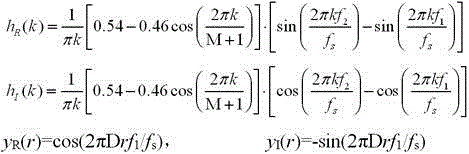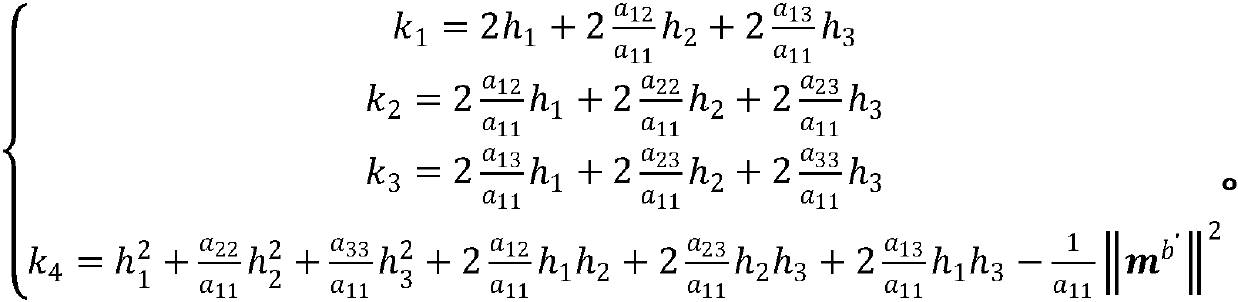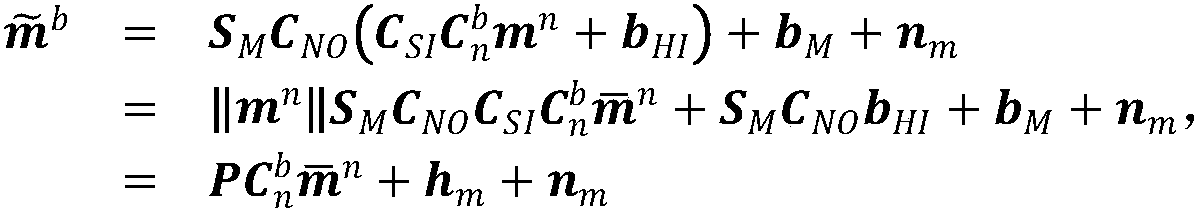Patents
Literature
70results about How to "Takes up little memory space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
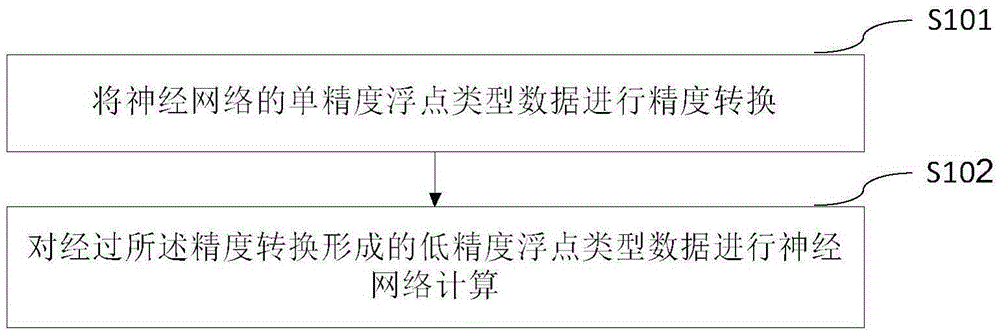
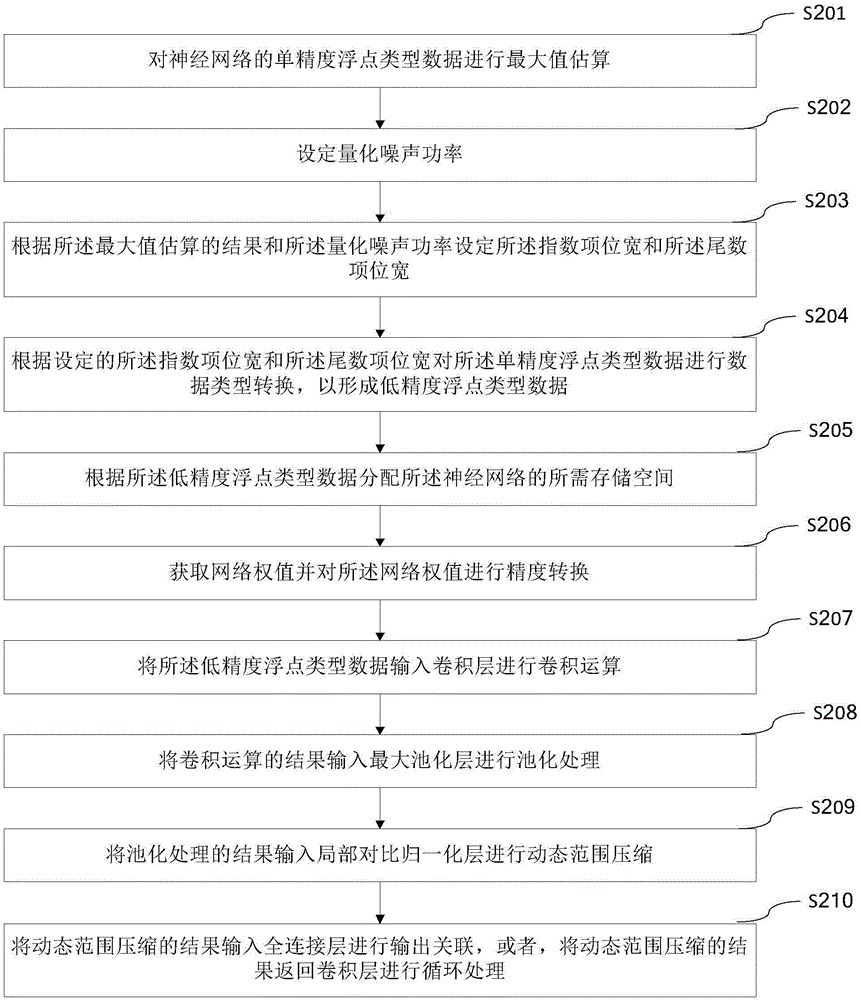
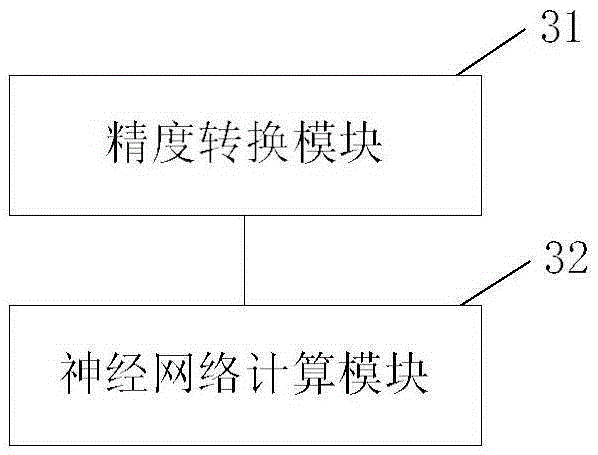
Data processing method and device based on neural network
InactiveCN106570559ASave bandwidthReduce overheadBiological neural network modelsData setNerve network
The application aims to provide a data processing method and device based on a neural network. The method comprises steps that precision conversion for single precision floating point type data of the neural network is carried out; neural network calculation for the low precision floating point type data after precision conversion is carried out. Compared with the prior art, the method and the device are advantaged in that solving a large storage content problem in a low precision mode is facilitated, the memory space occupied by a model can be saved, a larger model can operate through utilizing same hardware configuration, and the memory or hardware space occupied by a data set can be saved; when the model is deployed on a cluster, network bandwidth required during synchronization can be effectively reduced, communication cost can be effectively reduced, and integral performance is improved.
Owner:ALIBABA GRP HLDG LTD
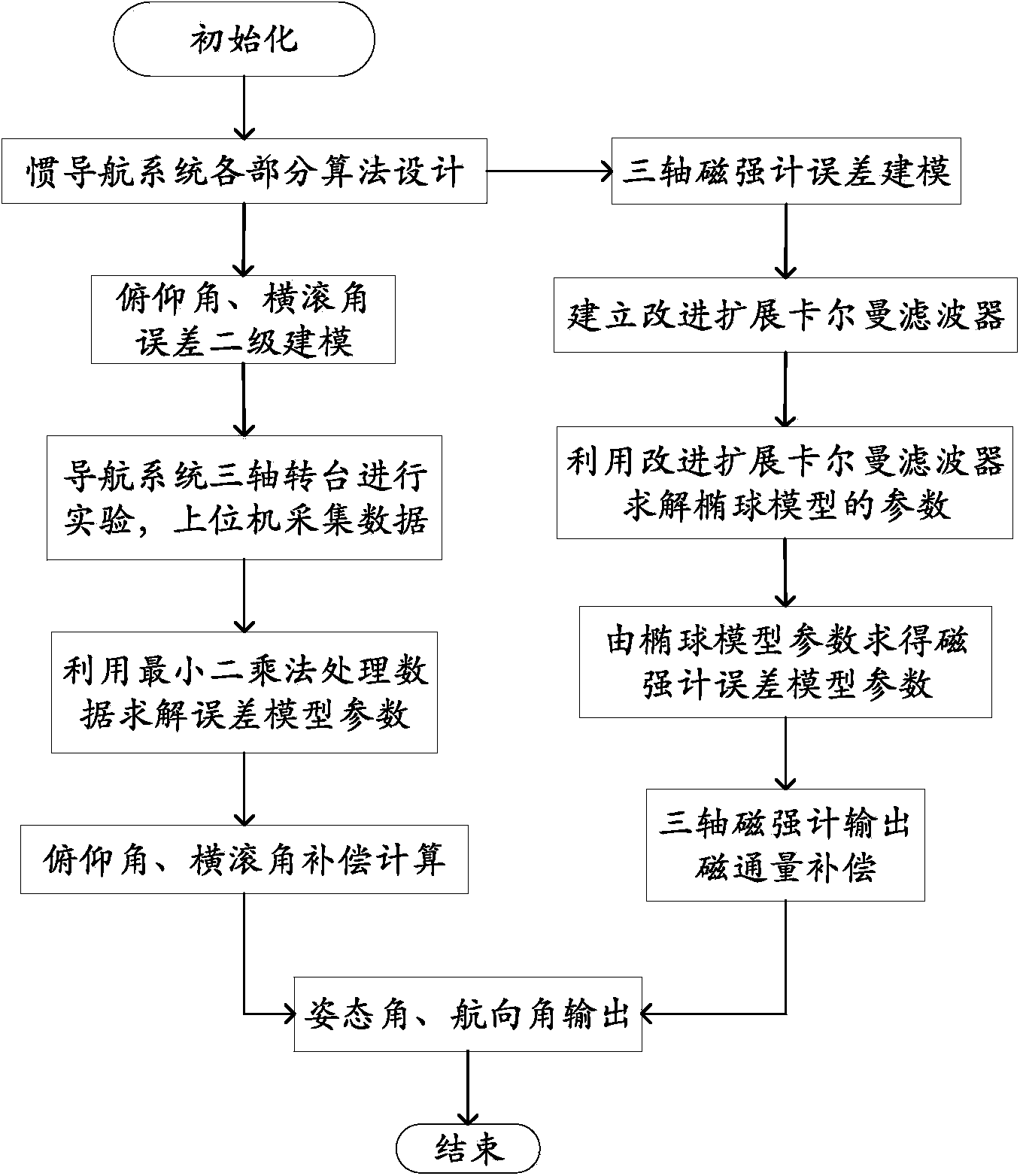
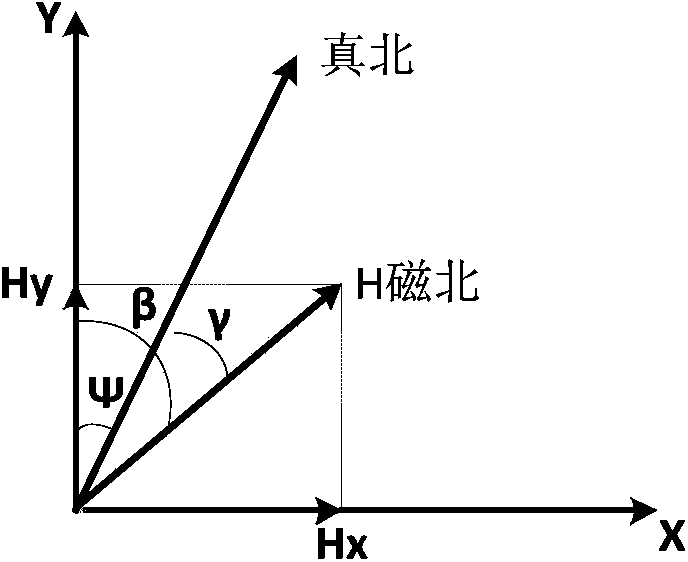
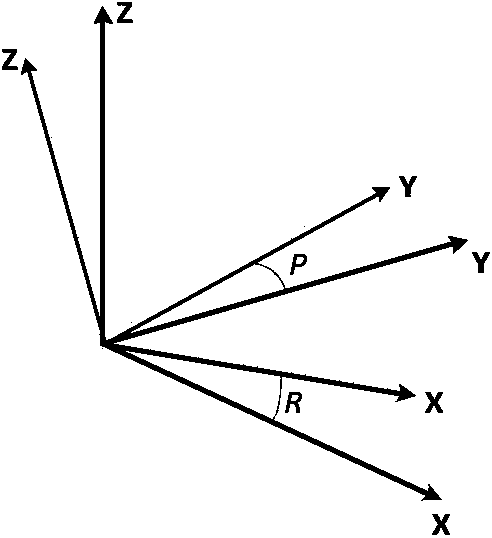
Correction method used for attitude and course angles of navigation system
ActiveCN103630137AHigh precisionAchieve positioningNavigational calculation instrumentsSimulationNavigation system
The invention declares a correction method used for attitude and course angles of a navigation system. The method comprises the following step of providing an effective method of conducting magnetometer error compensation and attitude angle error secondary modeling and correction, and realizing error correction of a whole system on the basis of an ellipsoid fitting method of improving expanded Kalman filter. The correction method is used for error correction of the attitude and course angles in an inertial integrated navigation and positioning system composed of an inertial measuring unit (IMU), a magnetometer and the like. According to the invention, a magnetic field compensation method is expanded to three-dimensional ellipsoid fitting from two dimensional elliptical fitting; a new ellipsoidal model and an improved extended Kalman filter method are utilized to conduct ellipsoid fitting; through the adoption of the method, the dynamical and real-time compensation for three-dimensional magnetic field interference of a carrier self can be effectively realized, and the accuracy in the measurement of the geomagnetic field is improved, thereby improving the precision of the course angle of the carrier; the error secondary modeling is conducted on the attitude angle information output by the navigation system, and then compensation is conducted on the output attitude angle to improve the precision of the attitude angle in real time.
Owner:SOUTHEAST UNIV
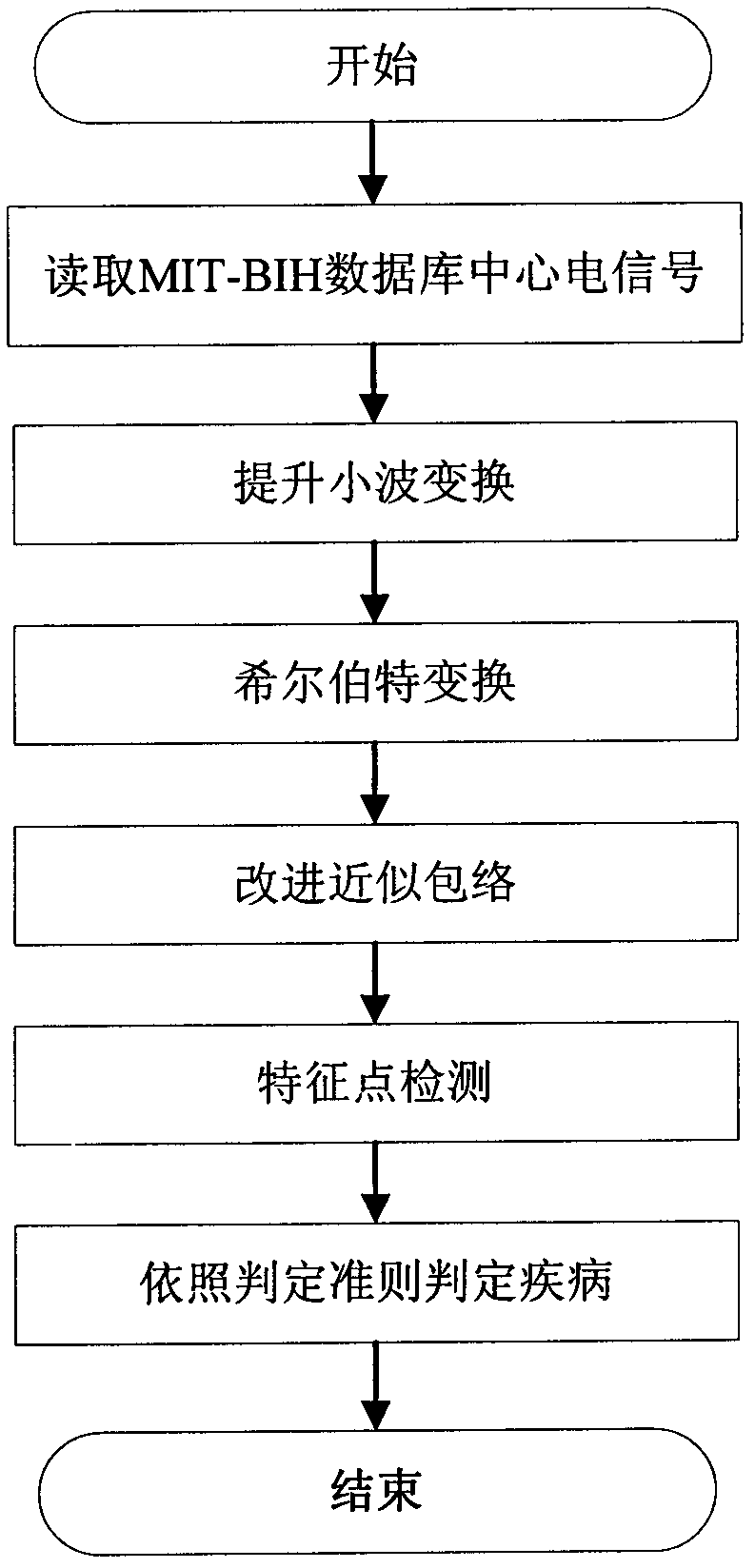
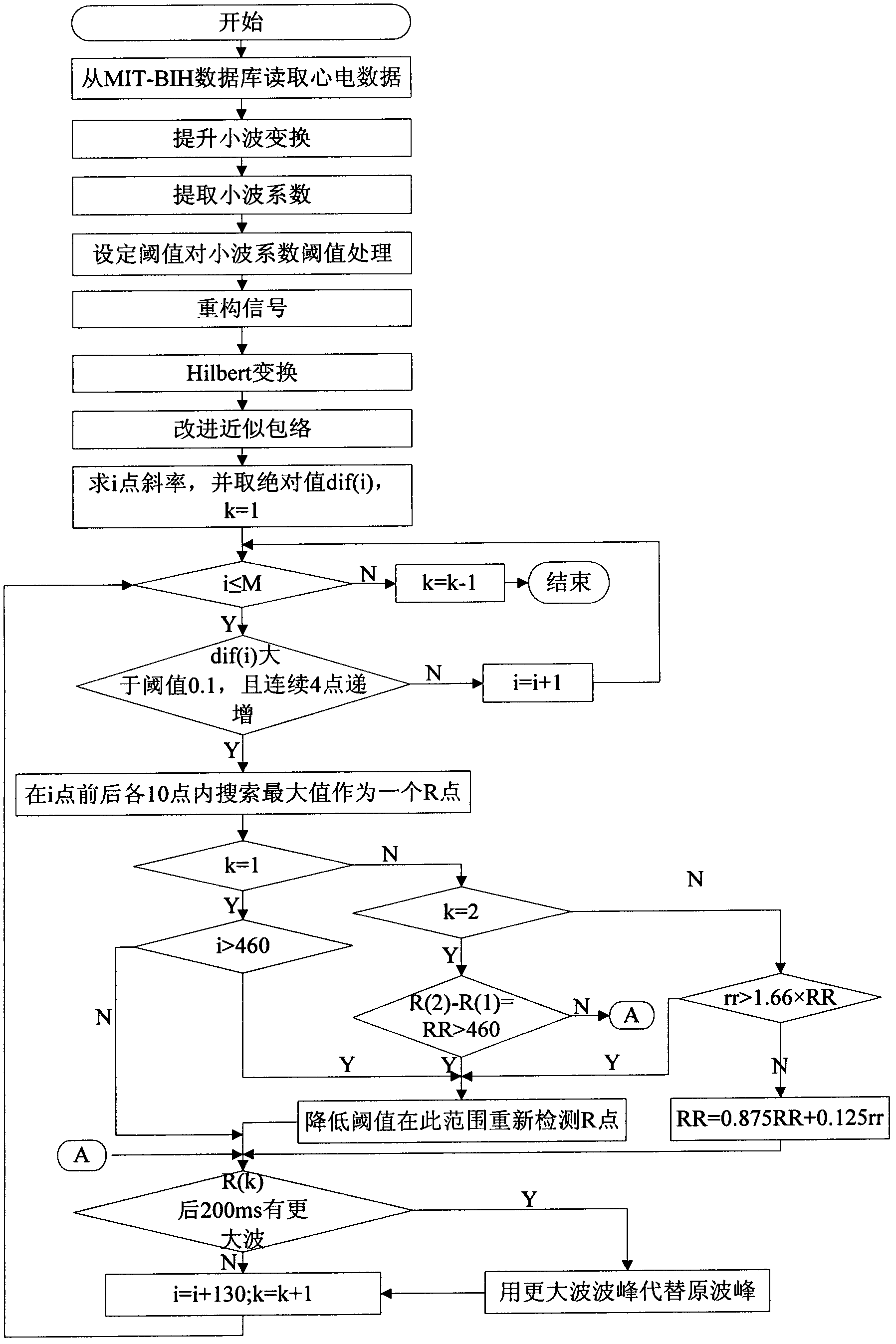
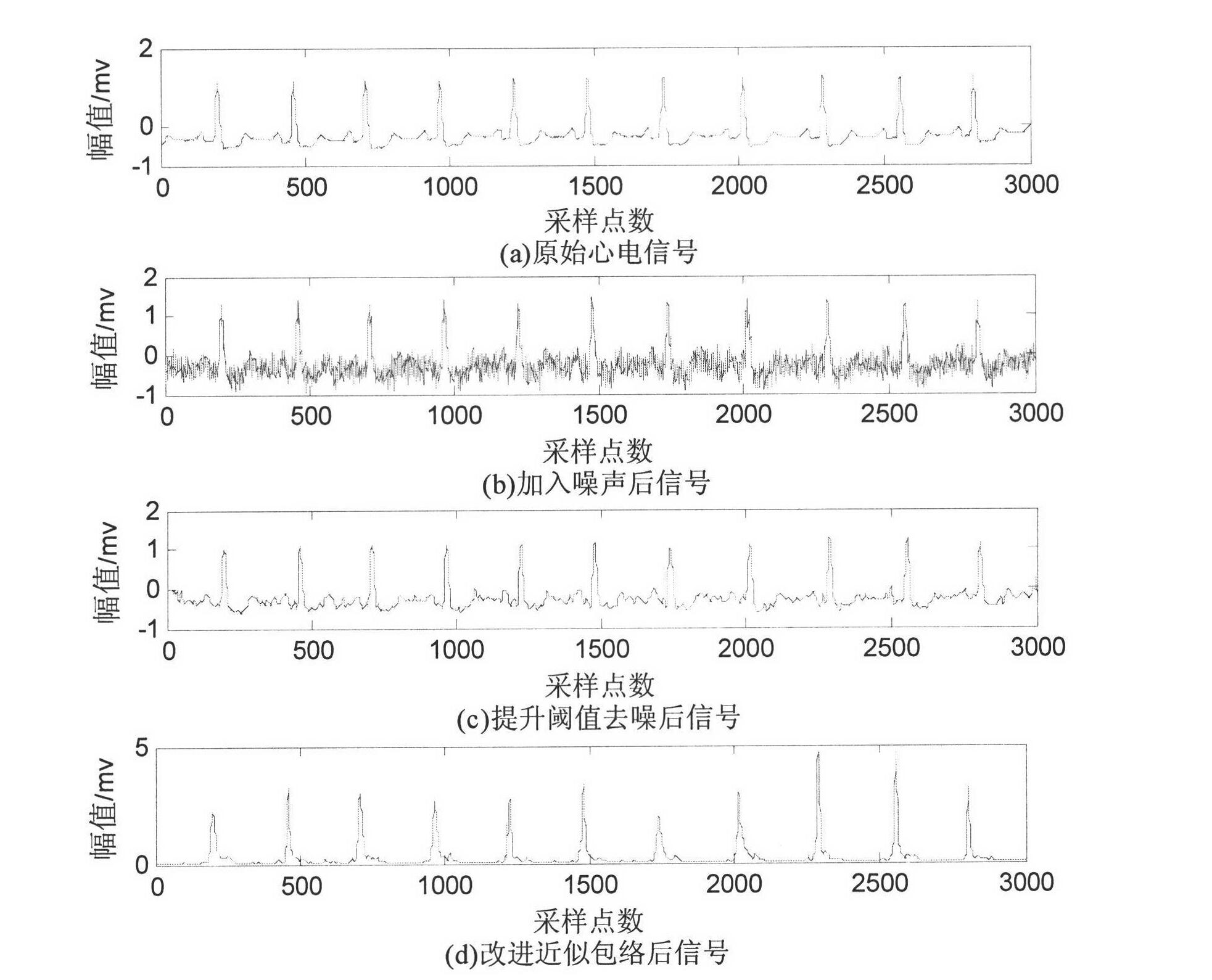
Electrocardiogram signal feature detection algorithm based on wavelet transformation lifting and approximate envelope improving
InactiveCN102626310AImprove the speed of the denoising processHigh speedDiagnostic recording/measuringSensorsT waveMit bih database
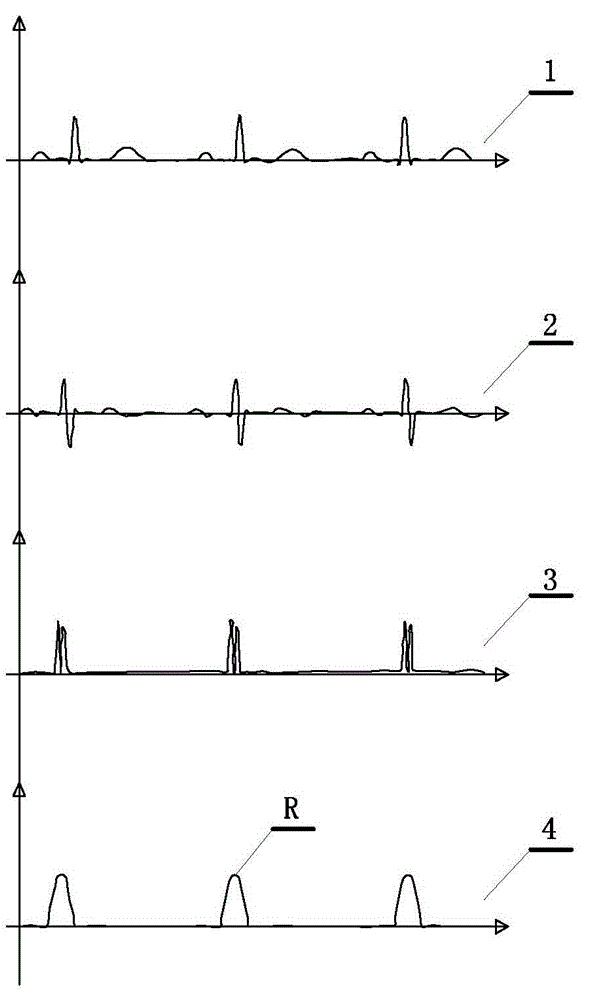
The invention discloses an electrocardiogram signal feature detection algorithm based on wavelet transformation lifting and approximate envelope improving and belongs to a weak bioelectrical signal processing technology field. The current electrocardiogram signal detection technology applied clinically can not give consideration to both a detection precision requirement and a real time requirement. Electrocardiogram signal pretreatment algorithm based on wavelet lifting for improving semi-soft threshold denoising and approximate envelope improving and electrocardiogram feature detection algorithm based on a slope threshold are provided in the invention. Detection criterions are set based on waveform characteristics and time domain distribution characteristics of the electrocardiogram signals. Position detections of R wave, start-stop points of the QRS waves, P wave and T wave are carried out respectively to the electrocardiogram signals. The electrocardiogram signal feature detection algorithm provided in the invention is easy, quick and suitable for parallel processing, and occupies little memory space and is convenient for DSP chip realization. Even in strong noise and P / T wave interference circumstances, R point position can be accurately detected through the algorithm provided in the invention. An R wave false detecting rate of 105 data containing serious noise disturbance is only 0.27% compared with MIT-BIH Database annotation.
