SM4 algorithm white box implementation method and device
An implementation method and white-box technology, which is applied in the fields of information security and cryptography applications, can solve problems such as confusion of cryptographic algorithms, failure of SM4 white-box algorithms and products to meet practical applications, and poor versatility of SM4 white-box algorithms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
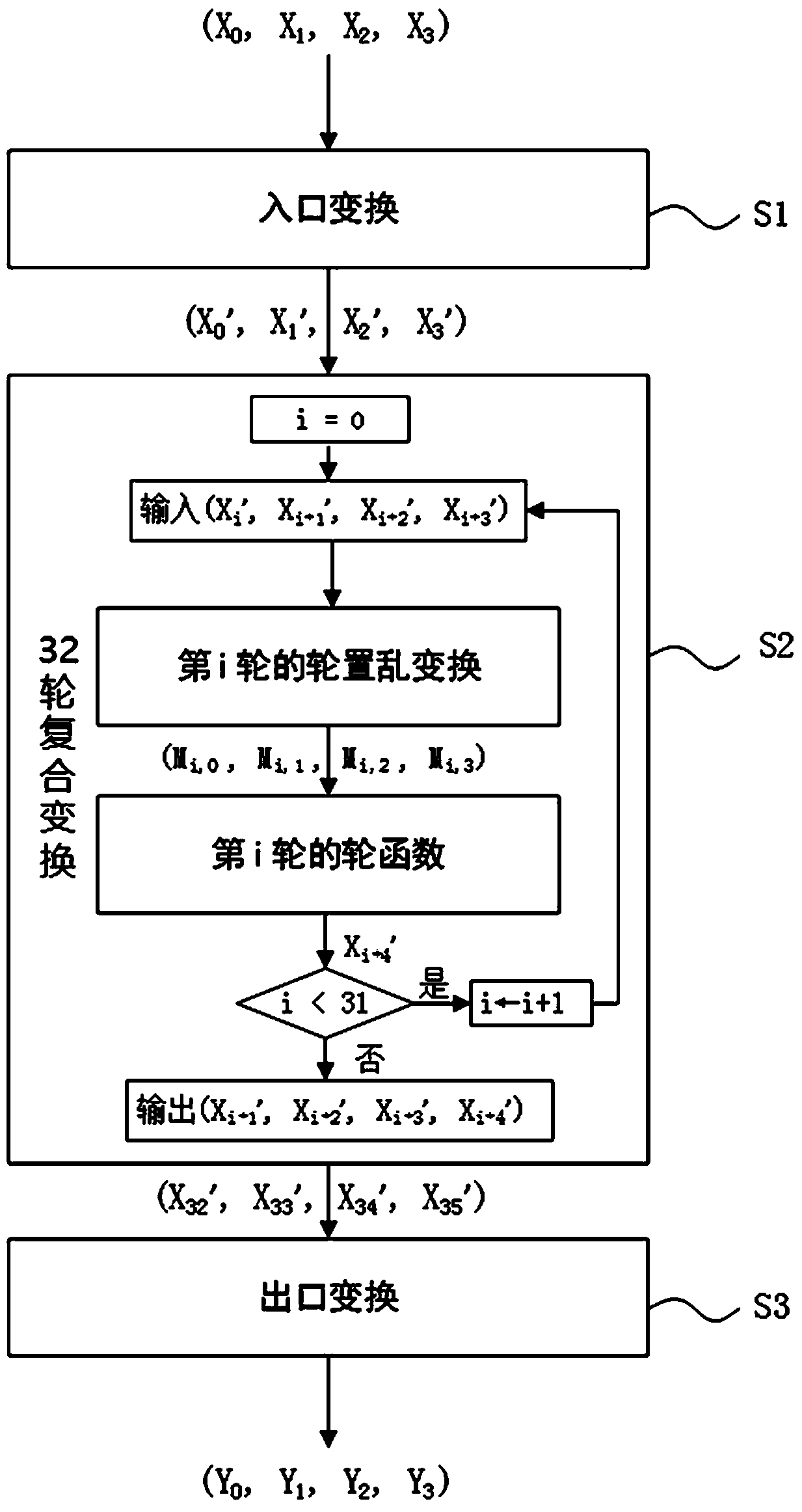
[0060] Such as figure 1 Shown, a kind of SM4 algorithm white-box implementation method comprises the following steps:
[0061] S1, 128-bit input data (X 0 ,X 1 ,X 2 ,X 3 ) to obtain 128-bit data (X 0 ’,X 1 ’,X 2 ’,X 3 ');
[0062] S2, (X 0 ’,X 1 ’,X 2 ’,X 3 ’) After 32 rounds of compound transformation, 128-bit data (X 32 ’,X 33 ’,X 34 ’,X 35 '); the compound transformation of each round is composed of round scrambling transformation and round function, assuming 0≤i≤31, in the compound transformation of the i-th round, the input of the round scrambling transformation is 128 bits Data (X i ’,X i+1 ’,X i+2 ’,X i+3 ’), the output is 128-bit data (M i,0 , M i,1 , M i,2 , M i,3 ), the input of the round function in this round is (M i,0 , M i,1 , M i,2 , M i,3 ), the output is 32-bit data X i+4 ’; where the round key of each round is generated by the encryption key and hidden in the round function;
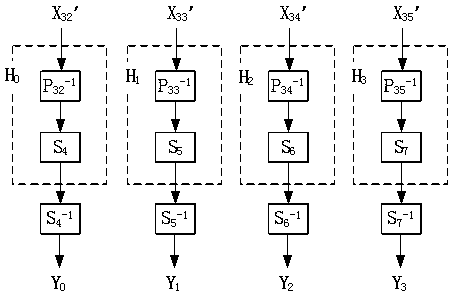
[0063] S3, (X 32 ’,X 33 ’,X 34 ’,X 35 ’) get the ...
Embodiment 2
[0095] Based on the same inventive concept as the above-mentioned method, as figure 2 As shown, the present embodiment is a white-box implementation device for SM4 algorithm, including an entry transformation unit, a composite transformation unit, and an exit transformation unit, and the composite transformation unit is connected to the entry transformation unit and the exit transformation unit respectively; The compound transformation unit includes a round scrambling transformation module and a round function module;
[0096] The entry conversion unit will input 128-bit data (X 0 ,X 1 ,X 2 ,X 3 ) for entry conversion to obtain 128-bit data (X 0 ’,X 1 ’,X 2 ’,X 3 '); the composite transformation unit will (X 0 ’,X 1 ’,X 2 ’,X 3 ’) to perform 32 rounds of compound transformations to obtain 128-bit data (X 32 ’,X 33 ’,X 34 ’,X 35 ’); the export transformation unit will (X 32 ’,X 33 ’,X 34 ’,X 35 ’) to carry out export conversion, and obtain the 128-bit output...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com