Unsafe XSS defense system identification method based on reinforcement learning
A defense system and reinforcement learning technology, applied in the field of network security, can solve problems such as being bypassed, and achieve the effects of avoiding losses, improving security, and strengthening defense capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
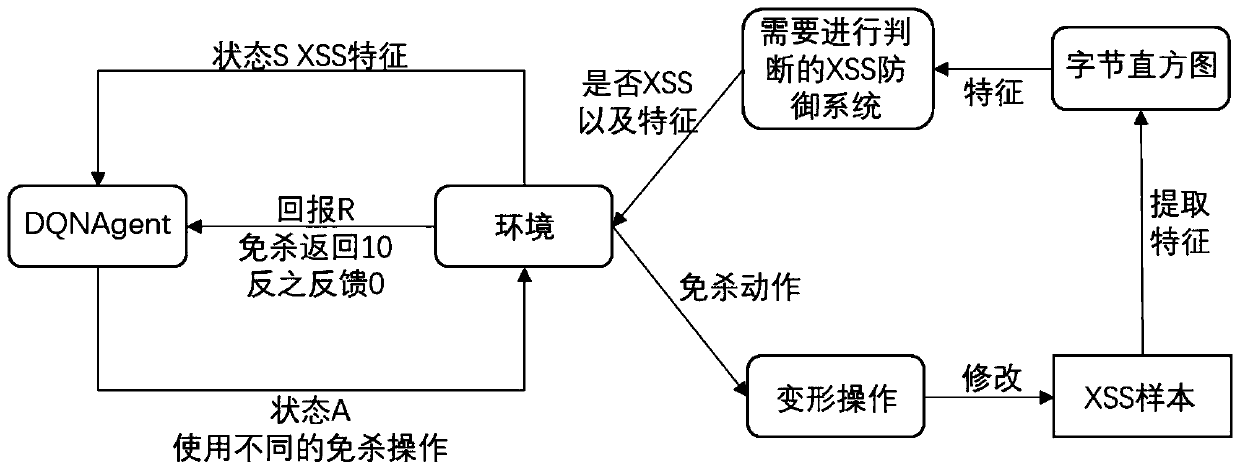
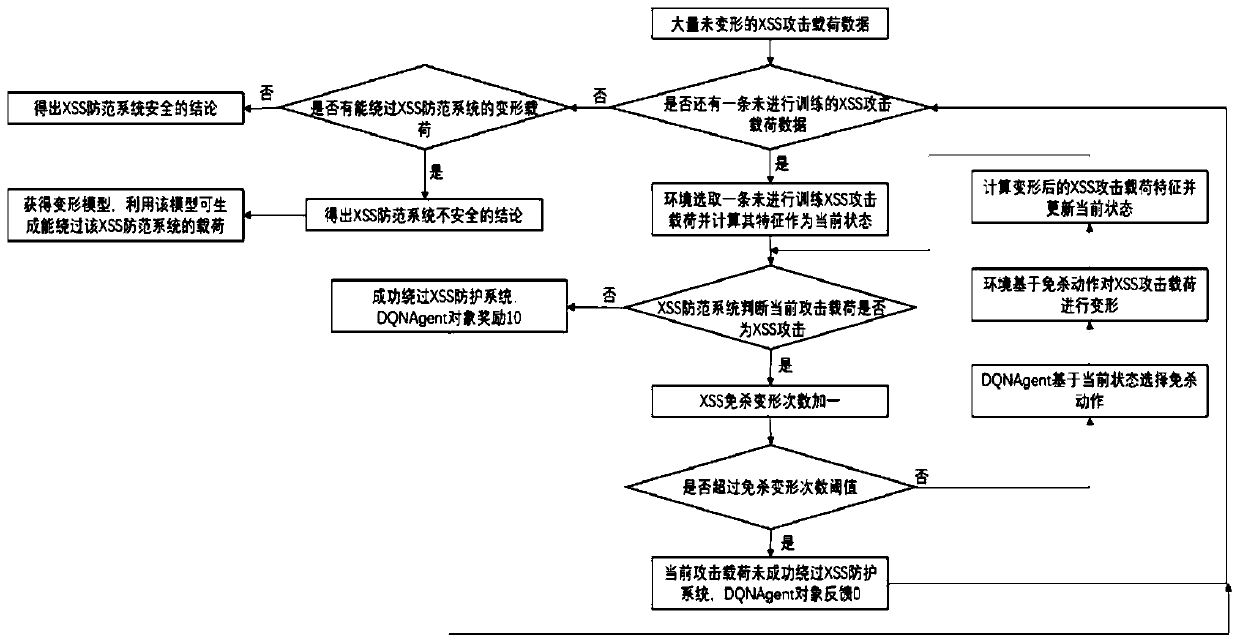
[0032] Such as figure 1 As shown, the present invention provides a method for identifying an insecure XSS defense system based on reinforcement learning, comprising the following steps:
[0033] S1. Use the Bytes Histogram method to perform feature extraction on the XSS attack load. The purpose of feature extraction is to vectorize the XSS attack load to extract features, and use the feature vector of the XSS attack load as the state to transfer.
