ROP and variant attack dynamic detection method based on multi-strategy instruction detection
A technology of instruction detection and dynamic detection, applied in the field of memory attack and defense, can solve the problems of high performance overhead, high performance consumption, and large memory occupation, so as to reduce the false positive rate and false negative rate, and improve the accuracy rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] Below in conjunction with accompanying drawing and specific embodiment, the present invention will be further described:
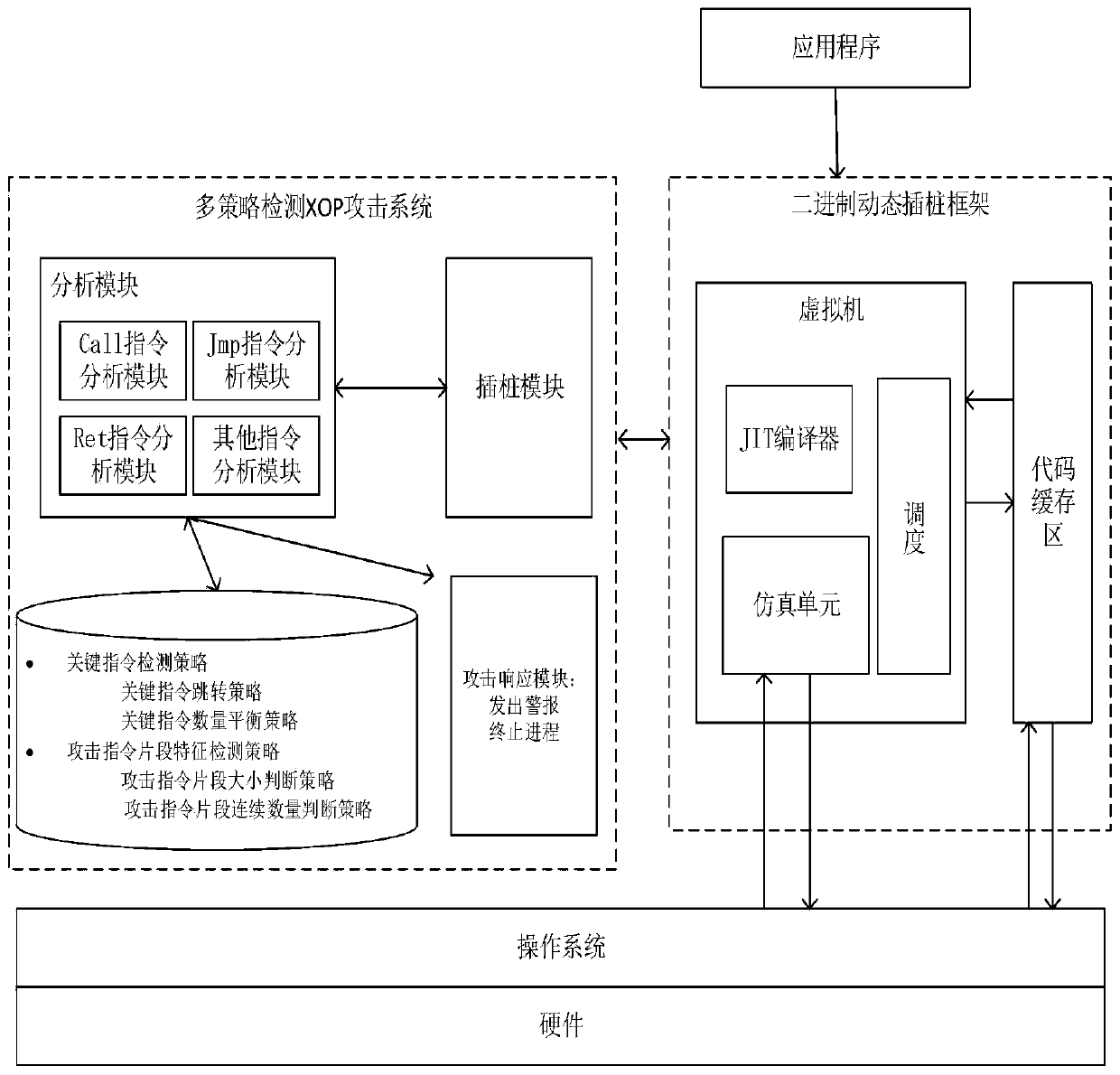
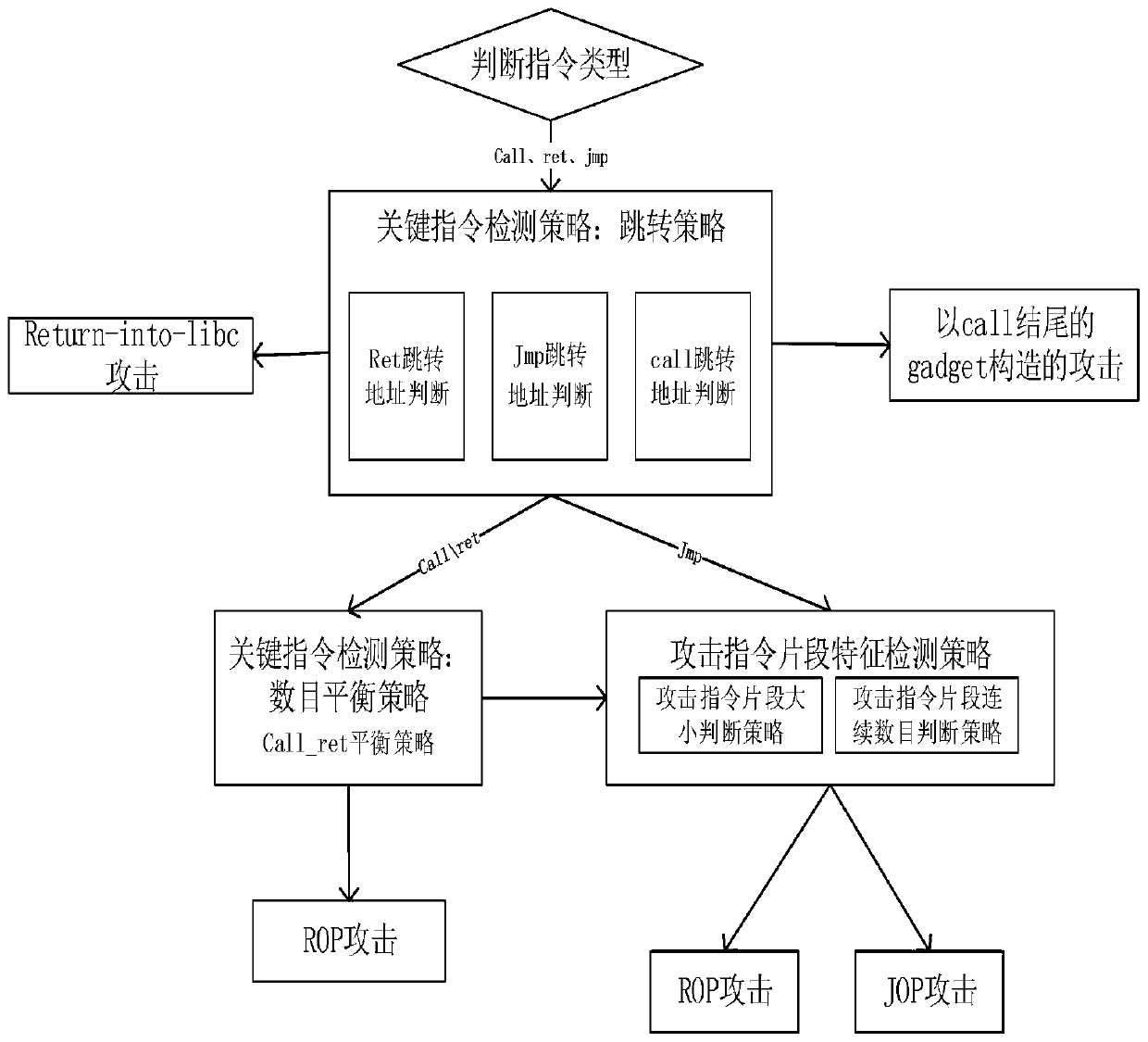
[0055] Key instruction detection (key instruction jump strategy and key instruction quantity balance strategy) proposed by the present invention and attack instruction fragment feature detection (attack instruction fragment size and continuous length judgment strategy) multi-strategy judgment ROP attack and variant attack detection method The overall framework of the system is attached figure 1 As shown, it mainly includes command analysis module, stub insertion module, process alarm and termination module.
