Microblog user trust evaluation method based on trust propagation
A trust propagation and user technology, applied in the field of social network analysis, can solve problems such as sensitive information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with accompanying drawing:
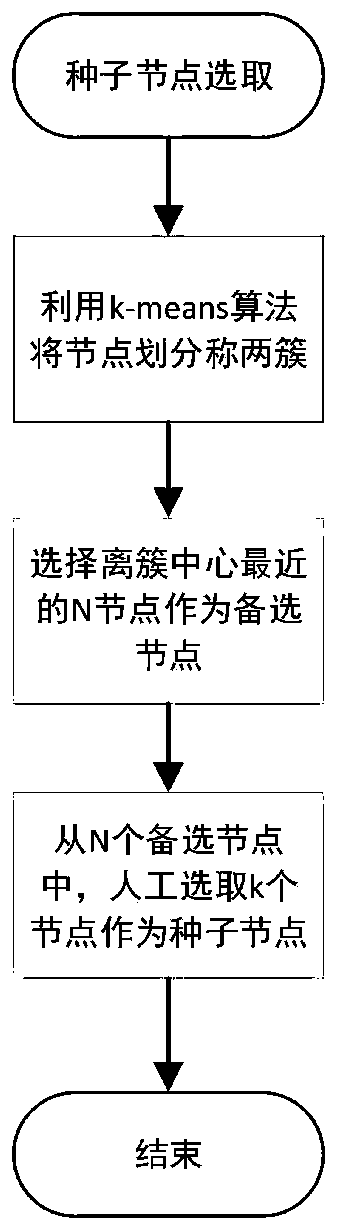
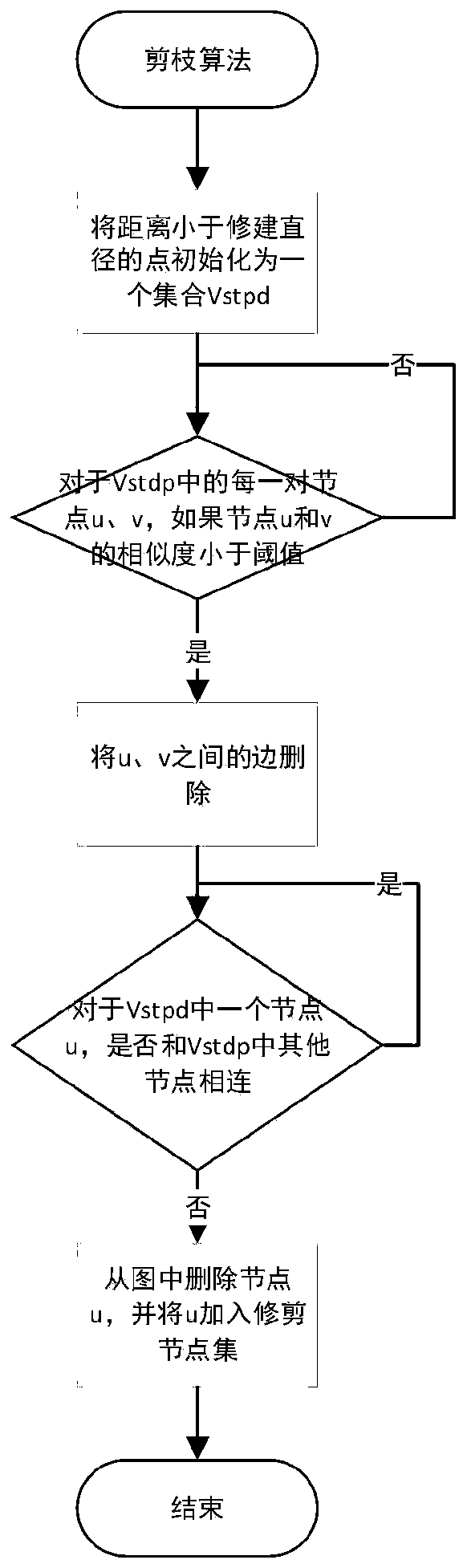
[0035] as attached figure 1 As shown, for user u i and user u j relationship; as attached figure 2 As shown, it is the flow chart of the seed node selection method; as attached image 3 Shown is the flow chart of the pruning method; as attached Figure 4 Shown is the flow chart of the trust propagation method.
[0036] 1. In Weibo, users and their social relationships (such as followers and following relationships) and social activities (such as posting Weibo and hot topics) are the main entities. Some typical social activities in Weibo are summarized in Table 1.
[0037] Table 1 Five social activities in Weibo
[0038]
[0039]In order to distinguish malicious activities from legitimate activities, a very intuitive idea is to distinguish whether the social activities of these entities are malicious activities by measuring the trustworthiness of each entity. Thi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com