Method for judging e-mail address scanning behaviors
A technology of email address and email address, which is applied in the field of judgment of email address scanning behavior, can solve the problems of no identification and interception of email address scanning behavior, theft of important data information of users, etc., and achieve effective identification and interception of email address scanning Behavior, improve security and privacy, improve the effect of user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
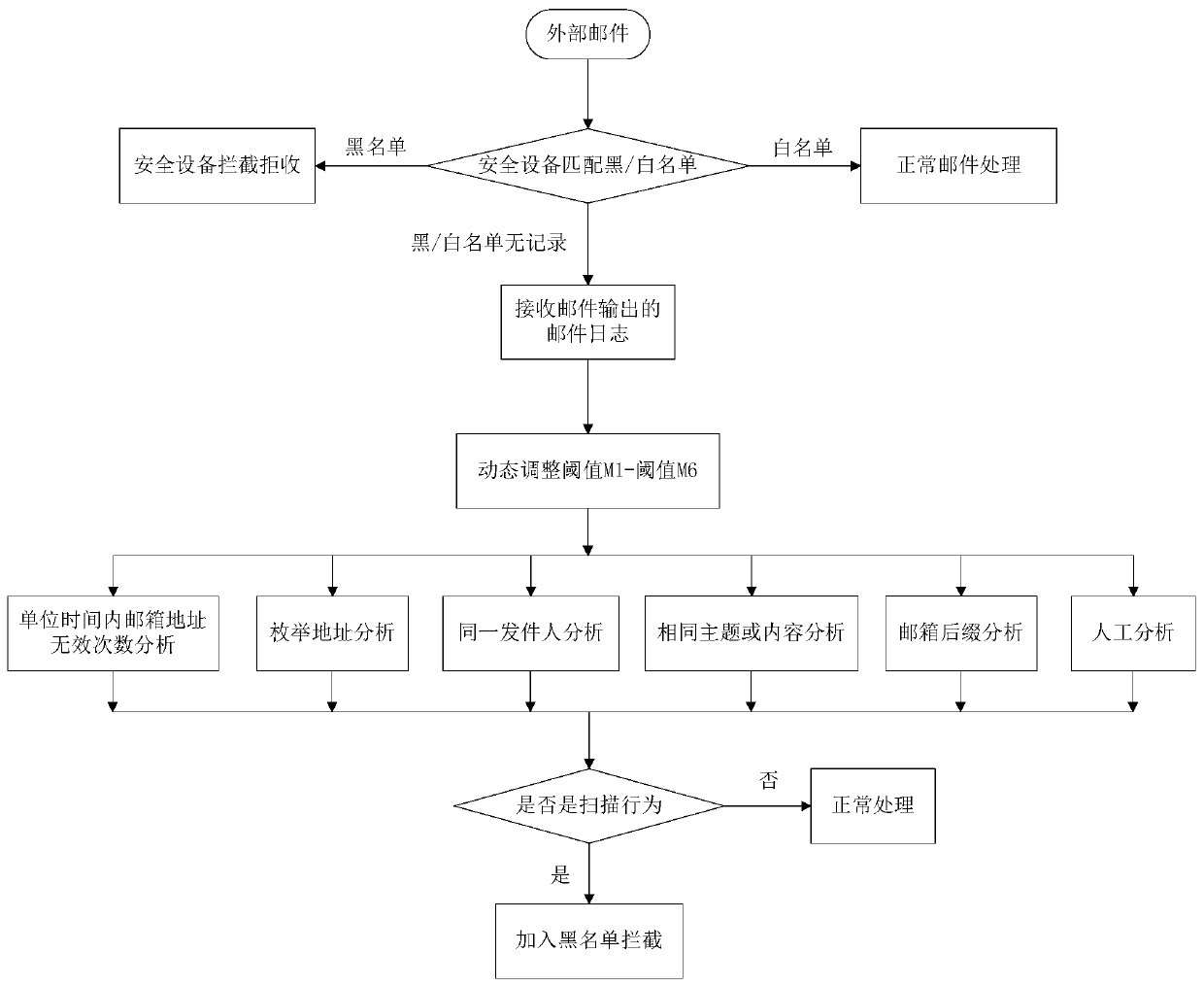
[0026] Such as figure 1 The method for judging the scanning behavior of the e-mail address of the present invention includes:
[0027] A. First, intercept incoming emails and / or external email sources through security devices such as firewalls and email security gateways. If the intercepted incoming emails and / or external email sources can match the blacklist records in the security device, disconnect the network connection and mail protocol, otherwise continue. In this way, the attacker can only perceive that the connection is disconnected, but cannot know the status code of the returned email, and then cannot know whether the email address really exists, and cannot achieve the purpose of email address scanning. In addition, mailbox users will not receive scanned emails, which improves user experience and prevents waste of email system resources.
[0028] If the intercepted incoming mail and / or external mail sources match the whitelist records in the security device, the se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com