Owner:TIANJIN POLYTECHNIC UNIV
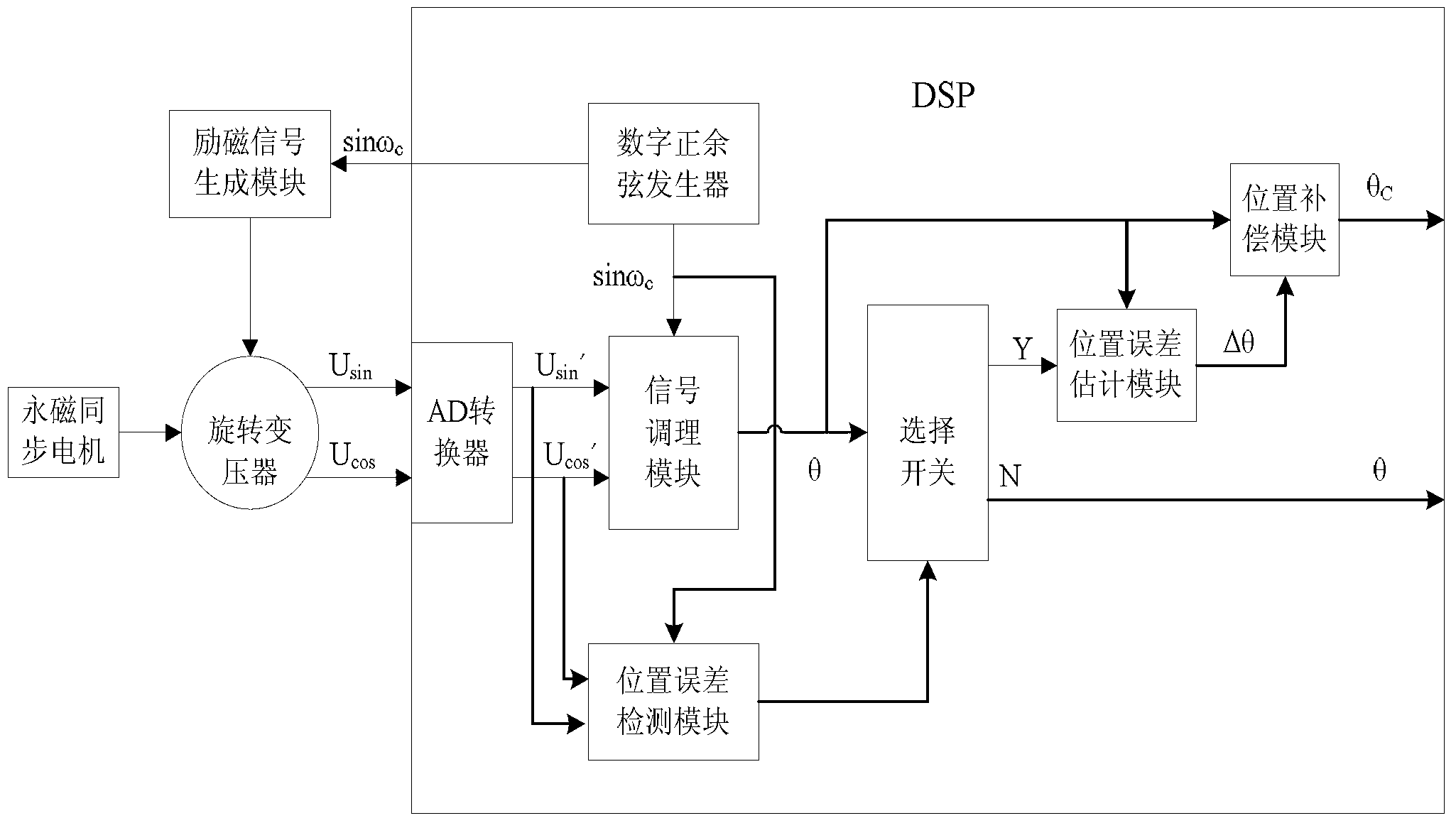
Rotating transformer digital converter capable of on-line failure detection and fault-tolerant control
ActiveCN103256946AHigh precisionEasy to detectConverting sensor output electrically/magneticallyKaiman filterEngineering
The invention discloses a rotating transformer digital converter capable of on-line failure detection and fault-tolerant control. According to the method, an electric automobile PMSM is used for controlling matched utilization of a microprocessor DSP and the rotating transformer so as to achieve a PMSM rotor position of a drive system of the PMSM. Failures of the rotor position of the drive system of the PMSM can be detected real-timely. Meanwhile, a kalman filter is adopted for identifying errors of the rotor position, and realizing self-adaptive fault-tolerant control, and therefore precision of acquiring the rotor position is improved.
Owner:HEFEI UNIV OF TECH
Correspondence address identifying and standardizing method
ActiveCN102955833AHigh precisionImprove throughputSpecial data processing applicationsCorrespondence analysisRecall rate
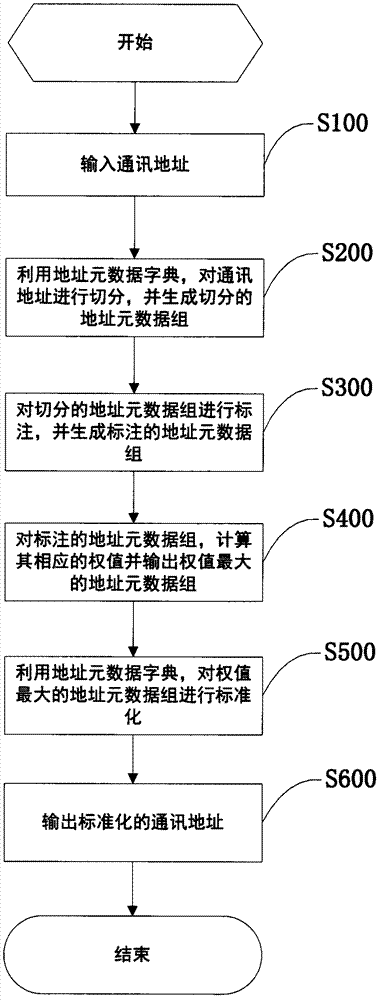
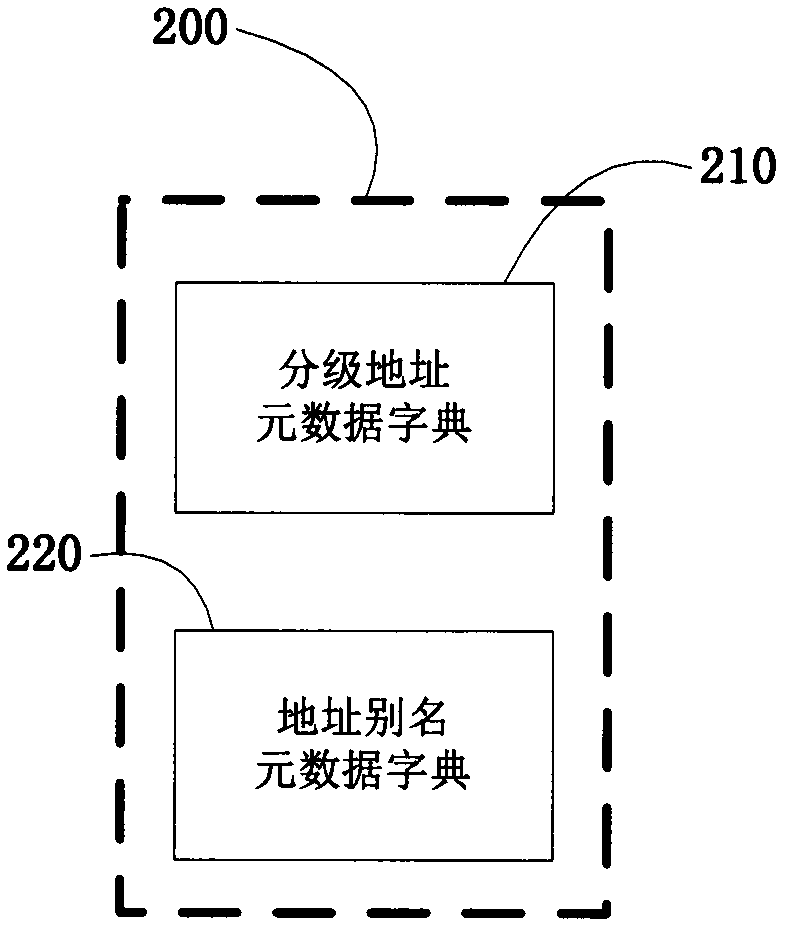
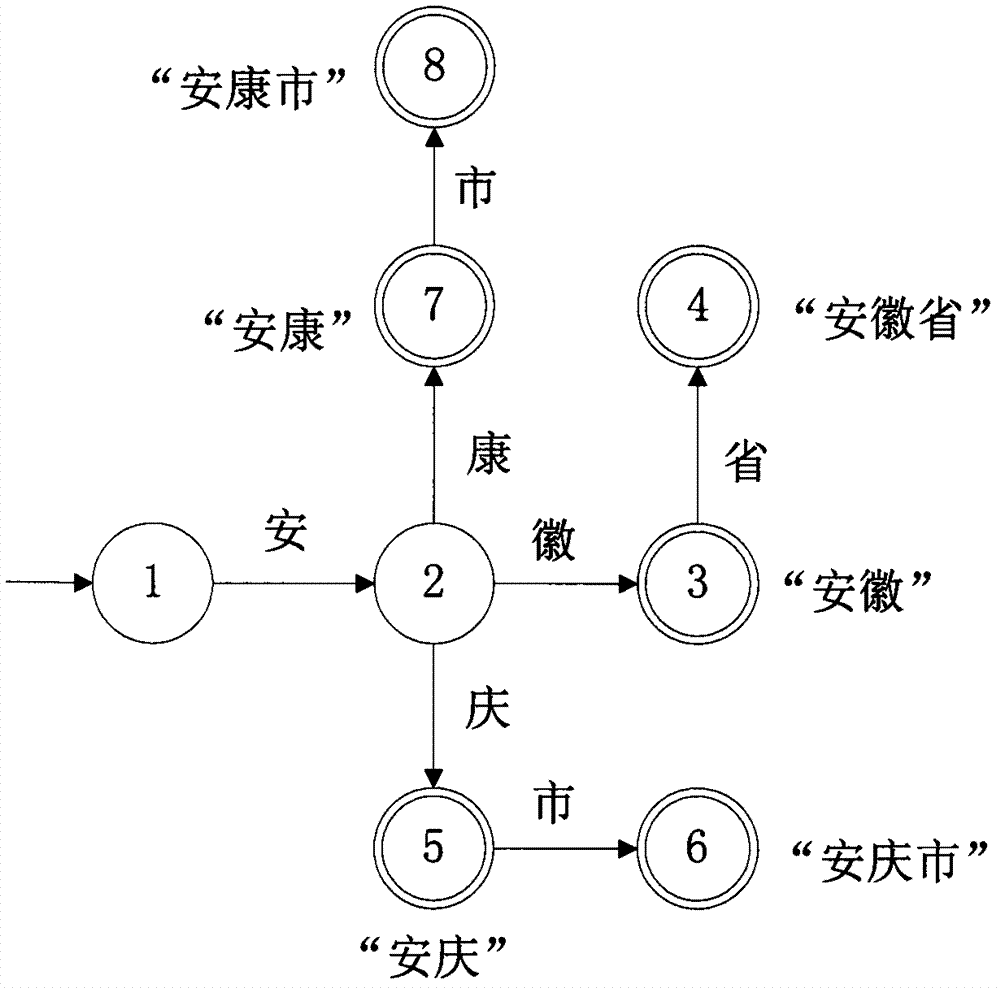
The invention provides a correspondence address identifying and standardizing method which is used for solving the problem of correspondence address identification and standardization. The correspondence address identifying and standardizing method comprises the following steps: inputting a correspondence address; segmenting the input correspondence address by using an address metadata dictionary, and generating segmented address metadata groups; labeling the segmented address metadata groups, and generating labeled address metadata groups; calculating corresponding weight values of the labeled address metadata groups and outputting the address metadata group with the largest weight value; standardizing the address metadata group with the largest weight value by using the address metadata dictionary, and generating a standardized correspondence address; and outputting the standardized correspondence address. By adopting the correspondence address identifying and standardizing method, the precision of correspondence address processing is improved, and the throughput rate and recall rate of correspondence address processing are relatively high.
Owner:SHENZHEN AUDAQUE DATA TECH
Implementation method of least recently used (LRU) policy in solid state drive (SSD)-based high-capacity cache
ActiveCN103150136AEasy to implementComplicated operationData conversionBloom filterSolid-state drive
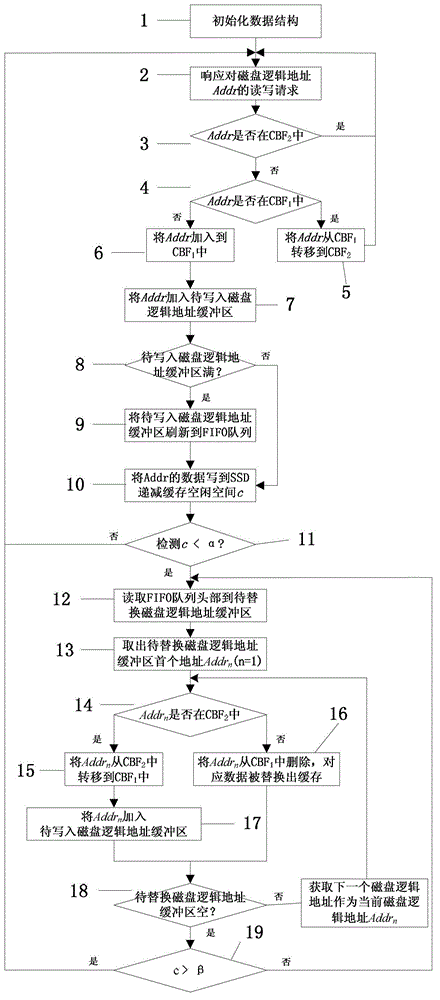
The invention discloses an implementation method of a least recently used (LRU) policy in a solid state drive (SSD)-based high-capacity cache. According to the method, logic addresses of an upper-layer application read-write request are combined into a first in first out (FIFO) queue; two counting Bloom filters are respectively used for recording the logic addresses which are accessed for one or more times in the FIFO queue; and the FIFO queue and the two counting Bloom filters can accurately simulate the behavior of an LRU queue. The FIFO queue is stored on an SSD, and does not occupy a memory space. The two counting Bloom filters are stored in a memory, and occupy a very small memory space. Functions of the LRU queue are realized with extremely-low memory overhead. The implementation method has the advantages of simplicity in implementation, quickness in operation, small storage occupation space and low memory overhead.
