Database security auditing method and system and computer readable storage medium
A security audit and database technology, applied in the field of network security, can solve the problems of lack of database security audit methods, etc., and achieve the effect of reducing the workload of manual audit, improving work efficiency, and increasing coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The specific embodiments of the present invention are used to illustrate the present invention, but are not limited to the specific embodiments.
[0023] According to the application scenario of the express industry system, this embodiment audits various operation behaviors of the database account. Certainly, the present invention is not only applicable to the security audit of the express industry database, but also applicable to various business systems and databases with huge data volume.
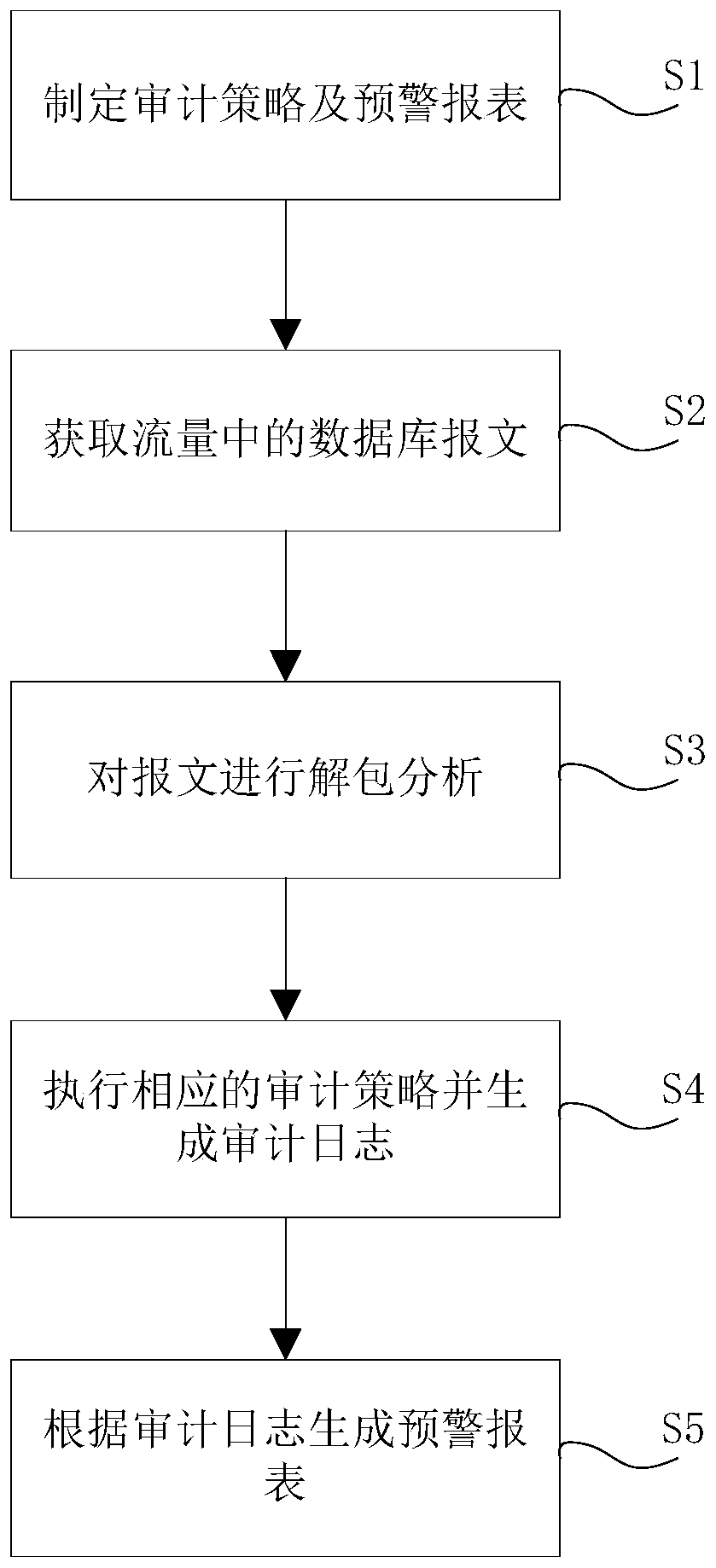
[0024] figure 1 It is an overall flowchart of the database security audit method in the embodiment of the present invention.
[0025] Such as figure 1 As shown, the database security audit method of the present embodiment includes the following steps:
[0026] Step S1, formulate an audit strategy and an early warning report for the operation behavior of the database account.
[0027] The operation behavior of the database account includes the operation behavior of the personal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com