Encryption method and system based on information transmission
A technology of information transmission and encryption method, which is applied in the field of encryption, can solve the problems of poor security, poor information security, and no protection, etc., and achieve the effect of small dependence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
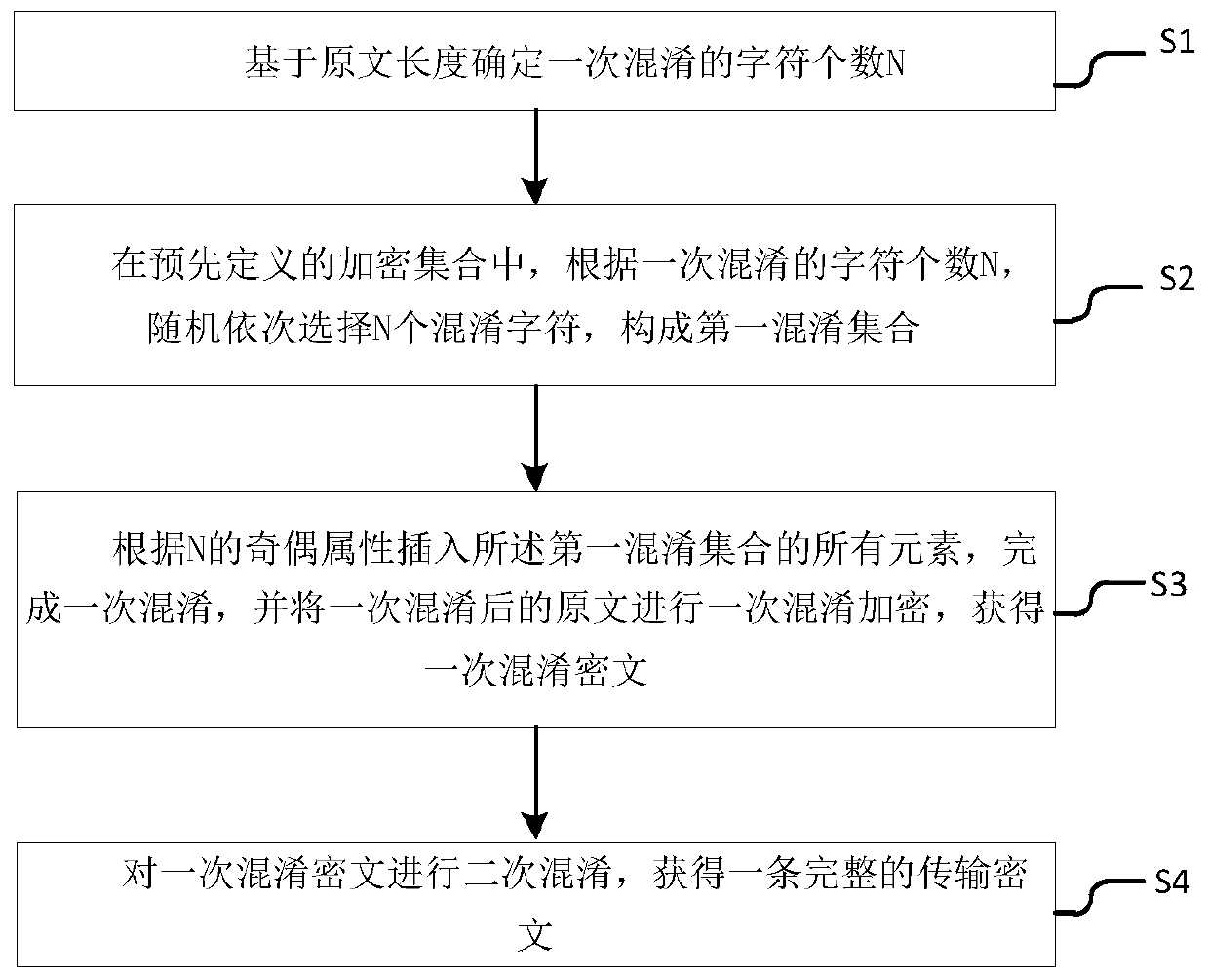
[0056] Embodiment 1: Determine the character number N that is confused once based on the length of the original text; in the pre-defined encryption set, according to the character number N that is confused once, randomly select N confusing characters in turn to form the first confusing set;
[0057] When N is an odd number, all elements of the first confusion set are inserted sequentially in the original text from small to large odd-numbered column positions;
[0058] When N is an even number, then insert all elements of the first confusion set in sequence from small to large even column positions in the original text;
[0059] Obtain an obfuscated ciphertext after one obfuscated encryption, calculate the adding position of the next obfuscated character based on the length of the first obfuscated ciphertext, and insert the obfuscated characters to obtain a complete transmission ciphertext.
[0060] Among them, the number N of characters to be confused based on the length of th...
Embodiment 2
[0078] Embodiment 2: Based on the same inventive concept, the present invention also provides an encryption system based on information transmission, including:
[0079] A determination module is used to determine the number N of characters to be confused based on the length of the original text;
[0080] A building block, used to randomly select N obfuscated characters in sequence according to the number N of obfuscated characters in a predefined encryption set to form a first obfuscated set;
[0081] A primary obfuscation module, configured to insert all elements of the first obfuscation set according to the parity attribute of N, complete an obfuscation, and perform an obfuscation encryption on the original text after an obfuscation to obtain an obfuscated ciphertext;
[0082] The acquisition module is used to perform secondary obfuscation on the primary obfuscated ciphertext to obtain a complete transmission ciphertext.
[0083] Those skilled in the art should understand ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com