Owner:NAT UNIV OF DEFENSE TECH
Intelligent video monitoring system and performance test method of algorithm thereof
ActiveCN101656891APromote improvementRun fastClosed circuit television systemsSpecial data processing applicationsComputer hardwareVideo monitoring
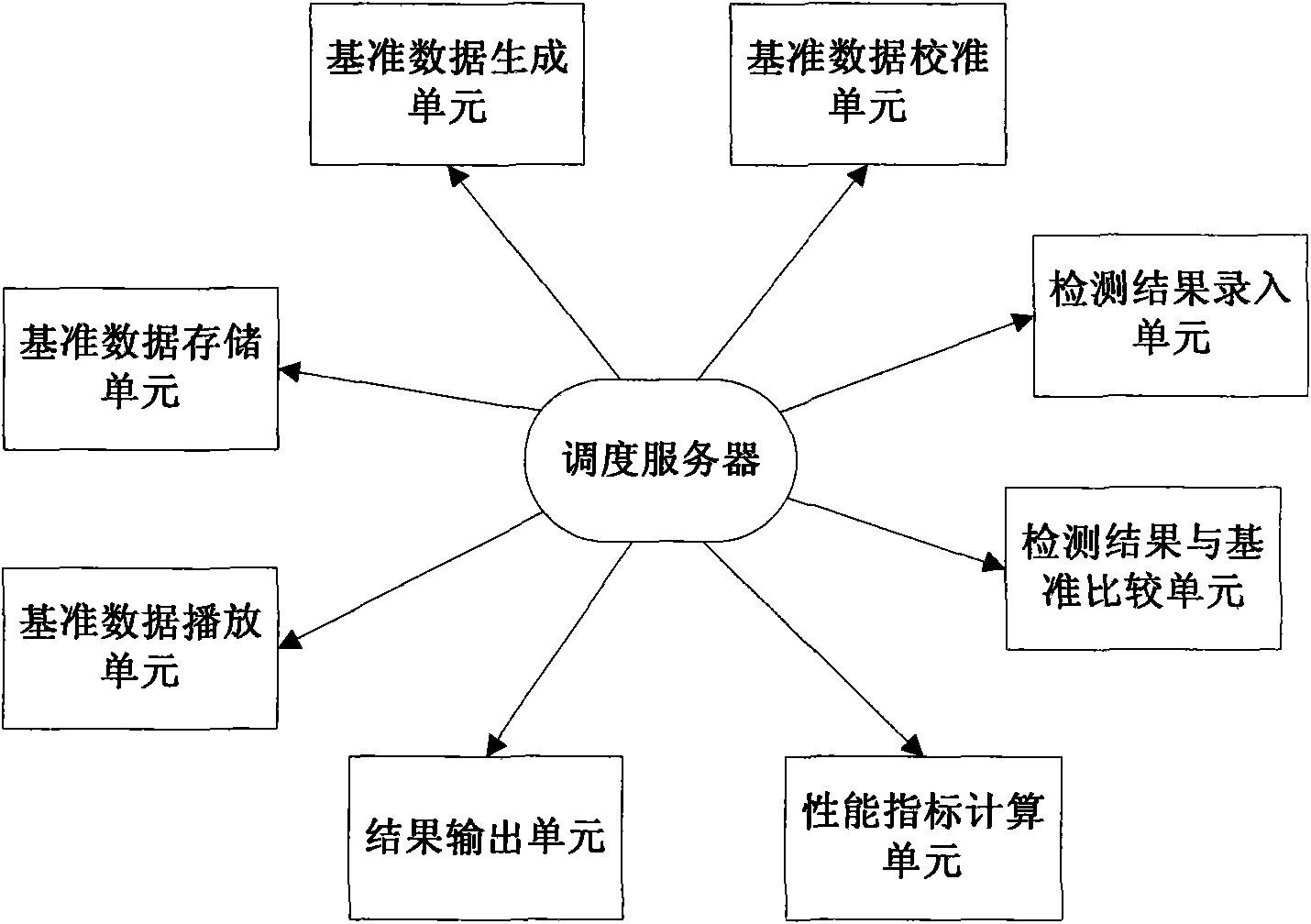
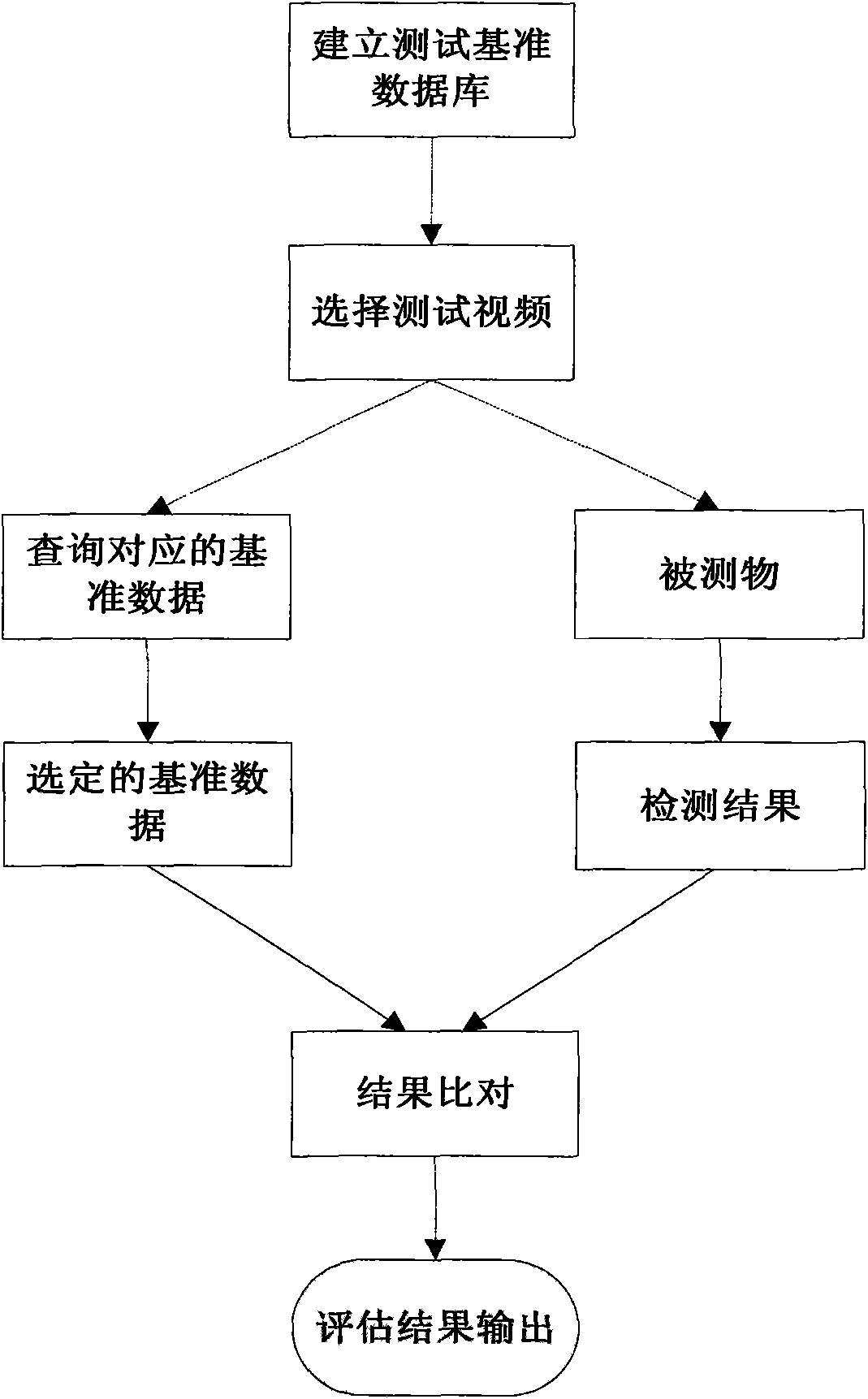
The invention provides an intelligent video monitoring system and a performance test method of an algorithm thereof. The test method is completed by a test system composed of a reference data generation unit, a reference data calibration unit, a reference data storage unit, a reference data playing unit, a detection result input unit, a detection result and reference comparing unit, a performanceindex calculation unit, a result output unit and a scheduling server. The method for testing the intelligent video system or the algorithm comprises the following steps: firstly establishing a reference database for testing, and sequentially performing reference data generation, calibration and storage on a video for testing; then selecting the test video, performing function detection on the tested system or the tested algorithm on the selected test video, and storing a detection result as an XML file with a specified format; and finally comparing the file with the reference data corresponding to the video, and outputting a comparison and evaluation result in a text and graphics mode.
Owner:BEIJING ZHONGDUN SECURITY TECH DEV +1
Memory based method for searching quickly the longest matching of IP address
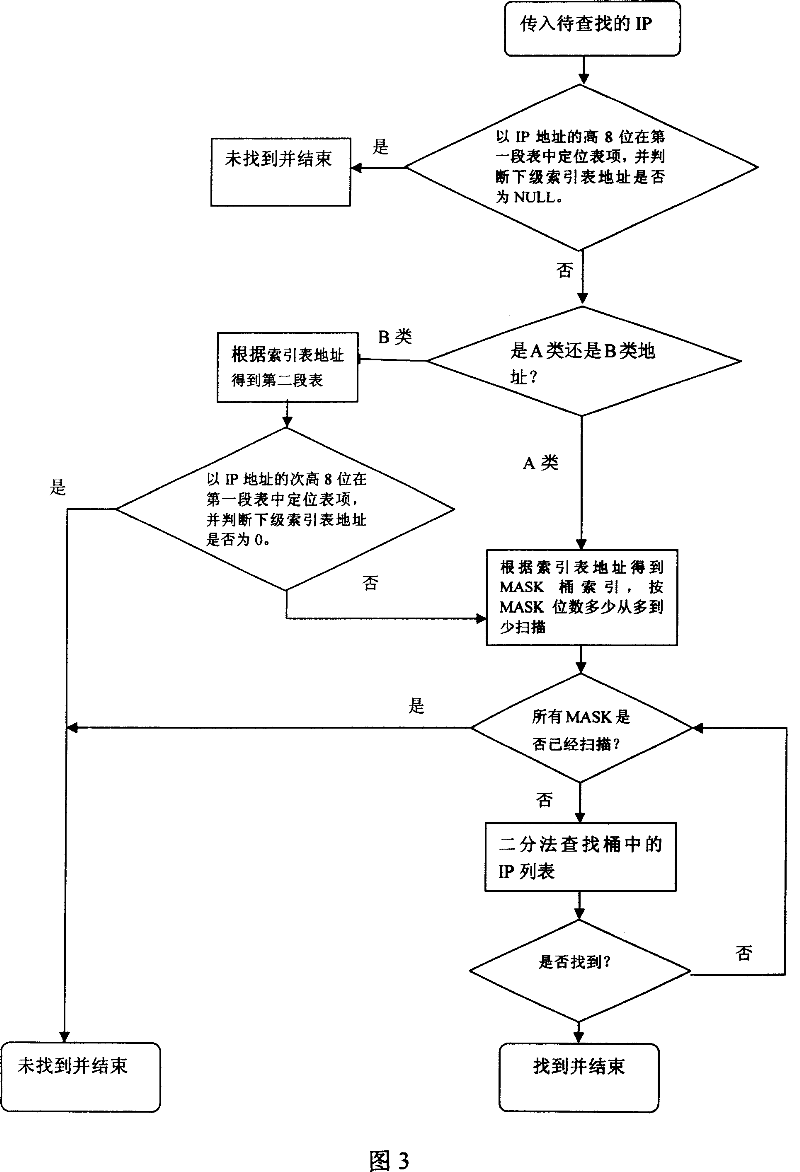
InactiveCN101043421ASimple methodImprove efficiencyData switching networksSpecial data processing applicationsIp address8-bit
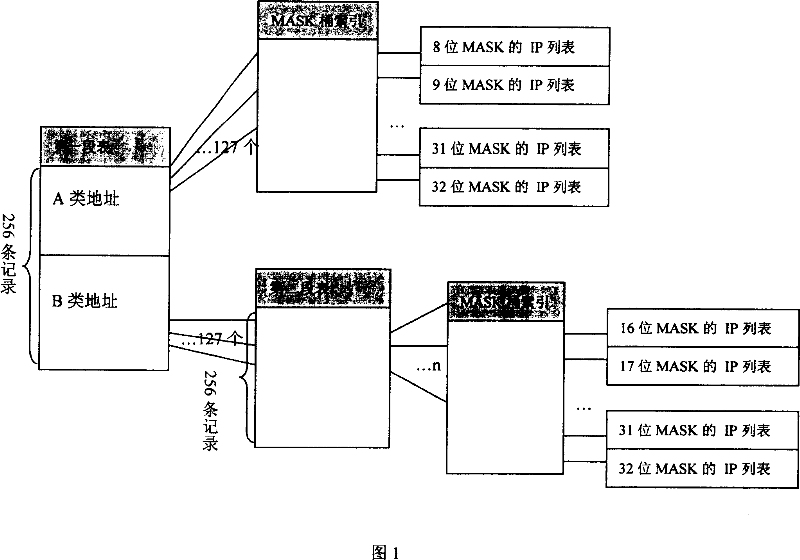
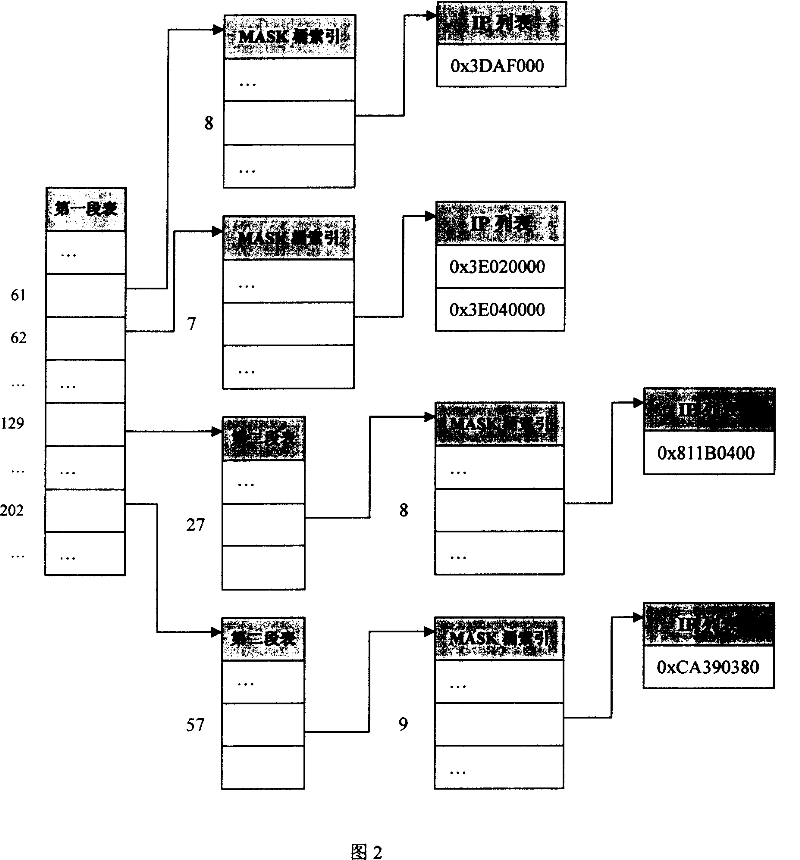
The related fast lookup method based on memory IP address longest match comprises: first, classifying the IP address into the A and B type, building index tree with 8-bit as one segment, setting A-type address as one layer, and B-type address as two layers; to the bottom layer, building a MASK bucket index every connecting an IP sequence table for storing the final IP item; when looking up, deciding the coming IP address as A- or B-type; for A type, according to the obtained MASK bucket index, using bisection way for matching from the 32-bit MASK IP table till finding out or failure; for B type, leading into the second segment table, locating in the second segment table by inferior 8-bit of IP address, then leading into the MASK bucket index as the A type. This invention is high efficient and fast.
Owner:上海复娱文化传播股份有限公司
R wave detection algorithm based on extremum field mean mode decomposition and improved Hilbert enveloping
InactiveCN103190901AImprove detection accuracyFast operationDiagnostic recording/measuringSensorsEcg signalElectricity
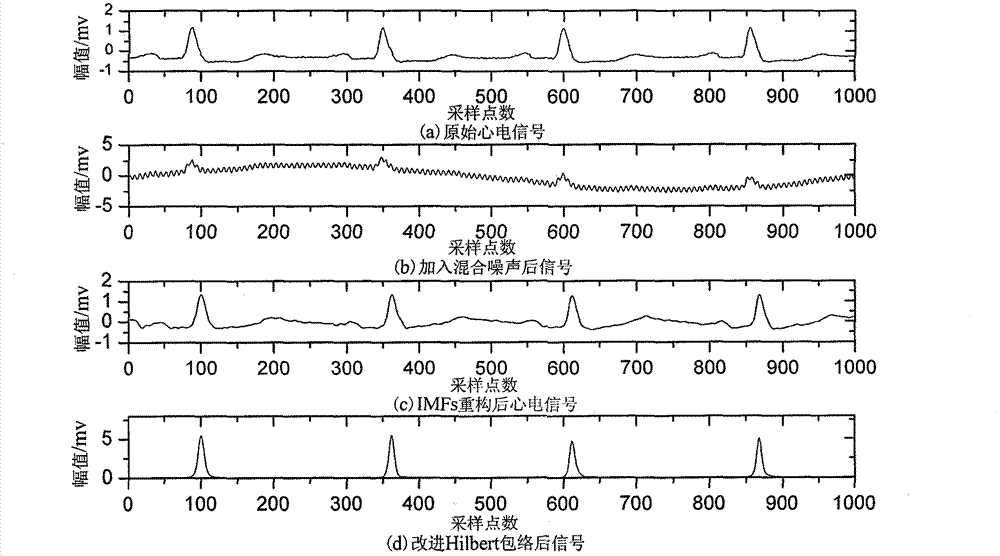
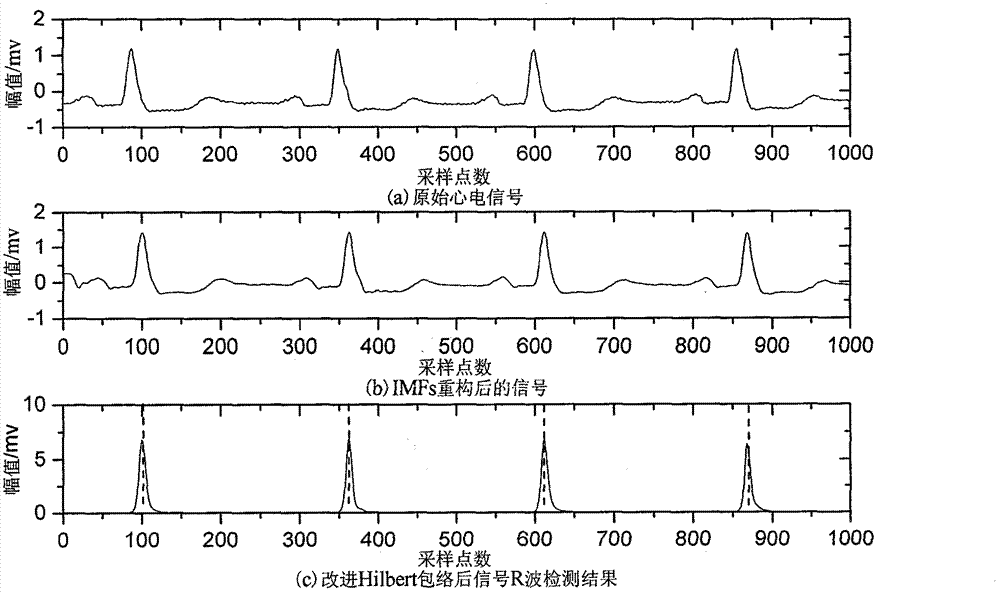
The invention discloses an R wave detection algorithm based on extremum field mean mode decomposition and improved Hilbert enveloping and belongs to the technical field of weak biological signal processing. An electrocardio signal pre-processing algorithm based on the extremum field mean mode decomposition and the improved Hilbert enveloping and an R wave detection algorithm based on slope threshold are provided. Detection criteria are set according to wave form characteristics and time domain distribution characters of electrocardio signals, and positions of R waves with most obvious characters and highest information amount in the electrocardio signals are detected. An extremum field mean mode decomposition algorithm improves empirical mode decomposition speed and can effectively restrain mode superimposition and boundary effect. The improved Hilbert enveloping can effectively restrain interference of noise and other characteristic waves an can also enhance energy of the R waves. The R wave detection algorithm based on the extremum field mean mode decomposition and the improved Hilbert enveloping can also detect positions of R points accurately even if interference of strong noise and large P / T waves exists. A Massachusetts institute of technology-Beth Israel hospital (MIT-BIH) data base is used for detecting the R wave detection algorithm. Sensitivity of the R wave detection algorithm is 99.94%, and positive predictive rate is 99.87%.
Owner:TIANJIN POLYTECHNIC UNIV
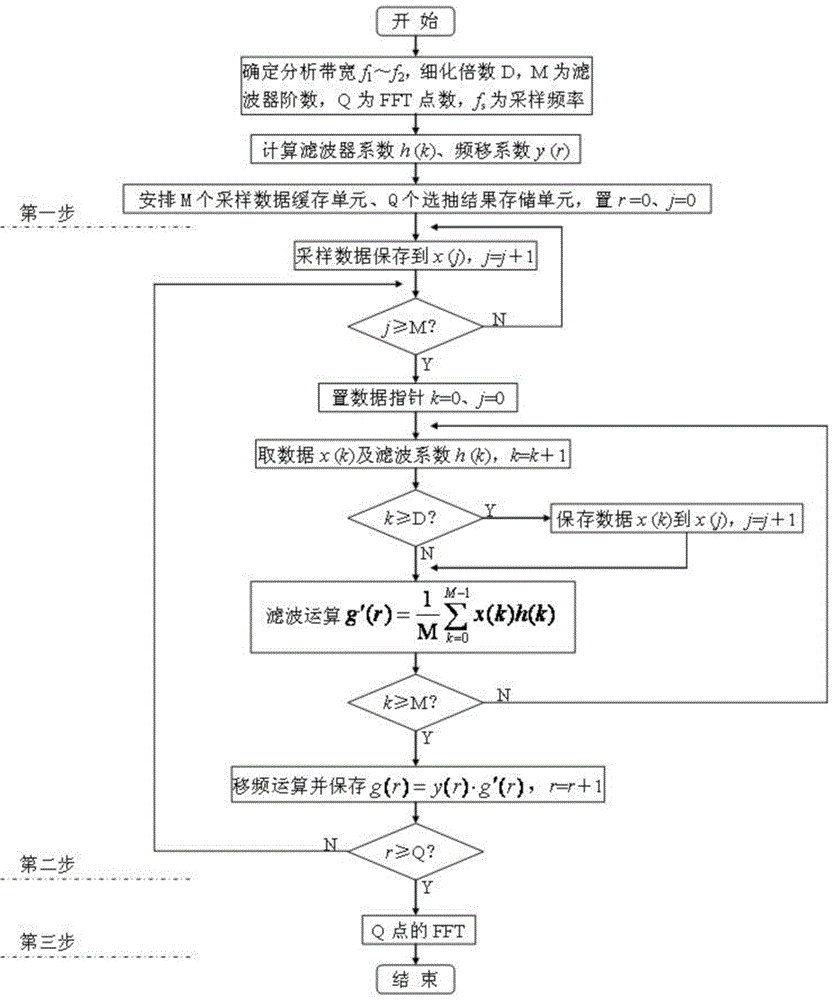
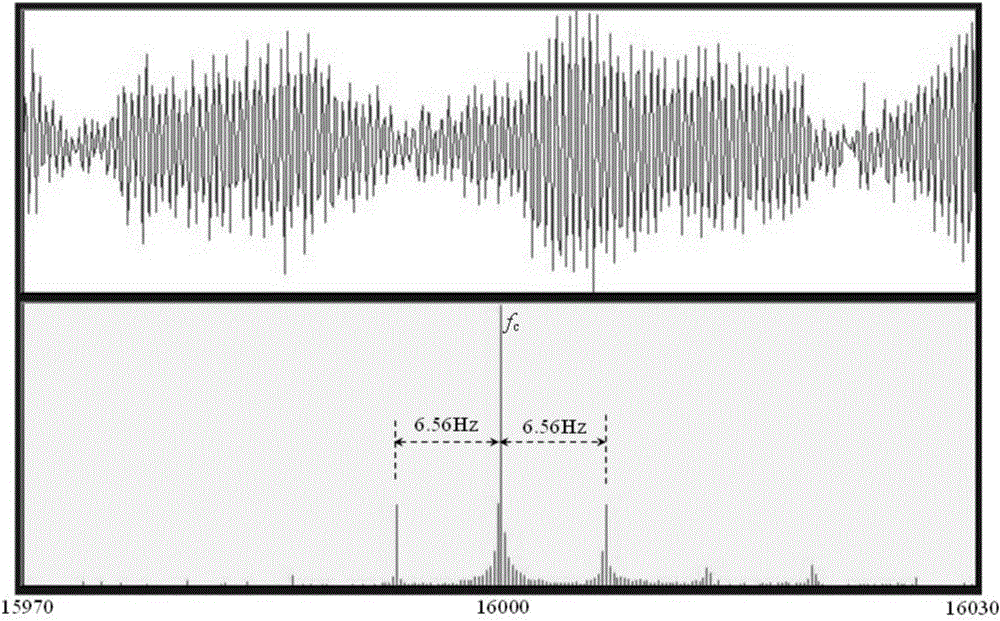
DSP-based real time ZFFT method
ActiveCN105911351AStrong digital processing abilityTakes up little memory spaceFrequency analysisFrequency shiftSpectral line
The invention discloses a DSP-based real time ZFFT method comprising the following three steps: (1) a filter coefficient and a frequency shift coefficient of a ZFFT are calculated offline and temporarily stored according to application needs; (2) data sampling operation is carried out while online ZFFT data selecting, filtering and frequency shift operation is conducted; (3) after a result of step (2) is subjected to offline FFT operation, refined spectral line with required bandwidth can be obtained. According to the DSP-based real time ZFFT method, ZFFT operation characteristics and strong digital processing capability of a DSP are effectively utilized; ZEET data selecting and sampling are combined, and filtering and frequency shift operation is performed after being dispersed to a plurality of sampling periods; a refined spectral line in an analyzed bandwidth scope can be obtained with only an FFT of a Q point when sampling operation ends; compared with a conventional ZFFT method, the DSP-based real time ZFFT method is advantaged by small occupied memory space, good real-time property, and capability of meeting requirements of online monitoring and real time signal analyzing and processing systems.
