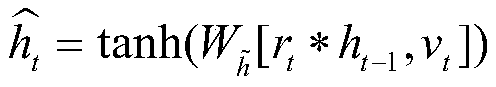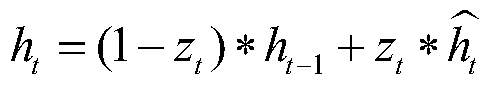Injection attack detection method based on gating cycle unit and attention mechanism
A technology of injecting attack and loop units, applied in neural learning methods, digital data information retrieval, unstructured text data retrieval, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
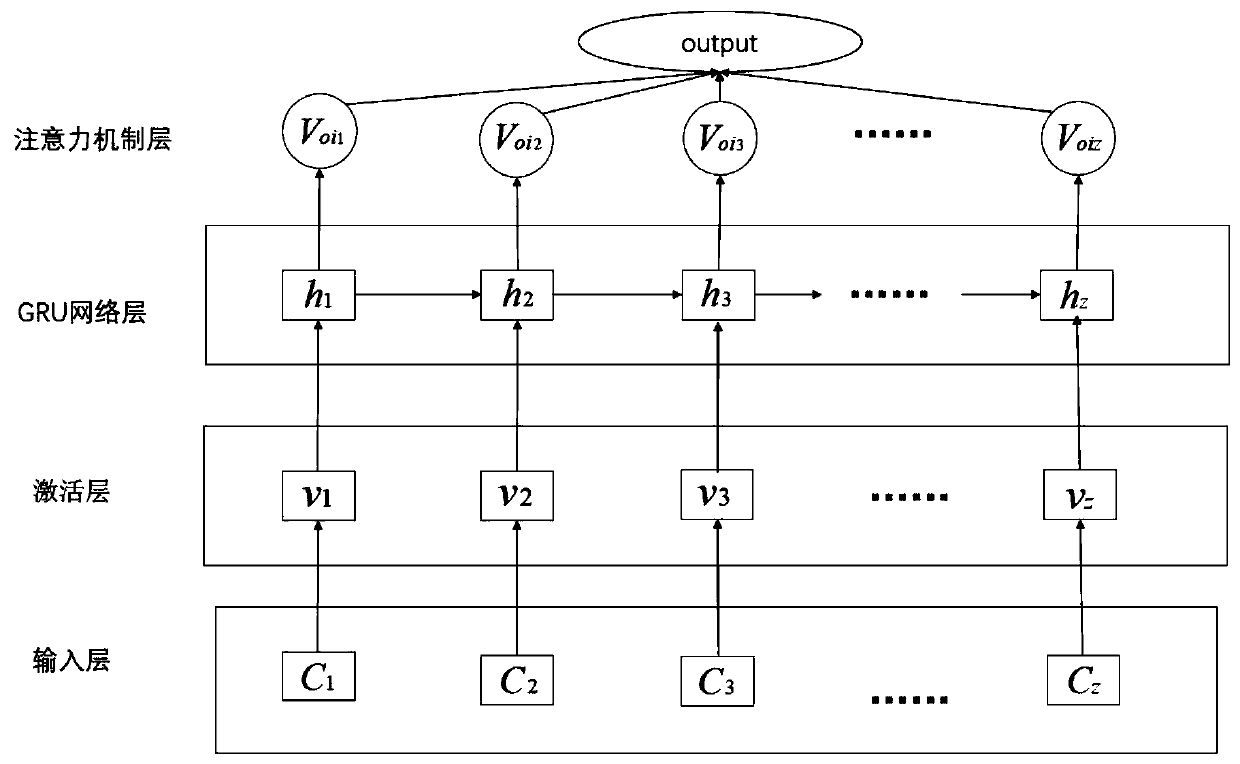
[0046] The present invention will be further described below in conjunction with a common injection attack—a practical example of SQL injection attack detection.
[0047] Take SQL injection attack detection as an example:
[0048] Using the present invention to realize SQL injection attack detection can be divided into two stages to construct an injection attack detection model. There are two stages: preprocessing stage and training stage. In general, in the preprocessing phase, the input data is preprocessed and formatted for use in the training phase; the process is described in detail below:
[0049] 1. Preprocessing stage
[0050] 1.1 Data Standardization
[0051] In this phase, the data needs to be normalized. Standardize some morphemes (such as reserved words in SQL statements, database table names, special symbols, etc.) in combination with the actual situation of SQL statements, that is, classify according to the standardized word symbol mapping table (that is, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com