Method for detecting network flood attack behaviors
A detection method and behavioral technology, applied to electrical components, transmission systems, etc., can solve problems such as high misrecognition rate, increased method cost overhead, and reduced real-time efficiency of the method, so as to reduce detection cost, improve detection sensitivity, and improve The effect of applicable space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
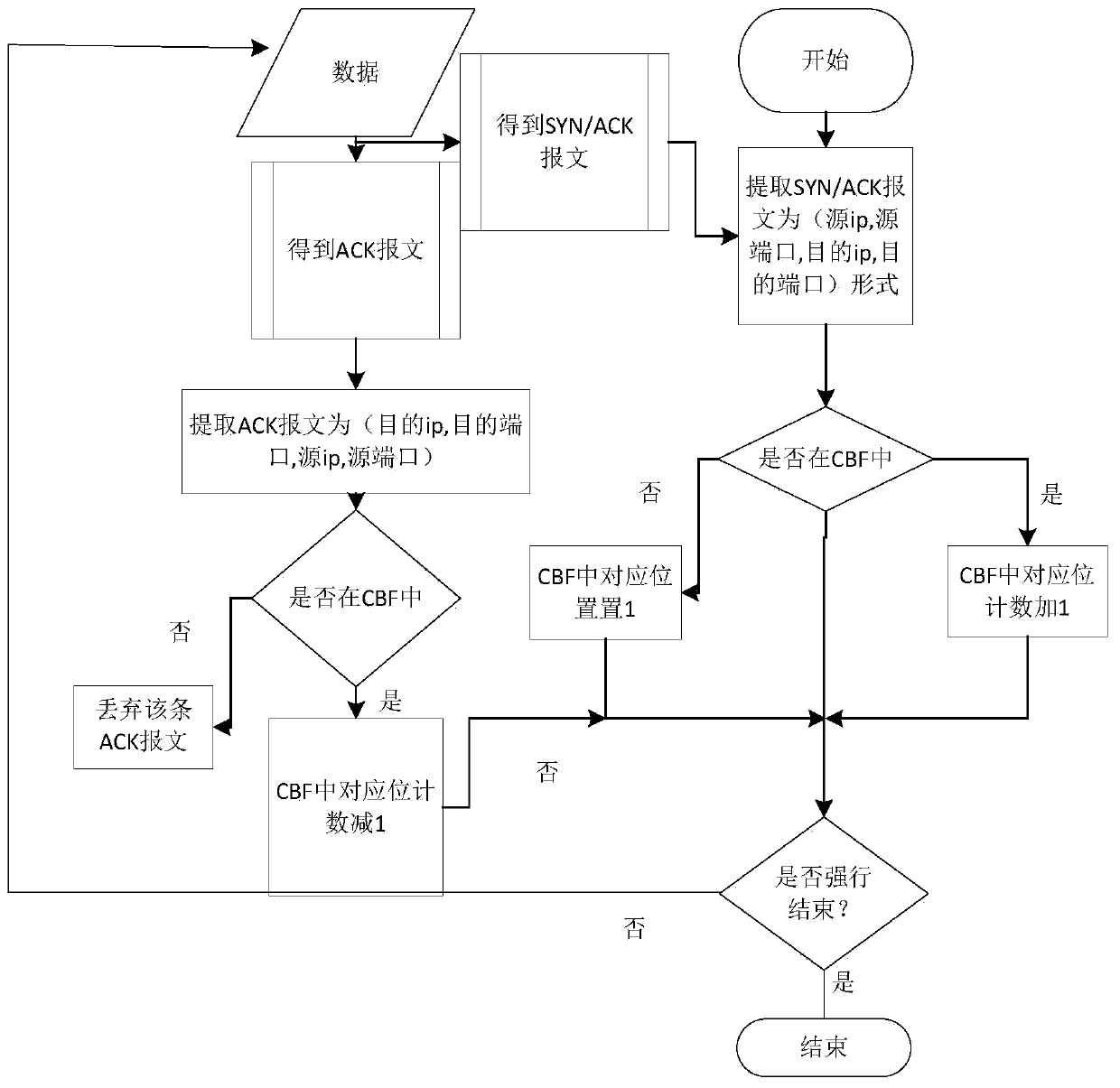
[0058] Packet Statistics Based on Counting Bloom Filter
