Face authentication method, image base input method and device and processing equipment
A face image and authentication method technology, applied in the field of image processing, can solve the problems of slow unlocking process of mobile devices, substandard quality of face images, and unlocking failures, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
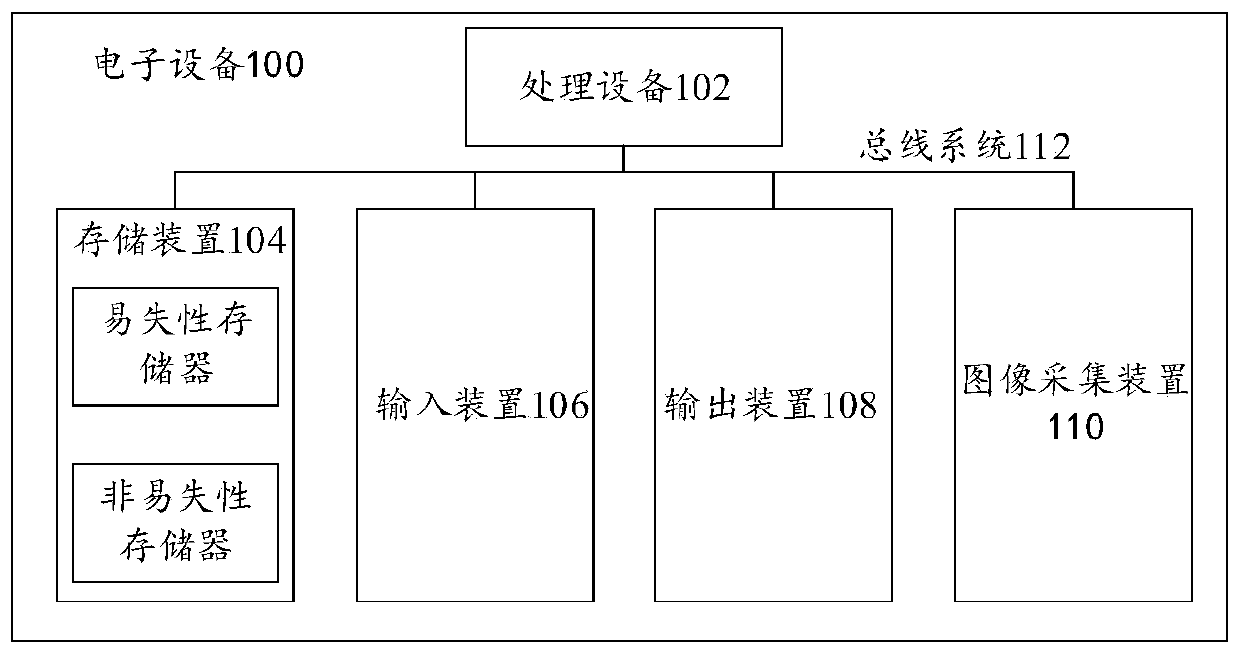
[0030] First, refer to figure 1 An example electronic device 100 for implementing the face authentication method and the image base database entry method according to the embodiment of the present invention will be described.
[0031] Such as figure 1 A schematic structural diagram of an electronic device is shown, and the electronic device 100 includes one or more processing devices 102 and one or more storage devices 104 . Optionally, figure 1 The electronic device 100 shown may further include an input device 106, an output device 108, and an image capture device 110, and these components are interconnected by a bus system 112 and / or other forms of connection mechanisms (not shown). It should be noted that figure 1 The components and structure of the electronic device 100 shown are only exemplary, not limiting, and the electronic device may also have other components and structures as required.
[0032] The processing device 102 may be a gateway, or an intelligent termi...
Embodiment 2
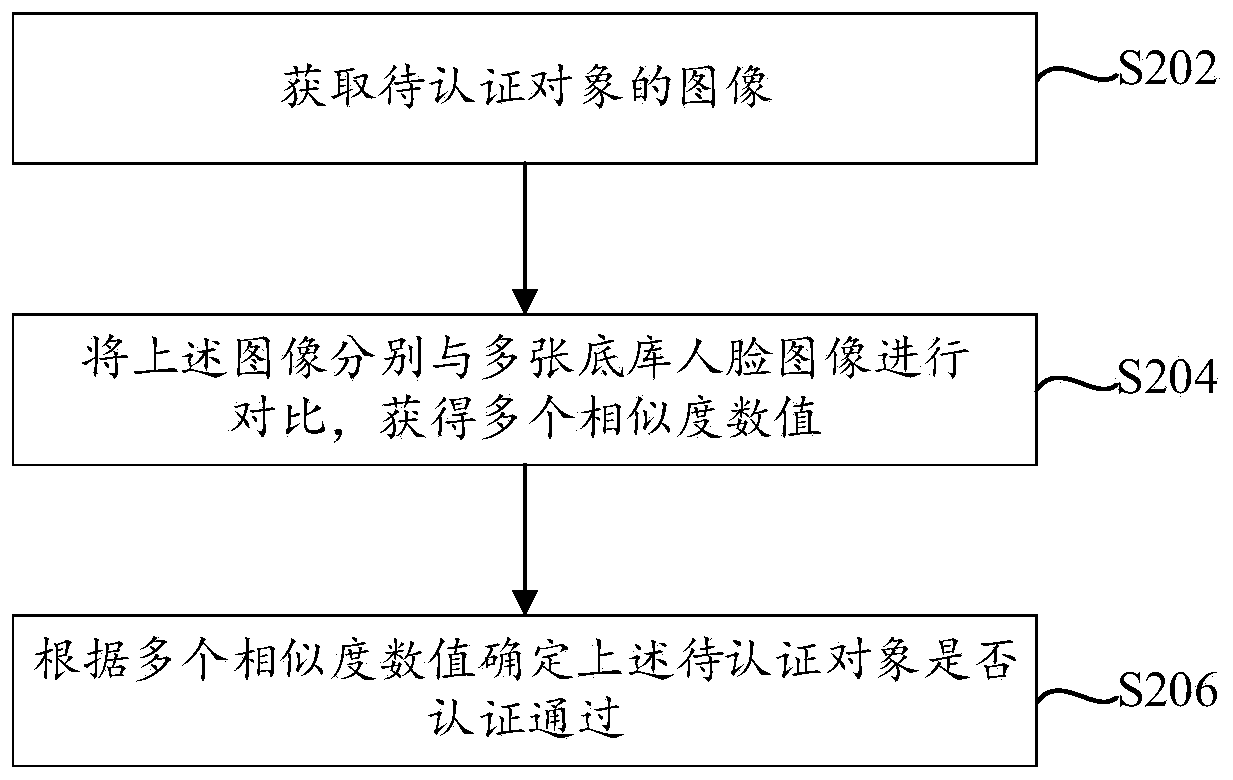
[0040] see figure 2 Shown is a flow chart of a face authentication method, which can be executed by the electronic device provided in the foregoing embodiments, such as a mobile terminal. The method specifically includes the following steps:
[0041] Step S202, acquiring the image of the object to be authenticated.
