Application program monitoring method, device and system
A technology of application programs and monitoring devices, applied in the computer field, can solve problems such as the difficulty of accurately judging whether an application program has been monitored, and achieve the effect of convenient monitoring and management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] In the embodiment provided by the present invention, the applied container cluster is described by taking the creation of the container cluster based on the Kubernetes open source orchestration software, that is, the k8s container cluster as an example.
[0053] In a k8s cluster, there are generally multiple hosts, and multiple Pods run on each host. The Pod is the basic operating unit of the k8s cluster. A Pod consists of one container or multiple containers. The containers contained in the Pod run on the same On the host, using the same network command space, IP address and port, they can discover and communicate with each other through the local host, and can also share a storage volume space. Applications in the same Pod can see each other's processes, and can also Use systemVipc or posix message queues for communication.
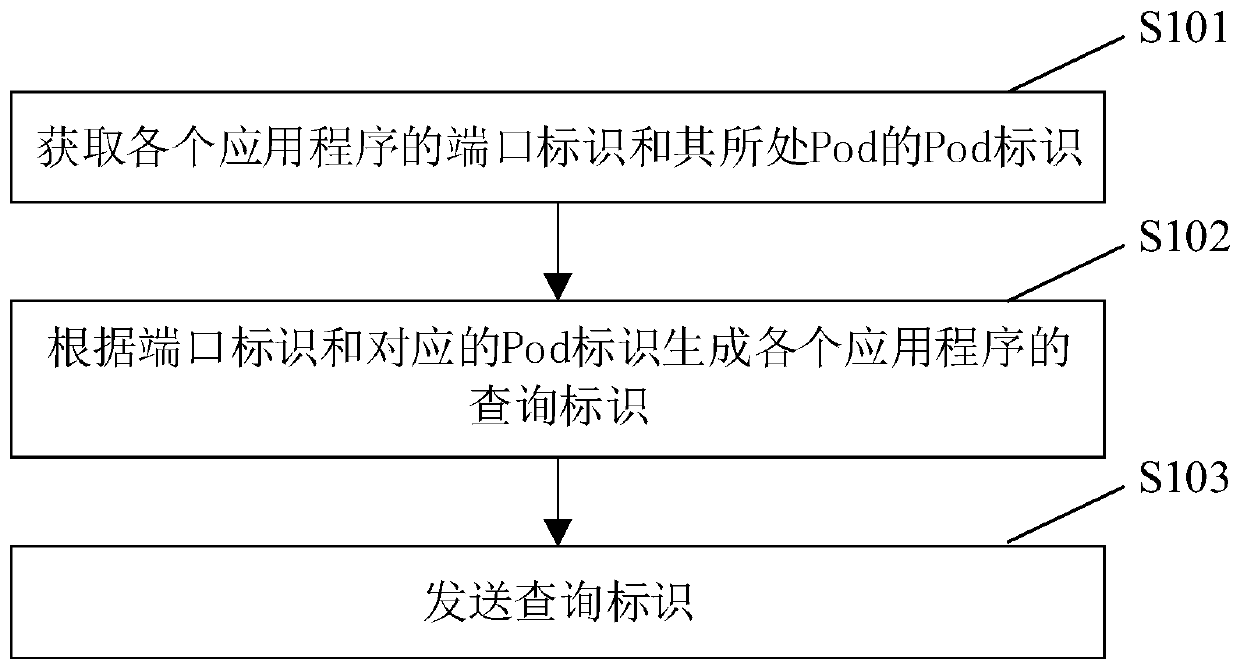
[0054] figure 1 A flowchart of an application program monitoring method according to an embodiment of the present invention is shown. The meth...
