Information processing method and device
A processing method and target technology, applied in the computer field, can solve problems such as not enough to ensure the security of private information, and achieve the effect of small amount of uploaded data, protection of private data, and good encryption performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
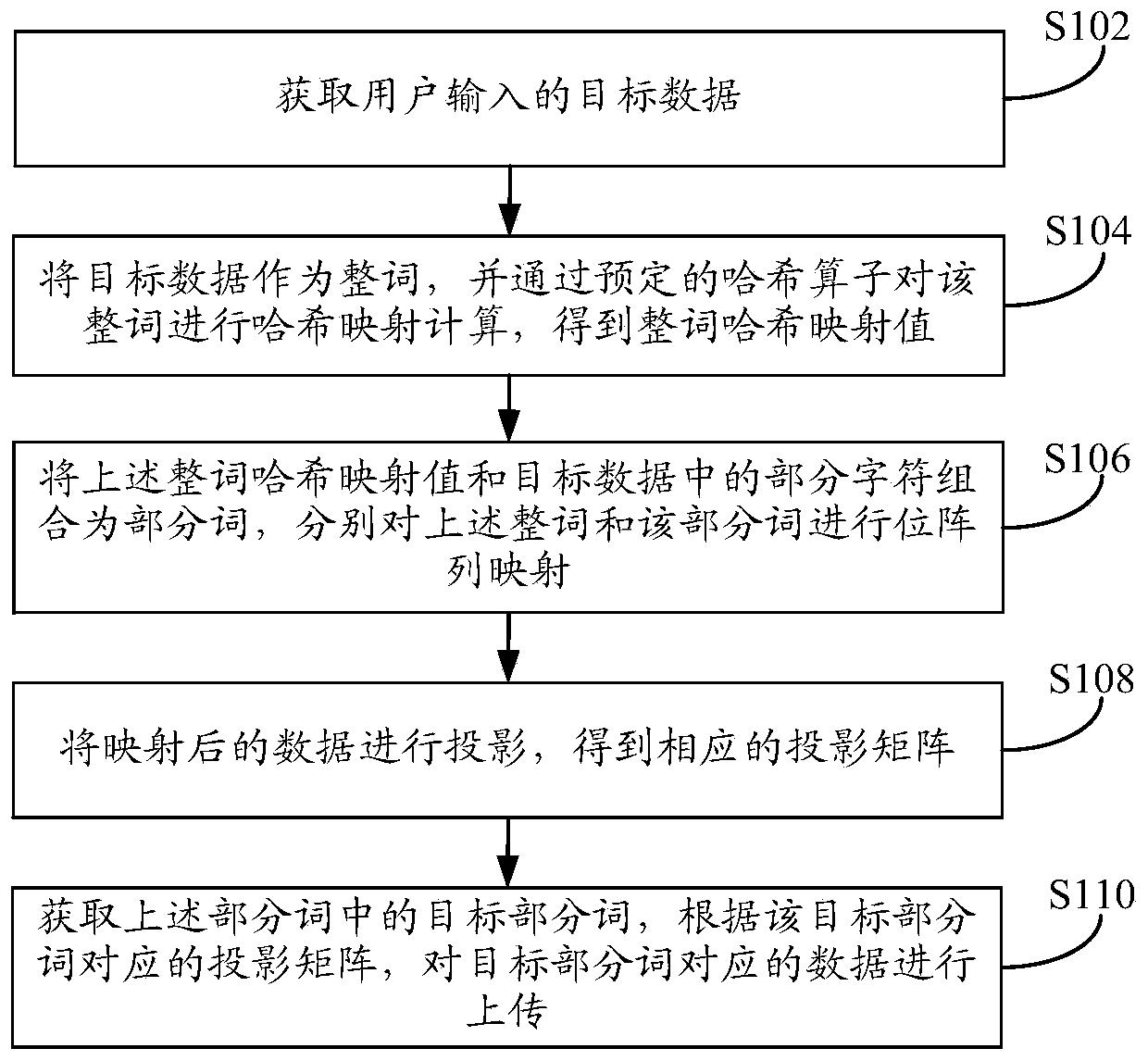
[0046] Such as figure 1 As shown, the embodiment of the present application provides a method for processing information. The execution subject of the method may be a terminal device, wherein the terminal device may be a terminal device such as a personal computer, or a mobile terminal device such as a mobile phone or a tablet computer. . The method can be applied to processes such as privacy protection of user data. The method specifically may include the following steps:
[0047] In step S102, the target data input by the user is acquired.
[0048] Wherein, the target data may be any data. In the embodiment of the present application, the target data may be a search term (or hot search term, etc.) input by the user, such as "World Cup France" or the domain name "google".
[0049] In implementation, at present, various operators (such as communication operators, game operators, etc.) Integration and data fusion technologies are flourishing. At the same time, the convenien...
