User permission control and transfer method and system in edge cloud scene
A technology of user permissions and transfer methods, applied in transmission systems, electrical components, digital data authentication, etc., can solve the problems of complicated permission control, user over-authority access, and high mobility of edge cloud users, so as to avoid complicated permission control. , the effect of preventing information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
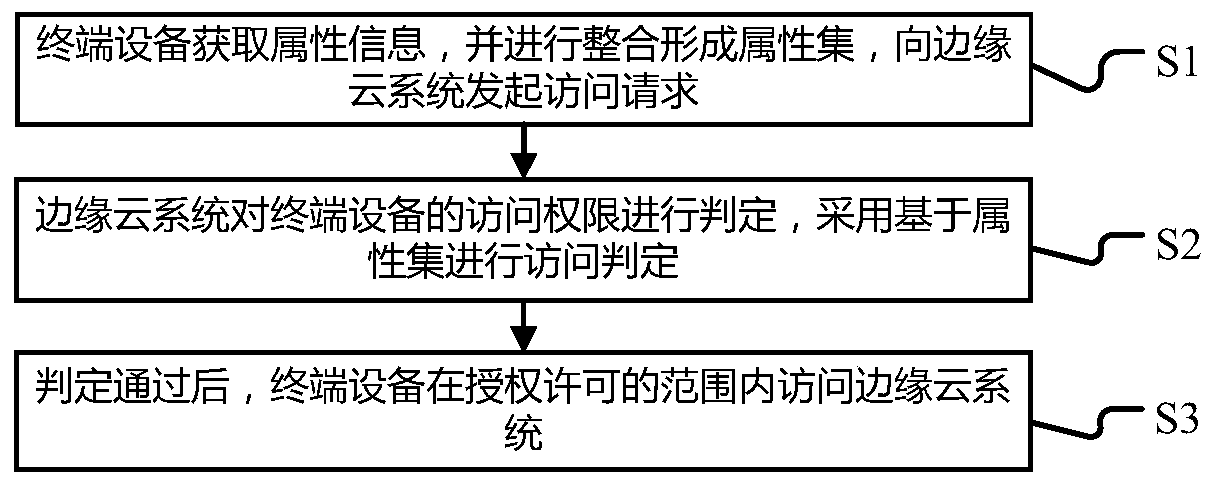
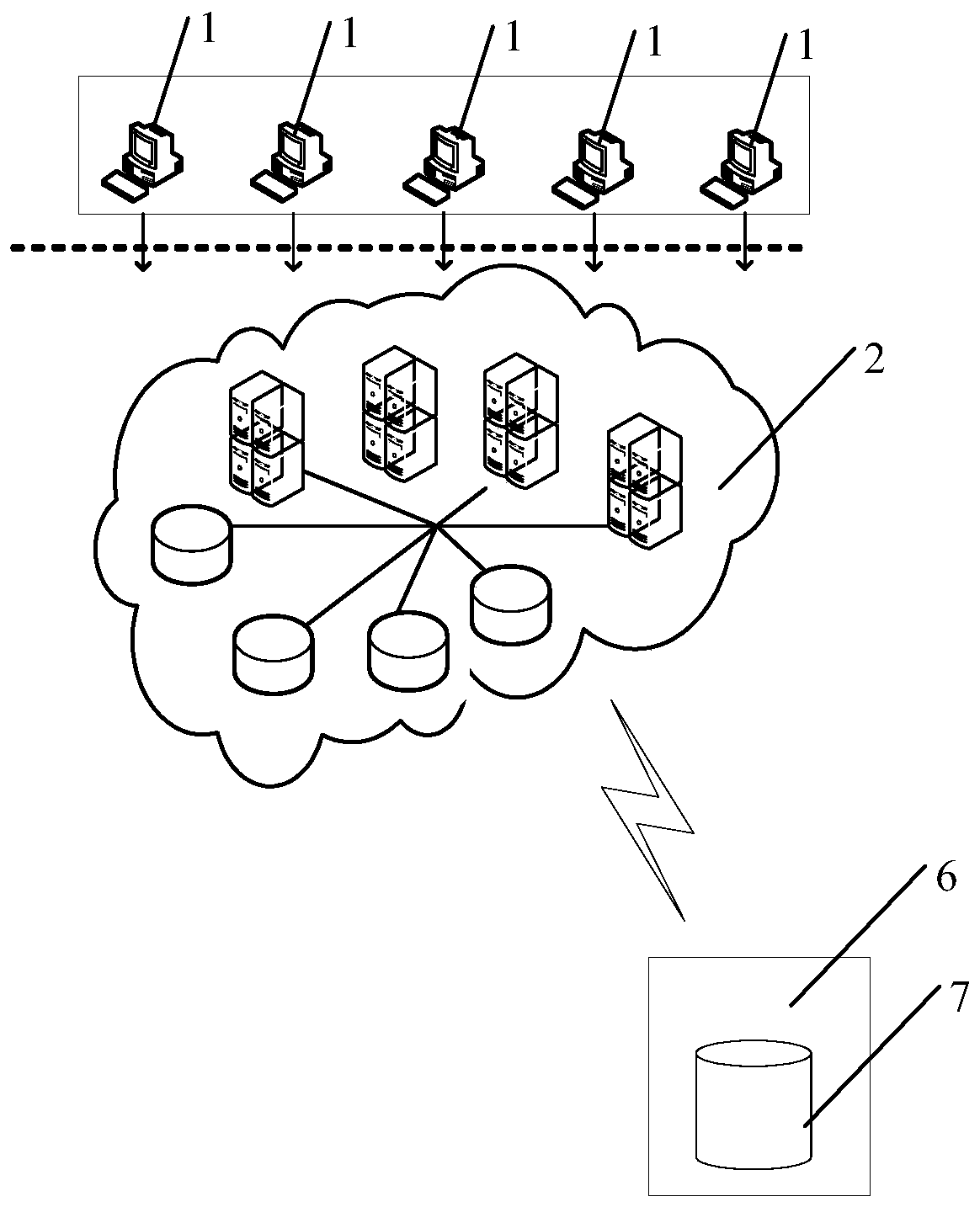
[0059] The present invention provides a user authority control and transfer method in an edge cloud scenario, such as figure 1 As shown, the methods include:
[0060] S1, the terminal device acquires attribute information, integrates it to form an attribute set, and initiates an access request to the edge cloud system;
[0061] The attribute information is input by the user, and may also be preset by the terminal device based on the running process.
[0062] Attribute information can be subject attribute, resource attribute, environment attribute, permission attribute and so on.
[0063] Principal attributes are instructions that can operate on resources. The resource attribute can be access resource information to the edge cloud system or resource information that needs to be obtained.
[0064] The permission attribute can be an attribute of a series of actions such as opening, reading, writing, deleting, and querying resources such as files, documents, images, and videos. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com