Embodiment 2
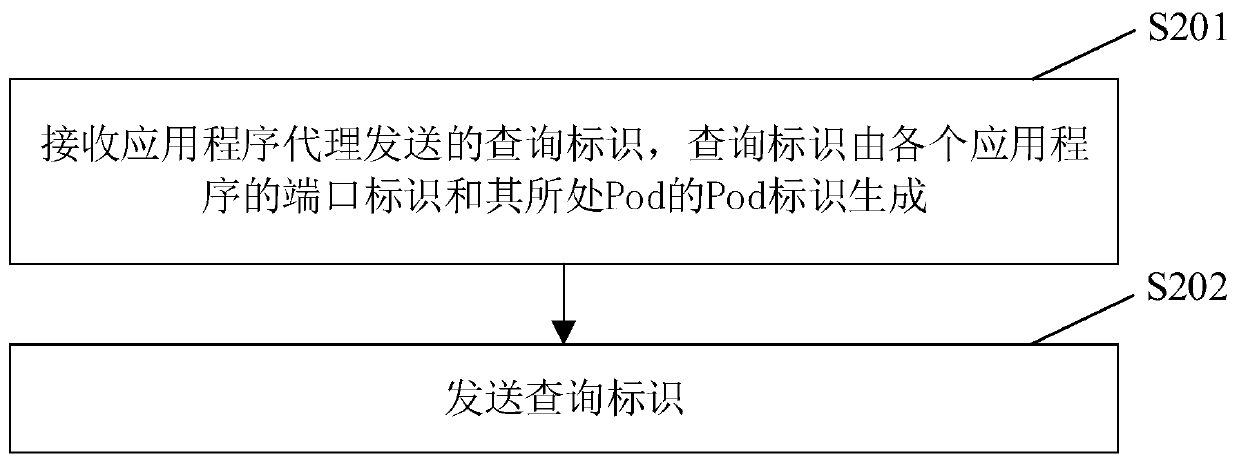
[0072] figure 2 A flow chart of another application program monitoring method according to an embodiment of the present invention is shown. The method is applied to the host in the above-mentioned k8s cluster, the host includes at least one Pod, and one of the at least one Pod is deployed with a monitoring server agent, and the monitoring server agent monitors at least one application agent. This method can be used for each application in the container cluster program to monitor, such as figure 2 As shown, the method includes the following steps:
[0073] Step S201: The monitoring server agent receives the query ID sent by the application program agent, and the query ID is generated by the port ID of each application program and the Pod ID of the Pod where it is located.
[0074] Specifically, for the generation process of the above-mentioned query identifier, refer to the relevant descriptions of the above-mentioned step S101 and step S102, and details are not repeated he...
Embodiment 3
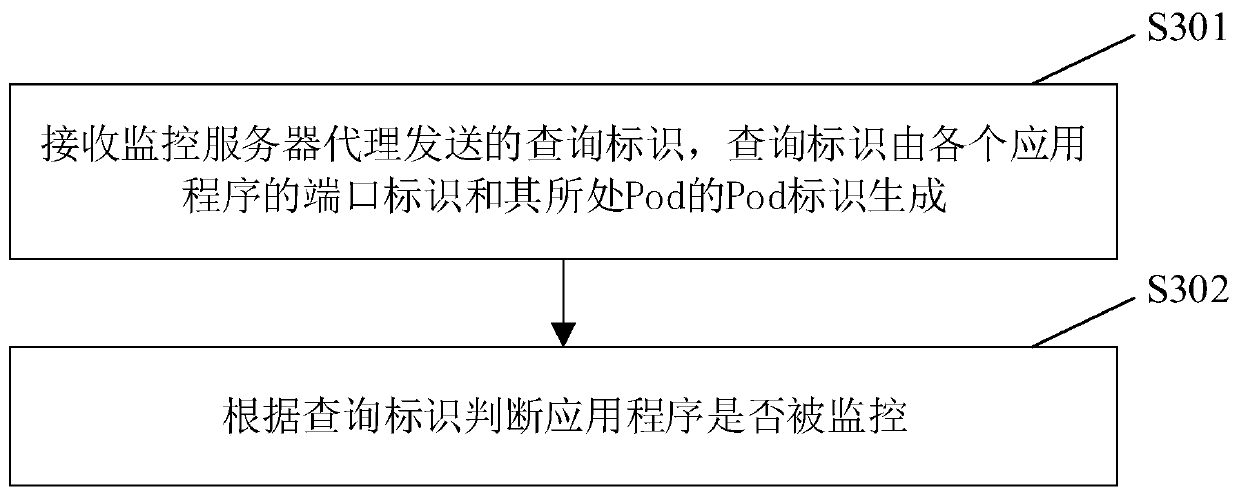
[0088] image 3 A flow chart of another application program monitoring method according to an embodiment of the present invention is shown. This method is applied to monitor the monitoring server of the above-mentioned k8s cluster, and this method can be used to monitor various applications in the container cluster, such as image 3 As shown, the method includes the following steps:
[0089] Step S301: The monitoring server receives the query ID sent by the monitoring server agent, and the query ID is generated by the port ID of each application program and the Pod ID of the Pod where it is located.
[0090] Specifically, for the generation process of the above-mentioned query identifier, refer to the relevant descriptions of the above-mentioned step S101 and step S102, and details are not repeated here. In practical applications, the query identifier sent by the monitoring server agent is received through the above monitoring server.
[0091] Step S302: The monitoring serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com