Owner:HUNAN UNIV OF SCI & TECH
Method for realizing single-mode RAIM (Receiver Autonomous Integrity Monitoring) under small number of visible satellites based on assistance of clock correction
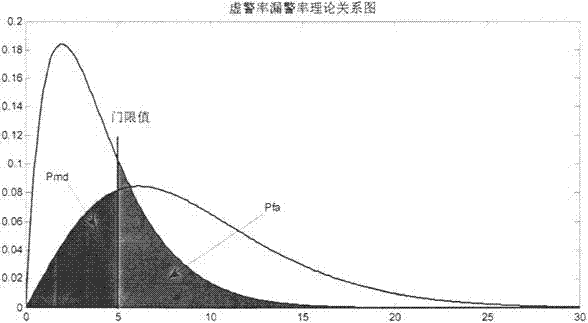
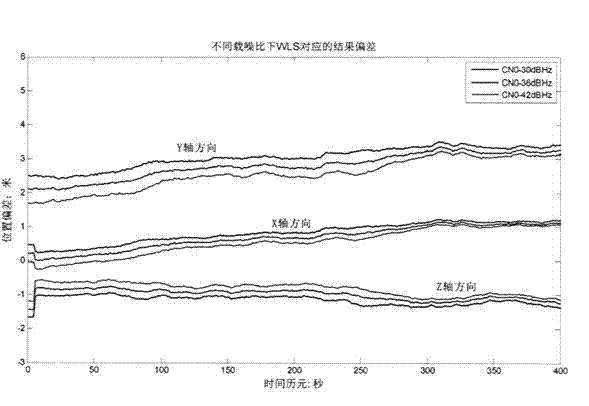
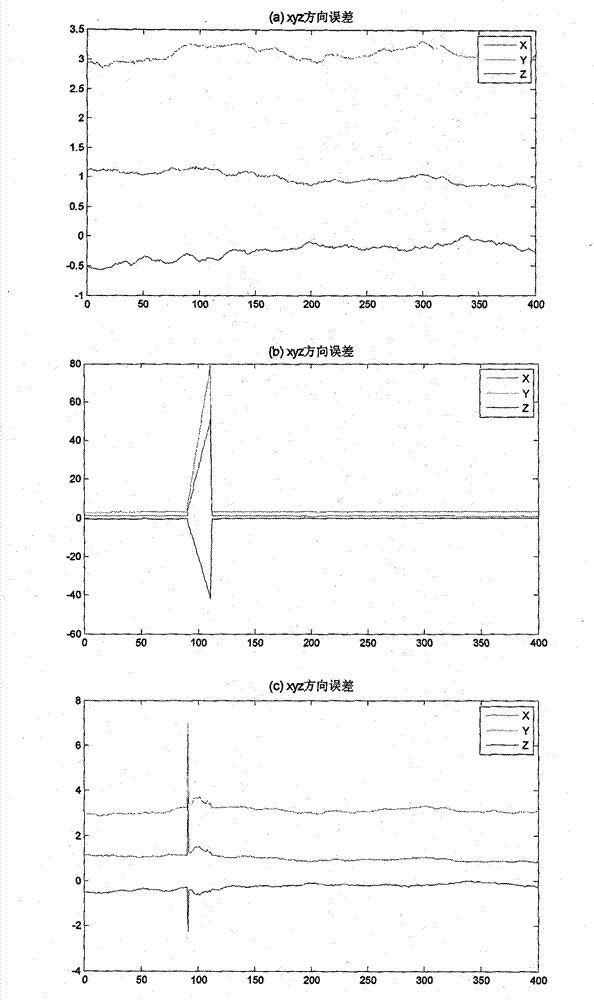
InactiveCN103592657AHigh precisionEasy to implementSatellite radio beaconingClock rateClock correction
The invention discloses a method for realizing single-mode RAIM (Receiver Autonomous Integrity Monitoring) under a small number of visible satellites based on assistance of clock correction, which is a method for realizing single-mode RAIM under the condition that the number of the visible satellites is small in loop tracking. Clock correction prediction is carried out through a Newton interpolation model under the premise that the clock frequency of a receiver is stable, and detection and elimination of a fault satellite can be carried out under the condition that the number of the visible satellites is five, thereby improving the positioning precision, the continuity and the stability of the receiver. The method comprises the steps of: first, determining weight factor in weighted least squares through parameters such as a carrier-to-noise ratio and the like of satellite signals; then, carrying out RAIM availability detection through a false alarm rate, a missed alarm rate, an observation equation and a weight matrix, determining a detection threshold value by using a tolerant false alarm rate in a non-precision condition, and carrying out clock correction prediction for the receiver through the Newton interpolation model so as to realize detection and elimination of the fault satellite, and finally, carrying out analysis and comparison on a dilution of precision (DOP) after a clock correction auxiliary equation is added. The method disclosed by the invention can realize detection and elimination of the fault satellite under the condition that only one redundant satellite exists, reduces the space dilution of precision through the clock correction auxiliary model, and improving the positioning accuracy of the receiver and the system robustness.
Owner:PEKING UNIV
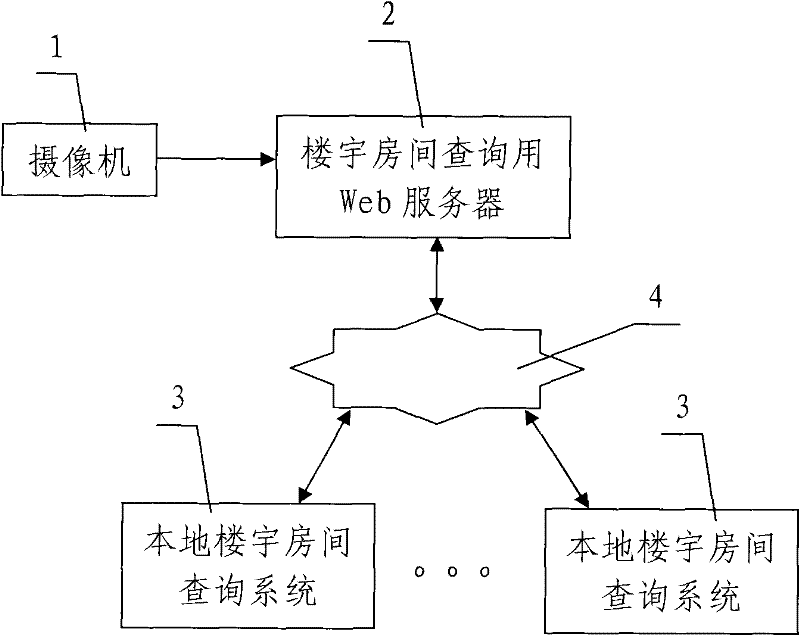
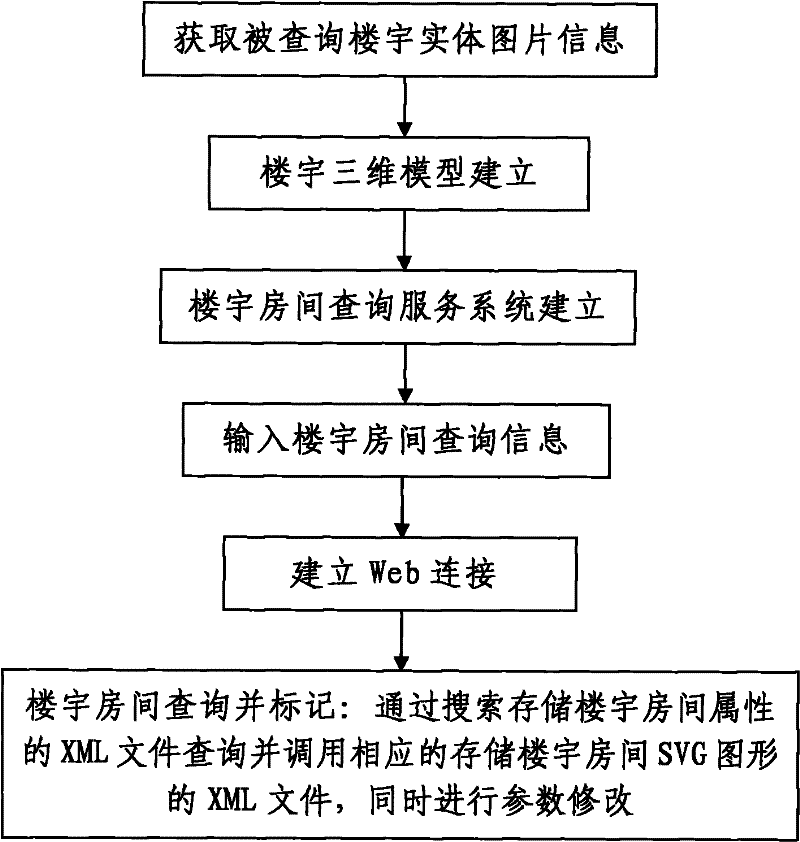
SVG-based Web GIS building room query system and query method
InactiveCN101751477ANovel and reasonable designEasy to operateSpecial data processing applicationsGraphicsWeb service
The invention discloses a SVG-based Web GIS building room query system and a query method; the query system comprises an image acquisition system, a building room query Web server and a local building room query system; wherein, the local building room query system is connected with the building room query Web server through Internet or LAN. The query method includes the following procedures: the query information is inputted to the local building room query system, the building room query Web server searches the XML files of building room attributes and calls the SVG file which stores the building room graph correspondingly, and then the SVG file is marked to inform the user the specific location information of the queried room. The SVG-based Web GIS building room query system and the query method has reasonable design, low investment cost, high query speed and good query effect, also has high popularization value, can solve the defects that the building query method in prior art has high investment cost, complicated operation procedures, and lacks of generality and flexibility in practical application.
Owner:CHANGAN UNIV
Method for rapidly retrieving picture
ActiveCN101308502AReduce occupancyHigh speedSpecial data processing applicationsInput/output processes for data processingThumbnailHand held
The invention discloses a rapid image retrieval method, relating to a method which retrieves and displays digital images; the method solves the problem of complicated retrieval input. The method of the invention comprises the following steps: the process of creating and storing the comparison table between an image name assembly and a simplified name alphabet on an image processing device; the process of storing images on a storage medium; the process of establishing an image file chain table on the image processing device based on the images stored on the storage medium; the process of creating a hash table of the image simplified names on the image processing device based on the alphabet of the comparison table and the image file chain table; and the process of retrieving the images on the storage medium by simplified names and displaying the thumbnails of the retrieval result on the image processing device through the hash table and the image file chain table. The method of the invention enables the operator to input the simplified names of the images during the retrieval process, so as to avoid the image names expressed in complicated vocabulary; therefore, the method requires small input amount and is simple to operate, which occupies small storage space and has fast speed in the middle process; the method is suitable for hand-held image browsing devices.
Owner:NANJING WANLIDA TECH
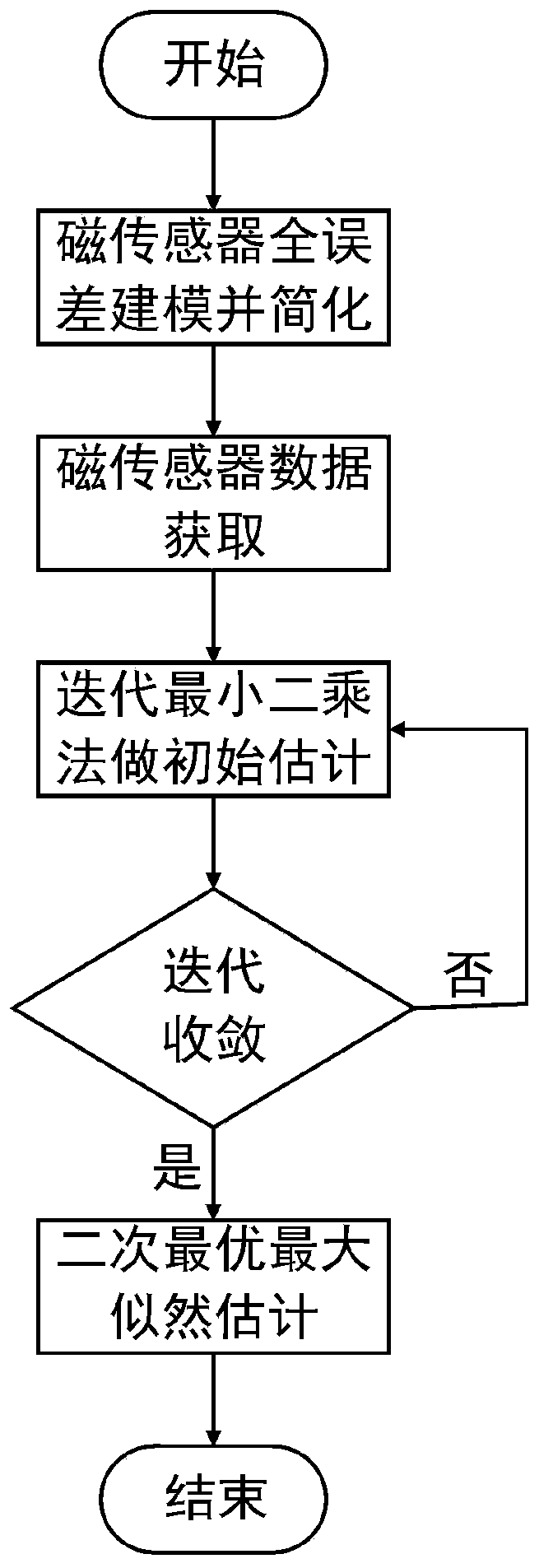
Real-time calibration method for magnetic sensor
ActiveCN110174123ALow costEasy to operateMeasurement devicesDesign optimisation/simulationComputer scienceLeast squares
The invention discloses a real-time calibration method of a magnetic sensor. The method comprises the following steps: establishing a magnetic sensor measurement full error model and integrating to obtain a simplified measurement model; rotating the magnetic sensor, and acquiring a plurality of groups of three-axis data of the magnetic sensor in the rotating process; obtaining an ellipsoid trajectory model according to the plurality of groups of three-axis data and the simplified measurement model, and obtaining an estimation of the magnetic calibration parameters based on an iterative least square method; and on the basis of iterative estimation, completing the estimation of the parameters of the magnetic sensor by adopting secondary unbiased maximum likelihood estimation. The real-time calibration method of the magnetic sensor does not need the assistance of large-scale equipment, and is low in cost, small in calculated amount and simple and convenient to operate.
Owner:SUZHOU UNIV
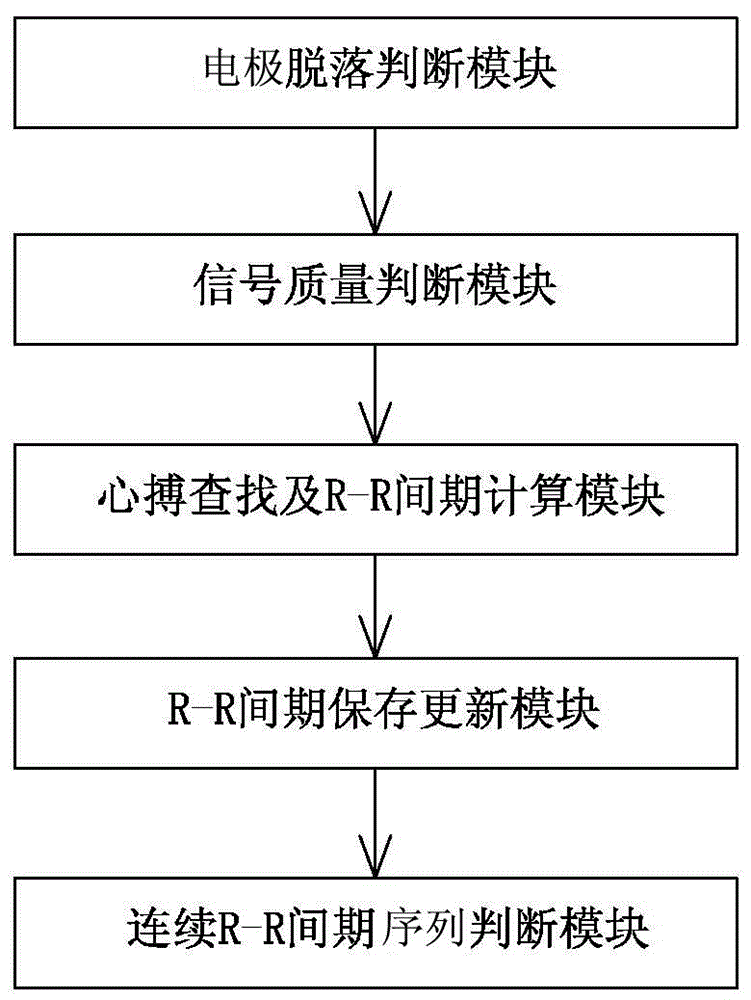
Method for handheld electrocardio detector to automatically start electrocardiogram recording
ActiveCN104783783AEfficient collectionEfficient analysisDiagnostic recording/measuringSensorsWaveform analysisHand held
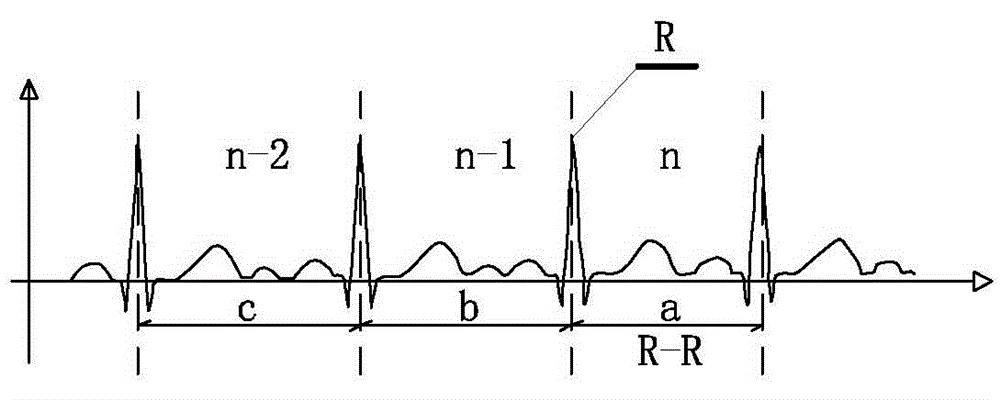
The invention discloses a method for a handheld electrocardio detector to automatically start electrocardiogram recording. The method comprises the steps of judging whether an electrode disengages through an acquired signal, judging whether an interference signal in electrocardiogram signals exceeds a set value through the acquired signal, and judging whether the electrocardiogram signals are stable. According to the method, by adding stability judgment, interference waves are further filtered out, the R-R interval judgment method is adopted for stability judgment, waveform interference situations such as weak signals and severe interference are effectively eliminated, analysis of various waveforms such as normal electrocardiogram waveform and bigeminy, trigeminy, quadrigeminy waveforms can be achieved, and finally high-quality, low-interference and effective electrocardiogram waveforms are acquired and analyzed.
Owner:CONTEC MEDICAL SYST
Method and device for realizing NAT
InactiveCN106331196ASimple structureMeet diverse needsTransmissionInternal memoryResource utilization
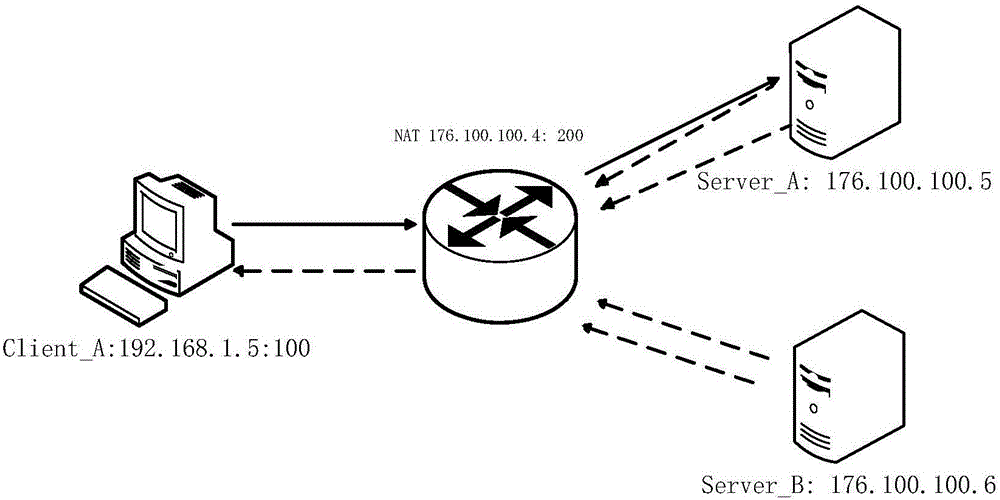
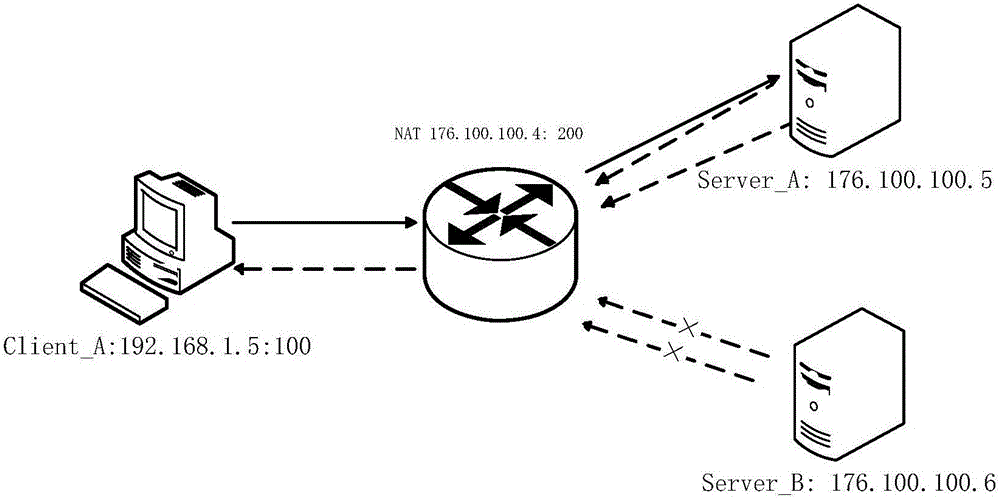
The invention discloses a method and device for realizing NAT. The method comprises the following steps: creating a mapping table and a filtering table, and correspondingly setting a first key value and a second key value for inquiring the mapping table and the filtering table; when a message is sent from a private network to a public network, realizing address NAT conversion via the mapping table; when the message is sent from the public network to the private network, realizing the address NAT conversion via the filtering table; and then forwarding the message after the NAT conversion. By adoption of the method and device disclosed by the invention, diversified demands of users can be satisfied, and the mapping table and the filtering table are simple in structures, small in internal memory space occupation and high in query efficiency. In the method and device disclosed by the invention, an address mapping relation is recorded by the mapping table, therefore the ip resource utilization rate of the public network can be improved, moreover the times of accessing an address pool in the NAT conversion process of the message can also be greatly reduced, and thus the NAT efficiency is improved.
