Intelligent lock control technology based on encrypted two-dimensional code and IPV6
A control technology and smart lock technology, applied in the field of smart locks, can solve the problems of easy adhesion of fingerprints to the scanning board, insufficient practicability, and increased work difficulty, so as to increase practicability and convenience, increase work efficiency and improve work efficiency. Economic benefits, effects of increased safety and practicality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
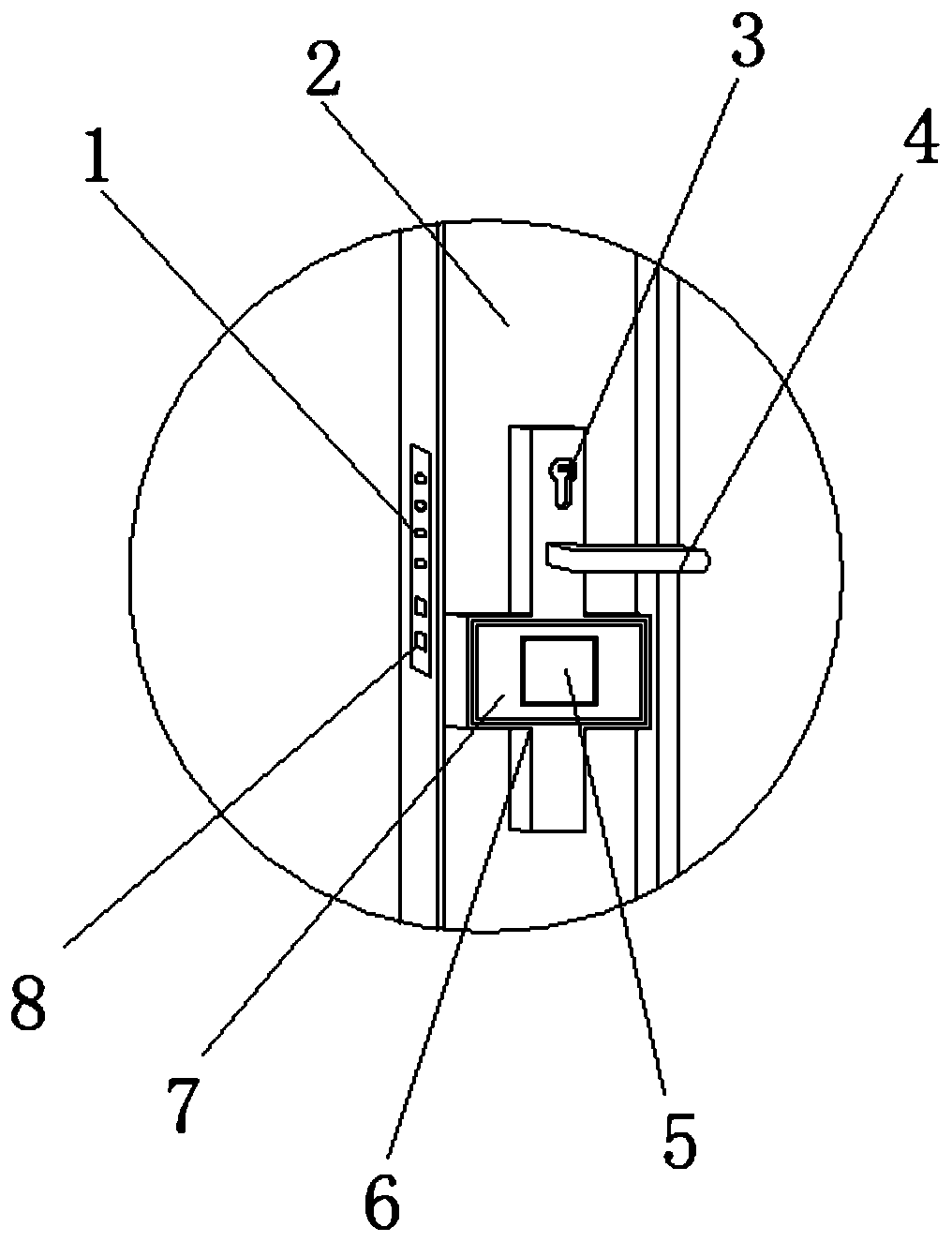
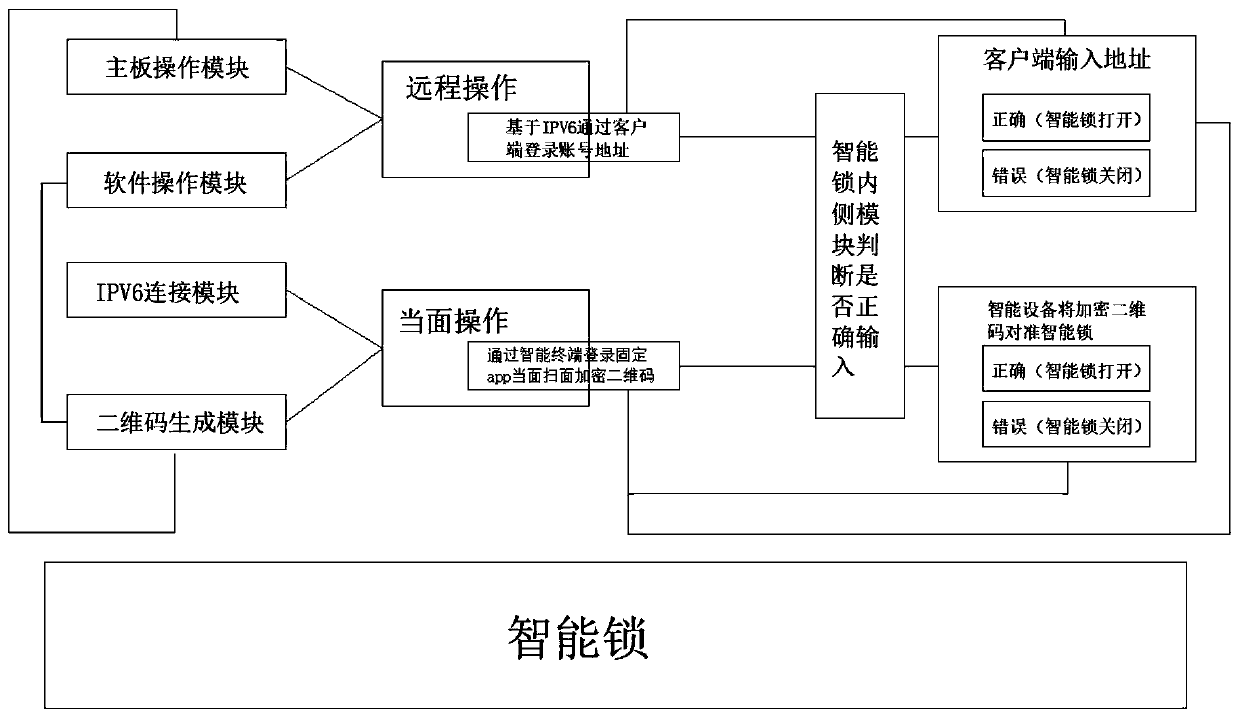
[0019] see Figure 1 to Figure 3 , the present invention provides a technical solution: an intelligent lock control technology based on encrypted two-dimensional code and IPV6, including an intelligent lock, a mainboard operation module inside the intelligent lock, a software operation module, an IPV6 connection module and a two-dimensional code generation module, The smart lock includes a shell 6, an operation panel 2 is arranged around the shell 6, a fixed plate 7 is fixedly connected in the middle of the shell 6, a display screen 5 is fixedly connected in the middle of the fixed plate 7, and a keyhole 3 is opened in the middle of the top of the shell 6. And the keyhole 3 runs through one side surface of the casing 6, the middle of the top of the casing 6 is fixedly connected with the handle 4, the middle of one side of the casing 6 corresponds to the position of the operation panel 2 and is fixedly connected with the limit column 1, and the bottom of the limit column 1 The ...
