Credible power access control method based on block chain
An access control and block chain technology, applied in the direction of instruments, electrical digital data processing, digital data protection, etc., to achieve the effect of ensuring security, simple implementation method, and data authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
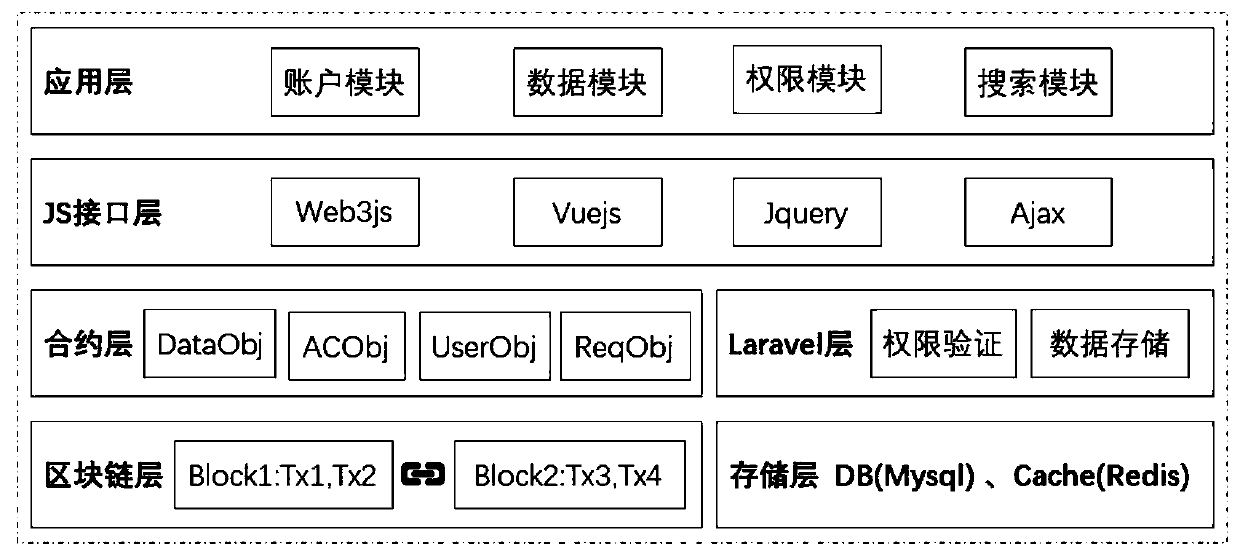
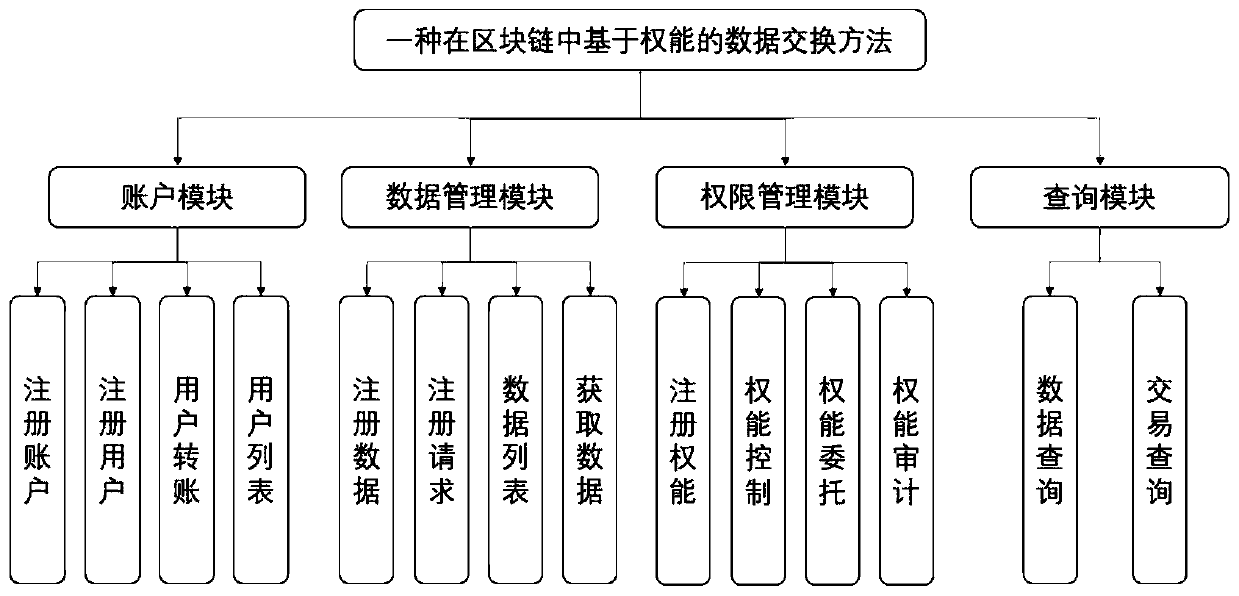
[0065] In order to describe the content and object of the present invention more concisely and clearly, the present invention will be further described below in conjunction with the accompanying drawings. The specific steps to implement the case are as follows:
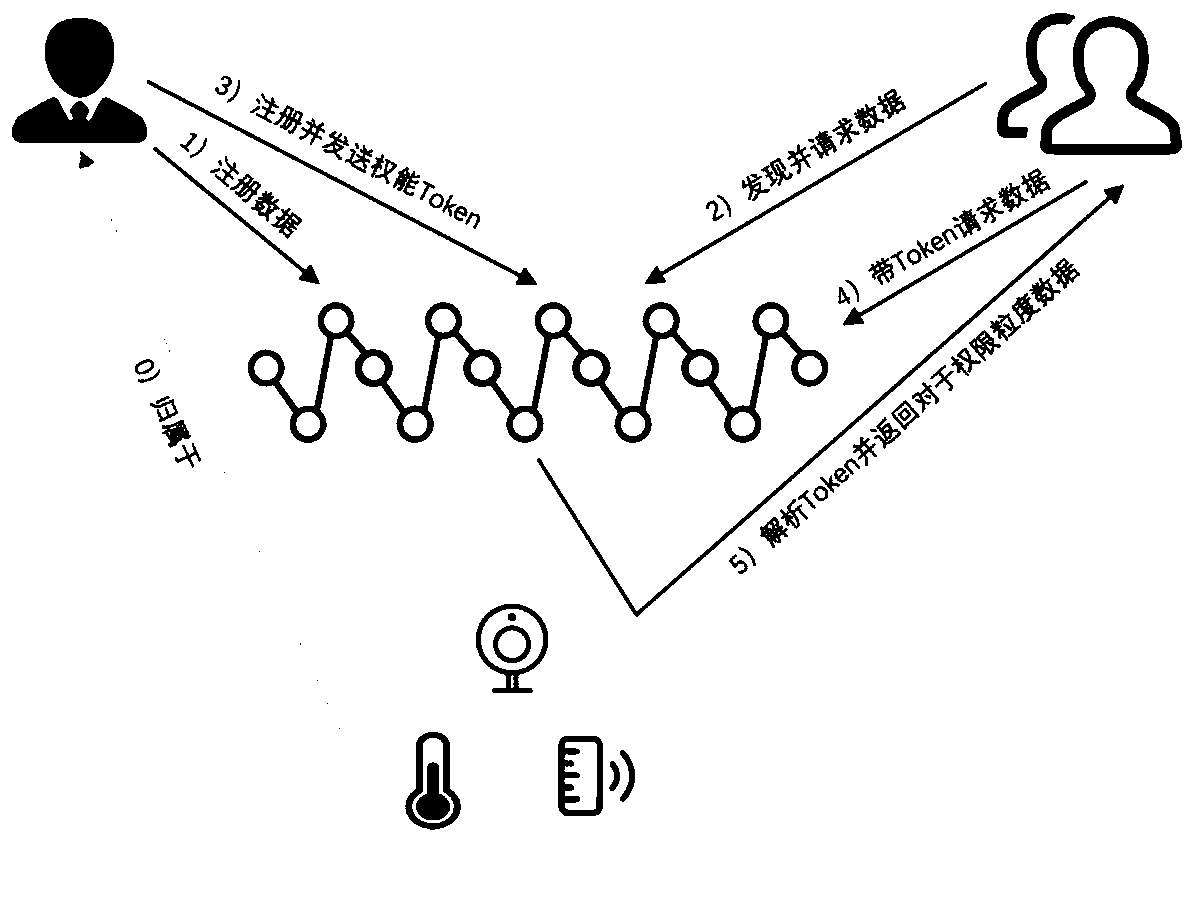
[0066] Step 001: User registration, other steps will verify whether the account address is registered, such as Figure 7 shown.
[0067] Step 002: User A registers the data information owned by user A and registers capabilities, such as Figure 9 shown.
[0068] Step 003: User B views the published data, such as Figure 10 shown.
[0069] Step 004: User B discovers the required data, registers the data request, and the system automatically adds the request to the requested data request list. Such as Figure 11 shown.
[0070] Step 005: User A reviews user B's request on the capability control page, and clicks Commit if he agrees, and Deny if he disagrees.
[0071] Step 006: If user A agrees to the request, use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com