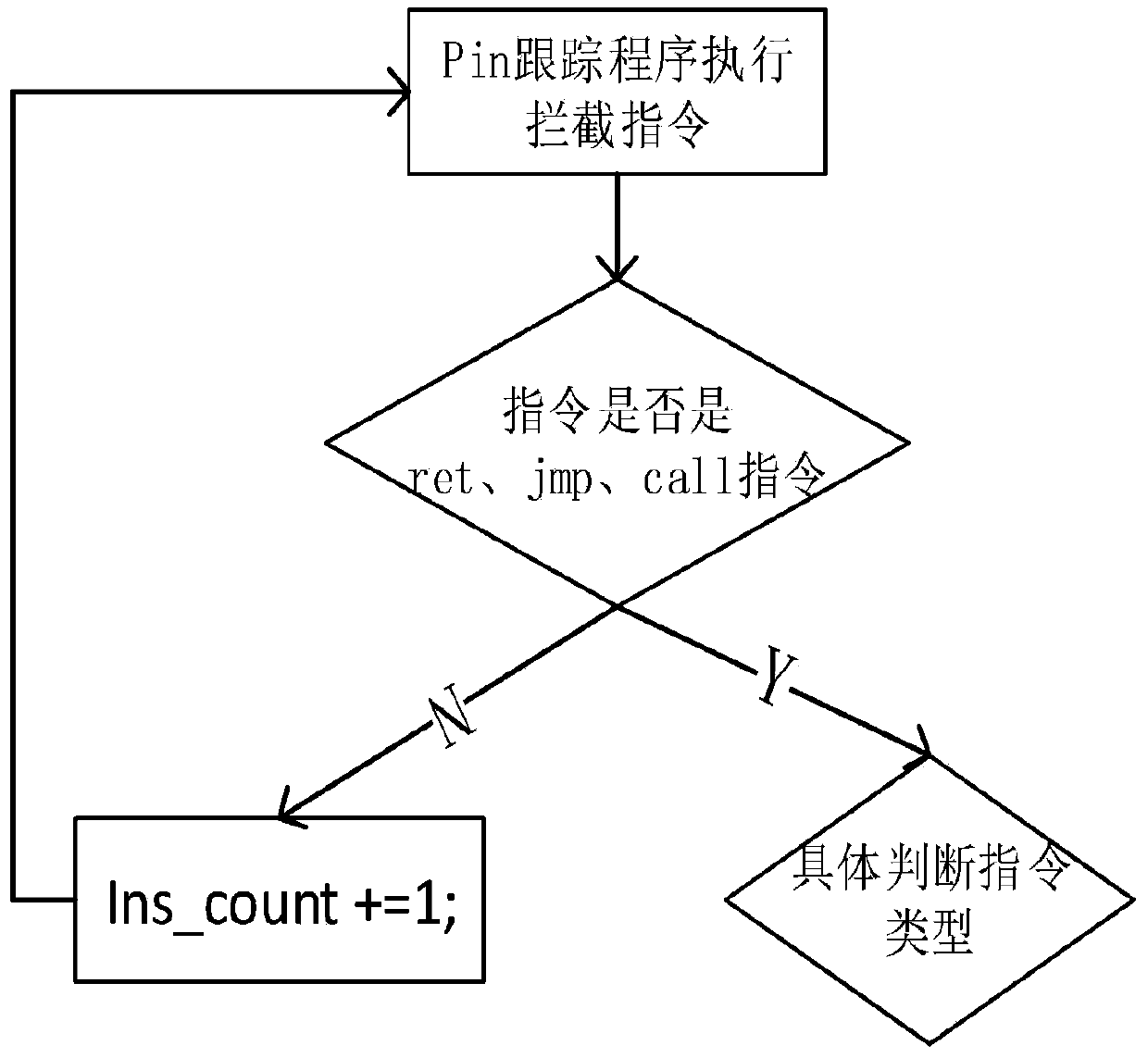
[0056] The instrumentation module is mainly used to perform instruction-level instrumentation on the loaded target file (source code), and determine the location and content of the instrumentation by analyzing the type of the instruction. For example, after the ret instruction is detected, the ret analysis code is inserted before the ret instr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com