Key storage method, device and server
A key server and key storage technology, applied in the field of key storage methods, devices and servers, can solve the problems of low computing performance, poor scalability, and inability to realize data sharing, and achieve the effect of enhancing security and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
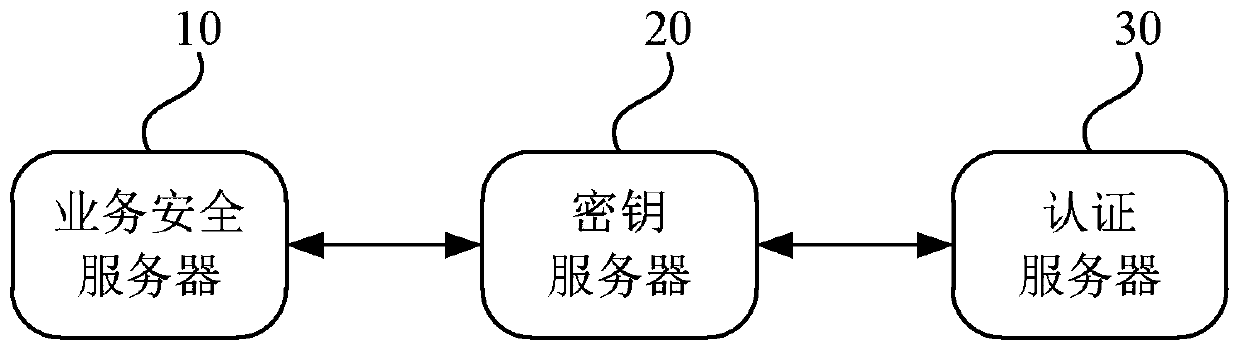
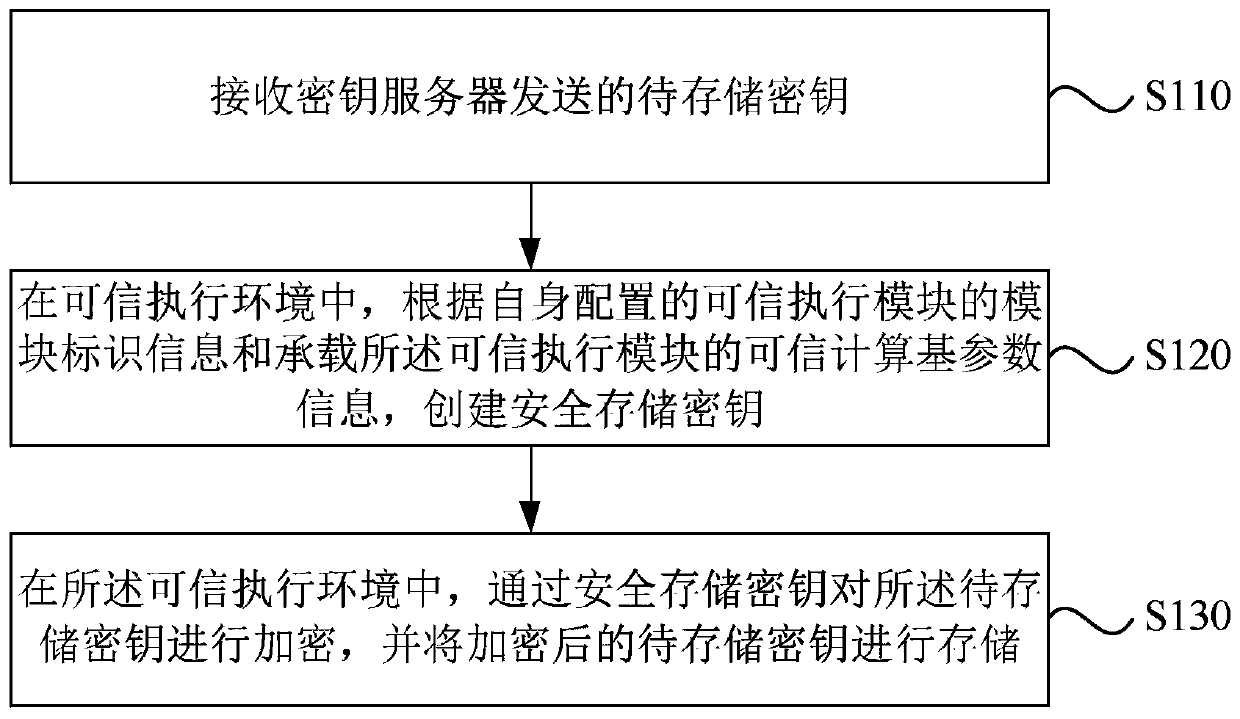
[0047] Figure 1B It is a flow chart of a key storage method in Embodiment 1 of the present invention. The present invention is applicable to the case where the key is safely stored in a shareable business security server. The method is executed by a key storage device, and the device It is implemented by software and / or hardware, and is specifically configured in a business security server.
[0048] like Figure 1B A key storage method shown is applied to a business security server, including:
[0049] S110. Receive the key to be stored sent by the key server.
[0050] Wherein, the key to be stored may be key information with certain security risks, such as a root key.
[0051] In this step, the key to be stored is generated by the key server and sent to the service security server. Correspondingly, the service security server receives the key to be stored.
[0052] It should be noted that, in order to enhance the security of data transmission between the key server and ...
