A method for cracking encrypted mails
A mail and mail server technology, applied in the direction of electrical components, digital transmission systems, transmission systems, etc., can solve problems such as low cracking efficiency and affect user behavior, and achieve high cracking efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Attached below figure 1 , the present invention is further elaborated:
[0021] A method for decrypting encrypted emails, its implementation is as follows:
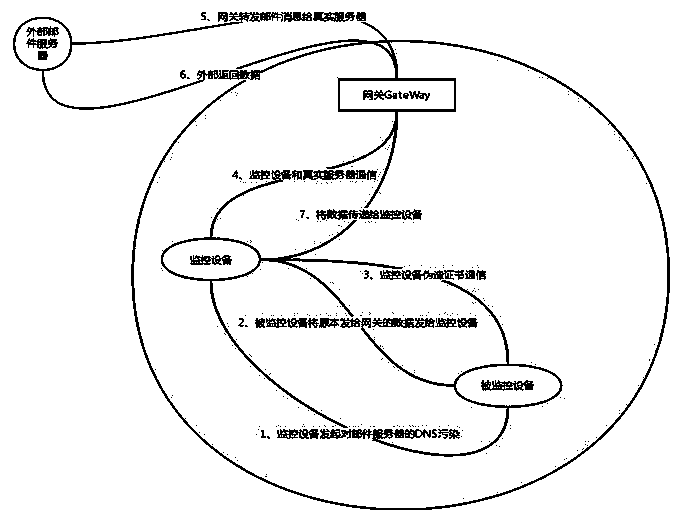
[0022] DNS pollutes the real mail server, so that the data originally sent to the real server is forwarded to the mail monitoring device.
[0023] The monitoring device uses the forged certificate of Openssl to deceive the monitored host.
[0024] The monitoring device uses the local private key to decrypt the network data from the monitored host.
[0025] The monitoring host sends the analyzed real data to the real server.
[0026] Combined with the accompanying drawings, the system is mainly composed of monitoring equipment and monitored hosts. The monitoring device is deployed on the switch bypass branch, and the monitored hosts are all hosts under the switch. The monitoring equipment mainly cracks and records the encrypted email behavior generated by the monitored host.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com