Embodiment 2
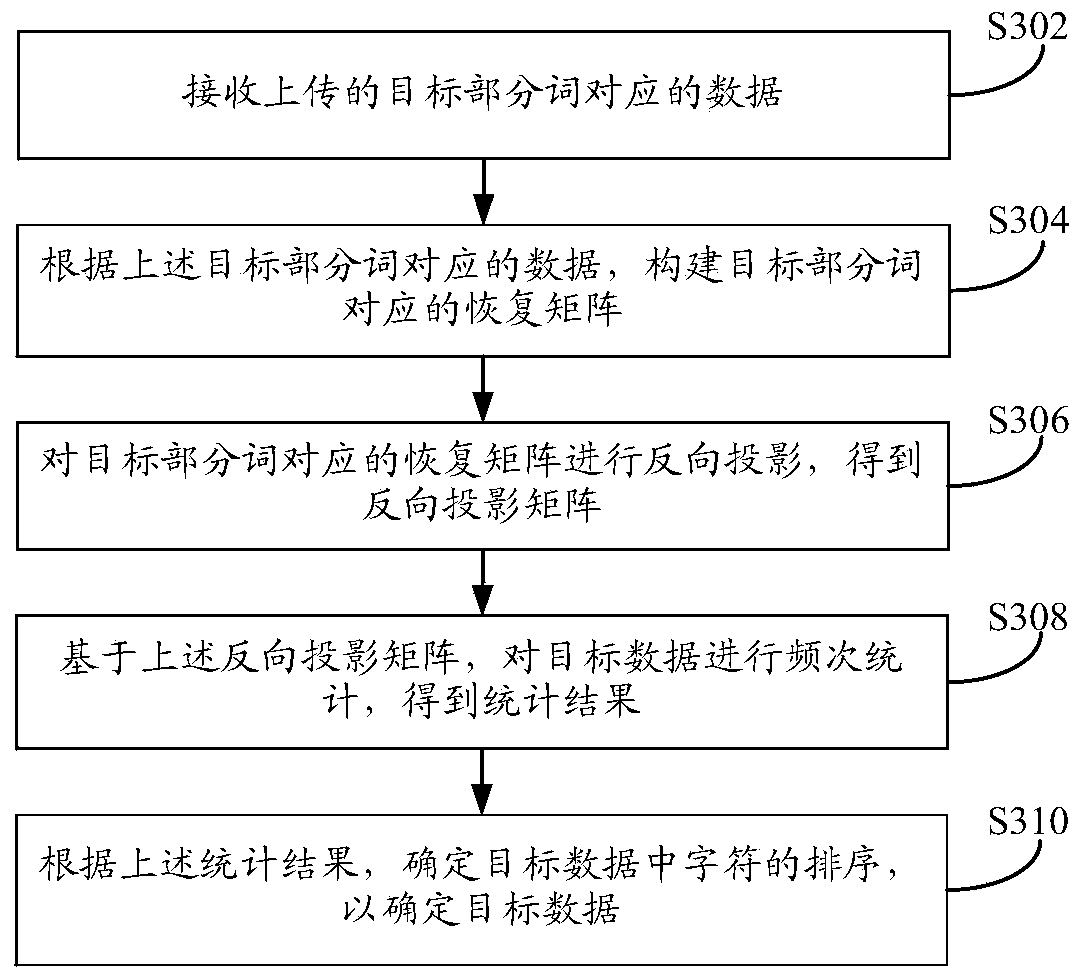
[0085] Such as image 3 As shown, the embodiment of the present application provides an information processing method, and the execution body of the method may be a server, wherein the server may be a single server or a server cluster composed of multiple servers. The method can be applied to processes such as privacy protection of user data. The method specifically may include the following steps:
[0086] In step S302, the data corresponding to the uploaded target part word is received, the data corresponding to the target part word is the target data input by the user as the whole word, and the whole word is hash-mapped by a predetermined hash operator Calculate and obtain the hash map value of the whole word, combine the hash map value of the whole word and some characters in the target data into part words, perform bit array mapping on the whole word and part words respectively, and project the mapped data, The corresponding projection matrix is obtained, and after th...
Embodiment 3
[0098] Such as Figure 4 As shown, the embodiment of the present application provides a method for processing information, and the execution subject of the method may be a terminal device and a server, wherein the terminal device may be a terminal device such as a personal computer, or a mobile phone such as a mobile phone or a tablet computer. For the terminal device, the server may be a single server or a server cluster composed of multiple servers. The method can be applied to processes such as privacy protection of user data. The method specifically may include the following steps:
[0099] In step S402, the terminal device acquires the target data input by the user.
[0100] For the specific processing process of the above step S402, reference may be made to the relevant content of the step S102 in the first embodiment above, and details will not be repeated here.
[0101] In step S404, the terminal device takes the target data as the whole word, and performs hash mappin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com