A method and device for securely accessing a mobile phone terminal to an information network
A mobile phone terminal and information network technology, applied in the field of network security, can solve the problems of inability to use password modules such as USBKEY, fraudulent use and tampering, security risks, etc., and achieve the effects of reducing security risks, preventing tampering and forgery, and authenticating security and reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
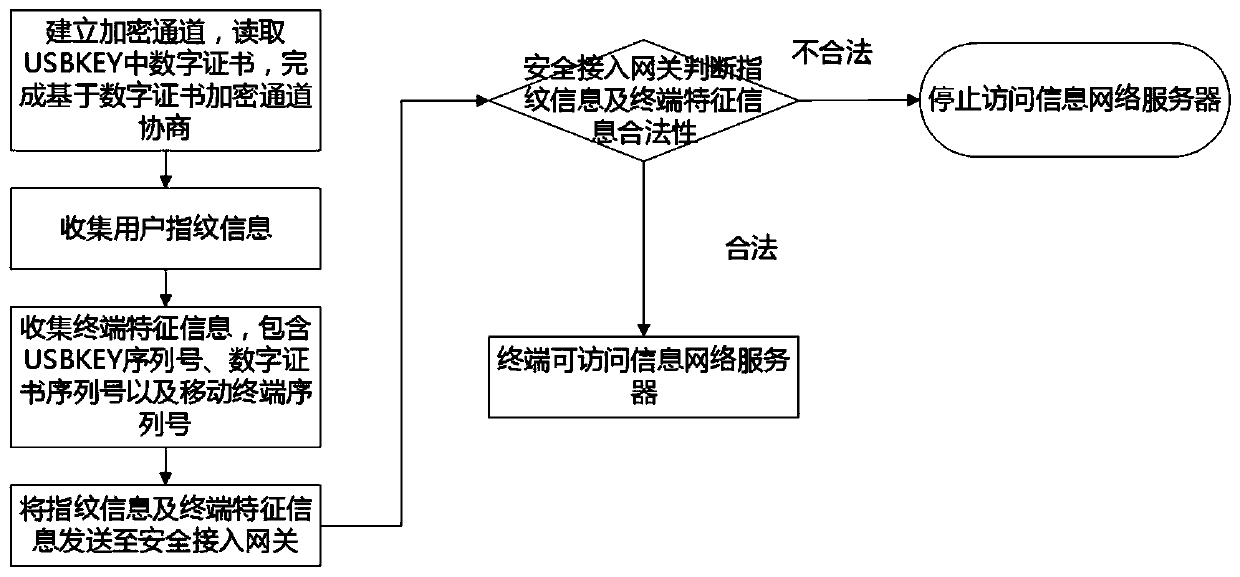
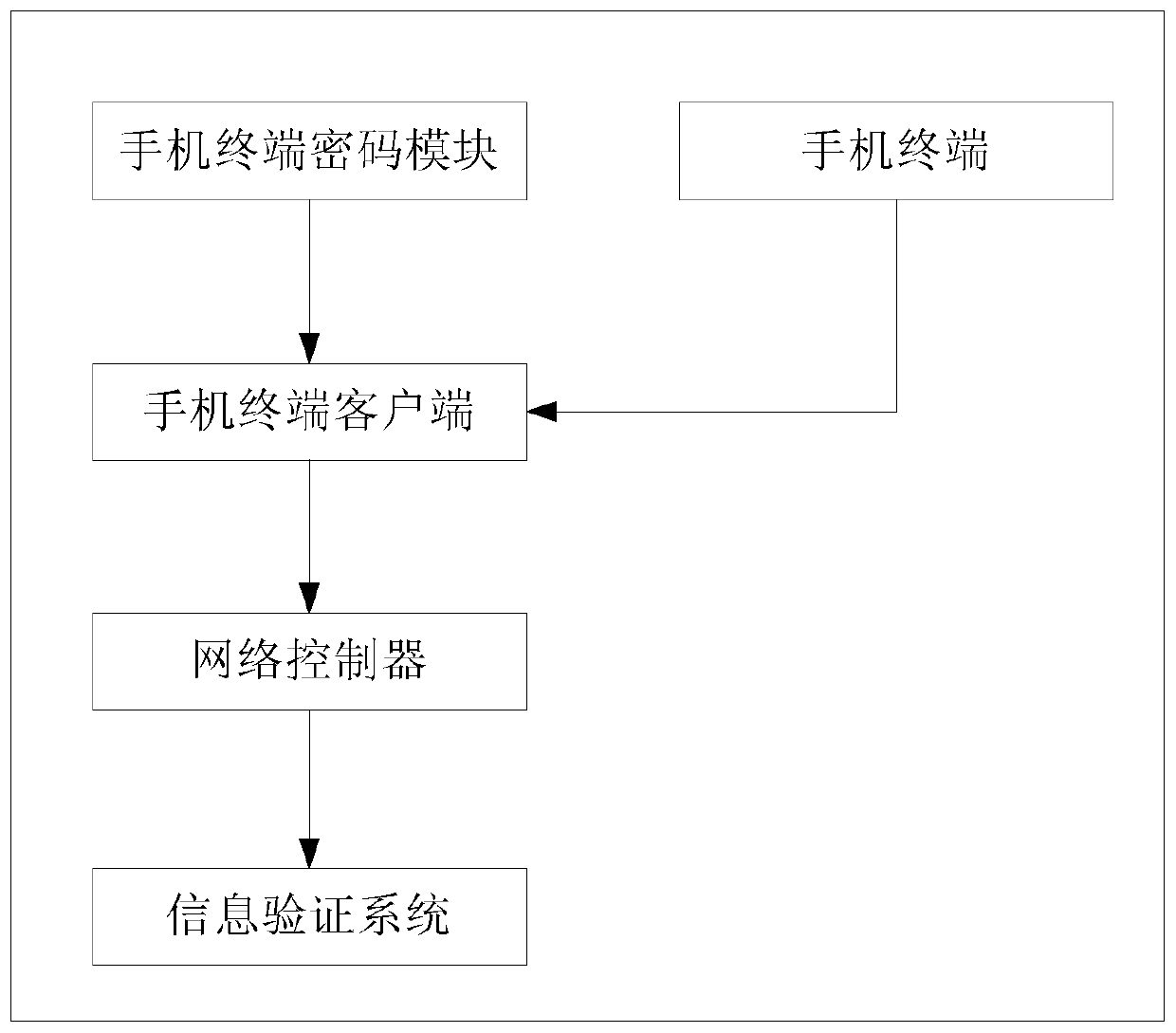
[0090] In Embodiment 1 provided by the present invention, the mobile phone terminal encryption module is inSE as an example for description. The equipment and environment configuration of this embodiment 1 are as follows:
[0091] 1) Complete information network environment;
[0092] 2) A mobile terminal with inSE built-in mobile terminal password module, has obtained a user digital certificate, and has been written into inSE. The mobile terminal network control APP has been installed. With mobile wireless network data communication capabilities. Has a front camera.
[0093] 3) A network control server, deployed at the entrance of the information network, can establish an HTTPS connection with the mobile terminal, and has the capability of signature verification.
