Interface authentication method and system based on SE chip and storage medium
An authentication method and interface technology, applied in transmission systems, electrical components, etc., can solve problems such as security vulnerabilities and transmission information leakage, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
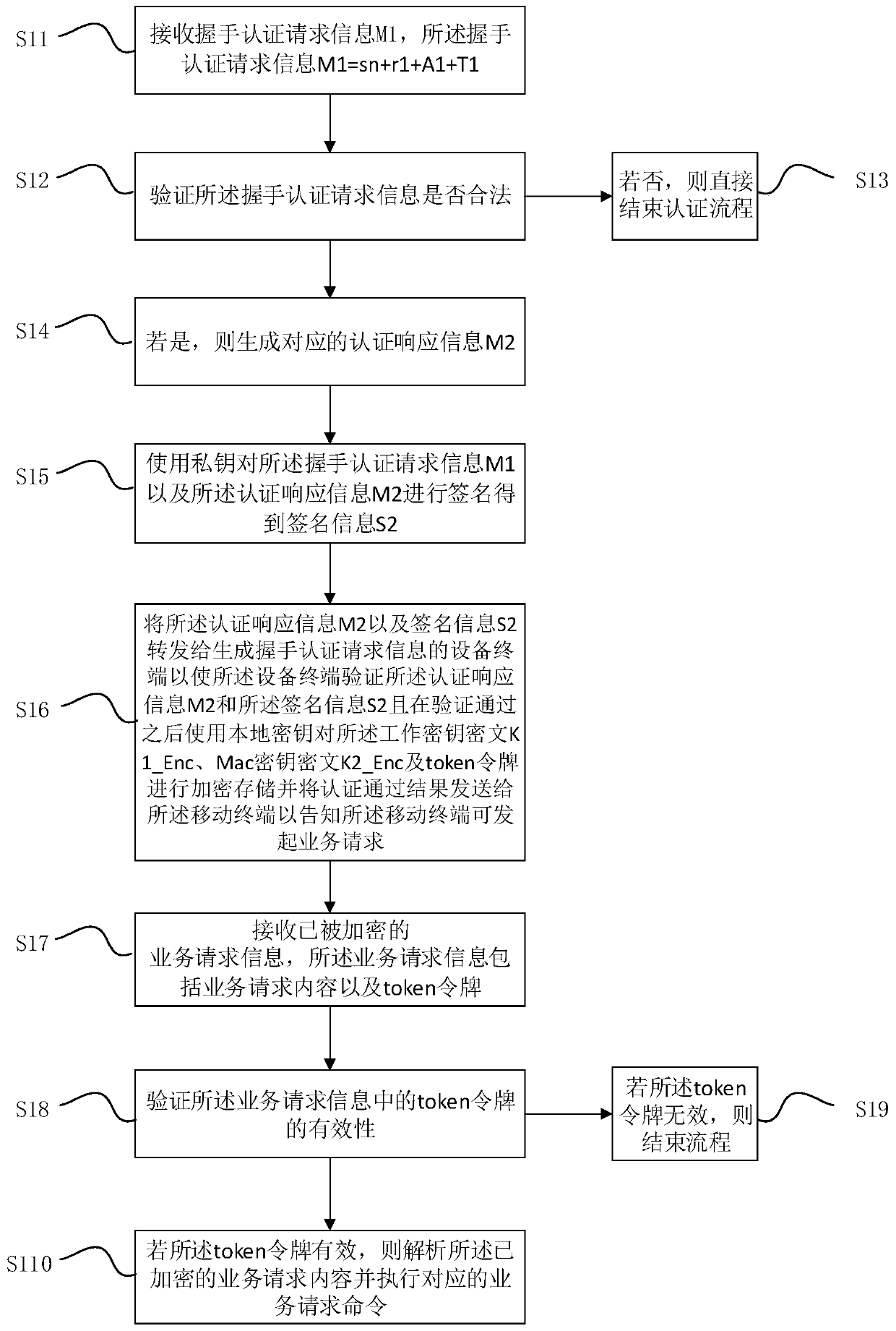
[0067] As a preferred embodiment, it also includes the following steps:
[0068] After the business request command is executed, determine whether the business request is the final business request;
[0069] If so, generate and encrypt response information that does not contain sensitive information, and the response information is also encrypted by the SM4 algorithm and transmitted through a secure channel;
[0070] If not, a response message containing sensitive information is generated and encrypted;
[0071] Return the encrypted response information to the mobile terminal that initiated the service request so that the mobile terminal can judge whether to initiate the next round of service request according to the response information; wherein, if the response information contains sensitive information, initiate the next round of service request A round of service requests; if the response information does not contain sensitive information, the current process is completed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com