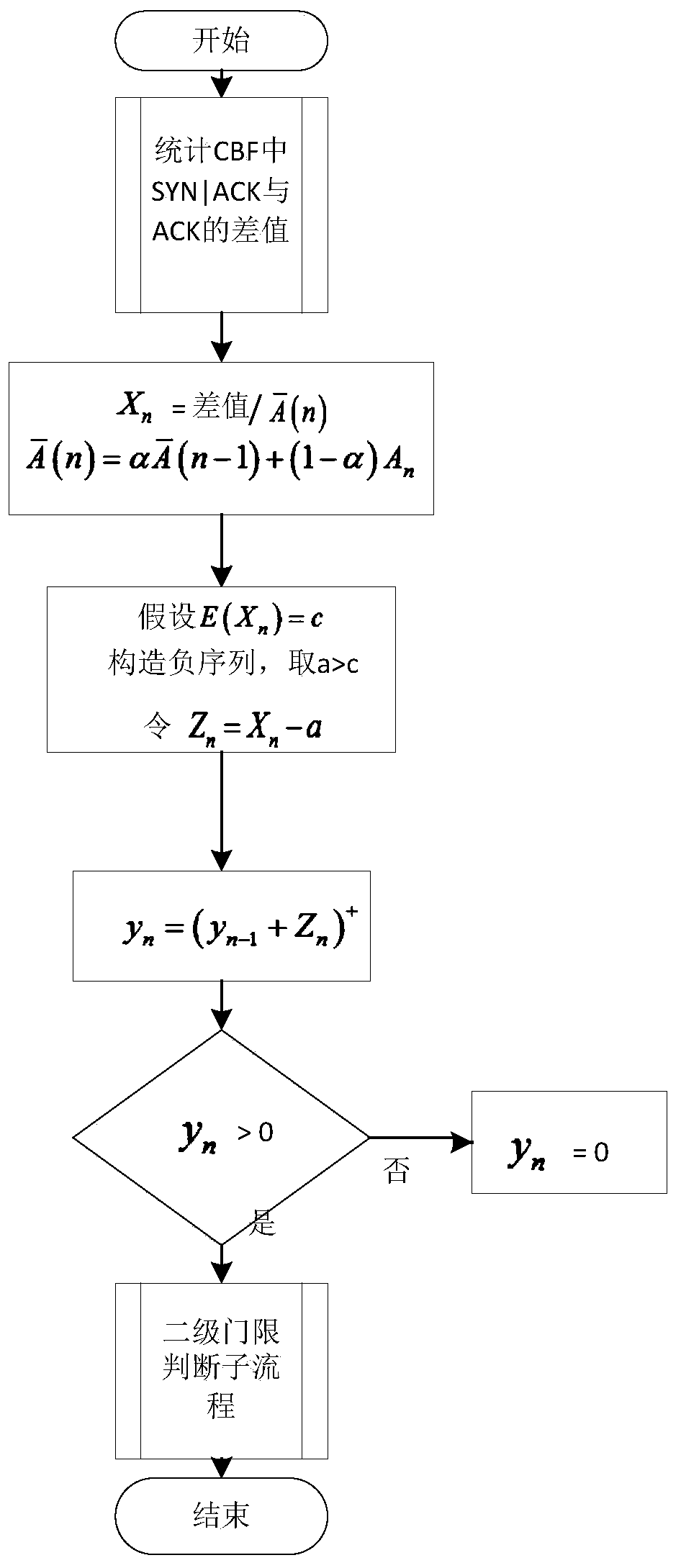
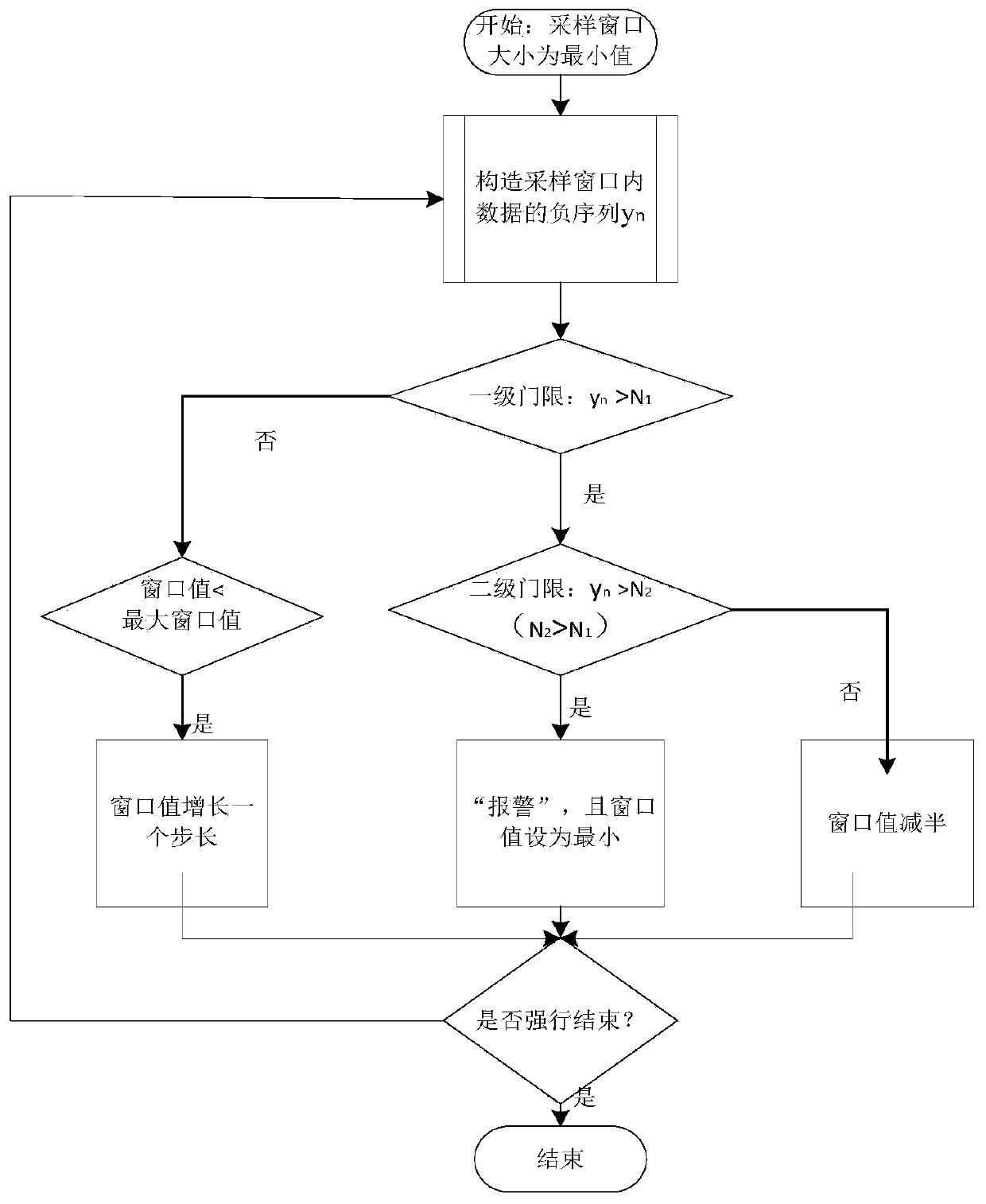
[0059] When analyzing various network problems, a network stream connection is generally marked with a standard quintuple (source IP address, source port, destination IP address, destination port, transport protocol). According to the statistics of the DDoS attacks that have occurred, more than 90% of them are TCP floods, and among the TCP floods, SYN floods are the most common. When a SYN flood attack occurs, the number of SYN request connection packets in the network will increase rapidly, and the distribution of IP addresses and ports of the packets will also change. In order to make the attack easy to control, attack packets are generally forged by attack software. Due to software settings and other related problems, source IP addresses will be reused in large quantities, and the distribution is relatively concentrated, and there are certain rules to follow. In order to cover up their location and increase the diff...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com