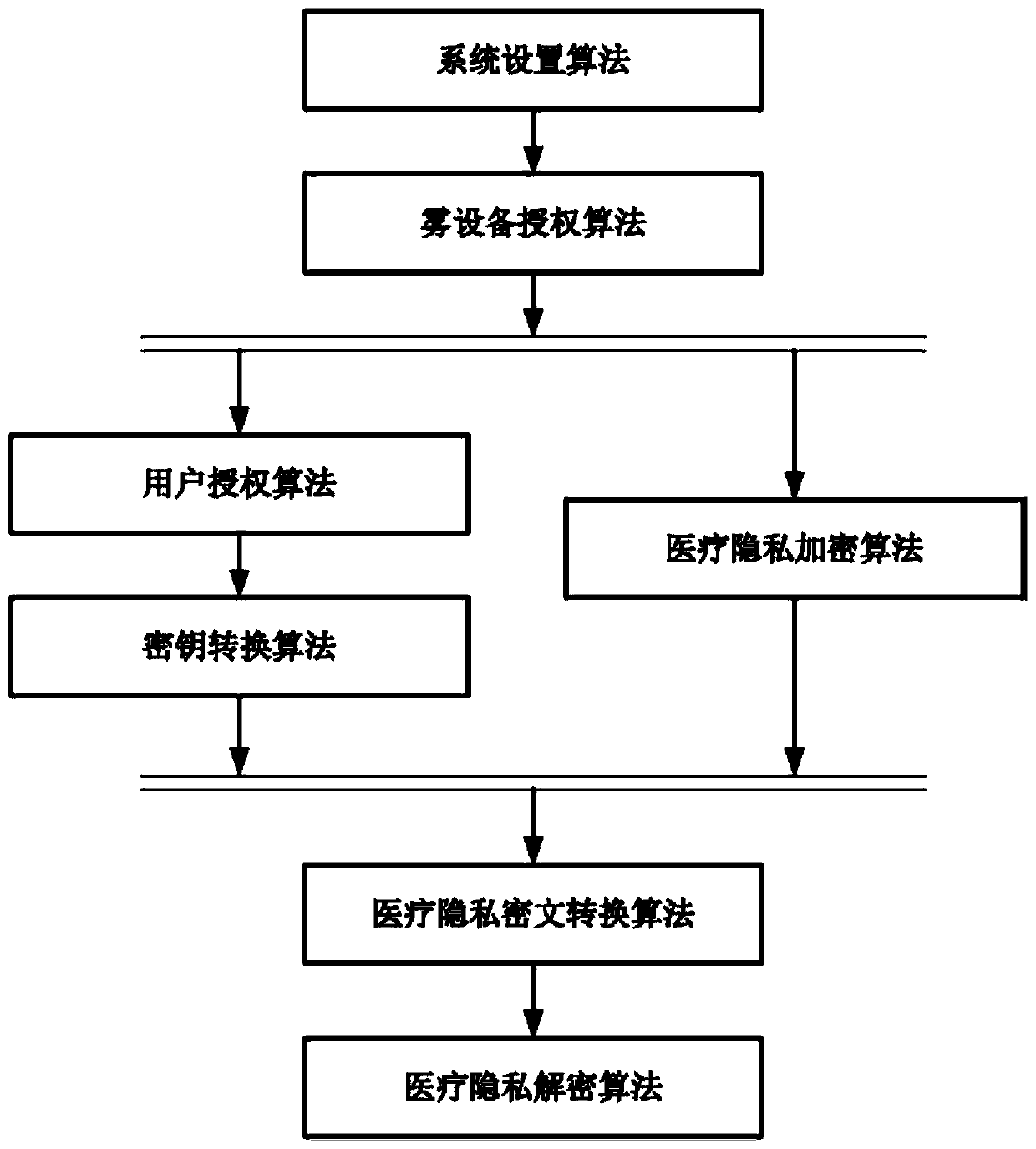
[0043] Architecture of the present invention:
[0044] Attributes: Attributes refer to certain characteristics of users of the medical system, such as gender, age, medical history, etc., and attributes are represented by att j Indicates that j is the unique index number of each attribute.
[0045] Attribute set: a set composed of attributes, in this method there are global attribute set Ω, local attribute set Ω i And user attribute set S three types of attribute sets. The global attribute set Ω contains all attributes of all users in the fog computing medical device; the local attribute set Ω i Contains a medical system fog device A i The managed attributes, where i represents the level of the fog device of the medical system, satisfy i≥1; the user attribute set S includes all the attributes of a medical system user.
[0046] Access strategy: a stra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com