Blind Signcryption Method in Lattice Public Key Cryptosystem
A public key cryptography system and blind signature technology, applied in the field of network information security, can solve problems such as low calculation efficiency, abnormal scheme signature, unqualified, etc., and achieve the effect of improving operation efficiency, resisting quantum attacks, and high operation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
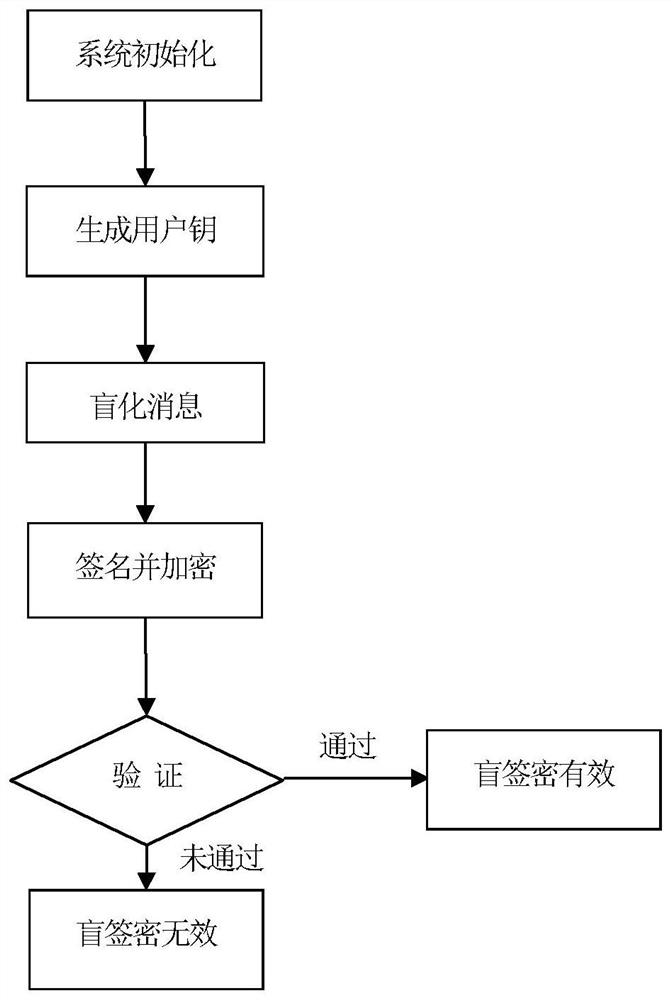
[0076] In this embodiment, the large prime number q is 2 128 For example, in figure 1 , the blind signcryption method under the lattice public key system of the present embodiment consists of the following steps:
[0077] A. System initialization
[0078] (A1) A trusted party defines a residual-like ring Z modulo q q The n-row and nk-column matrix G on, modulo q is:
[0079] q=p v
[0080] Wherein p is a large prime number, and v is a finite positive integer; in this embodiment, p is 2, and v is 128.
[0081] (A2) The trusted party defines three integers m 0 , m, m 1 Dimension to use as a matrix vector.
[0082] (A3) The trusted party defines the error rate α∈(0, 1) with error learning, and selects the Gaussian parameter
[0083]
[0084] (A4) The trusted party defines the ring R:
[0085] R=Z q [x] / f(x)
[0086] where f(x) is a polynomial. The f(x) of this embodiment is:
[0087] f(x)=x n +a n x n-1 +…+a 2 x+a 1
[0088] An irreducible polynomial whose ...
Embodiment 2
[0144] In this embodiment, the large prime number q is 2 256 For example, the blind signcryption method under the lattice public key system consists of the following steps:
[0145] A. System initialization
[0146] (A1) A trusted party defines a residual-like ring Z modulo q q The n-row and nk-column matrix G on, modulo q is:
[0147] q=p v
[0148] where p is a large prime number, and v is a finite positive integer; in this embodiment, p is 2 and v is 256.
[0149] The other steps of this step are the same as in Example 1.
[0150] Other steps are the same as in Example 1.
Embodiment 3
[0152] In this embodiment, the large prime number q is 2 512 For example, the blind signcryption method under the lattice public key system consists of the following steps:
[0153] A. System initialization
[0154] (A1) A trusted party defines a residual-like ring Z modulo q q On an n-row and nk-column matrix G, q is:
[0155] q=p v
[0156] where p is a large prime number, and v is a finite positive integer; in this embodiment, p is 2 and v is 512.
[0157] The other steps of this step are the same as in Example 1.
[0158] Other steps are the same as in Example 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com