[0042] The mobile terminal can collect images of the object to be authenticated through a camera, such as a front camera. When the user uses the mobile terminal to perform face unlocking, the user can point the face at the camera device, and the face image is collected by it, that is, the face image of the object to be authenticated is obtained. After the face image is acquired, feature extraction can be performed on it to obtain feature information corresponding to the face image, which is used in the comparison process in the subsequent steps.
[0043] Step S204, comparing the above-mentioned image with a plurality of face images in the bottom database to obt...
Embodiment 3
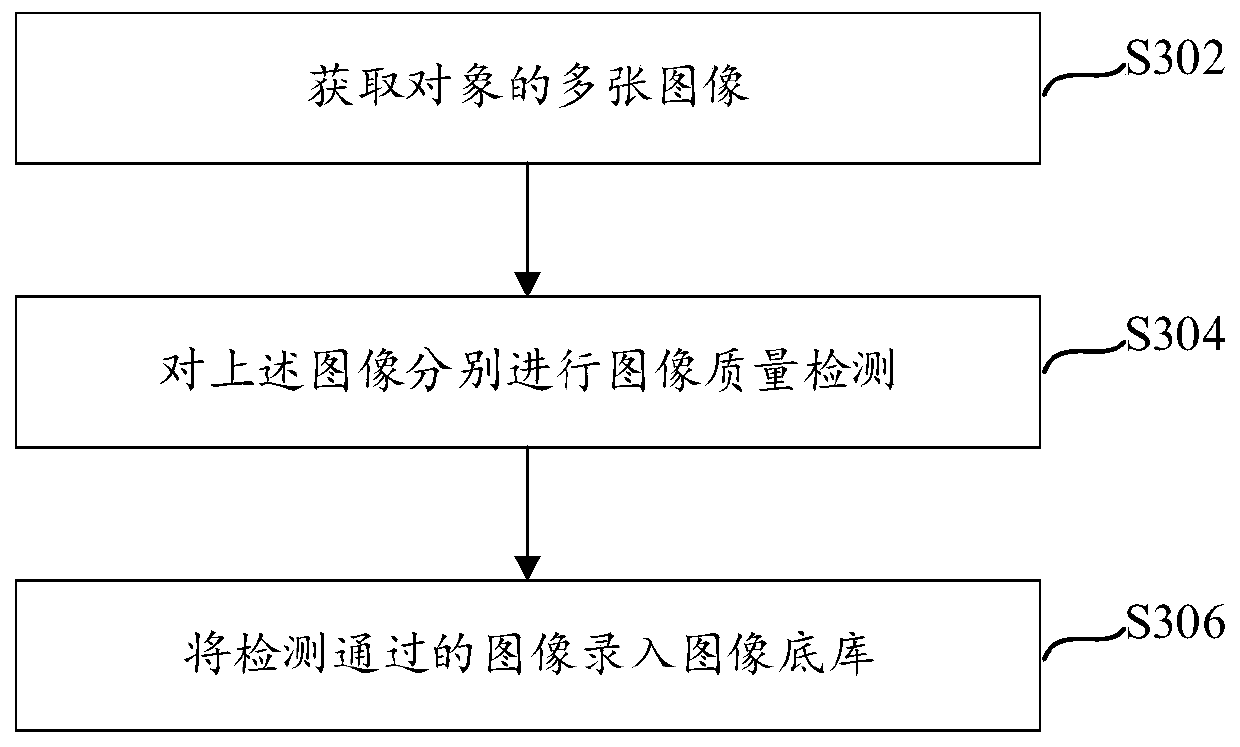
[0065] see image 3 Shown is a flow chart of a method for entering an image base database. This method can be executed by the electronic device provided in the foregoing embodiments, such as a mobile terminal. The method specifically includes the following steps:
[0066] Step S302, acquiring multiple images of the object.
[0067] In this embodiment, the face image of the subject can be captured by the front camera module of the mobile terminal.
[0068] Step S304, performing image quality detection on the above-mentioned images respectively.
[0069] For a specific image quality detection manner, reference may be made to the foregoing embodiments, and details are not repeated here.
[0070] In step S306, the image that passes the detection is used as the bottom library image of the above-mentioned object. . Delete the images that fail the detection, and reacquire at least one image of the object.
[0071] In this embodiment, the multi-bottom library image entry mechanis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com