Identity authentication method, device, equipment and system and readable storage medium
A technology of identity authentication and equipment, applied in the direction of user identity/authority verification, transmission system, digital transmission system, etc., can solve problems such as information security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
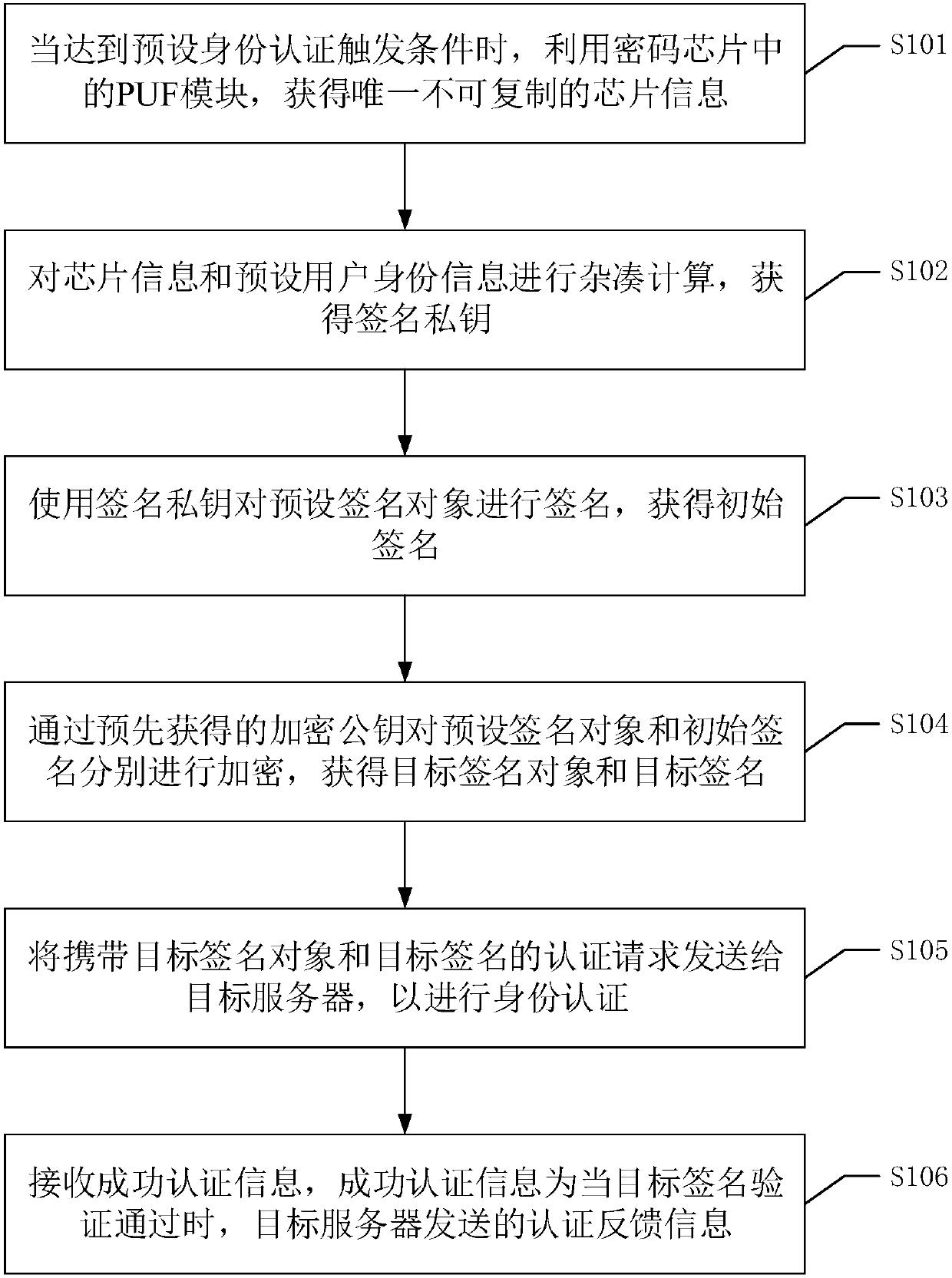
[0056] Please refer to figure 1 , figure 1 It is a flow chart of an identity authentication method in Embodiment 1 of the present invention, which can be used for a target client, and includes the following steps:
[0057] S101. When the preset identity authentication trigger condition is met, use the PUF module in the encryption chip to obtain unique non-replicable chip information.
[0058] Wherein, the target client may be a terminal device with an encryption chip such as a computer or a smart phone. The encryption chip may be a national secret chip.
[0059] Wherein, the preset identity authentication trigger condition may be when it is determined that the current user needs to perform identity authentication, such as logging in to a certain web page or a certain device. Specifically, the PUF module may be a module including a physically unclonable function circuit, and the module is made by utilizing the deviation of process parameters in the chip manufacturing process...