Owner:ZTE CORP
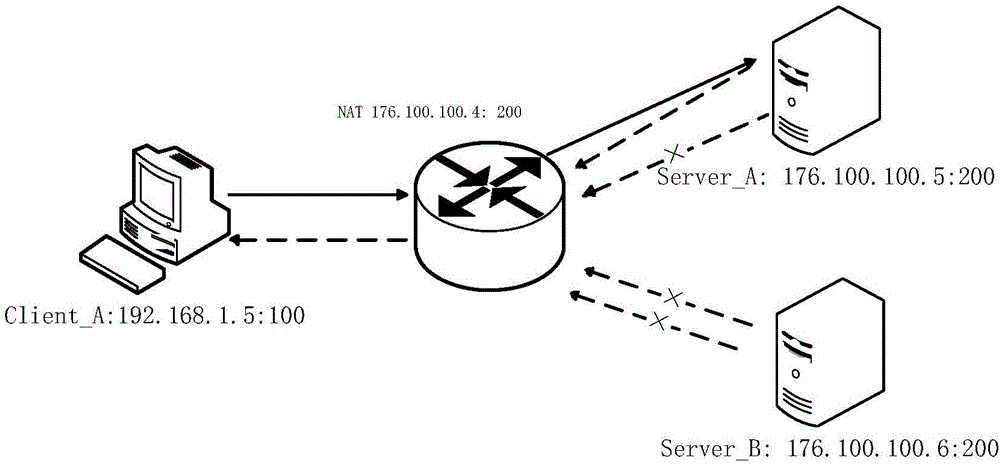
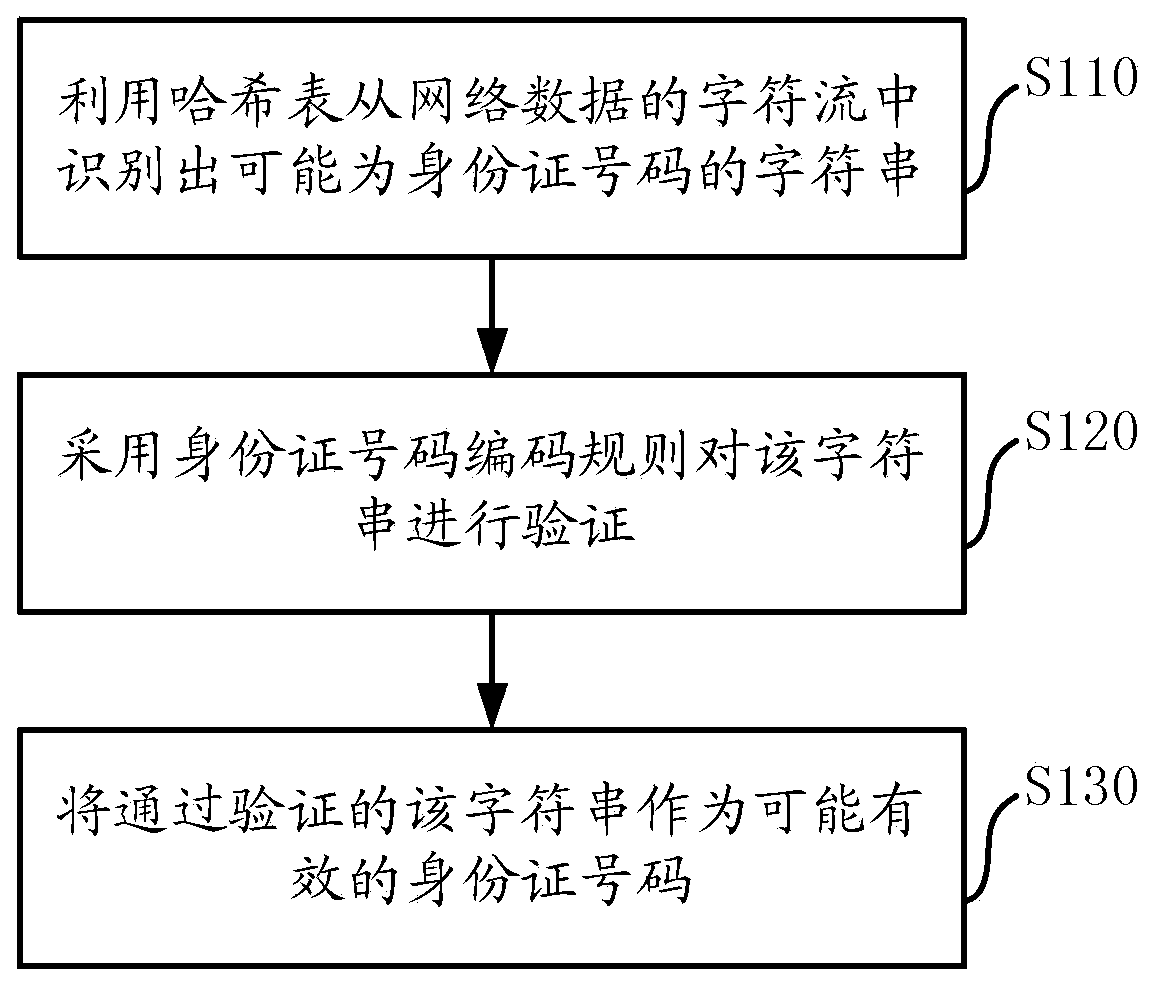
Recognition method and device of ID (identity) card numbers
InactiveCN104111932AImprove accuracyHigh speedSpecial data processing applicationsComputer hardwareNetwork data
The invention discloses a recognition method and device of ID (identity) card numbers and overcomes the defect that a mature method of recognizing ID card numbers from network data lacks at present. The recognition method includes: recognizing a character string, which may be an ID card number, from a character stream; verifying the character string, which many be the ID card number, according to ID card number encoding rules; using the ID card number, which may be the ID card number and which passes verification, as a positively effective ID card number. The recognition method and device of the ID card numbers according to the embodiment has the advantages that high-traffic webpage contents can be filtered and recognized in the network security field, accuracy is high, the speed is high, and small memory space is used in hardware equipment.
Owner:BEIJING VENUS INFORMATION TECH +1
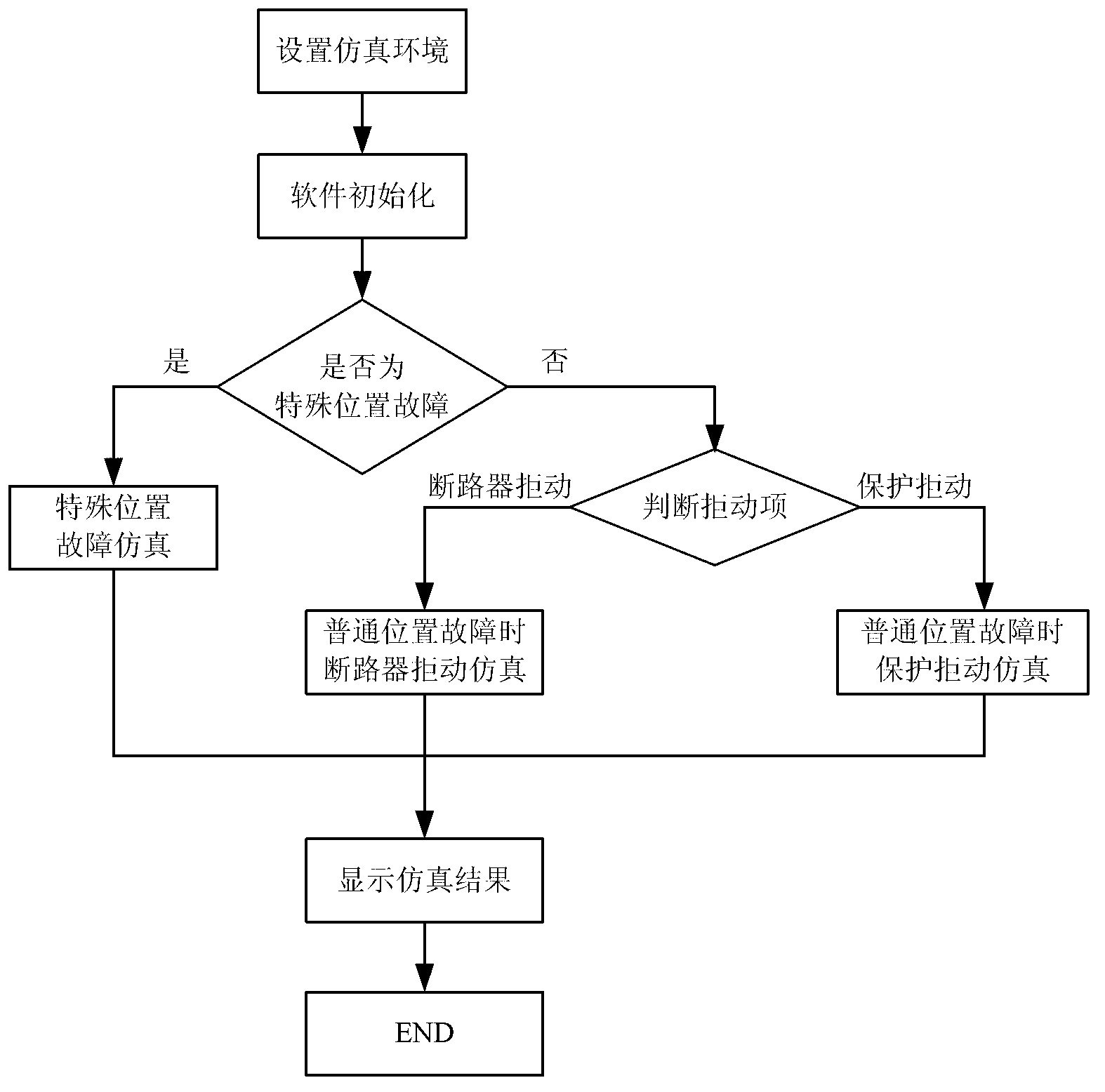
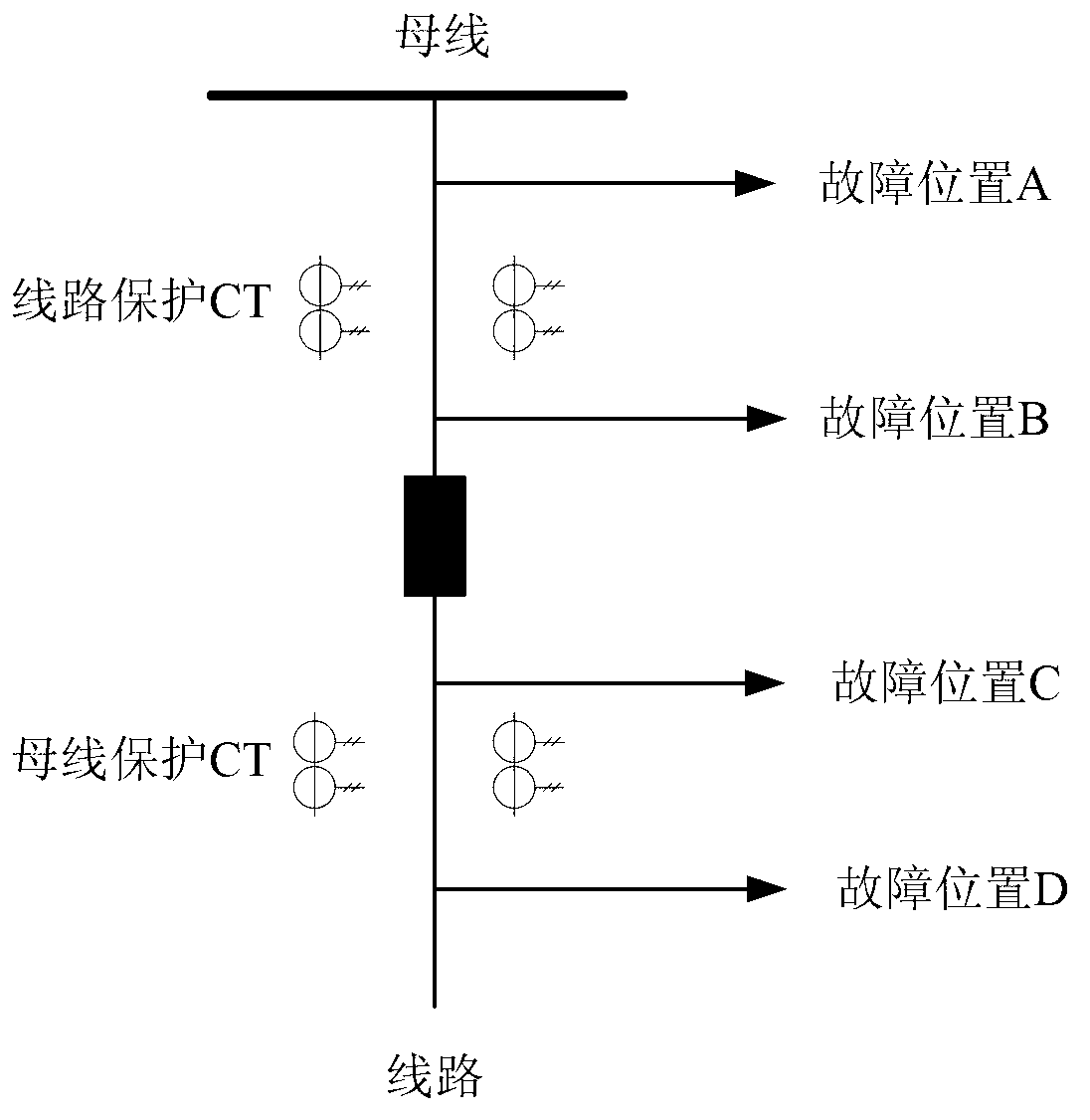
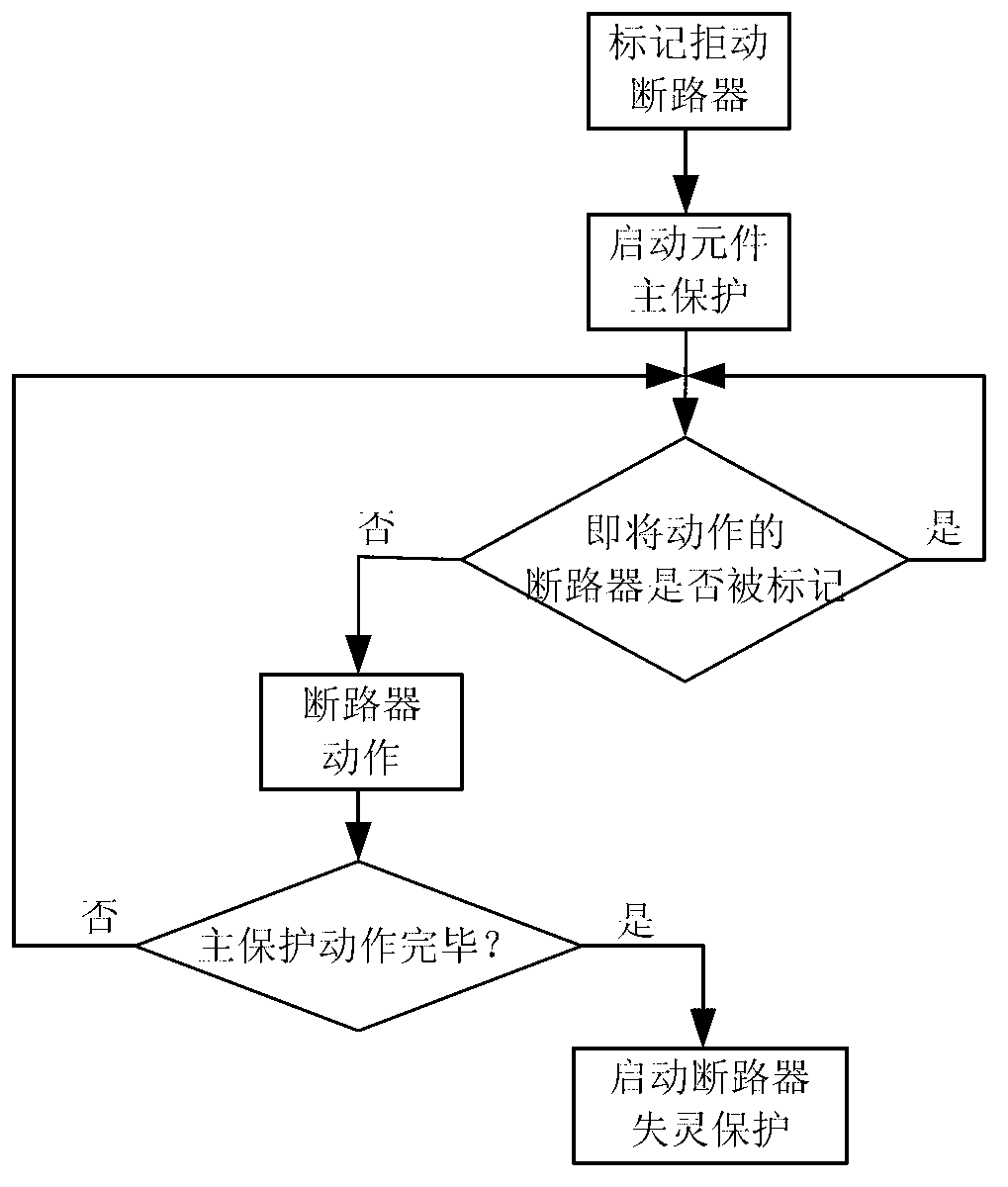
Simple and quick relay protection action simulation method for power system
ActiveCN103236682AEasy to set upPerfect simulation functionEmergency protective circuit arrangementsElectric power systemSimulation
The invention discloses a simple and quick relay protection action simulation method for a power system. The method comprises the following steps: providing a setting interface for a failure action simulation environment, and setting the simulation environment according to needs; identifying the set simulation environment, namely assigning values to corresponding variables to finish initialization work; performing simulation under conditions of different failure positions and different settings of an action refusing item; when a failure position is a special position, analyzing the advanced stripping or action refusing condition of line protection and bus protection; when the failure position is an ordinary position, and the action refusing item is circuit breaker action refusing, analyzing the action condition of protection in case of a circuit breaker failure; and when the failure position is an ordinary position, and the action refusing item is relay protection device action refusing, analyzing the condition of protection matching between upper-level and lower-level components. The method is simple and easy, unnecessary calculation is omitted, the operating time is shortened, a reference is provided for the check of relay protection setting, and a reliable result is obtained.
Owner:NANJING UNIV OF SCI & TECH
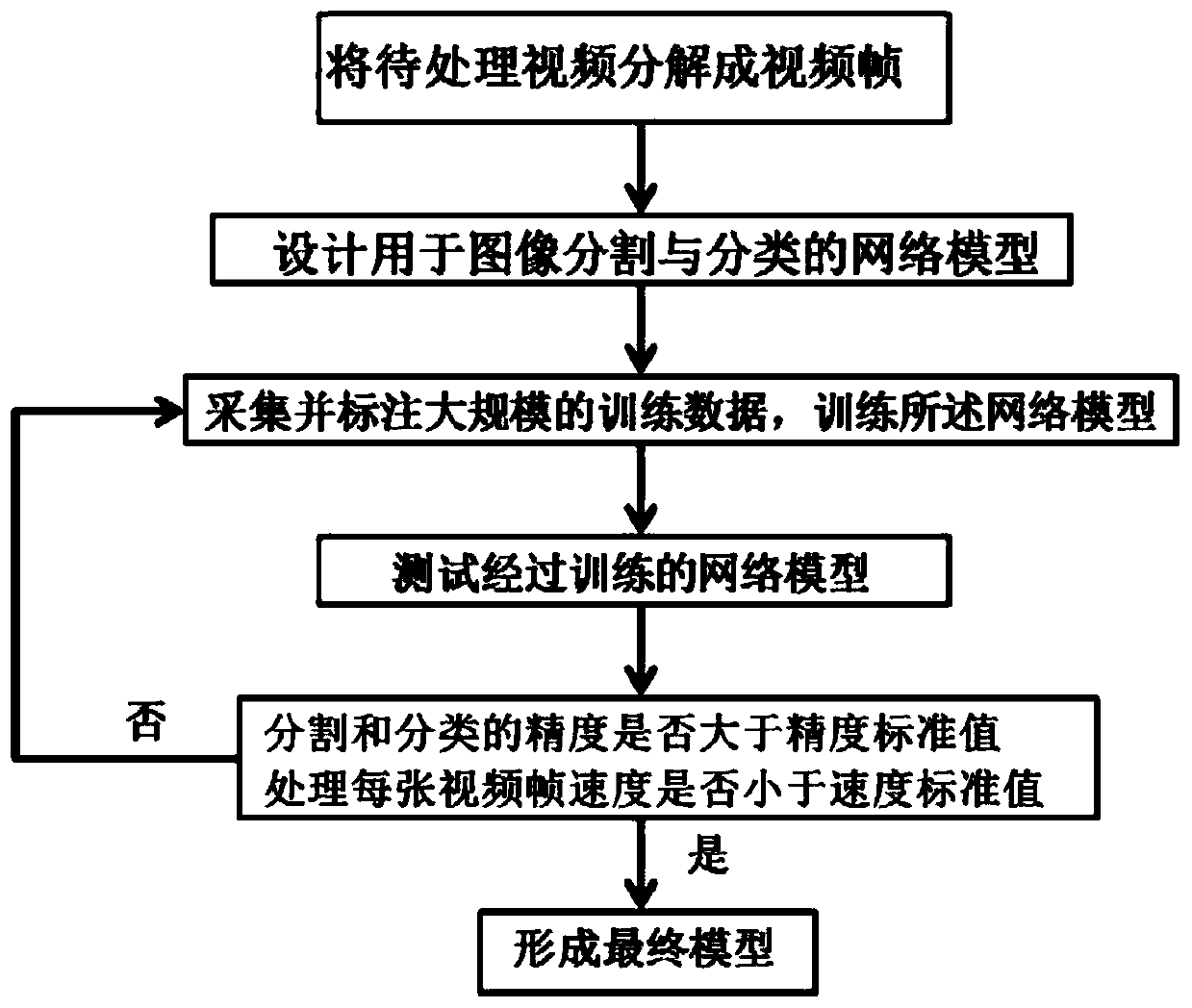
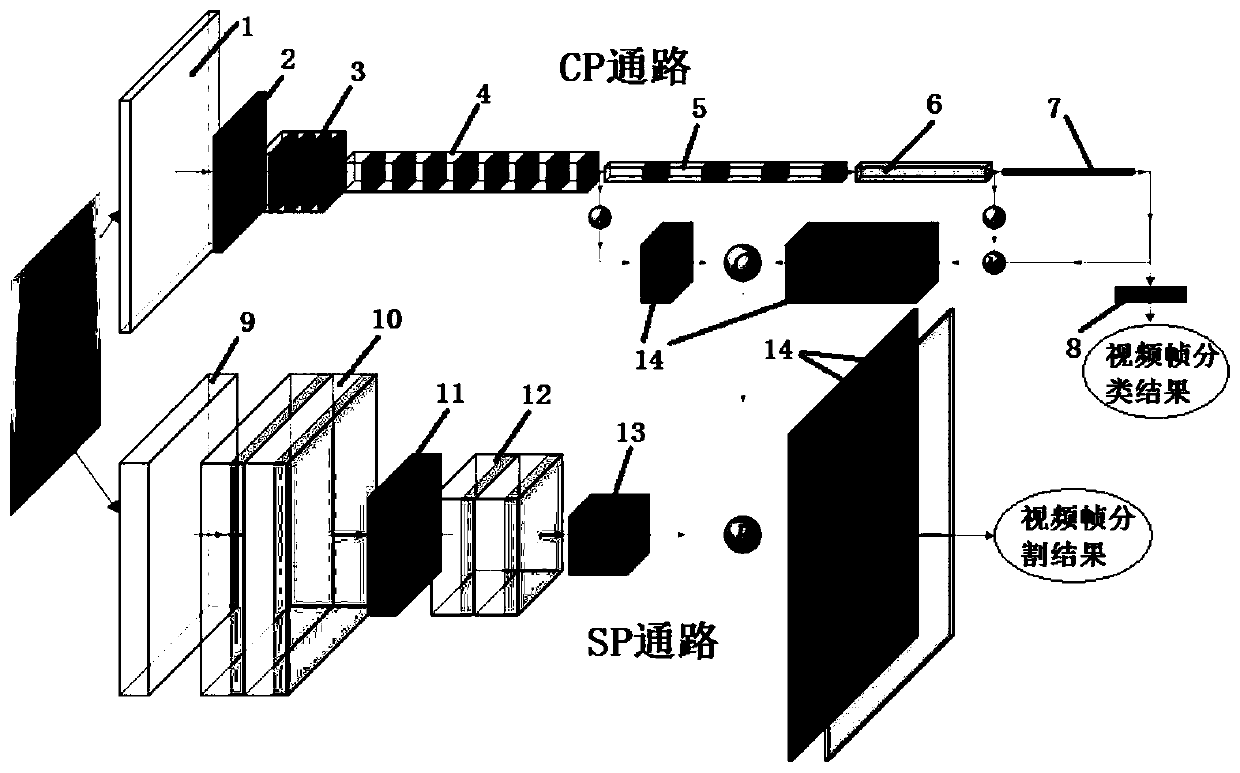
Image segmentation and classification method and device
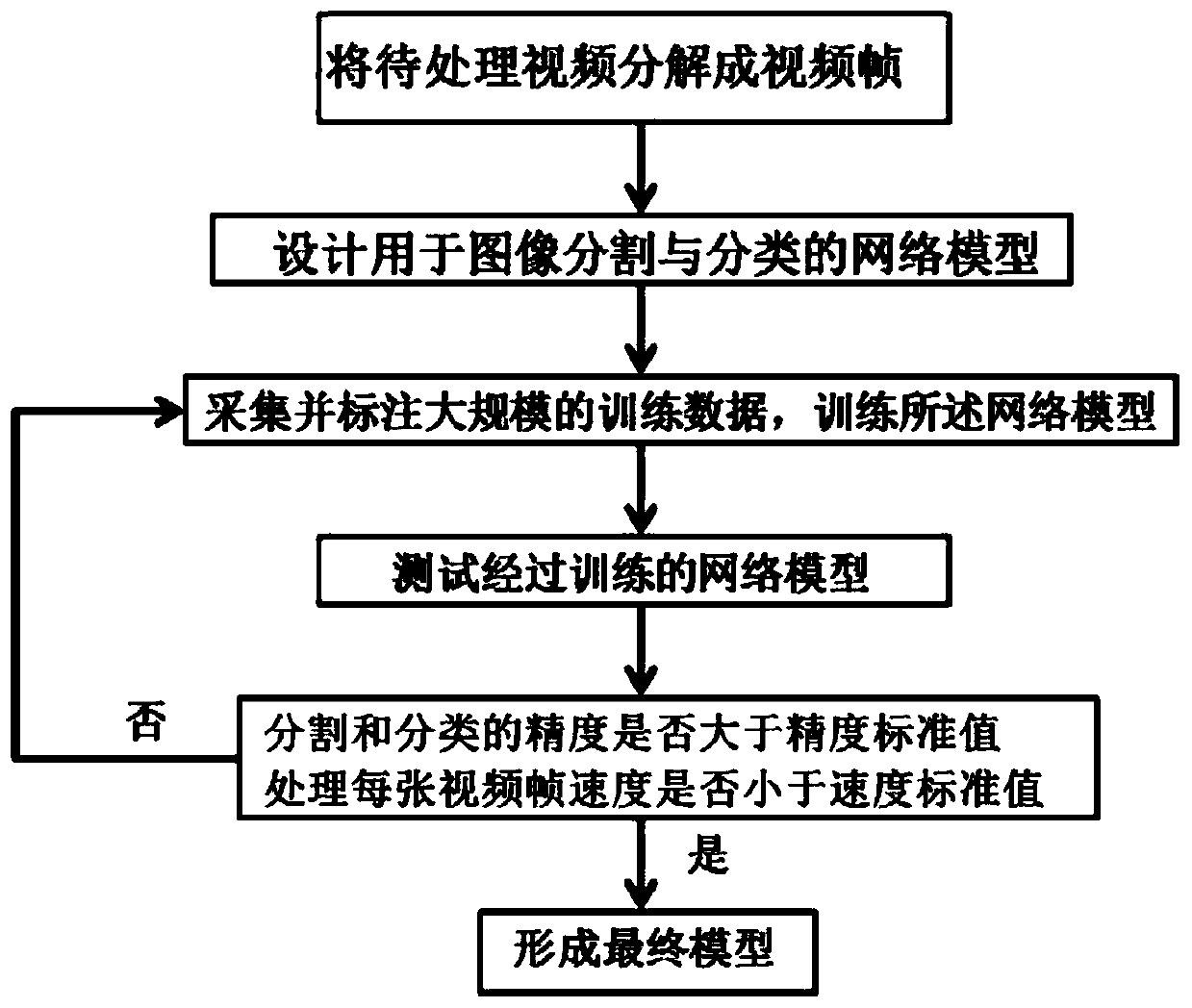
PendingCN111160356ATakes up little memory spaceFast splitCharacter and pattern recognitionNeural architecturesRadiologyClassification methods
The invention relates to an image segmentation and classification method and device, and the method comprises the steps: S1, building an image segmentation and classification network model, and achieving the segmentation and classification of image frames, wherein the segmentation and classification network model comprises a context information extraction path and a spatial information extractionpath, the context information extraction path is in communication connection with the spatial information extraction path, and the context information extraction path outputs an image classification result; the spatial information extraction path outputs an image segmentation result; and S2, training the segmented and classified network model to enable the network model to reach a preset standard.According to the network model for segmentation and classification in the method, end-to-end real-time semantic segmentation can be performed on the video acquired by the mobile terminal, the targetstate category of the scene in the image frame can be identified in real time, and semantic segmentation of the video and classification of the scene state in the image frame are completed in parallel.
