A kind of Android vehicle terminal system vulnerability detection system and method
A vehicle-mounted terminal and vulnerability detection technology, applied in the field of vulnerability detection, can solve the problems of lack of vulnerability library maintenance, lack of versatility, incomplete detection results, etc., to achieve the effect of enhancing scalability and easy and convenient modification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
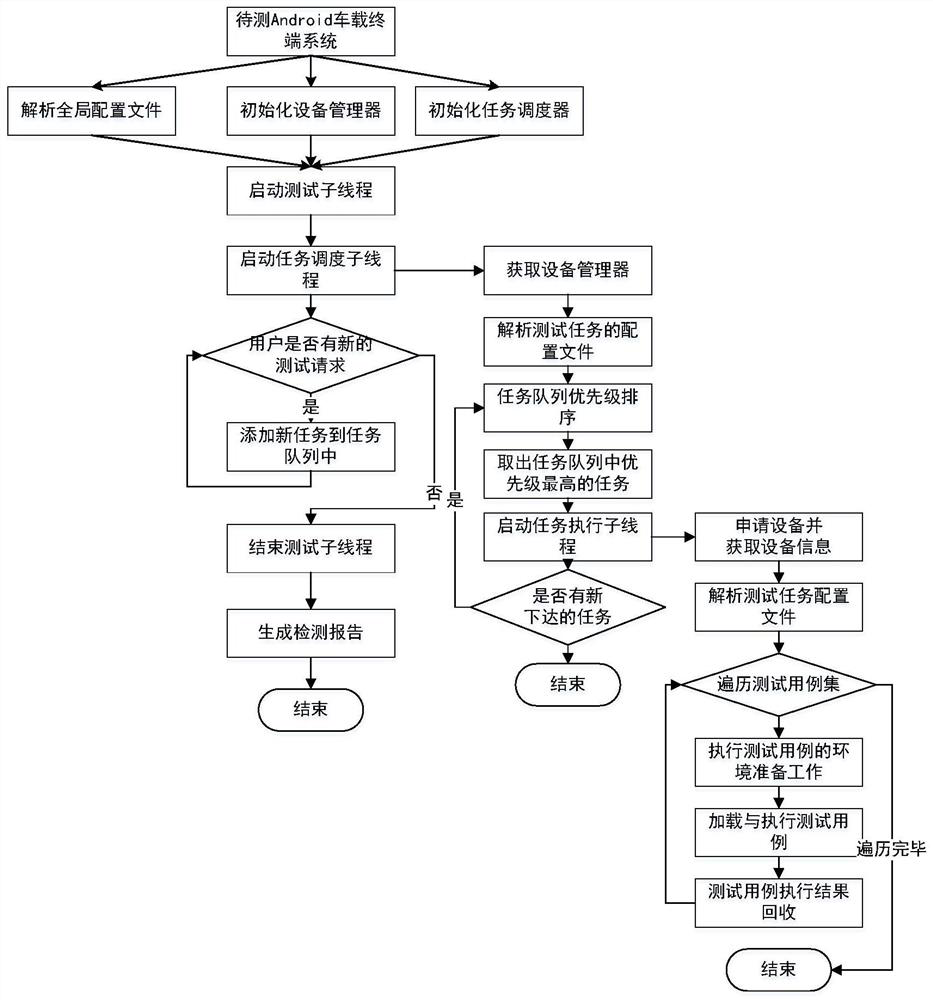
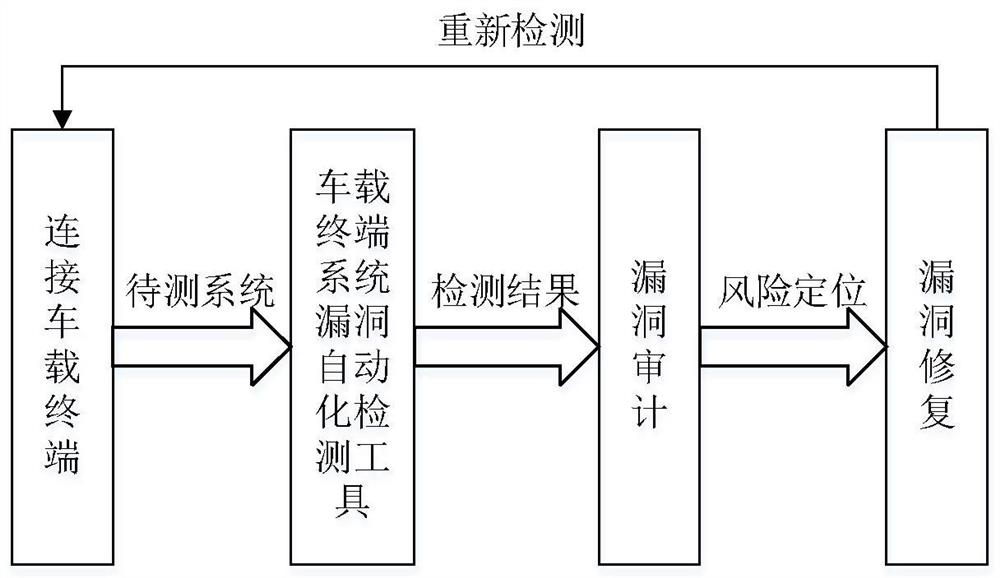
[0085] Attached to the following Figure 1-4 The present invention will be described in further detail.
