A method for verifying transmission data security
A technology for data transmission and security, applied in the field of verifying the security of transmission data, and can solve problems such as malicious attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
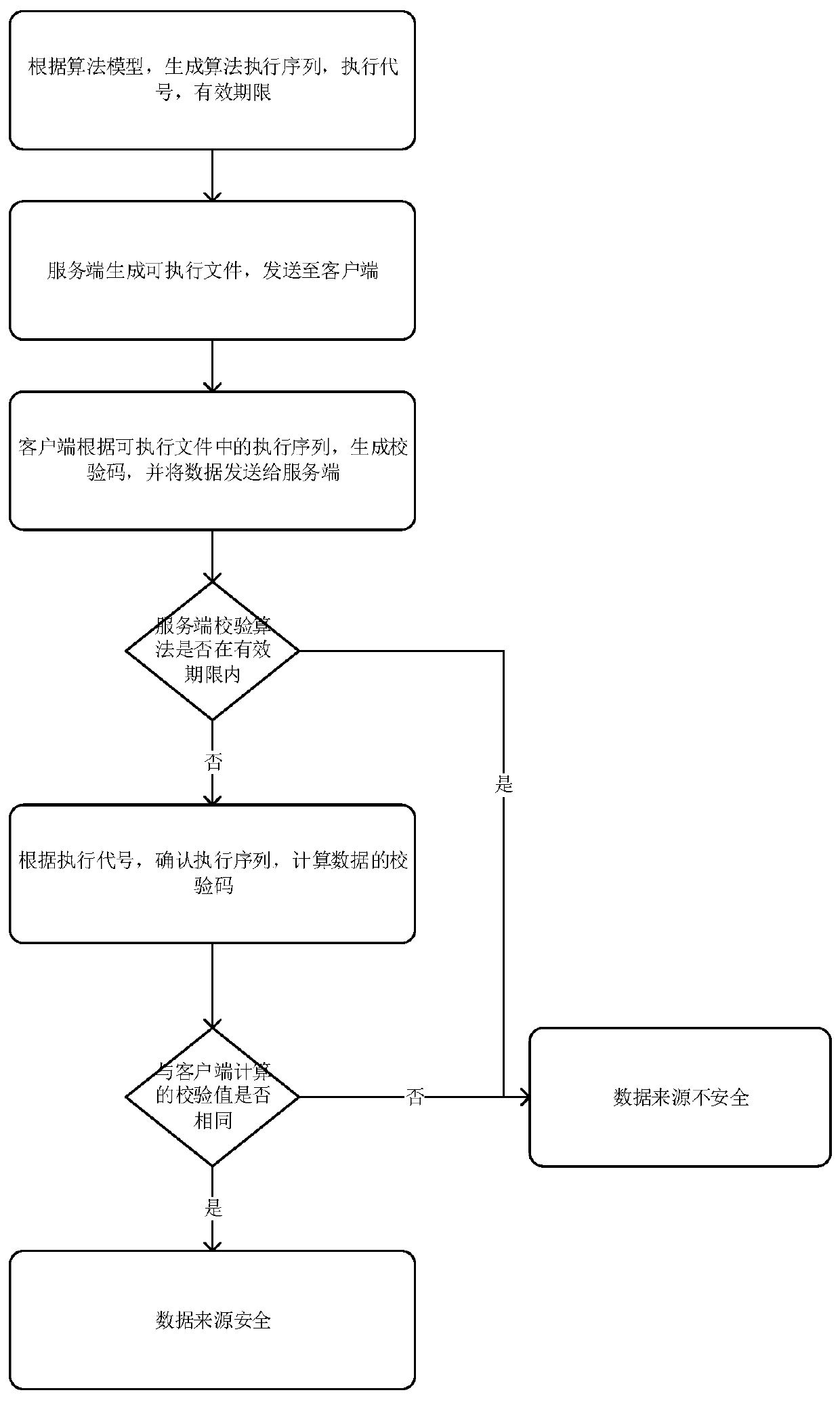
[0020] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
[0021] A method for verifying the integrity of transmitted data provided by the present invention comprises the following steps:
[0022] (1) Custom algorithm model: Reverse (string reversal), Swap (string dislocation exchange), Plus (according to the ACSii order of characters into 1), MD5 message digest algorithm, take these four algorithms as an example, but not limited to this.
[0023] (2) Generate the algorithm execution sequence, execution code, and validity period of the execution sequence on the server side according to multiple algorithm models T;
[0024] The execution sequence is: Reverse-Swap-Plus-MD5, the execution code is AgEincTHdk, the validity period of the execution sequence is within 30 minutes of the generation of the execution sequence, and the validity period is until 10:30:00 on December 22, 2018.
[0025] (3)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com