[0034] Convert the XSS attack load string to a byte histogram (Bytes Histogram), and convert the string to a byte array, count the number of occurrences of each character, and add a dimension to indicate the string length, using the defined string length The frequency of occurrence is calculated for all byte occurrences, so as to avoid excessive characters from adversely affecting the model.
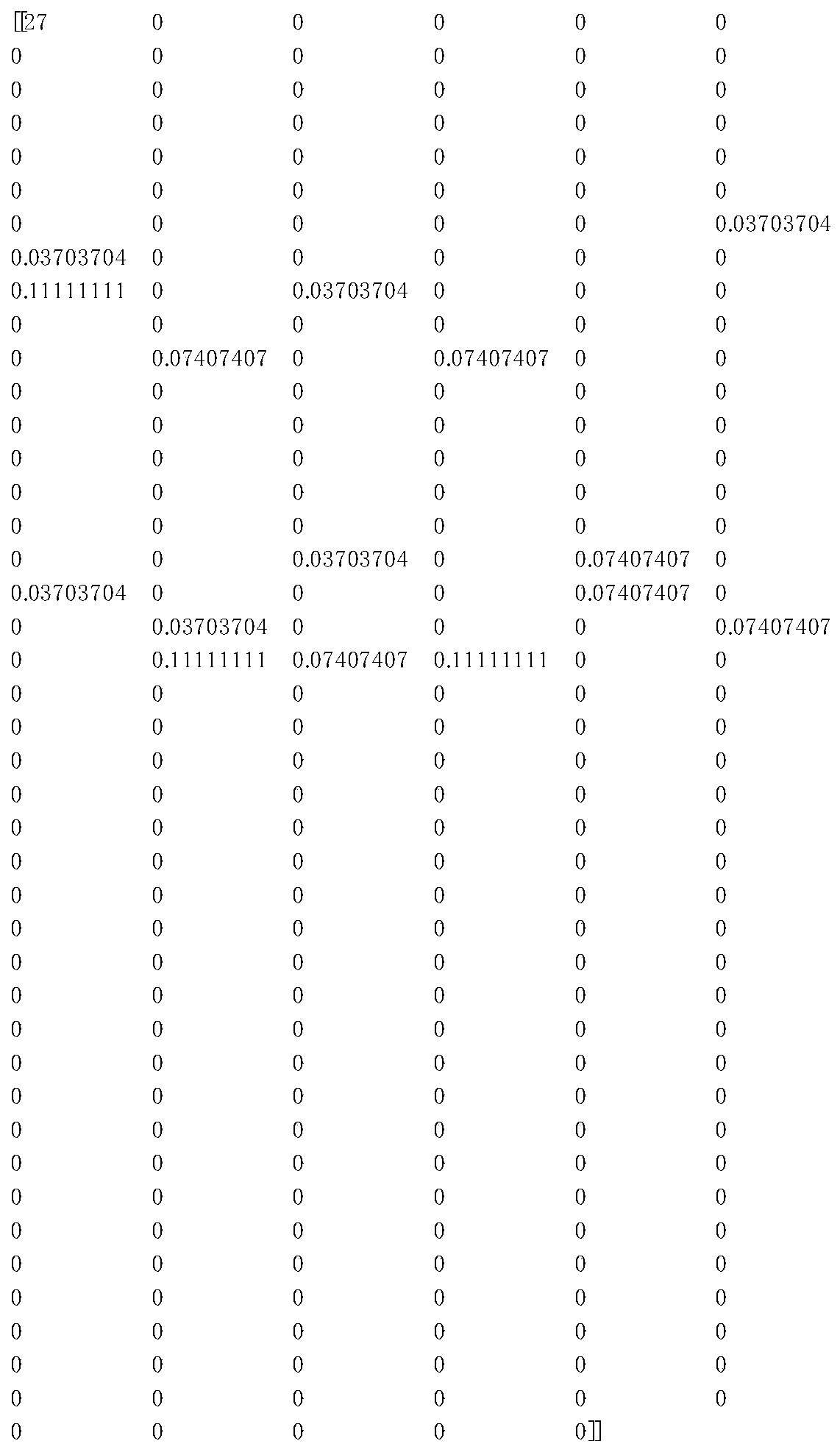
[0035] by alert( / 1 / ) As an example, through byte histogram conversion to get such as image 3 The 257-dimensional feature vector shown.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com