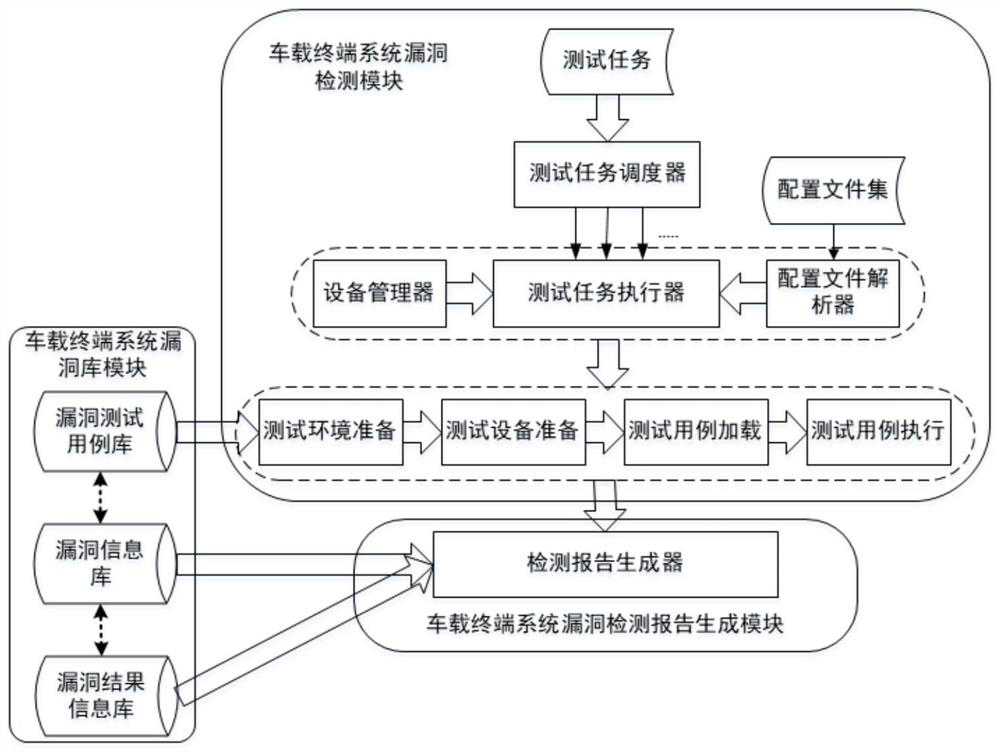
[0086] The tool is divided into three modules: Android vehicle terminal system vulnerability library module, Android vehicle terminal system vulnerability detection module, vehicle terminal system vulnerability detection report generation module. The system architecture diagram is as follows figure 1 shown.
[0087] 1) Vehicle terminal system vulnerability library module
[0088] (1) Vulnerability collection
[0089] Before building the vehicle terminal system vulnerability library, it is necessary to collect relevant typical vulnerabilities and study their vulnerability principles and other information. Vulnerabilities of typical operating systems are collected from three channels: related vehicle operating system vulnerabilities released by standard vulnerability libraries such as CVE and CNNVD, vulnerabilities collected from the Internet, and self-mining vulnerabili...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com