Internet of Things security agent data sharing module design method adopting a block chain technology
A security proxy and data sharing technology, which is applied in the field of IoT security proxy data sharing module design using blockchain technology, and can solve problems such as using revocation users and cloud server collusion attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
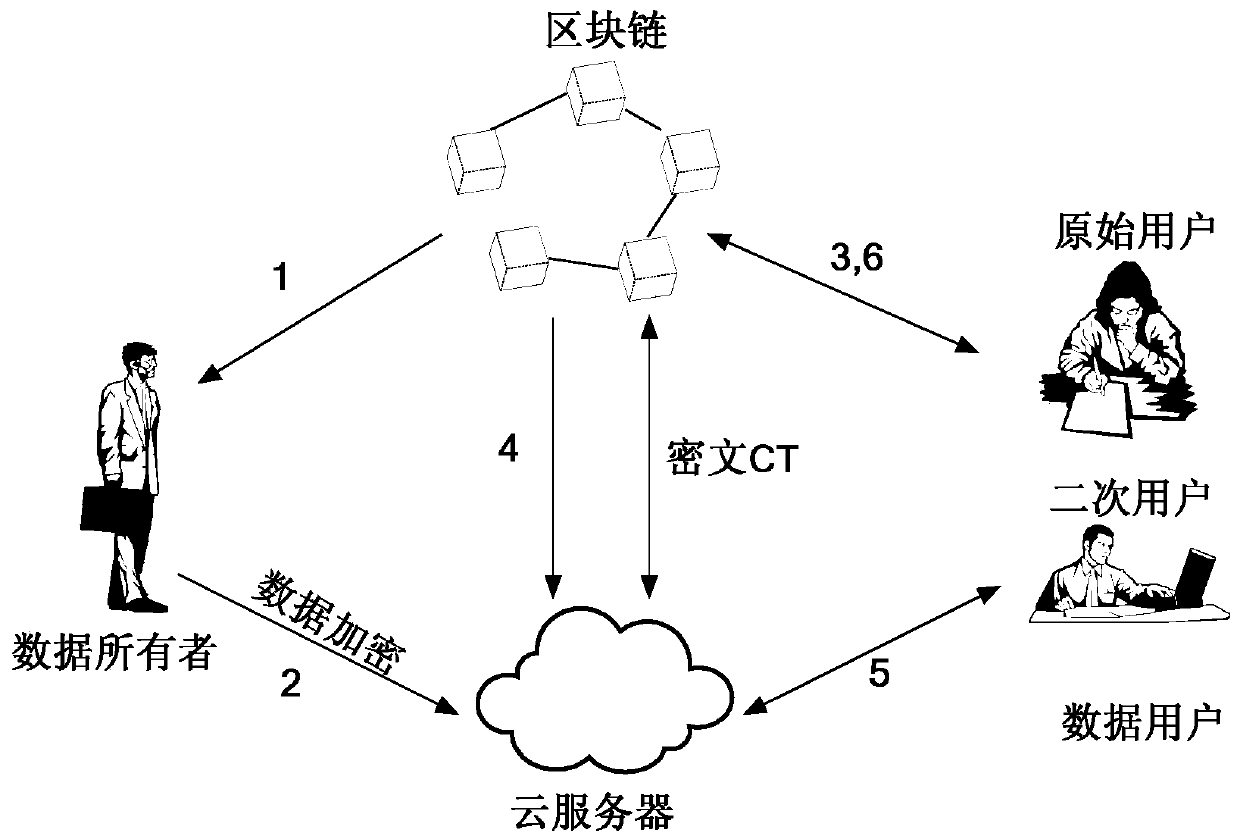
[0097] Such as figure 1 As shown, the Internet of Things data security sharing system of the present invention includes a blockchain network, a cloud server, a data owner and a data user. The data owner refers to the entity whose data is to be accessed, and the data can only be accessed when the private key of the data user corresponds to the attribute set specified by the data owner; the data user refers to the entity whose data is used by the system, and the data owner Both users and data users need to make predictions on the blockchain. The cloud server is a data repository, and all encrypted files are sent to the server through a secure channel.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com