Encrypted traffic classification method based on two-stage judgment
A traffic classification, two-stage technology, applied in the field of network security and user privacy, can solve the problems of accuracy rate limitation, unsatisfactory, technology has not been widely used, etc., to achieve the effect of improving the classification accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
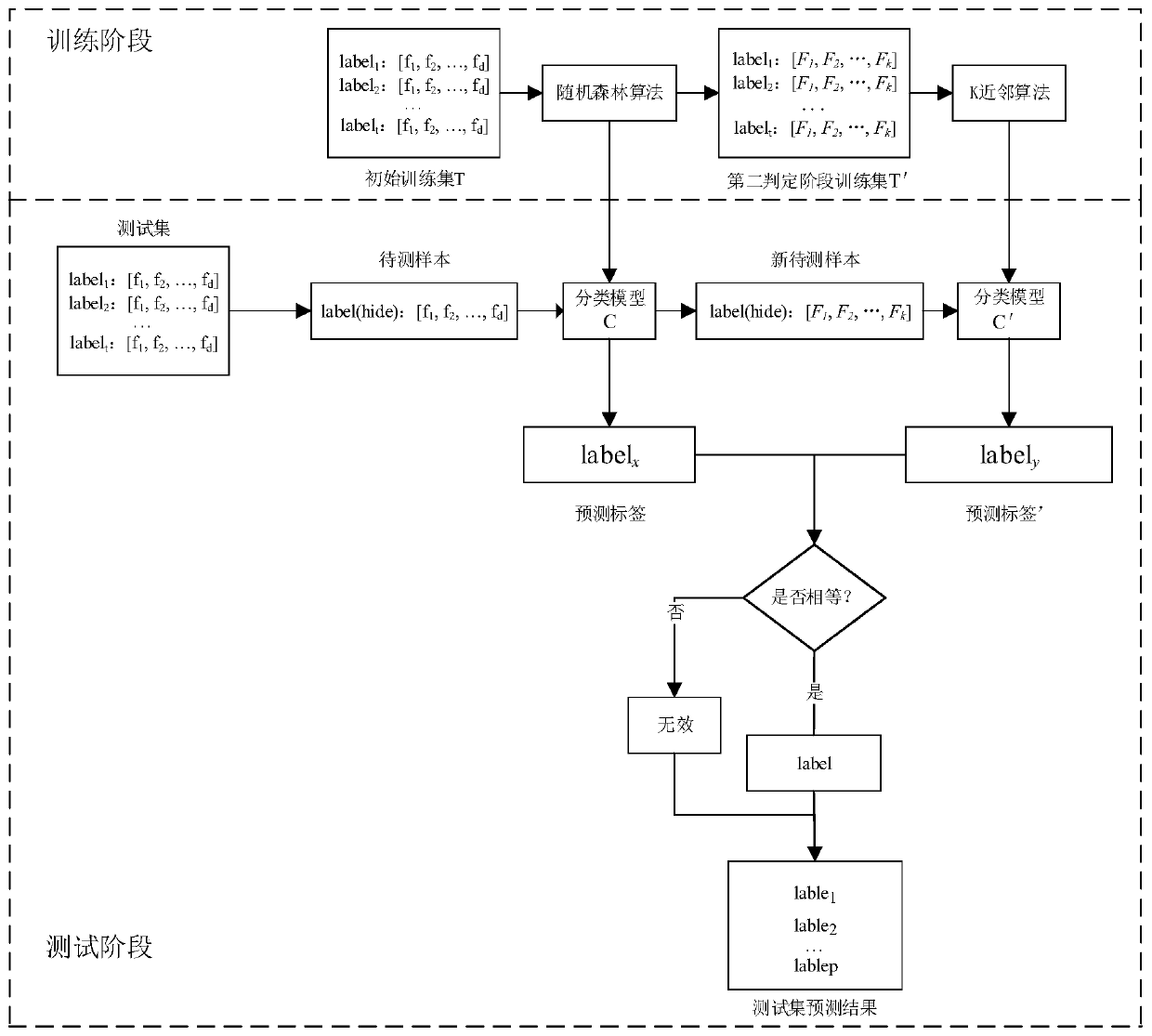
[0039] Step 1: First, the user provides a collection of encrypted traffic samples. Each encrypted traffic sample in the collection is an original traffic file containing data packets, and has a unique encrypted traffic type label, and the user provides a d-dimensional feature vector, which is recorded as a meta-feature vector. Then extract d-dimensional sequence features for each encrypted traffic, denoted as [f 1 ,f 2 ,..., f d ]. Assuming that there are a total of p encrypted traffic samples, the encrypted traffic type of the i-th encrypted traffic sample is marked as label i Then the encrypted traffic data set is recorded as T, expressed as follows:
[0040] {label 1 :[f 1 ,f 2 ,..., f d ], label 2 :[f 1 ,f 2 ,..., f d ],...,label p :[f 1 ,f 2 ,..., f d ]}
[0041] The sample label label is the network address of each flow, and the sample feature dimension is d.
[0042] Step 2: Train the classification model in the first judgment stage, use the random for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com