Embodiment 2
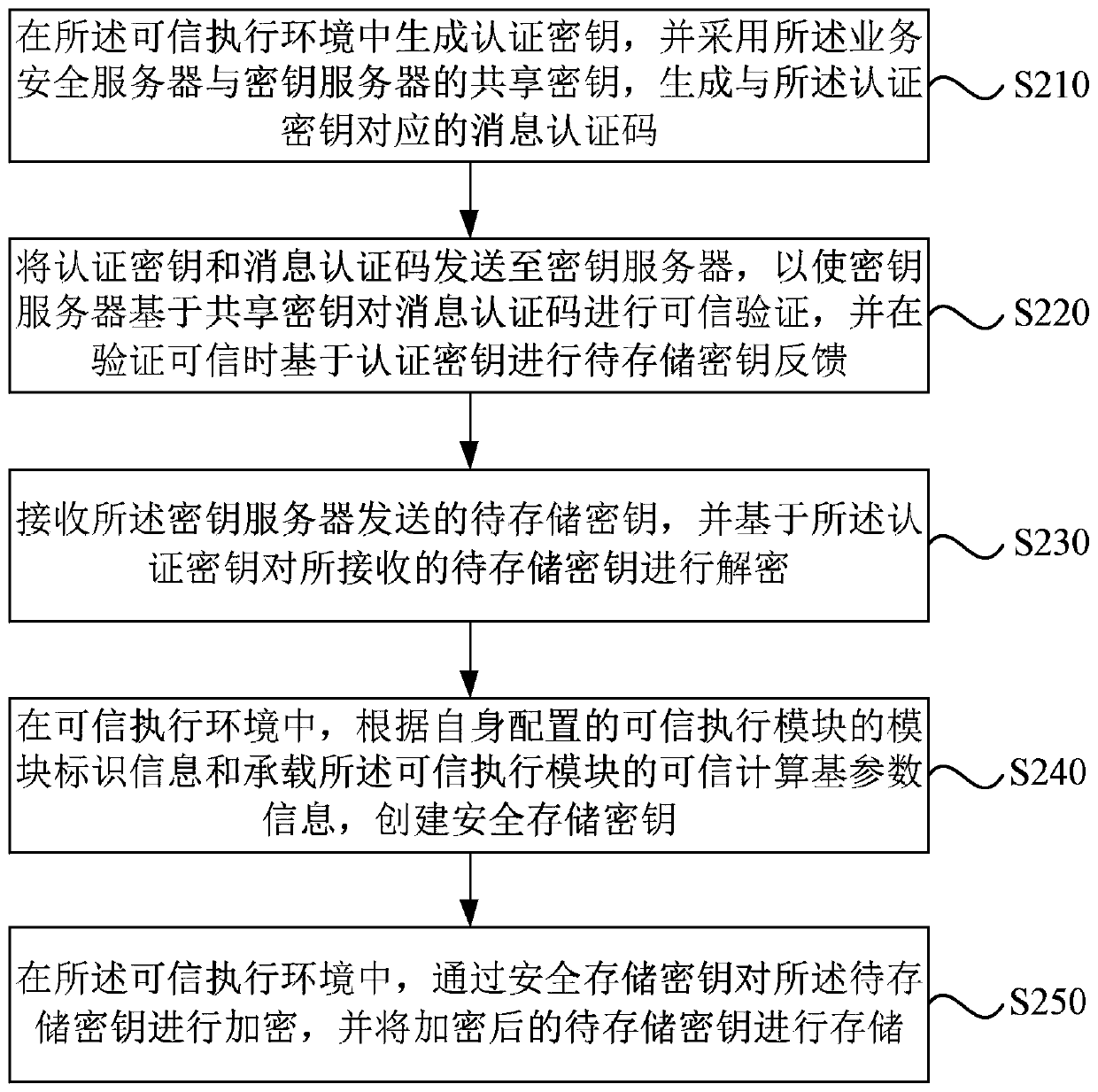
[0067] figure 2 It is a flow chart of a key storage method in Embodiment 2 of the present invention. This embodiment of the present invention is optimized and improved on the basis of the technical solutions of the foregoing embodiments.
[0068] Further, before the operation "receive the key to be stored sent by the key server", add "generate the authentication key in the trusted execution environment, and use the shared key of the business security server and the key server, generating a message authentication code corresponding to the authentication key; sending the authentication key and the message authentication code to the key server, so that the key server can authenticate the message based on the shared key The authentication code is credible, and when the verification is credible, the key to be stored is fed back based on the authentication key"; correspondingly, the operation "receiving the key to be stored sent by the key server" is refined into "receiving the sto...
Embodiment 3
[0083] image 3 It is a flow chart of a key storage method in Embodiment 3 of the present invention. This embodiment of the present invention is applicable to the case where the key is safely stored in a shareable business security server. The method is executed by a key storage device. The device is realized by software and / or hardware, and is specifically configured in the key server.
[0084] like image 3 A key storage method shown is applied to a key server, including:
[0085] S310. Generate a key to be stored.
[0086] Wherein, the key to be stored may be key information with certain security risks, such as a root key.
[0087] In this step, the key server generates a key to be stored according to the key generation mechanism set by itself, and sends it to the business security server. Correspondingly, the service security server receives the key to be stored.
[0088] S320. Send the key to be stored to the service security server, so that the service security server...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com