Owner:CAPITALBIO CORP
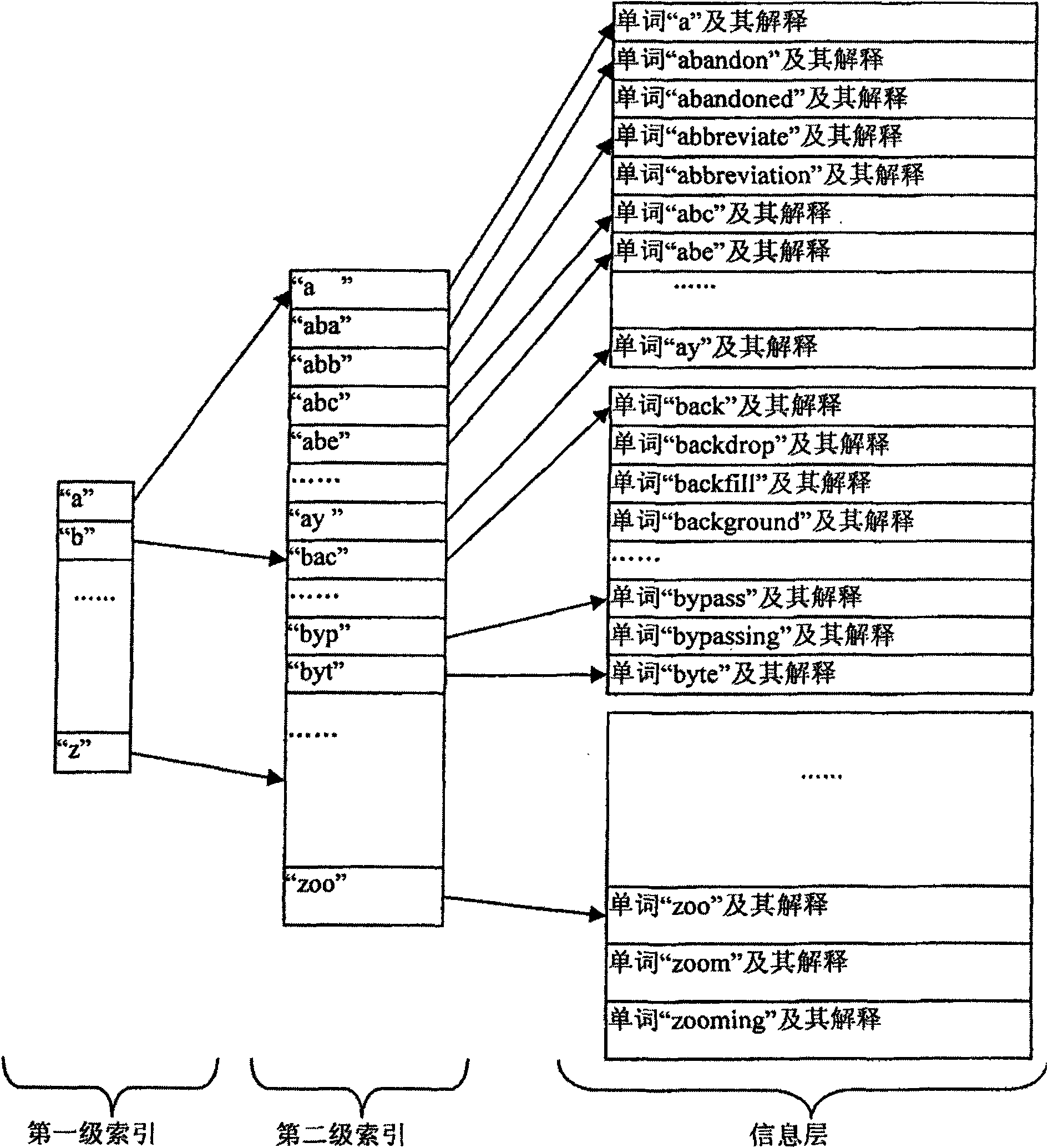
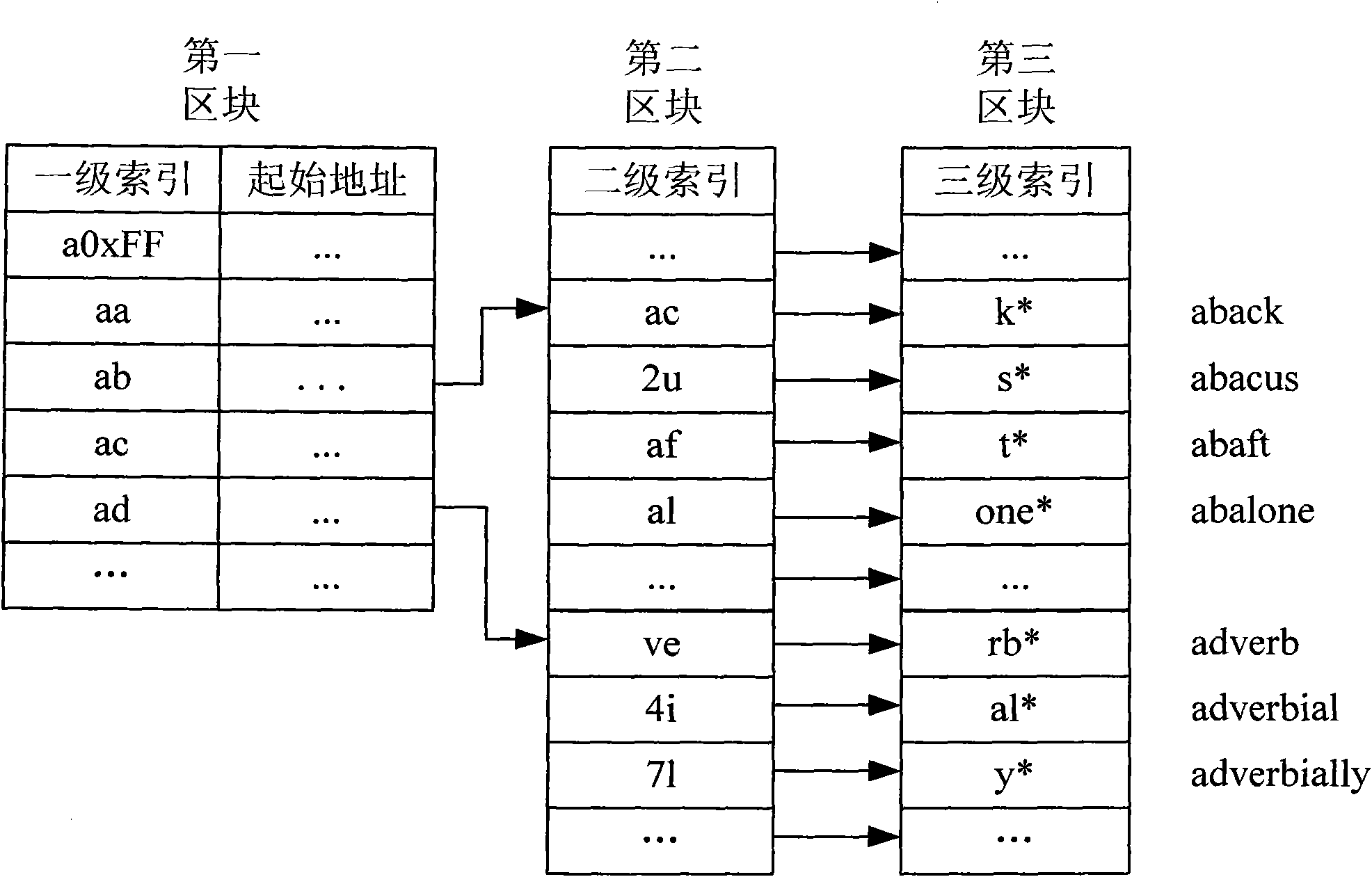
Lexicon creation method and system as well as corresponding word searching method and system
The invention discloses a lexicon creation method and a system as well as a corresponding word searching method and a system. Each word is divided into N letter groups; the lengths of the n'th letter group and the following letter group thereof are not fixed; a word base is divided into N blocks; the information of the nth letter group is respectively stored in each n-grade cell index; if the letters before the n'th letter group of the jth word and the (j-1)th word are the same and the number of the continuously same letters starting from the first letter of the n'th letter group is larger than 1, then the information of the n'th letter group stored by the jth n'-grade cell index is represented by the form of a number Rj plus the rest letters of the letter group, otherwise, the information is completely represented by the form of letters, wherein n' is equal to or more than 2 and is equal to or less than N; when indexing the inputted words, the number Rj in the n'-grade cell index is identified as the continuous Rj letters starting from the first letter of the n'th letter group of the word corresponding to the front n'-grade cell index of the same group. The invention can occupy less memory space simultaneously when quickly searching the word.
Owner:SUNPLUS TECH CO LTD +1
Management module of timer
The invention discloses a management module of a timer. The management module is typically applied to quality of service (QoS) software, timing overflow management of network data stream and the like. The management module comprises a multistage timing wheel in which the degrees of emergency of processed events are sequentially reduced from front to back and time units are sequentially increased from front to back, and the starting end of a back stage timing wheel is connected with the tail end of a front stage timing wheel adjacent to the back stage timing wheel. The management module of the timer has the advantages that the defects of large occupied internal storage space, long overflow check time and difficulty in determining the processing timing of the current active event in the prior art are overcome, so that small occupied internal storage space, short overflow check time, high expansibility and proneness to determining the processing timing of the current active event are achieved.
Owner:SUZHOU YUNCHU NETWORK TECH
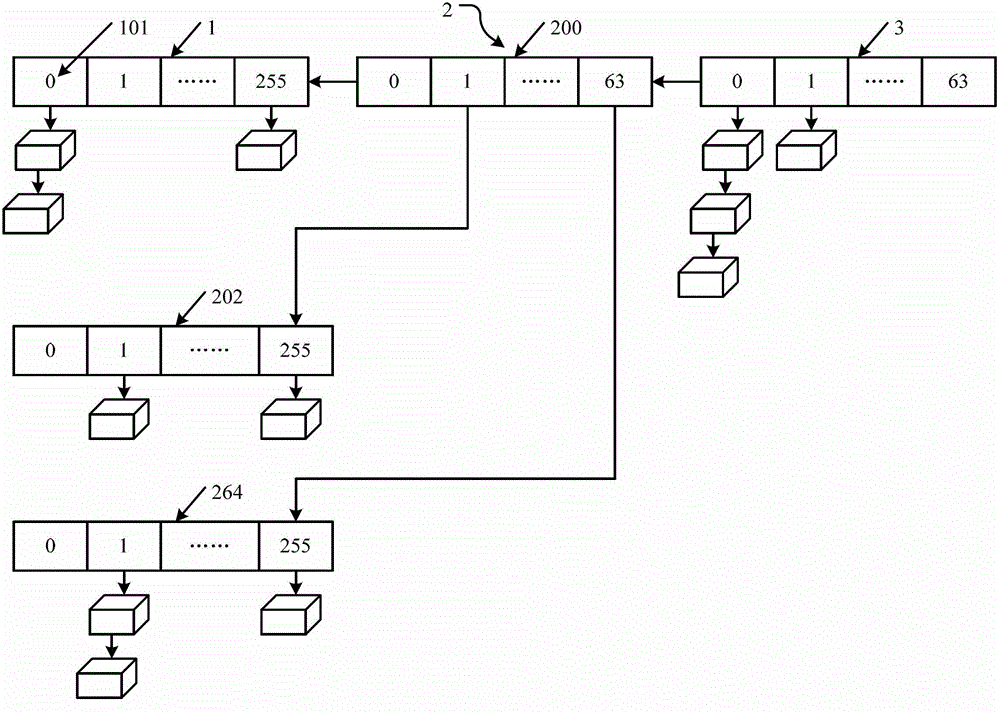
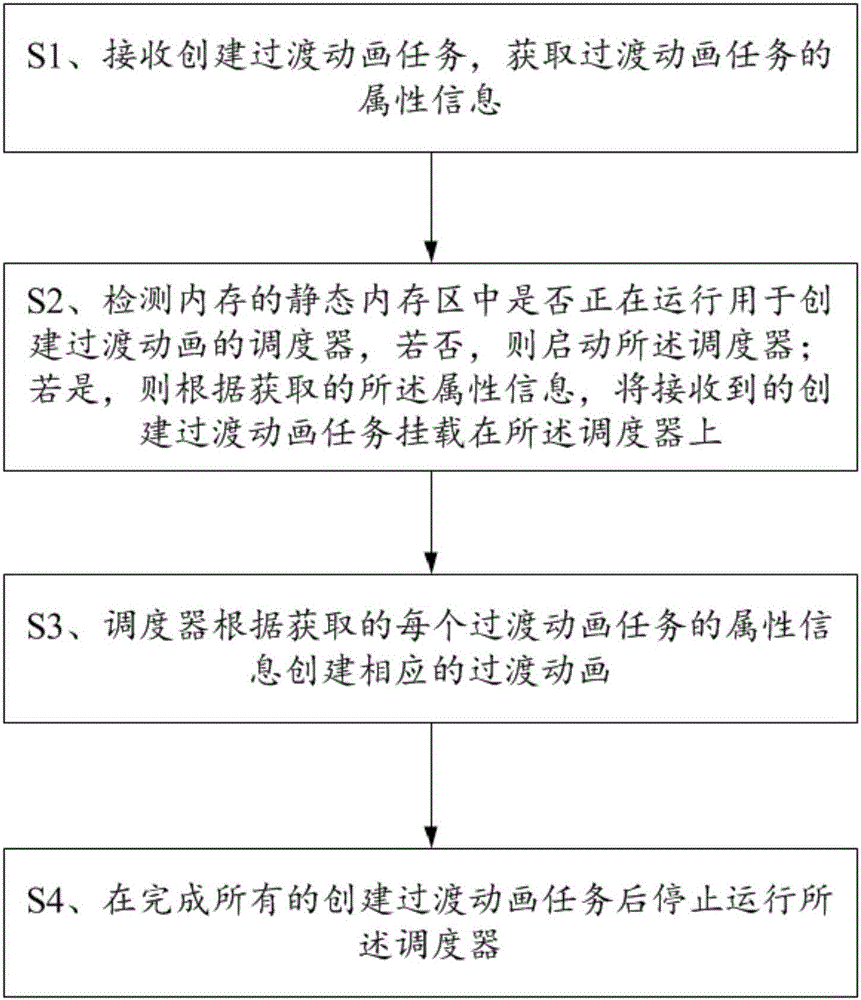
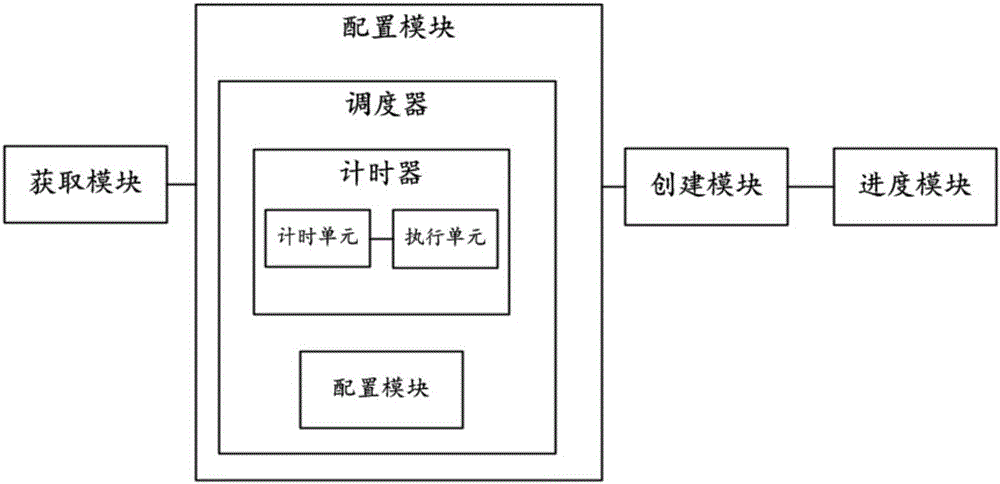
Method and apparatus for creating transition animations
The invention discloses a method for creating transition animations. The method comprises the following steps: S1: receiving a task for creating transition animations, and acquiring the attribute information of the transition animation task; S2: detecting whether a scheduler for creating transition animations is running in a static memory area of the memory, and if not, starting the scheduler and if so, mounting the received task for creating transition animations on the scheduler; S3: according to the attribute information of each acquired task for creating transition animations, creating the corresponding transition animations through the scheduler; and S4: stopping running of the scheduler after finishing all the tasks for creating transition animations. The invention also discloses an apparatus for creating transition animations. For the method and apparatus for creating transition animations, during the process for creating transition animations, when a new task for creating transition animations is received, the new task for creating transition animations is mounted on the scheduler, so that occupation of the operation resource for equipment is reduced and the utilization rate of CPU is improved.
Owner:ALIBABA (CHINA) CO LTD
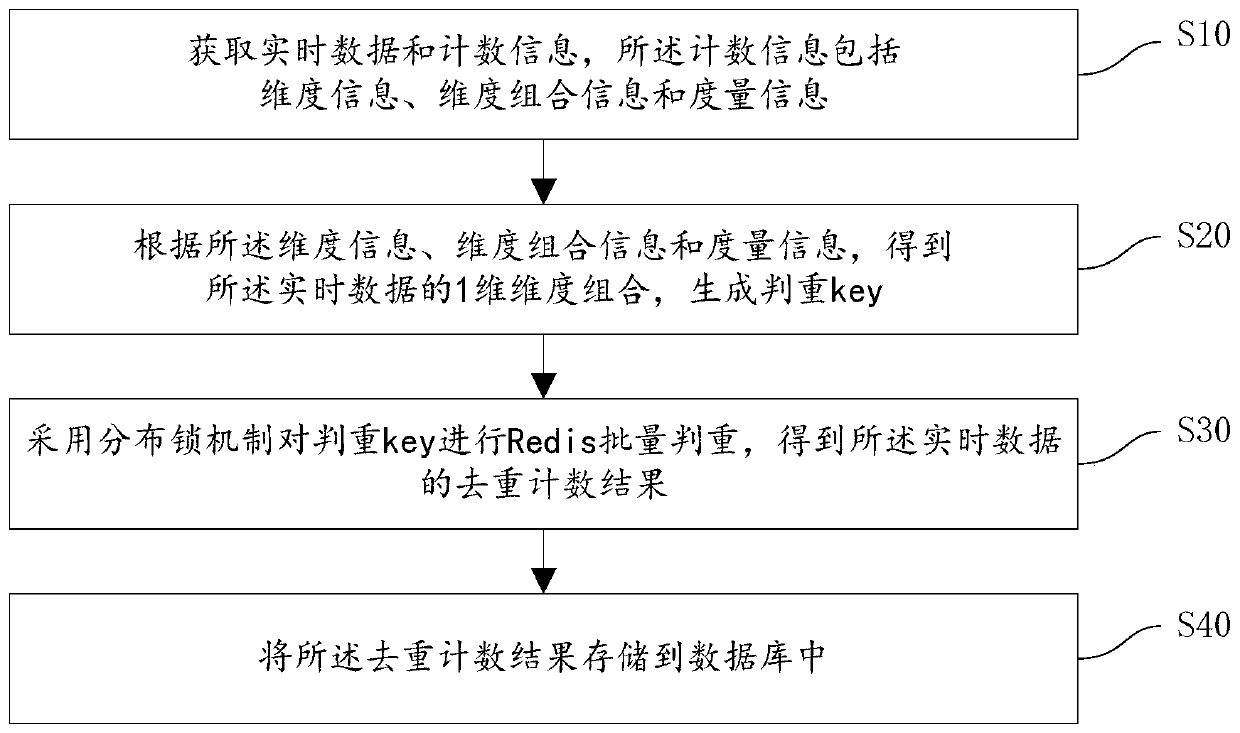
Real-time data deduplication counting method and device
ActiveCN110569263AAccurate calculationTakes up little memory spaceDigital data information retrievalSpecial data processing applicationsReal-time computingComputer science
The embodiment of the invention discloses a real-time data deduplication counting method and a real-time data deduplication counting device, which can realize accurate calculation of a measurement deduplication counting value of real-time data and simultaneously occupy a small memory space in a deduplication process. The method provided by the embodiment of the invention comprises the following steps: acquiring real-time data, dimension information, dimension combination information and measurement information; decomposing all dimension combinations of the real-time data into one-dimensional combinations according to the dimension information, the dimension combination information and the measurement information, and generating a weight judgment key; and performing Redis batch duplicationjudgment on the duplicate judgment key by adopting a distributed lock mechanism to obtain a duplicate removal counting result. The uniqueness of the measurement field of the real-time data under eachdimension combination can be ensured, and the accurate deduplication count value of the real-time data can be obtained through duplication judgment. Only the duplication judgment key of the one-dimensional dimension combination needs to be stored for duplication judgment, a large number of memory resources are released, the length of the duplication judgment key is fixed, and the Redis memory usage amount can be estimated.