Embodiment 2
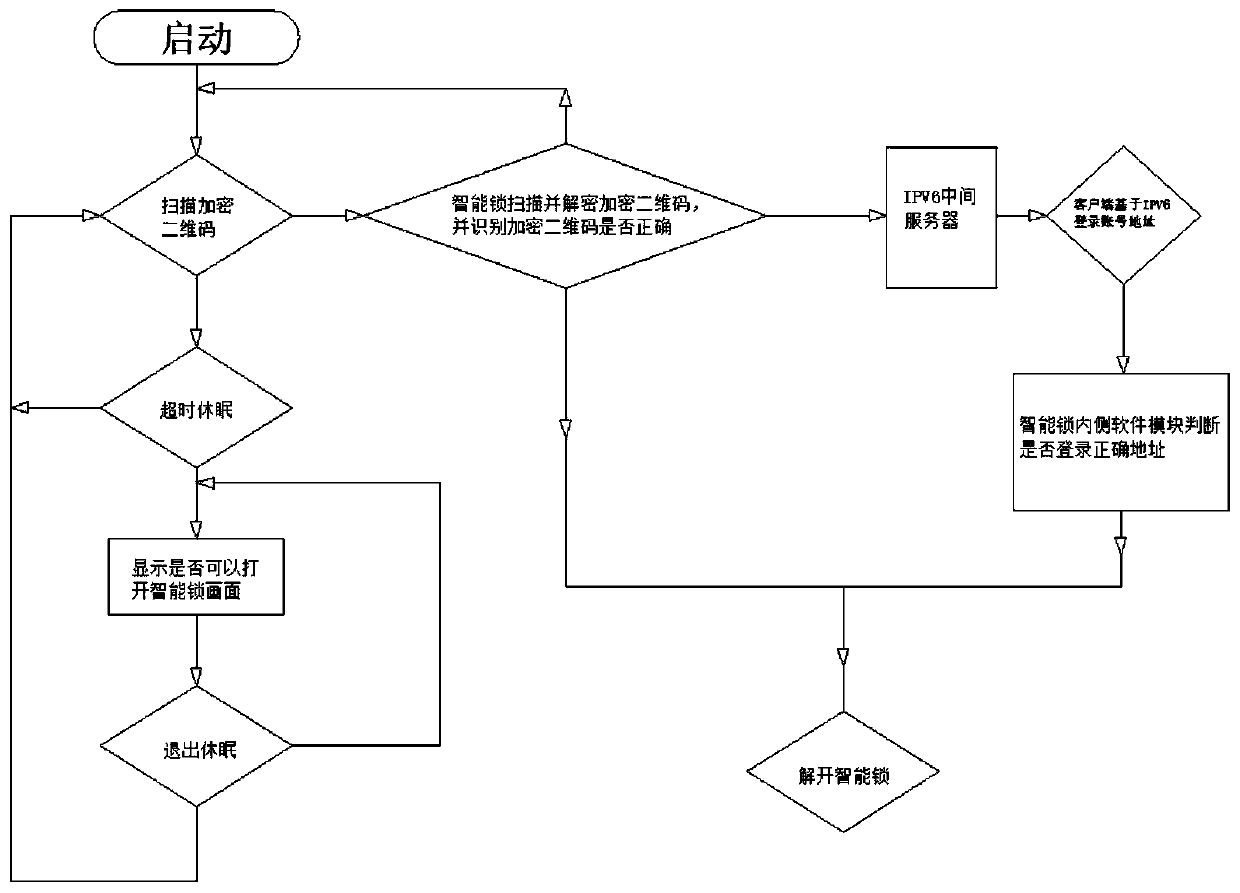
[0025]Input the original data into the inner side of the mainboard operation module inside the smart lock to generate a software lock. The specified counterpart data must be matched with the original data inside the mainboard operation module inside the smart lock before the software lock can be opened. After the software lock is opened, the smart lock is opened, and the software operation module can effectively connect to the external client. Through the connection between the client and the software operation module, it can be effectively judged whether the encrypted QR code is a correct QR code. When scanning When reading the encrypted two-dimensional code on the client and smart device, call the symmetric algorithm to decrypt the encrypted two-dimensional code through the public key corresponding to the private key. If the encrypted two-dimensional code is scanned correctly, the smart lock can be unlocked , when the encrypted QR code is scanned incorrectly, the smart lock w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com