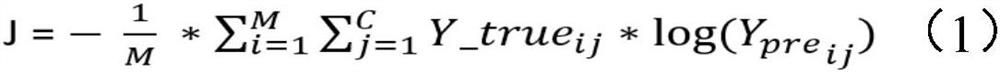A Software Security Vulnerability Detection Method Based on Tree-structured Convolutional Neural Network
A convolutional neural network and neural network technology, applied in the field of code vulnerability prediction in software source code, can solve problems such as insignificant effect, unfavorable code extraction, and imperfect functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be described in detail below with reference to the accompanying drawings and examples.
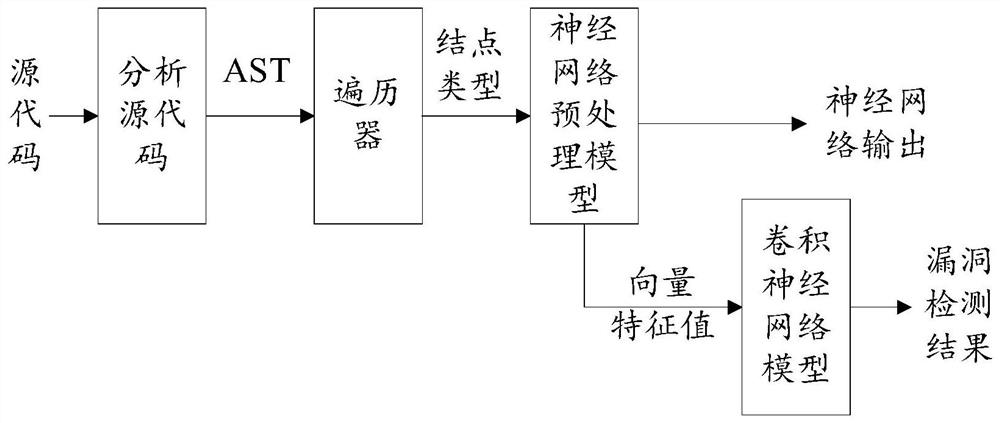
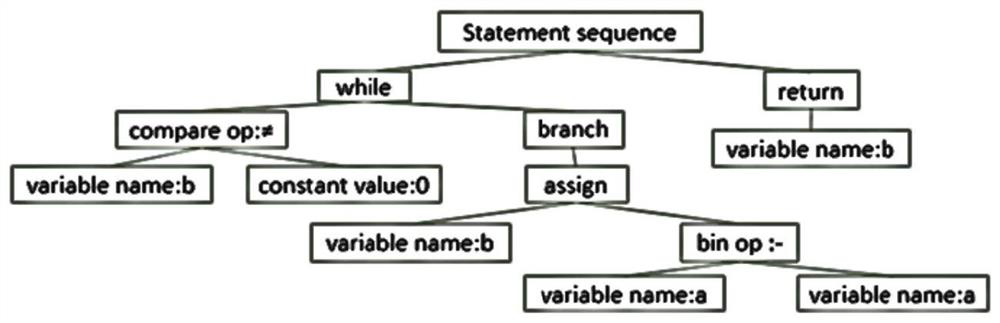
[0019] The models based on deep learning have achieved certain results, which also shows the powerful capabilities of deep learning in the field of vulnerability detection. However, the way they analyze and process source code ignores the structural features of the code itself, which is not conducive to obtaining all the features of the code. information. The present invention first proposes to apply the convolutional neural network based on the code syntax tree structure to the research of software vulnerability detection, obtain the syntax structure and semantic information of the code through the code syntax tree structure, preprocess the features through the neural network model, and obtain the syntax tree The vector feature representation of the node (the output of the embedding layer below), and then use the convolutional neural network as a code cla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com