Owner:SUNING CLOUD COMPUTING CO LTD
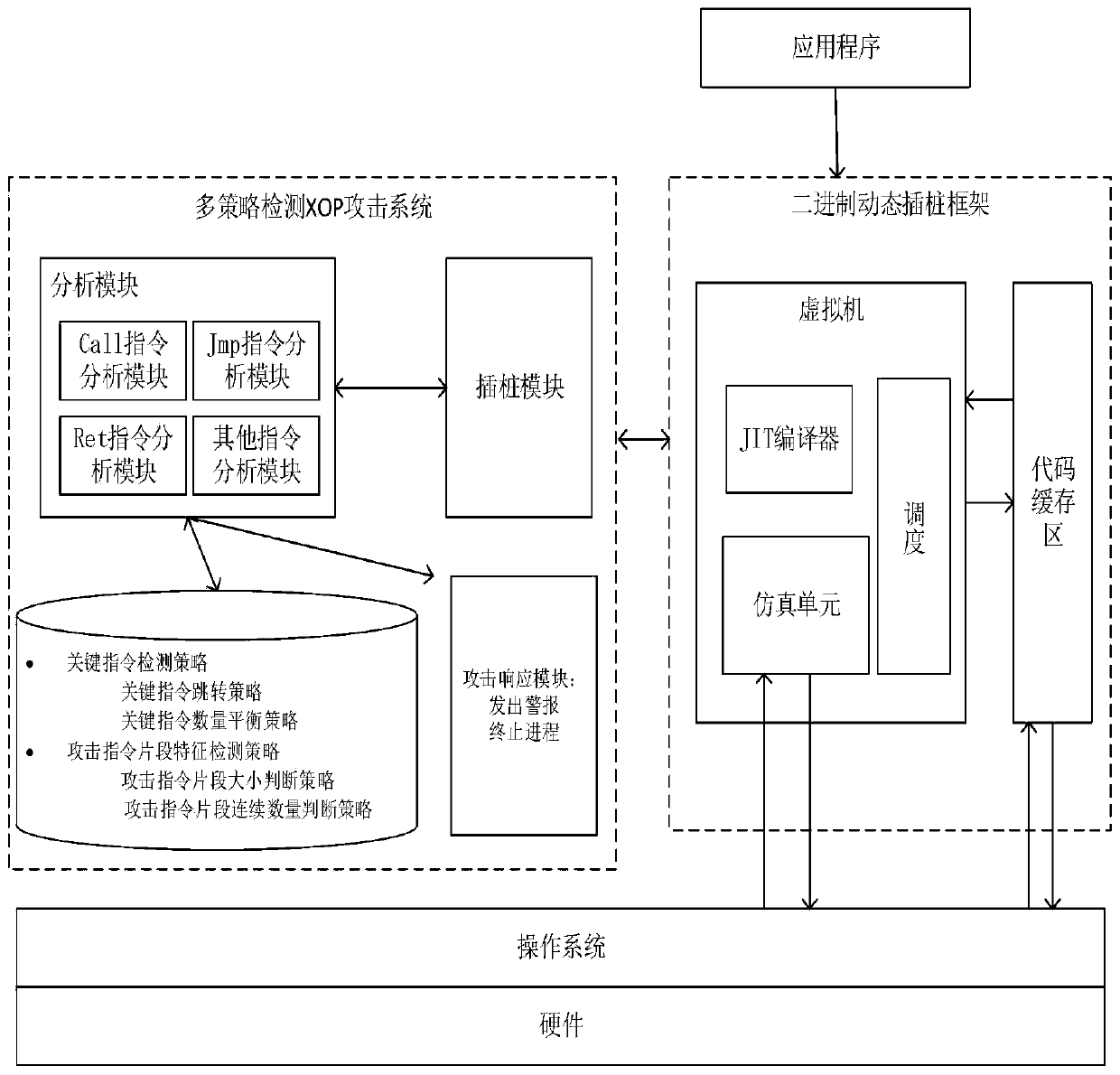
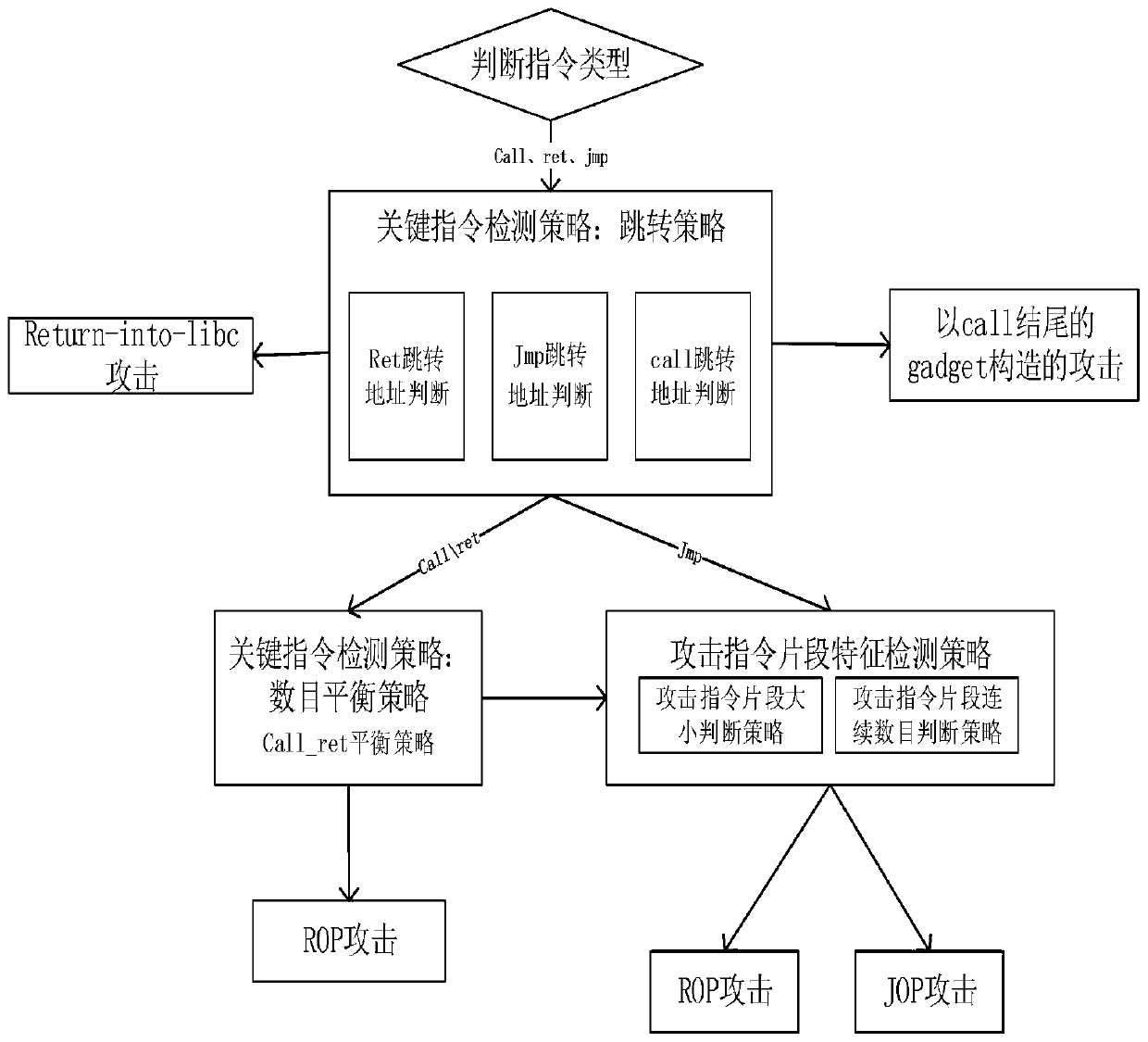
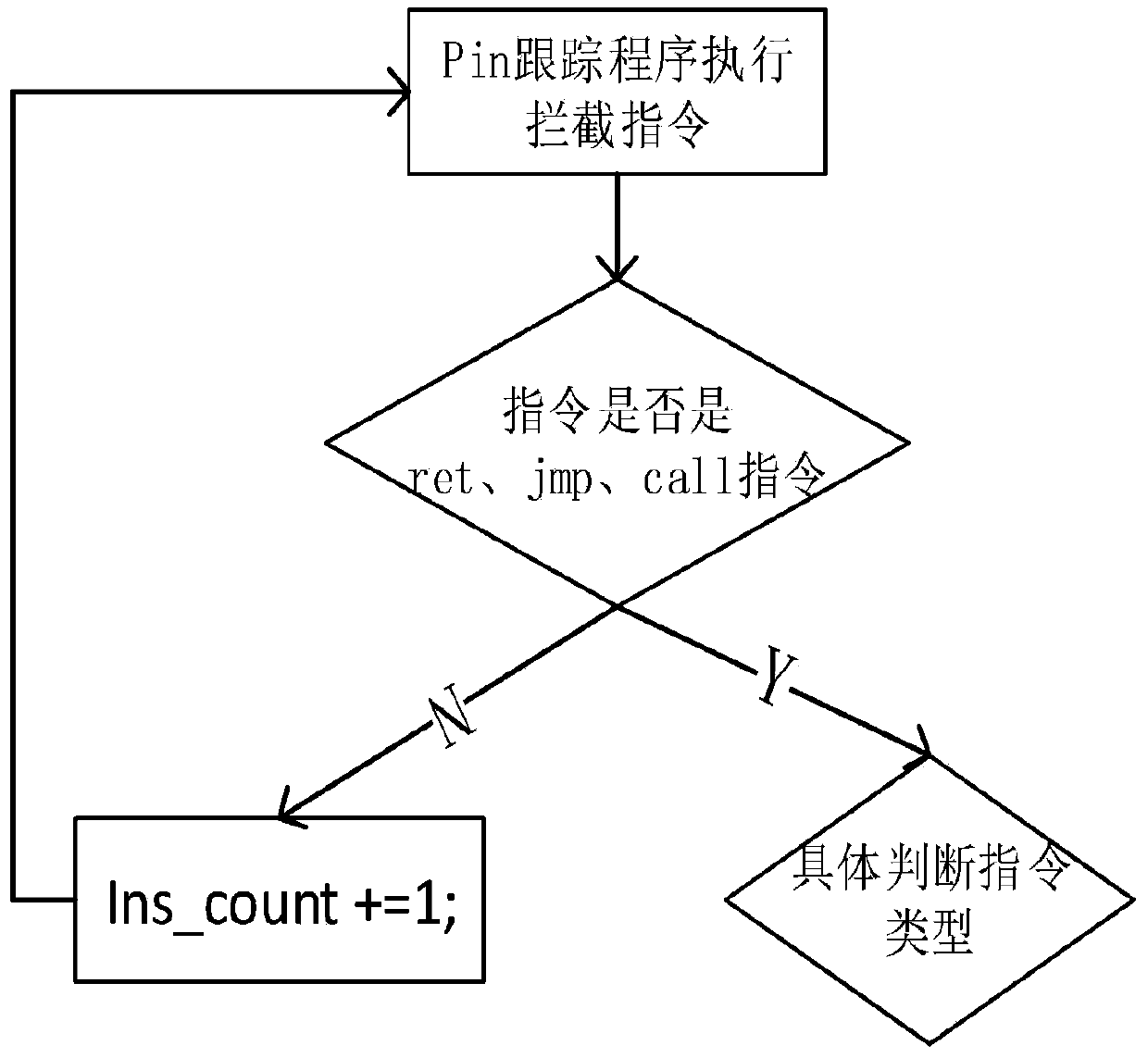
ROP and variant attack dynamic detection method based on multi-strategy instruction detection
ActiveCN109766690AImprove accuracyReduce false alarm ratePlatform integrity maintainanceFragment sizeDynamic instrumentation
The invention discloses an ROP and variant attack dynamic detection method based on multi-strategy instruction detection. The method is based on a binary dynamic instrumentation technology to intercept an instruction, and adopts two strategy judgment methods of a key instruction detection strategy and an attack instruction fragment feature detection strategy to realize ROP attack and variant attack detection. And the key instruction detection strategy performs characteristic analysis according to the instruction address and the instruction quantity. And the attack instruction fragment featuredetection strategy comprises an attack instruction fragment size judgment strategy and an attack instruction fragment continuous length judgment strategy according to the attack function and complexity feature analysis. According to the method, a multi-layer detection strategy is adopted, four characteristic dimensions of instruction addresses, the number, attack functions and attack complexity are integrated from two aspects of normal and abnormal instruction characteristics, and detection of ROP attacks and variant attacks of the ROP attacks is comprehensively achieved by combining a deterministic detection method and an uncertain detection method. The method is low in performance consumption and small in occupied memory space.
Owner:BEIJING UNIV OF TECH
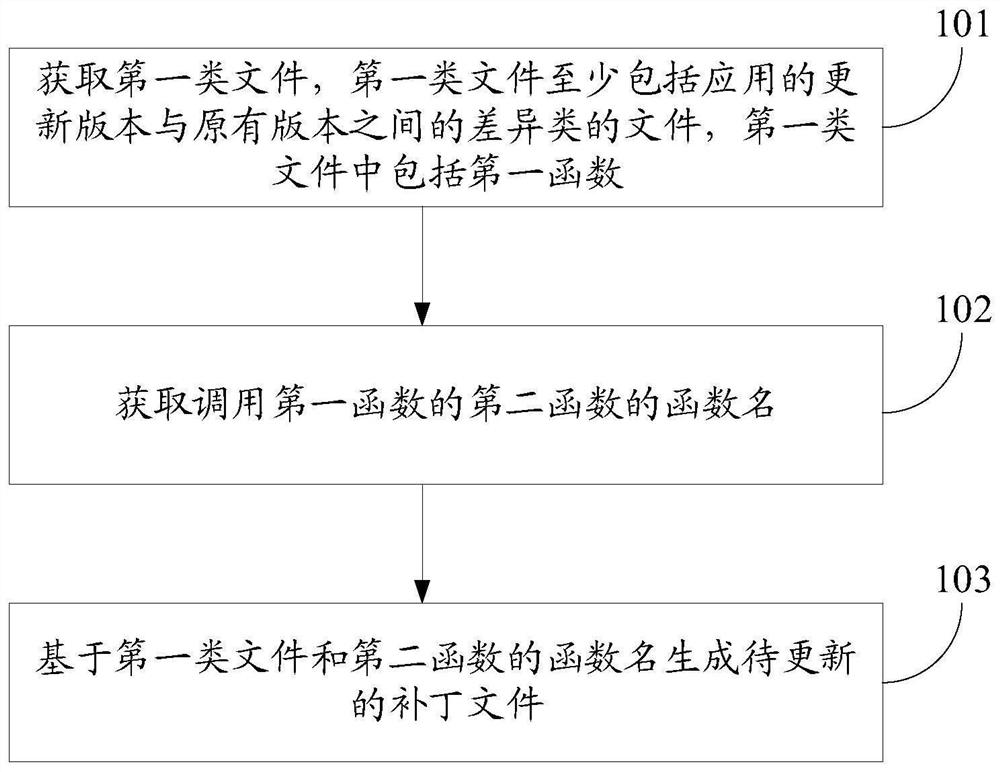
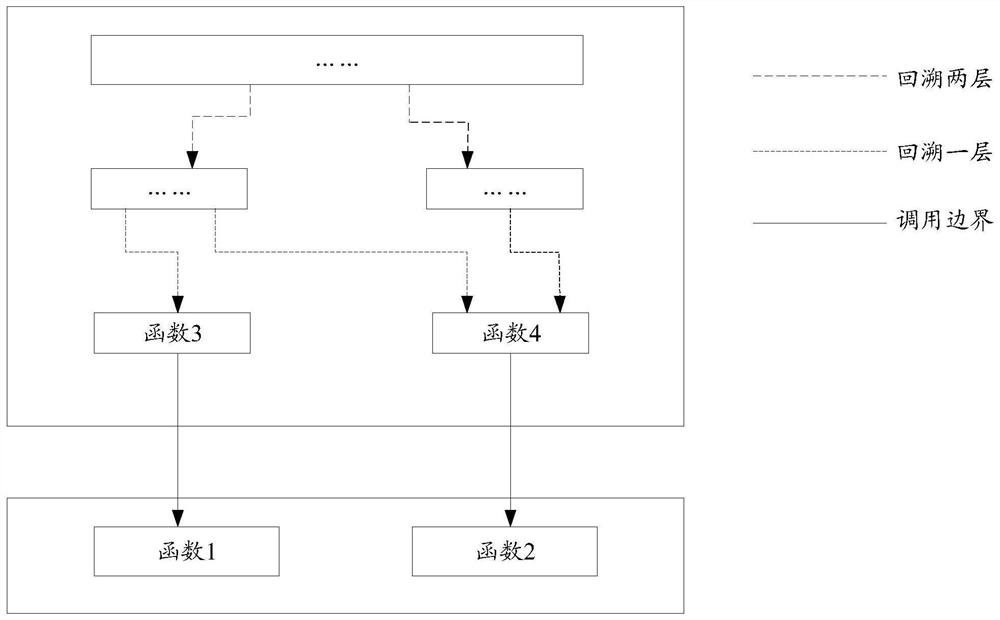
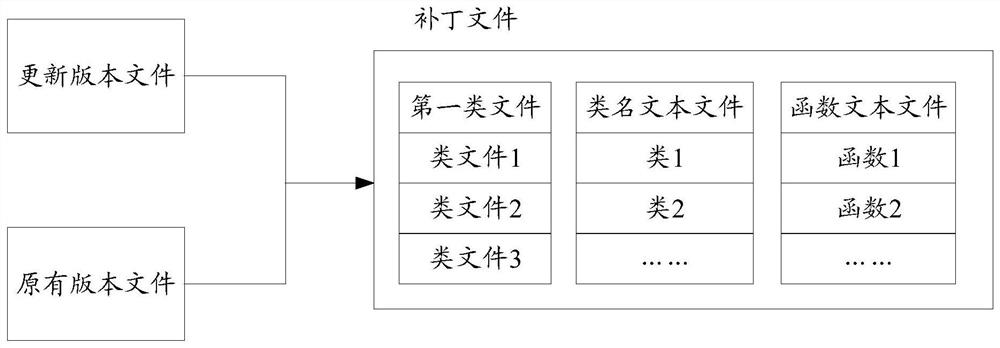
Application updating method and device, terminal and storage medium
ActiveCN112035153AExtend your lifeTakes up little memory spaceVersion controlProgram loading/initiatingTheoretical computer scienceTerm memory
The embodiment of the invention discloses an application updating method and device, a terminal and a storage medium, and belongs to the field of computers. The method comprises the steps that in therunning process of an application, a patch file to be updated of the application is obtained, the patch file comprises function names of a first type file and a second function, the first type file comprises a first function, and the second function is a function for calling the first function; when the application is started next time, inserting the patch file in front of the class file of the original version of the application in the class list of the class loader; and when a class loader is used for loading a second class of files in the class files of the original version, the execution mode of the second function is updated to interpretive execution, and the second class of files comprise the second function. When the application is updated, only the patch file needs to be inserted into the class list of the class loader, consumption of system resources and memory is reduced as much as possible on the premise that the application is successfully updated, and the service life of the terminal is prolonged.
Owner:TENCENT TECH (SHENZHEN) CO LTD
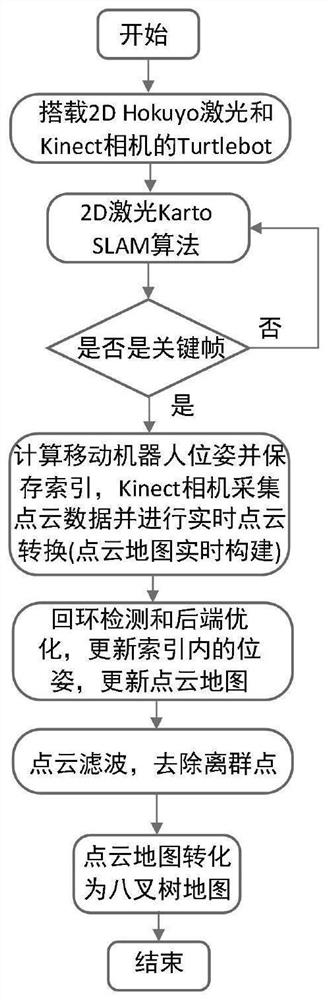
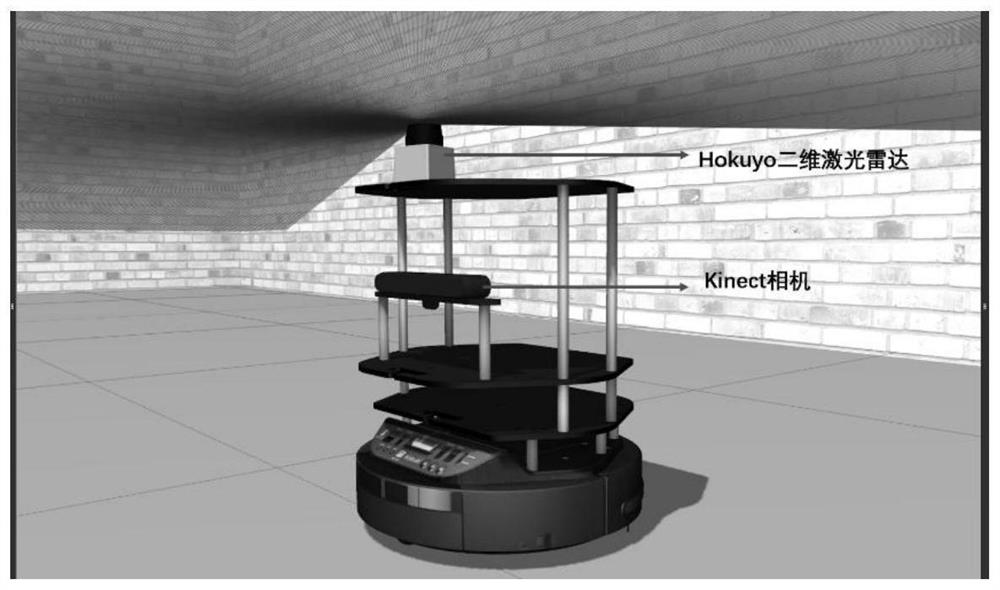
Octree map construction method and system
PendingCN113720324AHigh precisionLow computing resource requirementsCharacter and pattern recognitionNavigation instrumentsPoint cloudComputer graphics (images)
The invention discloses an octree map construction method and system. The method comprises the following steps of determining a key frame and a mobile robot pose under the key frame by adopting a laser map optimization SLAM algorithm according to laser radar and odometer data, collecting environment point cloud information, and converting the point cloud data under a camera coordinate system into a world coordinate system, splicing the point cloud information after coordinate conversion to obtain a three-dimensional point cloud map, based on the three-dimensional point cloud map, conducting loopback detection and back-end optimization on a laser map optimization SLAM algorithm, and acquiring an updated mobile robot pose and an updated three-dimensional point cloud map, filtering the updated three-dimensional point cloud map, and removing outliers of the updated three-dimensional point cloud map, and converting the filtered three-dimensional point cloud map into an octree map. Compared with a point cloud map, the octree map constructed by the method is easy to store, smaller in occupied memory space, flexible and convenient, and can be directly used for navigation.