Embodiment 2
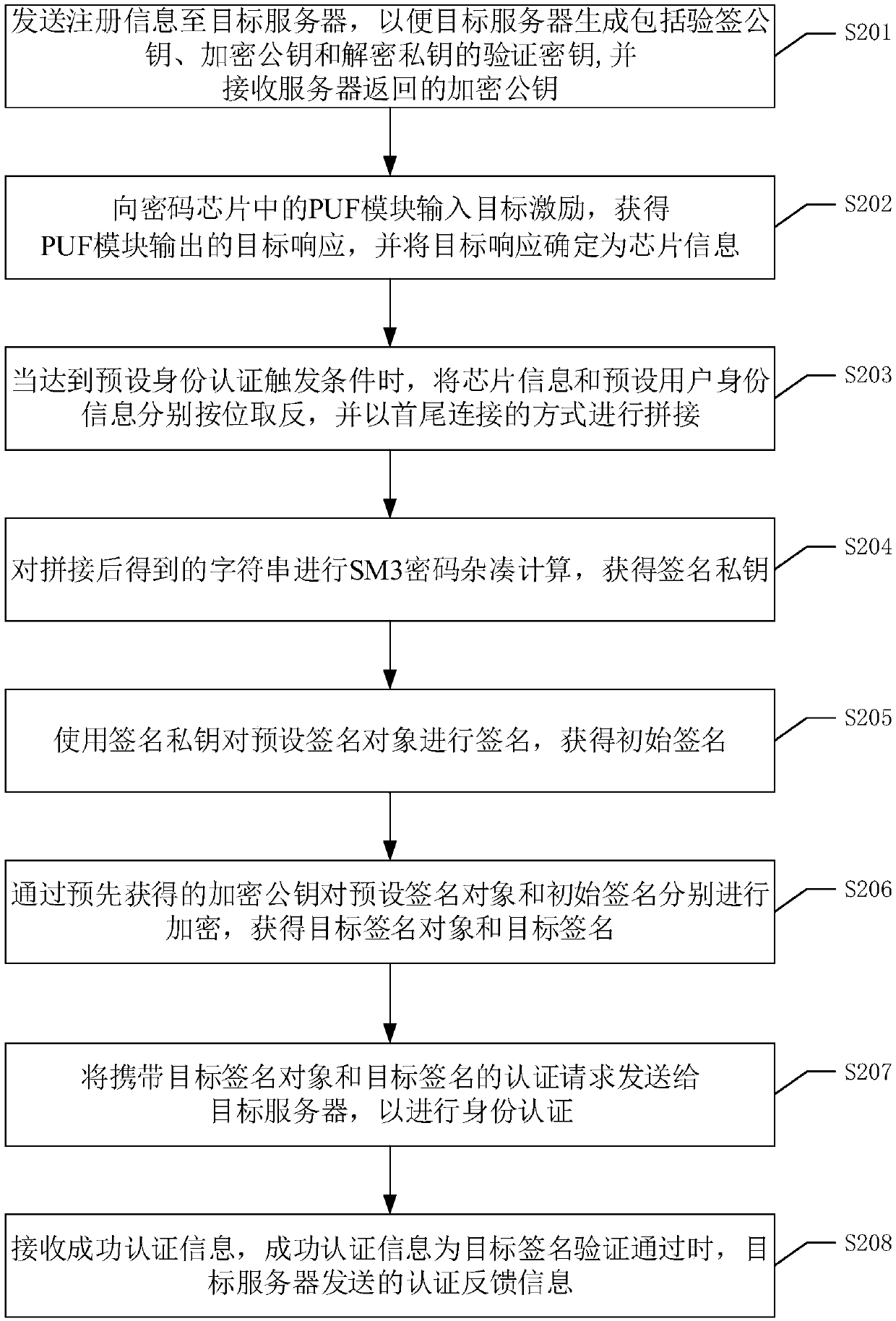
[0073] Please refer to figure 2 , figure 2 It is a flowchart of an identity authentication method in Embodiment 2 of the present invention, the method includes the following steps
[0074] S201. Send the registration information to the target server, so that the target server generates a verification key including a signature verification public key, an encryption public key, and a decryption private key, and receives the encryption public key returned by the server.
[0075] When the user registers in the target server through the target client, the target client sends the registration information to the target server. Wherein, the registration information is the same as the chip information and the preset user identity information. After receiving the registration information, the target server performs a hash operation on the registration information, and uses a public key generation algorithm to calculate a string of a set length obtained by the hash operation to obtai...
Embodiment 3
[0089] The technical solution provided by the present invention will be described in detail below by taking a specific application scenario of identity authentication between a client and a server as an example.
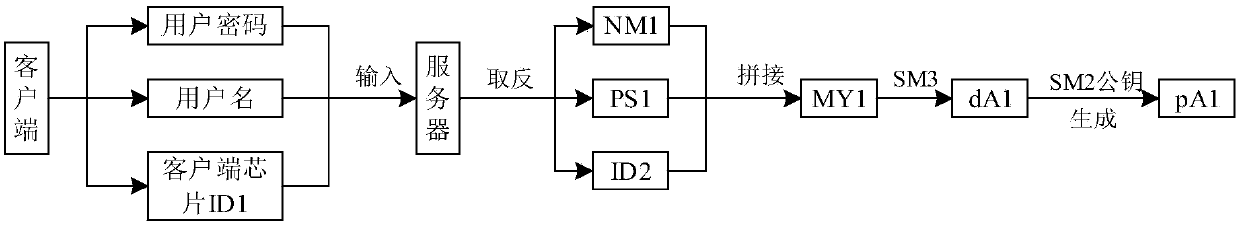
[0090] Please refer to image 3 , the process of user registration on the server through the client is as follows:
[0091]The client sends the user name, user password and client chip identity information (client chip ID1 shown in the figure) entered by the user to the server. Among them, the client chip ID1 is a unique non-replicable information generated by the PUF module in the national secret chip in the client. The server reverses the received user name, user password, and client chip ID1 bit by bit, and obtains the reversed information corresponding to the user name, user password, and client chip ID1, such as NM1, PS1, and ID2 in the illustration. After negation, connect NM1, PS1 and ID2 end to end in turn to obtain a character string MY1. Then perform SM3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com