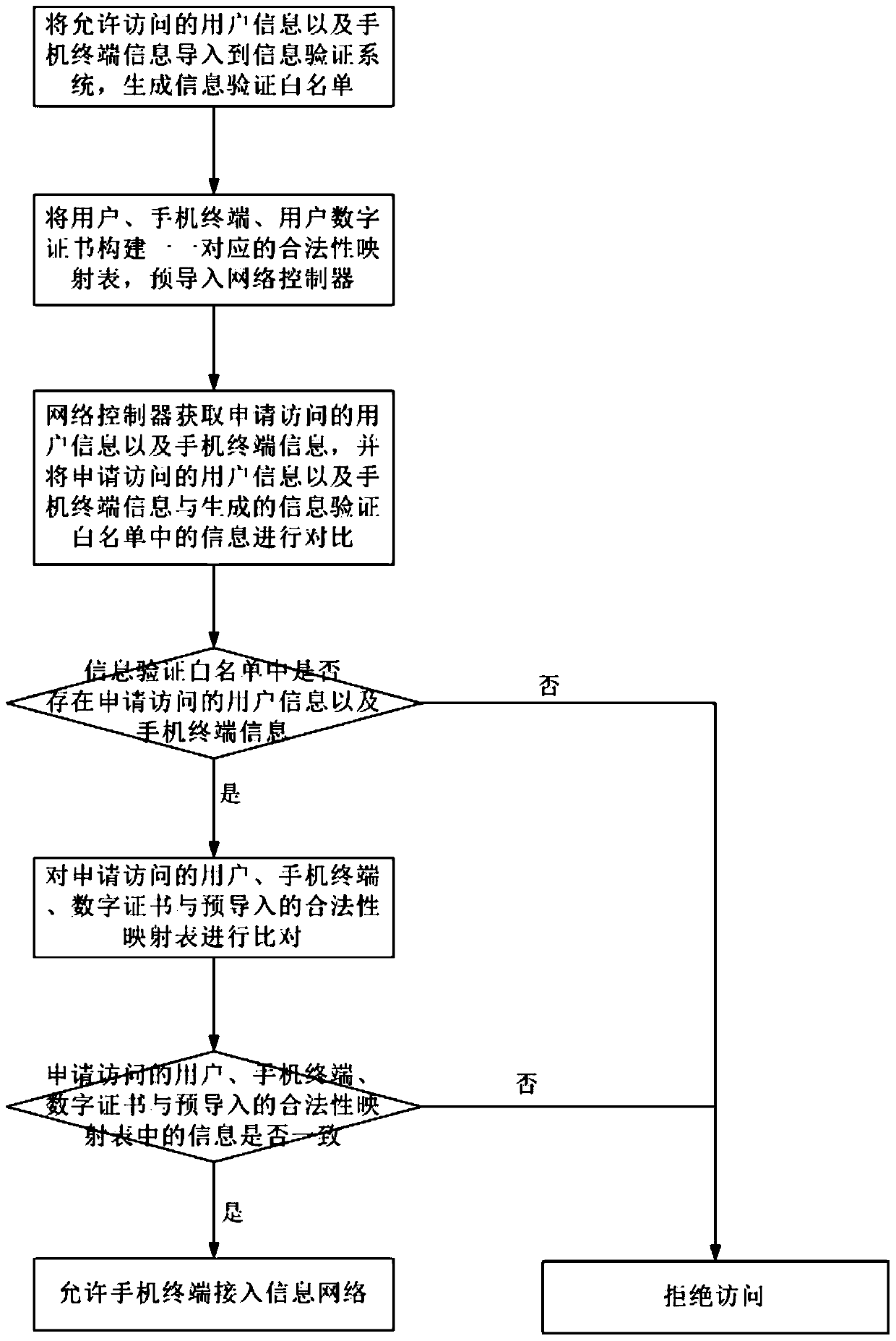
[0094] 4) A portrait data server, deployed in the information network, imports the portrait information of legal users in advance, and provides an interface for querying the portrait information of legal users. ...
Embodiment 2
[0115] In Embodiment 2 provided by the present invention, the mobile phone terminal encryption module is a TF card as an example for description. The equipment and environment configuration of this embodiment 2 are as follows:
[0116] 1) Complete information network environment;
[0117] 2) A mobile phone terminal with TF card interface, and the TF card of the cryptographic module has been inserted; the user digital certificate has been obtained and written into the TF card; the mobile terminal network control APP has been installed; it has the capability of mobile wireless network data communication; Front camera;
[0118] 3) A network control server, deployed at the entrance of the information network, can establish an HTTPS connection with the mobile terminal, and has the capability of signature verification;
[0119] 4) In the private cloud of the information network, create three virtual cloud hosts to realize the cloud deployment of the portrait data server, the termi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com