Owner:SHANGHAI UNIV
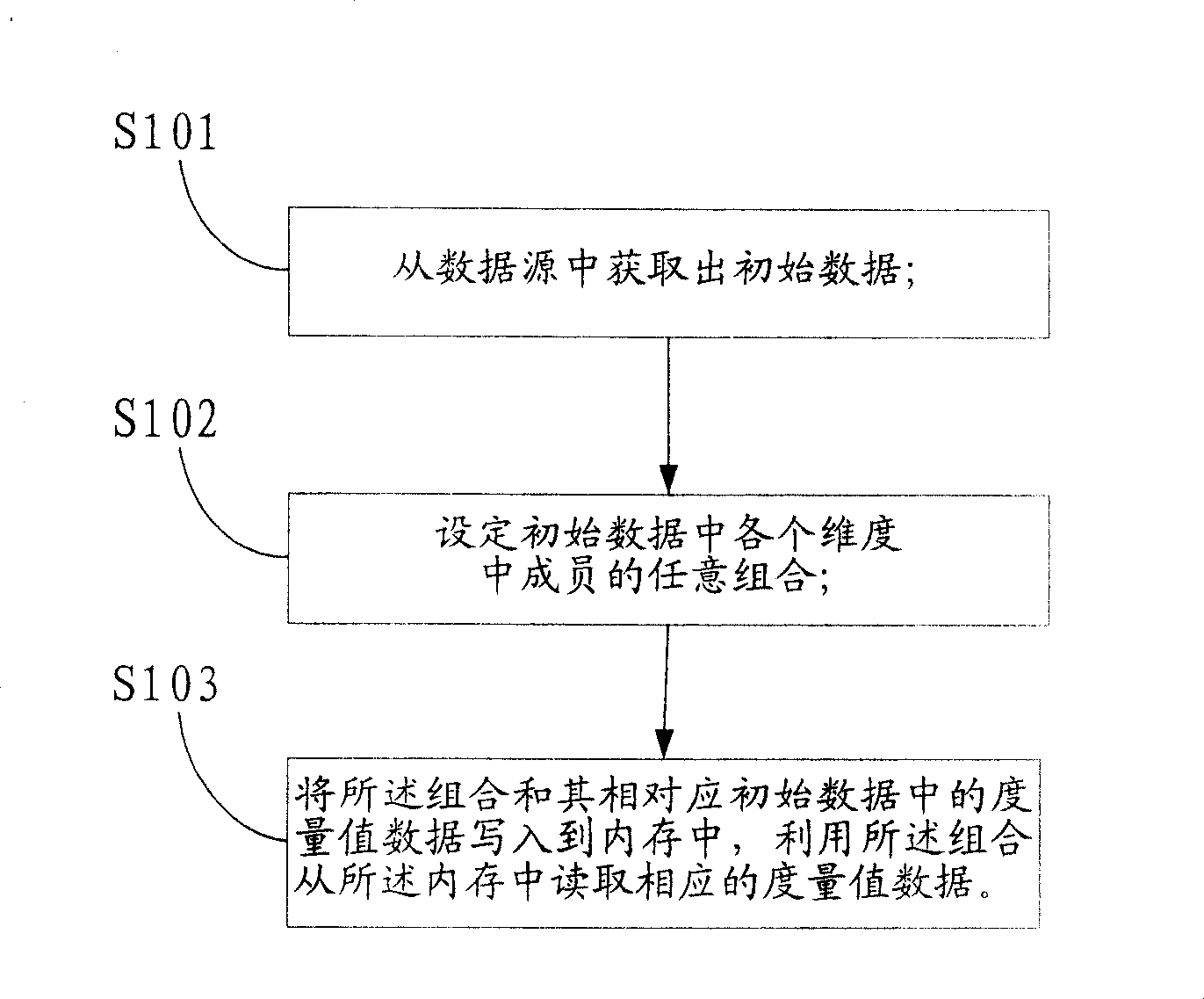
Multidimensional data reading and writing method and apparatus in on-line analytical processing system
ActiveCN100498785CSolve storage problemsTakes up little memory spaceSpecial data processing applicationsInternal memoryArray data structure
The invention relates to many dimensions data read-write method and device in on-line analytical processing system. It includes the following steps: getting original data from the data source; setting each dimensionality member random combination for the original data; writing the metric value data of the combination and its corresponding original data in the internal memory; using the combination to read corresponding metric value data from the internal memory. It uses Hash table or array form to write in and read out while read-write data from the internal memory. The many dimensions data model is stored as Hash table form which is good for internal memory storing and inquiring. While read-write small data quantity, the Hash table takes up little internal memory space which will not be the bottle-neck of the system performance, realize small data quantity OLAP storing and inquiring based on internal memory.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
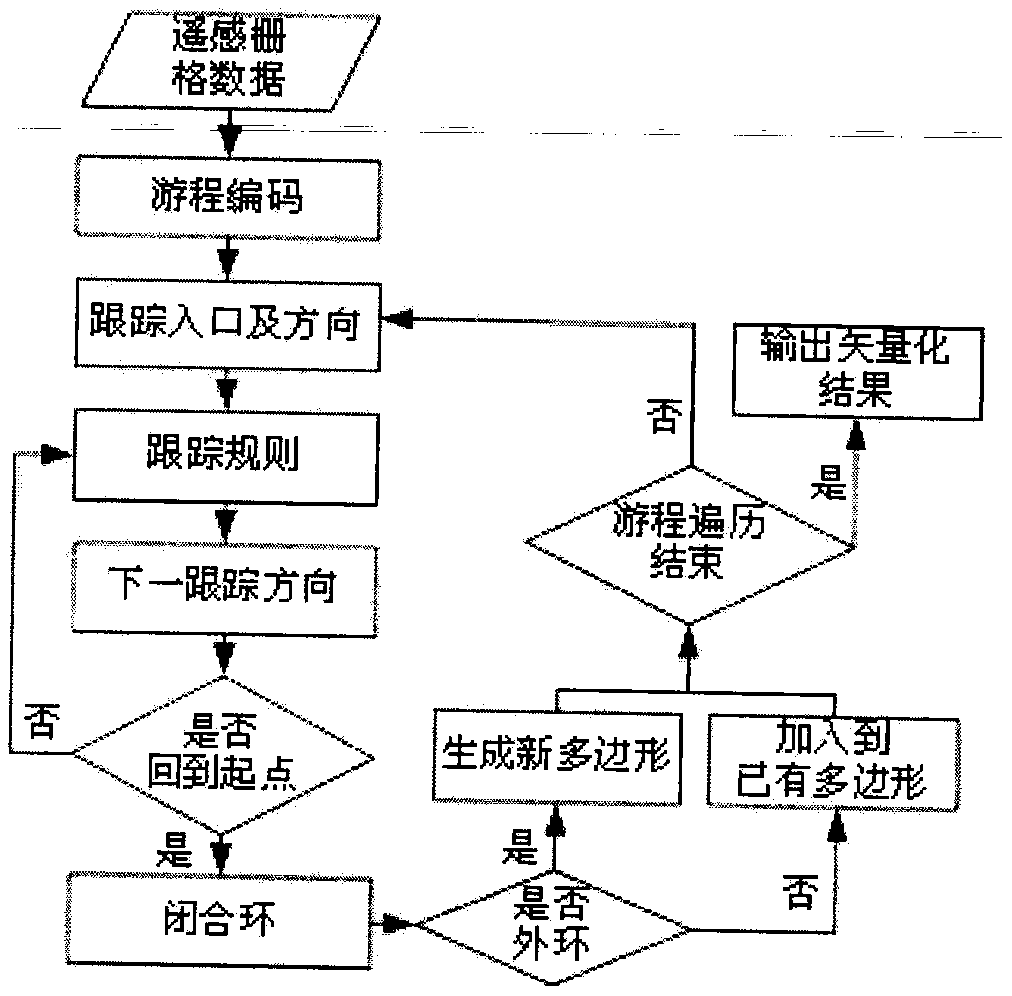
Raster data rapid vectorization method combining run-length coding and edge tracking
ActiveCN110675417ASave storage spaceImprove production efficiencyImage analysisDigital video signal modificationRun-length encodingEdge tracking
A raster data rapid vectorization method combining run-length coding and edge tracking comprises two steps of run-length coding and edge tracking, and edge tracking comprises the steps of determininga tracking entrance and an initial direction, determining a tracking rule, marking a run length, and judging and processing an inner ring and an outer ring. The step of determining the tracking rule comprises generating a 4-connected region and an 8-connected region. The run length marking step comprises marking related run length codes in the tracking process, the inner and outer ring judgment and processing step comprises judgment of an inner ring and an outer ring and association of the inner ring and the outer ring, and the whole algorithm process is divided into six steps. According to the method, the occupied memory space is greatly reduced, 4-connected polygons and 8-connected polygons can be generated, the search efficiency is improved, the middle process of generating arc sectionsby node points is omitted, and the closed boundary generation efficiency is improved. For the polygon with the inner ring, the inner boundary quickly corresponds to the outer boundary, so that the generation efficiency of the polygon with the inner ring is improved, and the vectorization efficiency is further improved.
Owner:自然资源部第六地形测量队
Offshore wind power plant equivalent method, system and device based on wake effect factors
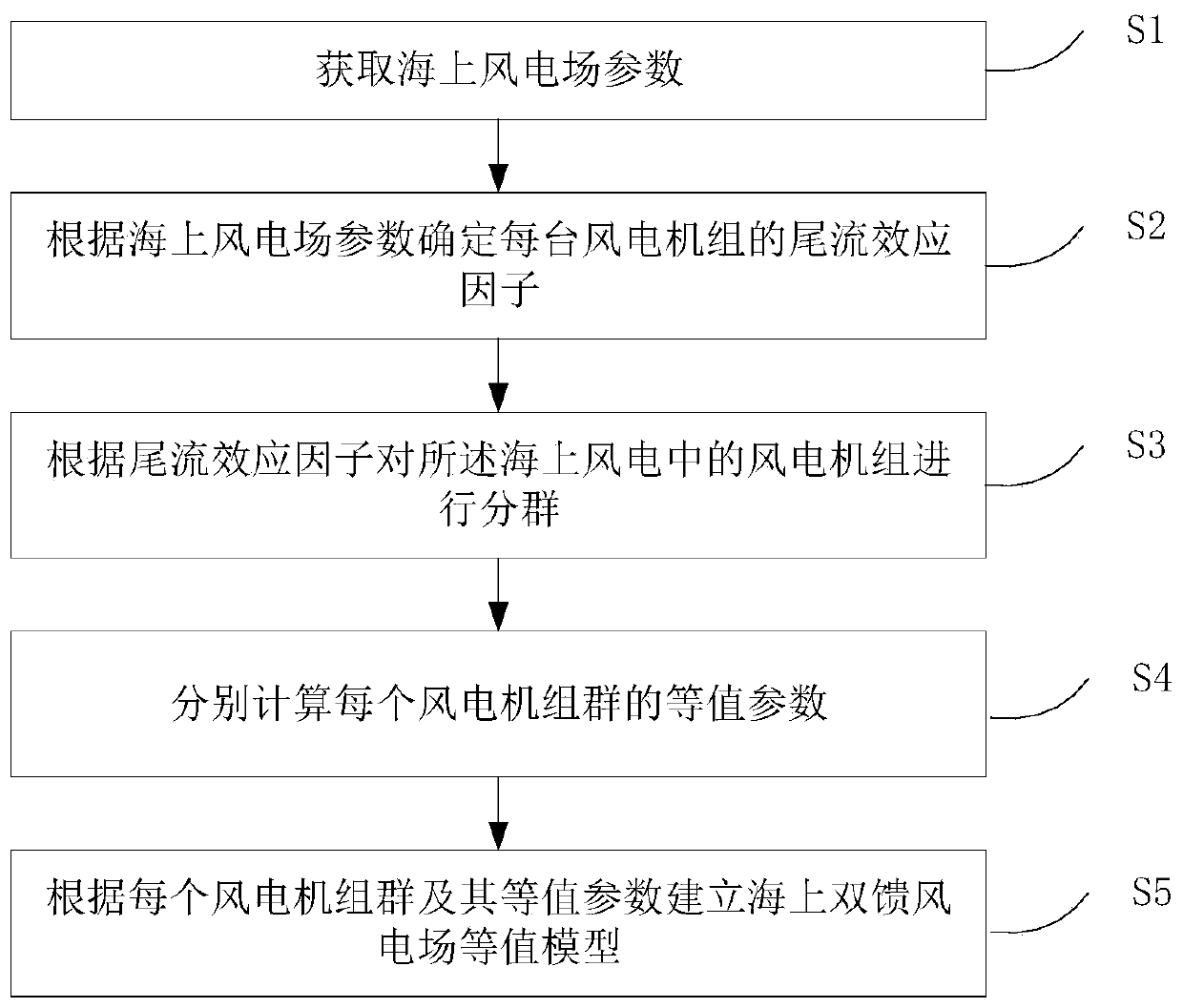
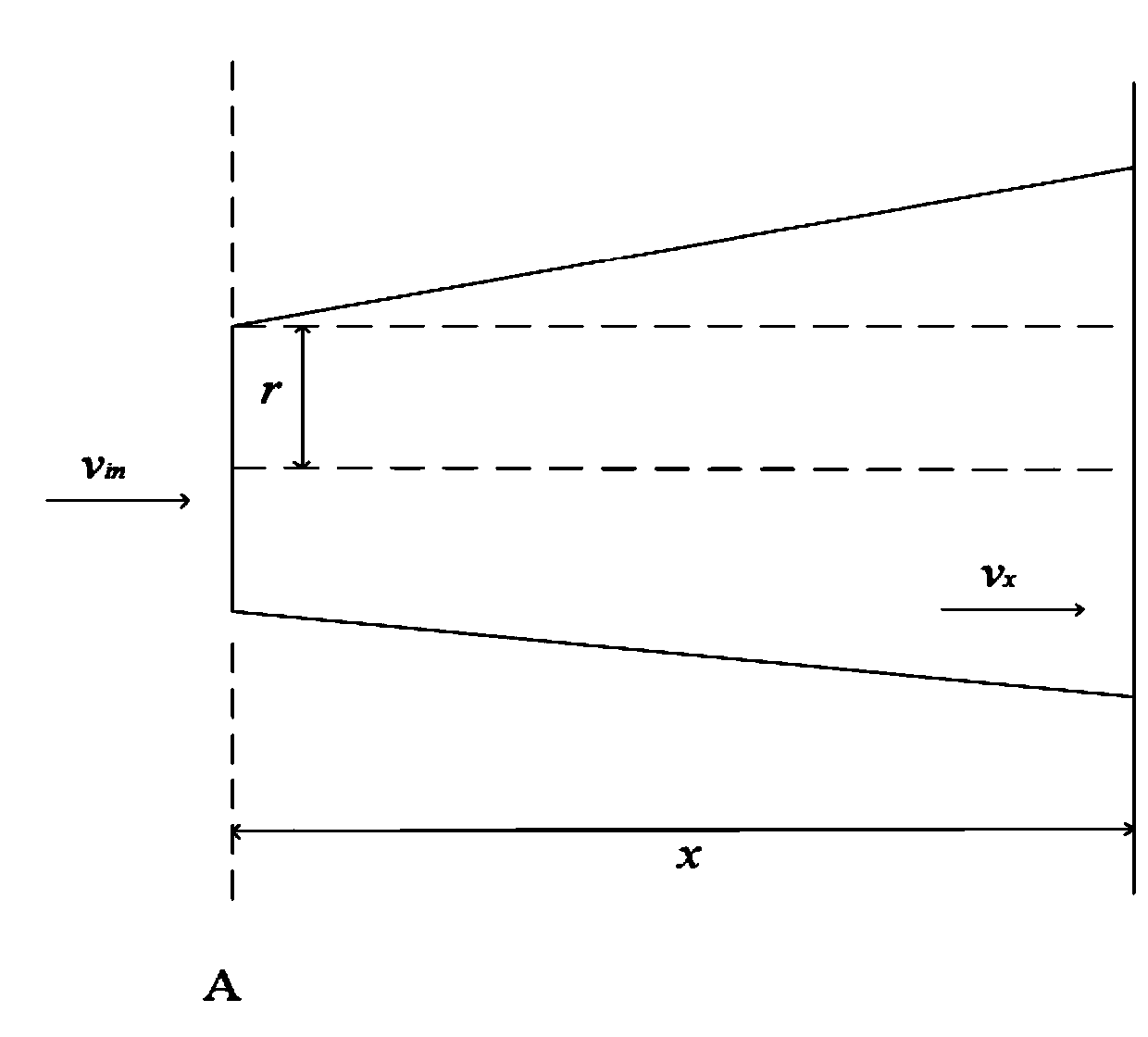
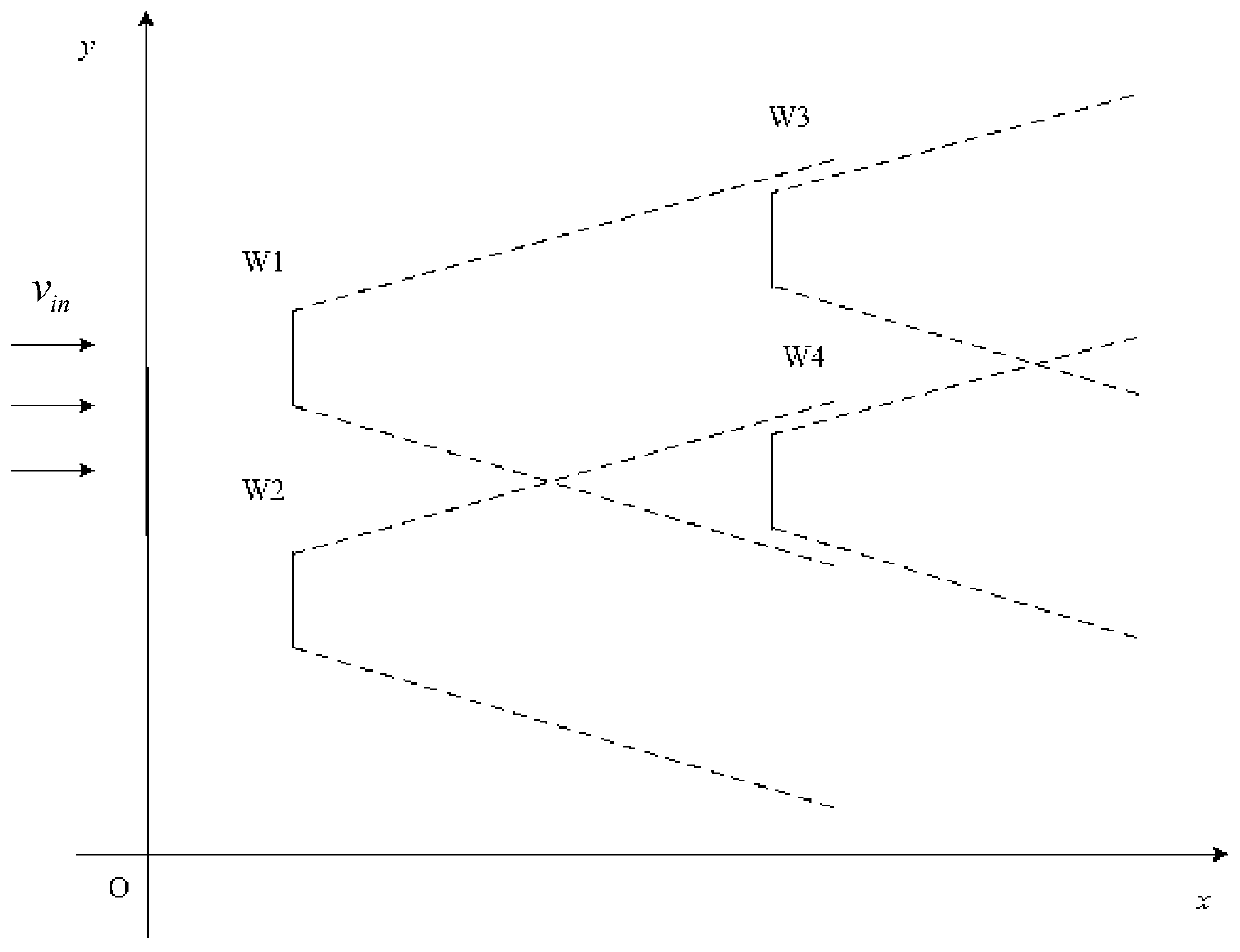
ActiveCN109802440AThe method is simple and easy to implementTakes up little memory spaceSingle network parallel feeding arrangementsWind energy generationElectric fieldUltrasound attenuation
The invention discloses an offshore wind power plant equivalent method based on wake effect factors. The method comprises the following steps: obtaining parameters of an offshore wind power plant, wherein the parameters of the offshore wind power plant comprise the incoming flow wind speed of the offshore wind power plant, the position information of each wind turbine set in the offshore wind power plant, the radius of wind wheels, an attenuation constant and a thrust coefficient; determining a wake effect factor of each wind turbine set according to the parameters of the offshore wind power plant; grouping the wind turbine generators in the offshore wind power according to the wake effect factors; calculating equivalent parameters of each wind turbine generator group; and establishing anoffshore wind power plant equivalent model according to each wind turbine generator group and the equivalent parameters thereof. The method is simple, easy to implement, small in occupied memory space, high in accuracy and suitable for large-scale offshore wind power research.
Owner:GRID POWER PLANNING & RES CENT OF GUANGDONG GRID POWER CO LTD +2
A military plotting method in three-dimensional scene
InactiveCN109087391AUnlimited imaginationReduced aesthetics3D modellingTriangulationCombined technique
The invention discloses a military plotting method under a three-dimensional scene, comprising a three-dimensional point military symbol plotting method and a three-dimensional function military symbol plotting method. A method for plot three-dimensional point military symbols comprises the following steps: step S11, relief processing of two-dimensional military symbols; Step S12, edge detection of the image; Step S13, drawing symbols. A 3-D function military mark symbol plotting method comprises the following steps: step S21, algorithm analysis; 22, determining an interpolation point by a variable step size interval averaging method; Step S23, determining a parameter interpolation step length l; Step S24: elevation adding. The invention realizes the real-time construction of the three-dimensional point military symbol based on the solid model and the bulletin board combination technology, combines the high abstraction of the two-dimensional symbol with the visualization of the three-dimensional symbol, and gives the combat commander infinite imagination space. At the same time, the triangulation algorithm of indefinite length interval bisection not only ensures that the nodes reduce the beauty of the curve, but also does not affect the efficiency of rendering.
Owner:GEOVIS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com