Label system-based access method
A label and system technology, applied in database model, digital data processing, structured data retrieval, etc., can solve the problem of complex number retrieval, and achieve the effect of speeding up the operation speed, high accuracy and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to enable those skilled in the art to better understand the technical solutions in the present application, the technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the accompanying drawings.
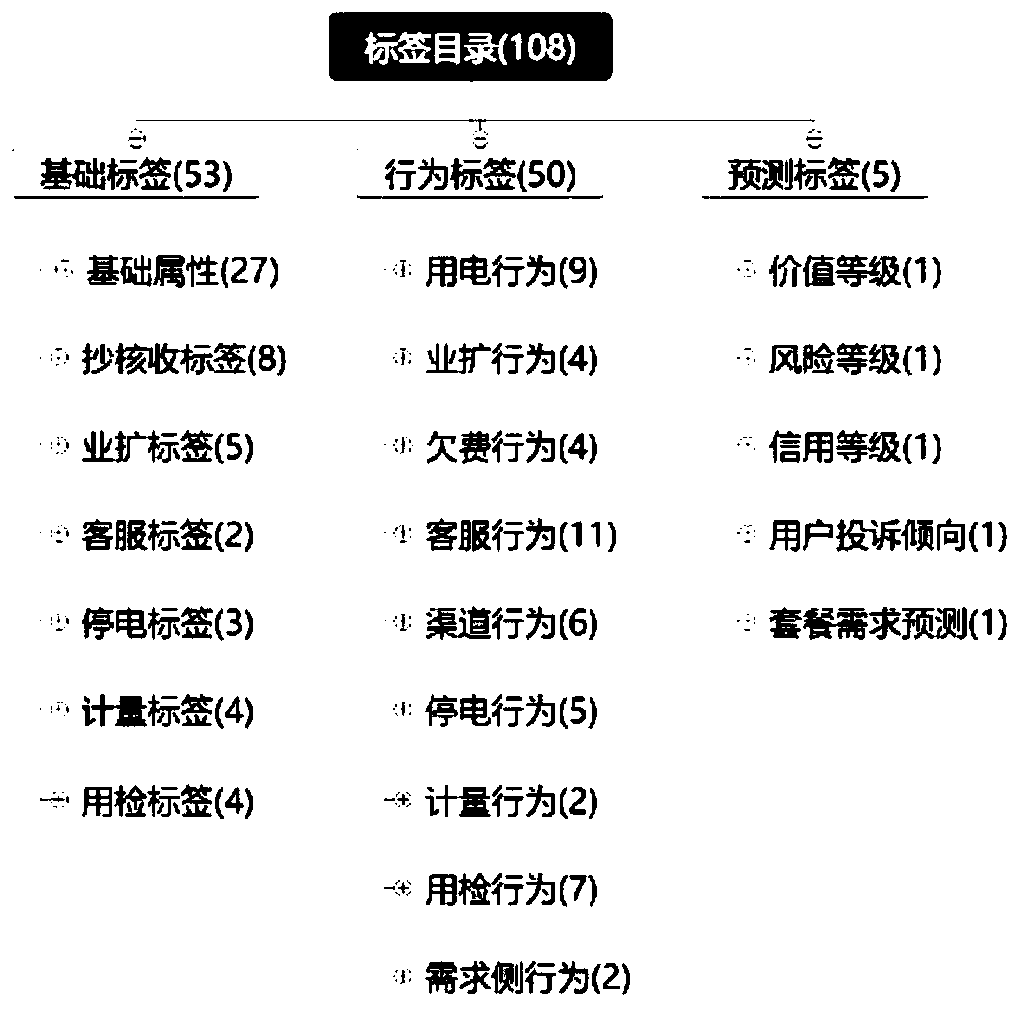
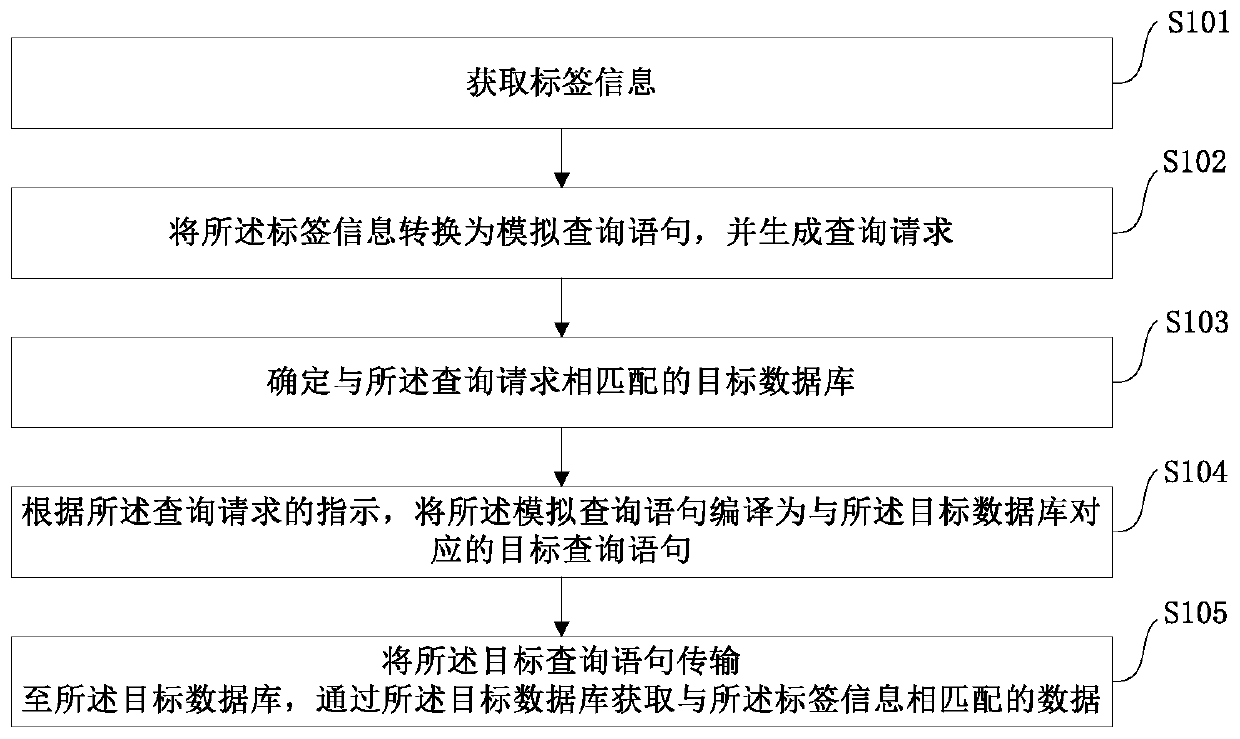
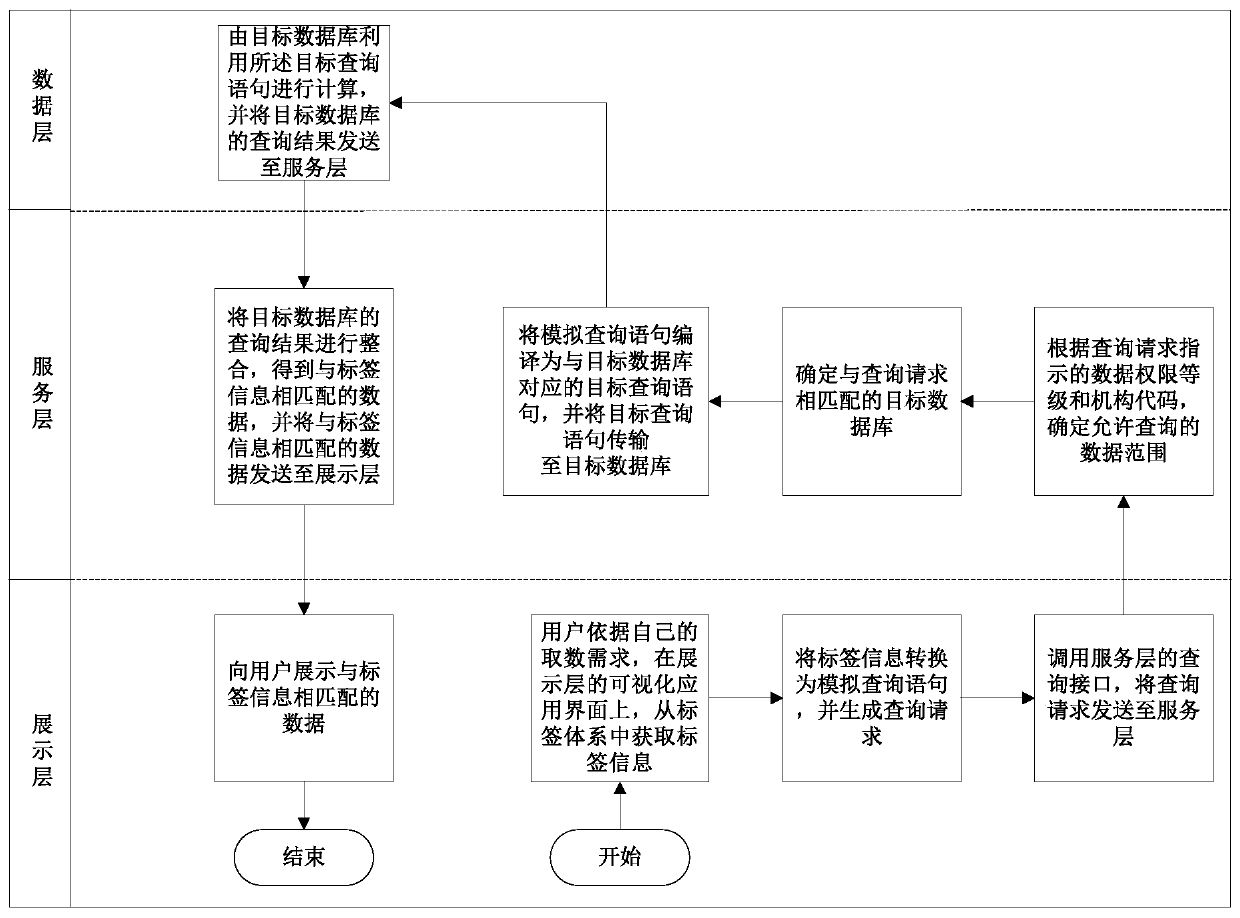
[0034] The method for obtaining numbers based on the label system described in the embodiment of the present application is mainly aimed at the customer label system of the power grid. The power grid customer labeling system is mainly based on business expansion, copy verification and collection, customer service, power outage, metering, usage inspection, demand side and other related businesses, sort out the main business and data objects, and screen out the typical business related to users Processes and data, thus formulating reasonable and scientific labels and labeling rules, and then calculating the label value according to the labeling rules, and organizing the labels according to the h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com