Cross-regional data security efficient interaction system and method for monitoring platform of electric power communication network
A power communication network and monitoring platform technology, applied in transmission systems, electrical components, etc., can solve problems such as high delay, low efficiency, and potential security risks in data interaction, and achieve low delay, efficiency improvement, and throughput. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
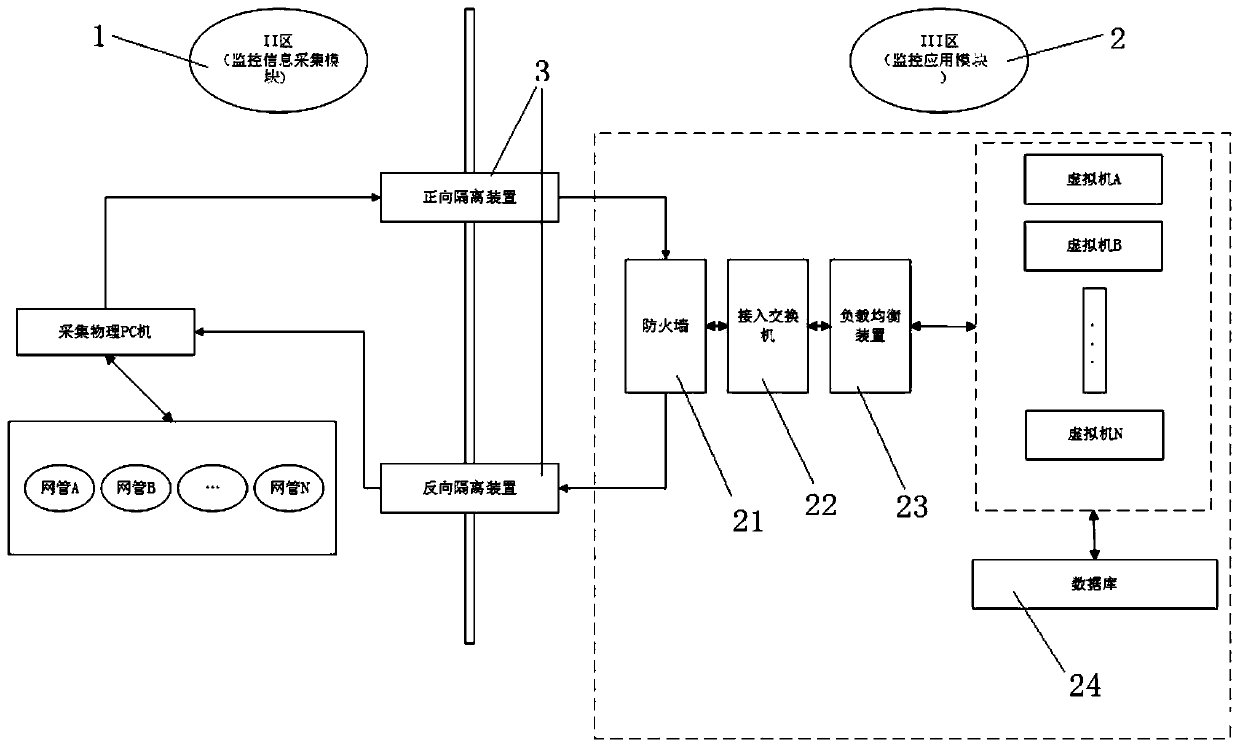
[0048] Such as figure 1 As shown, a power communication network monitoring platform cross-regional data security and efficient interaction system, including a monitoring information collection module 1, a monitoring application module 2 and an isolation device 3;
[0049] The monitoring information collection module 1 is used to collect the operation data of each network management, and transmits the collected data to the monitoring application module 2 for use by each business module;
[0050] The isolating device 3 is arranged between the monitoring information collection module 1 and the monitoring application module 2, the isolating device 3 includes a forward isolating device and a reverse isolating device, and the forward isolating device is used to realize the The one-way transmission of data from the monitoring information collection module 1 to the monitoring application module 2, the reverse isolation device is used to realize the one-way data transmission from the m...
Embodiment 2
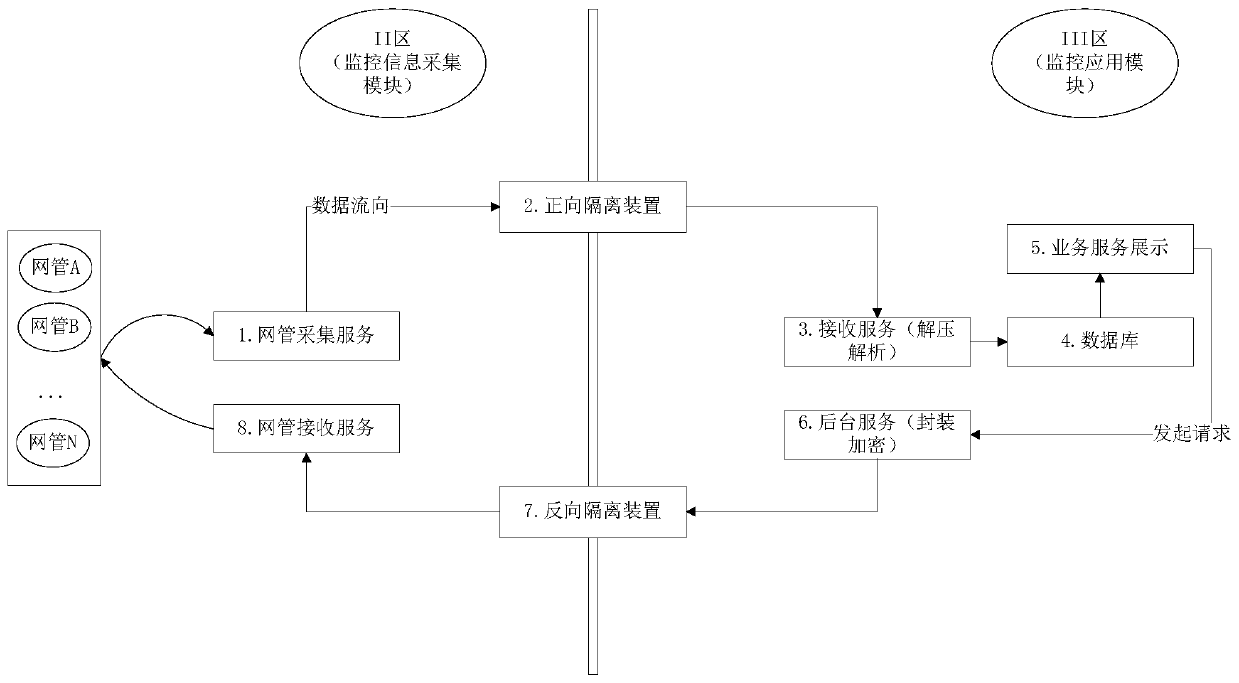
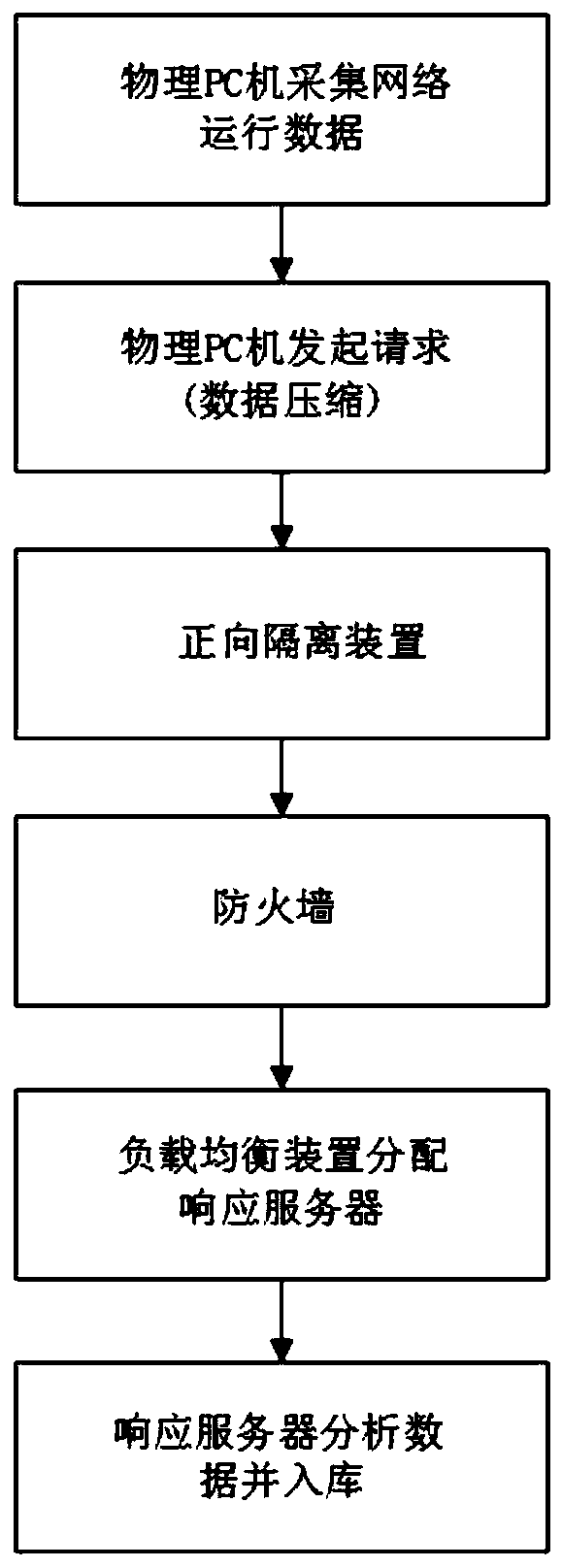
[0062] Such as Figure 2 to Figure 4 As shown, the difference between this embodiment and Embodiment 1 is that a safe and efficient cross-regional data interaction method for a power communication network monitoring platform includes forward isolation and reverse isolation, and the forward isolation collects each The operating data of the network management, and compress the collected data, and transmit it to the monitoring application module to receive the service through the forward isolation device, and perform decompression analysis and data storage; the reverse isolation is initiated by the user on each business module, and the monitoring The background of the application module receives the request, encapsulates and encrypts the request data according to the custom protocol, and then sends it to each network management command receiving service of the monitoring information collection module through the reverse isolation device, decrypts the data, and verifies whether the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com